Ultimate guide to mobile security for iPhone and Android devices


While most of us know to be vigilant when it comes to the security of our desktops and laptops—installing antivirus programs and regularly scheduling system scans—our mobile phones often aren’t afforded the same level of scrutiny. But as we rely on our phones more than ever before, mobile security has become essential in protecting our privacy.
In this guide, we’ll go into detail about mobile security tips, tricks, and best practices. Read on to secure your phone from the most determined of hackers.
Part 1: Essential mobile safety tips
Part 2: The security risks of mobile Wi-Fi networks
Part 3: How to guard your mobile apps and prevent data theft
Part 4: How charging your cell phone exposes it to risks
Part 5: The hidden risks of your SIM card and SMS messages
Part 6: Why it’s essential to lock your device
Part 7: The complete mobile security guide infographic
Part 1: Essential mobile security tips
Today’s iPhones, iPads, and Android devices are so powerful and advanced that owning one is like having a mini PC readily available. While that’s enabled greater connectivity, productivity, and social networking, it’s also meant that a wealth of data is stored in our pockets, susceptible to hackers and other security vulnerabilities.
Phones and tablets are exposed to unsecured Wi-Fi networks and always connected to a distant cellular antenna. They can also be physically stolen. That’s why it’s so important to adhere to security best practices. Here are the ones we recommend.
Activate a screen lock
Given that your mobile device has your private conversations, contacts, credit card details, and emails, it’s a good idea to make it as impenetrable as possible.
The first security layer is generally a screen lock. A screen lock needs a passcode or pattern for unlocking to qualify as a security measure. It should also automatically activate after a period of inactivity. The default setting for most phones is 30 seconds, but the length of time can be customized according to your liking.
We suggest you keep the lowest possible time duration before your screen lock kicks in to minimize the chance of your phone’s contents being accessible if you, say, walk away from your desk.
Always lock your phone manually when you are placing it away from you or someone suspicious is approaching.
Many devices also have fingerprint scanners and facial recognition features. Be careful of biometrics as a security option. While more convenient than passcodes, they can be fooled with the right equipment. And if your fingerprint becomes public information, you won’t be able to change it.
Encrypt your data
Public Wi-Fi networks may not be encrypted and may collect your personal information for profit. Navigate to websites using your bookmarks rather than hyperlinks, make sure the connection is protected with TLS (as indicated by a lock icon in your browser window), and use Tor or a VPN.
Be careful about which apps can access your data
Use reputable apps and review their permissions regularly to make sure they only have access to the data that you expect them to have.
As a basic rule, only download apps from reputable sources, such as Google Play, F-Droid, or the iOS App Store. Android phones can be loaded with third-party apps through SDK kits, but we urge you to be very careful when taking this step. Such third-party apps haven't been vetted by Google. Always verify that the application file comes from a reputable source and hasn’t been tampered with.
At the same time, make sure you carefully examine permissions for each app that you download. An antivirus app doesn’t need access to your photos or microphone, for example. If you believe you may have overlooked app permissions in the past, be sure to go back to your app settings and conduct a forensic audit.
Ever so often, it’s also worthwhile to do a spring cleaning of your apps. Our phones tend to get cluttered due to a propensity to download apps that we rarely use. We recommend you delete the ones that haven’t been opened in a while.
Protect against malware
Malware, or malicious software that seeks to do damage or steal your data for personal or political gain, has always been a part of the internet. Mobile malware often comes disguised as clones of popular and trusted apps. It might then steal account credentials, install other apps without permission, or perform some other unwanted action.
With 230,000 new malware strains appearing every day, it’s impossible to make a comprehensive list of all types of malware.
Be careful about which apps you install and who has access to your phone. If you’re in doubt, perform a factory reset to get your phone’s operating system back to its original state.
At the minimum, look out for apps that don’t have a critical mass of ratings on the App or Play Store. It might be an indication they have been newly uploaded and not have the same security features as well-established apps. You can also visit the