What is a honeypot in cybersecurity, and how does it work?
A honeypot in cybersecurity is a deliberately vulnerable system meant to attract attackers and observe their behavior, allowing security teams to study their attack techniques.
In this article, we’ll discuss how honeypots work, what their role is, and their benefits and risks in a cybersecurity setting.
What is a honeypot?
A honeypot (or a network honeypot) is a decoy system specifically designed to attract and interact with visitors, such as opportunistic attackers, automated scanners, or testing tools. It provides a controlled environment to study attacks without risking production assets. Honeypots often include intentional network weaknesses ready to be manipulated.
Cybersecurity teams can use honeypots to collect data about:
- Infiltration methods
- Attacker motives and targets
- Exploits and malware techniques
- Security weaknesses in the network environment
- Lateral movement and attacker behavior within a network
With the right security architecture, honeypots can make teams aware of new attack patterns before production systems are affected.
When multiple honeypots are used in the same network, this is called a honeynet. From the outside, it looks like a genuine network, with databases, routers, servers, and other systems.
How do honeypots work?
A honeypot will be designed to look like a legitimate and valuable target. It could be a payment gateway, banking interface, Internet of Things (IoT) device, Secure Shell (SSH) server, or an industrial control system (ICS). By simulating real systems like this, honeypots attract attackers and allow security teams to observe unauthorized access in a controlled environment.
Attracting attackers with decoy systems
To make a honeypot appealing, it may include realistic infrastructure such as databases, routing systems, and decoy data (like fake financial or health records). Deliberate vulnerabilities, like open ports or weak passwords, are often introduced to entice attackers further. However, if the system is too obviously vulnerable, attackers may recognize it as a trap and avoid engaging with the system, so these vulnerabilities must be carefully considered.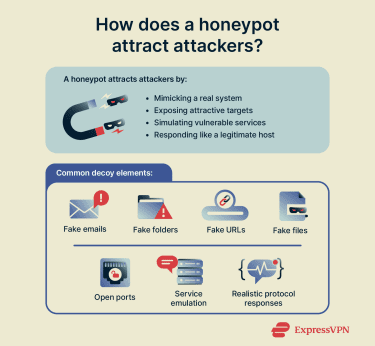
Monitoring malicious activity
Once the attacker engages with the honeypot, security teams can observe behavior such as:
- Intrusion attempts and exploit execution: Which vulnerabilities are targeted, and whether privilege escalation is attempted.
- Commands and tools used: Scripts executed, malware uploaded, or keystrokes captured.
- Data access attempts: Files or information the attacker tries to access, modify, or delete.
- Lateral movement: Attempts to explore the network or access other systems.
Some honeypots operate passively, collecting data without real-time monitoring. Even when live observation occurs, deeper analysis often happens after the attack, when the system can be safely examined without risking real assets.
Collecting and analyzing data on attack behavior
Honeypots provide valuable data for profiling attackers and understanding threats, including:
- Attacker origin indicators: IP addresses, geolocation patterns, virtual private network (VPN) or The Onion Router (Tor) usage, and session timing.
- Operational patterns: Techniques reused across sessions, attacker sophistication, and methods for exploiting vulnerabilities.
- Attack intent: Priorities and goals inferred from behavior while in the network.
- Threat level assessment: Potential impact and ease of exploitation.
This intelligence helps security teams improve their defenses, anticipate future attacks, and build profiles of attacker behavior for ongoing threat mitigation.
What are honeypots used for?
Honeypots are primarily used to understand how attackers operate, which vulnerabilities they target, and how security systems can improve using that insight. One of their most important roles is supporting threat intelligence efforts.
In addition to revealing technical attack methods, honeypots can sometimes uncover broader patterns in attacker behavior, providing insights into trends, motivations, or emerging threats that may reflect real-world events. Through these observations, researchers gain a clearer understanding of how modern cyberattacks unfold and how they evolve over time.
How do honeypots improve threat intelligence?
The collected data from honeypots can be turned into actionable knowledge that improves overall security posture in the following ways:
- Data enrichment and correlation: Honeypot logs are combined with security information and event management (SIEM), intrusion detection and prevention systems (IDS/IPS), threat feeds, malware reports, and other intelligence sources. This helps identify patterns, trends, and potential attack campaigns.
- Analysis and profiling: Security teams analyze attacker behavior and tactics at a higher level, mapping attack chains, assessing sophistication, and studying malware propagation methods.
- Actionable threat intelligence: Insights are converted into indicators of compromise (IP addresses, domains, and malware hashes), detection rules, alerts for unusual activity, and guidance for improving defenses.
- Operational feedback loop: Teams integrate this intelligence into security operations by updating monitoring tools, enhancing staff training, and refining network segmentation and firewall rules.
Over time, this process can improve overall resilience and response to both known and emerging threats.
Types of honeypots
Honeypots come in many forms, ranging from fully simulated traps in controlled environments to decoys deployed in real systems that detect threats and divert attackers away from valuable assets in real time.
Purpose-based classification
Based on their purpose, honeypots are either production or research honeypots.
Production honeypots
Production honeypots exist mainly to detect malicious activity and divert attackers away from legitimate systems, offering early warnings of an intrusion.
Their goal is to distract the attacker long enough that the IT team can identify the threat, contain the malware, and protect the legitimate product on the network. However, that might not always be the case, as attackers don’t always linger for too long.
While some production honeypots can be complex, most have a simple design, so they typically won’t hold a skilled attacker’s attention for too long. But they don’t need to; their value lies in quick intrusion detection with minimal risks.
Research honeypots
Research honeypots are used by governments, research organizations, security vendors, large enterprises, and academic institutions to study cybercriminals in-depth. They collect and catalog detailed data on malware and exploits used, entry points accessed, metadata (like IP and geolocation data), and attack patterns.
Unlike honeypots in production environments, research honeypots are usually in controlled environments. They typically don’t involve real users, production systems, or sensitive data, although some are intentionally deployed on live networks to observe real-world attacks.
Research honeypots are generally more complex, often simulating entire databases, servers, and website applications. A more realistic simulation lets researchers collect a variety of useful data.
| Data collected by research honeypots | Use |
| Malware samples | New malware strains observed in the wild let researchers study their mechanisms, reverse-engineer payloads, and develop security patches and detection signatures. |
| Infiltration tactics | Understanding why attackers target a certain system, how they gain access, and what methods they use helps profile emerging threats and create a proactive defense. |
| Custom scripts and tools | Capturing custom-made scripts and tools is critical to keeping up with how cybercriminals adapt and refine their techniques. |
| Phishing and spam tactics | Analyzing phishing emails and spam campaigns captured by email and web honeypots helps organizations improve employee training, email filtering, and social engineering defenses. |
Complexity-based classification
Honeypots can range from simple to highly complex, depending on their intended purpose.
Low-interaction honeypots
Low-interaction honeypots use fewer resources, simulate fewer processes and services, and are generally easier to spot. However, they’re easy to maintain and can collect useful data on attacks. Companies use them as early warning systems and to lure attackers away from valuable information.
Even if an attacker escapes the honeypot, the risk is limited, since it doesn’t run a full operating system and exposes only a few services and processes.
Many production honeypots are low-interaction by design. That said, in some cases, companies may choose to invest more in a sophisticated production honeypot to delay attackers and give security teams more time to respond.
High-interaction honeypots
High-interaction honeypots are more resource-intensive and simulate a large number of services and processes. Their primary goal is to engage cybercriminals for longer and occupy their time for one of two reasons:
- To protect high-value targets in production environments.
- To collect more in-depth data in a simulated environment.
Compared to low-interaction honeypots, they collect much more data on attackers, like specific malware used, custom scripts, and precise movements within a network. This makes them more useful in building mitigation strategies.
However, this advantage comes with a significant risk in production environments. Because they run real operating systems, services, and applications, these honeypots may allow actors to attack other targets on the network if compromised.
That’s why high-interaction honeypot security must be sufficiently advanced to prevent this. Most of these honeypots have a “honeywall” surrounding them that prevents lateral movement from criminals who escape the honeypot. This isn’t universal, as some setups rely on strict virtual local area network (VLAN) isolation instead, where the honeypot lives on its own separate network so it can’t interact with real systems.
Specialized honeypot examples
Because cybercrime affects many industries and attack methods differ by target and environment, honeypots are designed for various use cases. Below, you’ll find the most common types of specialized honeypots.
Email and spam traps
Email honeypots are simple decoy email addresses hidden on a website. Generally, only automated email harvesters used by spammers tend to find them, so incoming messages are typically spam.
Organizations can analyze these messages to identify spam campaigns, sender patterns, and emerging spamming techniques, and in some cases block or flag associated infrastructure. By diverting spam to decoy addresses, these honeypots help protect legitimate email accounts.
However, email honeypots aren’t well-suited for detecting targeted attacks such as spear phishing, which usually rely on curated address lists rather than automated harvesting.
Malware honeypots
A malware honeypot is designed to emulate vulnerable systems, services, or endpoints to capture malware and observe how it behaves once it gains access.
In this controlled environment, researchers can analyze malware behavior, infiltration and propagation methods, and vulnerabilities in the simulated software or API.
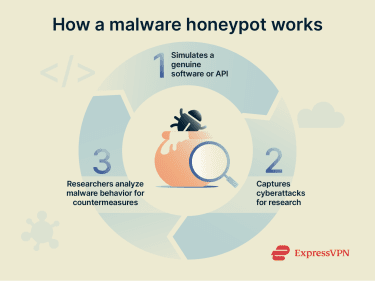
One example is the honeypot designed by SophosLabs, the threat research and intelligence division of the cybersecurity company Sophos, to study the Chalubo botnet. The malware infected devices (particularly computers running Linux) and built a botnet to launch distributed denial-of-service (DDoS) attacks. Using this honeypot, researchers were able to study the malware and develop countermeasures for the strain.
Decoy databases
Decoy databases contain fake data designed to lure cybercriminals, like dummy banking information, credit card details, or credentials.
Researchers intentionally make these databases vulnerable in a controlled environment to study credential theft and misuse, as well as brute-force attempts. The insights obtained can help strengthen database security, improve firewalls, and protect legitimate production databases in real-world attacks.
Spider honeypots
Spider honeypots are designed to attract web crawlers (also known as spiders) and data scrapers using decoy webpages and links. While they won’t always distinguish between malicious and legitimate automated crawlers without extra filtering, the honeypot pages are inaccessible through normal navigation, so most traffic to them is likely spam.
Organizations use spider honeypots to:
- Identify non-human traffic that may impact performance metrics.
- Develop strategies to block malicious data scrapers and ad harvesting.
There’s also a spider honeypot variant called a tar pit, which is designed to keep automated crawlers engaged on decoy pages for extended periods, wasting their resources and slowing down unwanted activity.
ICS and IoT honeypots
ICS honeypots are specialized decoys designed to simulate industrial environments like supervisory control and data acquisition (SCADA) networks, programmable logic controllers (PLCs), and other operational technology components. In some cases, they also emulate Industrial IoT (IIoT) devices used in these environments.
Security teams use these honeypots to study targeted attacks on industrial networks, including sabotage, disruption, and ransomware activity. They can reveal attacks against industrial protocols, such as:
- Modbus: Exploitation of unauthenticated commands, replay attacks, or insecure configurations.
- Distributed Network Protocol version 3 (DNP3): Abuse of protocol-specific weaknesses to gain unauthorized access or manipulate control data.
Monitoring this activity helps organizations understand how threat actors target ICS and IoT systems and develop appropriate detection and response strategies.
Client honeypots
Client honeypots lure cybercriminals by pretending to be a client (device or application that accesses a server). They actively seek out malicious networks and expose them to security teams.
These honeypots typically run in virtualized environments with containment procedures in place, which helps limit risk to researchers.
Honeybots
Honeybots are an emerging class of honeypots designed to interact more dynamically with attackers. Rather than passively storing data, they simulate realistic system responses to appear legitimate and engage attackers for longer.
Recent research has explored the use of machine learning (ML) and large language models (LLMs) to enhance this realism, making honeypots respond more convincingly to commands or interactions. It’s still largely experimental, but these developments point toward more adaptive and intelligent honeypot systems in the future.
Benefits and risks of using honeypots
While honeypots can provide valuable insight into an organization’s security posture, they also introduce trade-offs. Key considerations include:
- Visibility vs. exposure: Honeypots reveal attacker behavior, but attackers may learn to recognize them, reducing effectiveness.
- Cost vs. value: Deployment and maintenance require resources, but the intelligence gained can help prevent breaches and refine defenses.
- Simplicity vs. insight: Low-interaction honeypots are low-risk and cost-effective but offer less detailed data than high-interaction setups.
- False positives vs. signal clarity: Although false positives are rare, occasional legitimate interactions can skew observations.
- Engagement vs. risk: High-interaction honeypots provide richer data but increase risk if attackers attempt lateral movement.
- Training vs. operational overhead: While they offer hands-on learning for security teams, honeypots require ongoing monitoring and analysis.
- Proactive defense vs. limited coverage: Honeypots detect attacks and strengthen security indirectly but can’t replace comprehensive security controls.
- Internal vs. external threat detection: Honeypots expose malicious activity directed at them but can’t detect attacks elsewhere on the network.
Threat actors can also detect the use of honeypots and manipulate them to their advantage. For example, they may use techniques such as fingerprinting, which tricks a honeypot into interacting with intentionally invalid requests to reveal its nature.
AI-generated decoy classifiers also use pattern recognition to identify deception signals commonly associated with honeypots.
Overall, however, honeypots are well worth the trade-offs if implemented properly and isolated from production environments. They provide a glimpse into the real-world nature of attacks and exploits and are critical for informing cybersecurity responses to emerging threats.
Do honeypots protect your network or data?
For all their usefulness, can honeypots protect your network or data directly? Not exactly, as most of their benefits are indirect. Here’s why.
Why honeypots don’t block attacks
A honeypot doesn’t block attacks directly. It can only steer cybercriminals away from sensitive data and valuable services. What’s more, honeypots are reactive, not preventative: they collect intelligence when an attack is underway, so they can’t prevent it from happening or patch vulnerabilities.
Honeypots are also designed to be vulnerable to infiltration so that threat actors fall for the trap and expose their attack methods, malware, and identifiable metadata to the IT team.
Relying exclusively or primarily on honeypots to protect a system is a bad idea: they only detect threat actors that interact with them, so blind spots in security would become a serious problem. Essentially, they're designed for research, detection, and threat analysis in controlled or enterprise environments, not for endpoint protection.
How honeypots complement other security tools
Honeypots should be used in conjunction with other security tools like antivirus solutions, endpoint detection systems (EDS), and security information and SIEM tools. While traditional defenses focus on blocking known threats or detecting suspicious behavior, honeypots provide a controlled environment where malicious activity can be observed without risking critical assets.
Because honeypots have no legitimate users, any interaction with them is inherently suspicious. This makes the data they generate especially valuable when fed into SIEM and detection platforms, where it can improve the accuracy of alerts and reduce false positives. Insights from honeypot activity can also be used to fine-tune endpoint detection rules and enrich threat intelligence feeds.
Used together, these tools create a layered defense: preventive controls reduce attack surface, detection systems monitor for abuse, and honeypots add insight into attacker behavior. This all helps security teams respond faster and adapt defenses based on real-world attack techniques rather than assumptions.
FAQ: Common questions about honeypots
Are honeypots legal to use?
Honeypots are generally legal, but deploying a defensive honeypot can raise legal and privacy considerations, depending on how it’s implemented and what data it collects. In particular, honeypots that log network traffic, commands, or identifiers may capture personal or sensitive information, which can trigger data protection obligations in some jurisdictions.
Can attackers detect a honeypot?
Yes, attackers can sometimes detect honeypots, especially low-interaction deployments that don’t fully replicate a real operating system or environment. Inconsistencies such as sparse or artificial system logs, unrealistic uptime, or services that behave differently than expected can break the illusion. More sophisticated attackers may also probe timing, resource usage, or system responses to determine whether they’re interacting with a decoy.
How effective are honeypots in detecting threats?
Honeypots are effective at detecting threats that interact with them. After all, one of the fundamental roles of a honeypot is early warning of malicious interactions. Their biggest drawback is their inability to detect cybercriminals who avoid the honeypot, meaning they must be used alongside other security measures for full coverage.
Can honeypots help detect insider threats?
Yes, honeypots can detect insider threats because any access attempts on them are typically suspicious. Organizations can deploy internal honeypots within their networks to monitor for unauthorized access, policy violations, or malicious activity by employees, contractors, or other insiders. Proper monitoring and analysis of these interactions help distinguish genuine threats from benign anomalies.
How is a honeypot different from an IDS or IPS?
Honeypots often integrate with intrusion detection systems (IDS) to analyze activity and generate alerts. The IDS analyzes relevant data gathered by the honeypot (like logs and metrics), identifies attack patterns, and alerts security personnel. An intrusion prevention system (IPS), on the other hand, takes active action against attackers, blocking or preventing attacks on a network. It’s a proactive layer of defense, while a honeypot is a research and detection tool.
What’s the difference between a honeypot and a honeynet?
A honeypot is a single decoy system, while a honeynet is made up of multiple interconnected honeypots. The goal of a honeynet is to mimic a genuine network, with decoy workstations, servers, routers, and network segments. Honeynets offer a broader view of an attacker’s behavior throughout the network, like how they move between multiple databases and the exploits they use.
Are honeypots a replacement for firewalls or antivirus tools?
No, honeypots are not replacements for firewalls, antivirus software, or other core security controls. They can’t protect a network or prevent attacks directly; their primary function is to observe attacker behavior and collect intelligence. Relying solely on honeypots can create a false sense of security.
Can honeypots generate false positives?
Yes, honeypots can generate false positives, but it’s uncommon. Because honeypots are generally isolated and not used by legitimate users or systems, most interactions are suspicious or malicious. However, false positives can occur if automated scripts, misconfigured systems, or benign scanners inadvertently access the honeypot. These false alarms can skew observations or trigger unnecessary alerts, so it’s important to interpret honeypot data carefully.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN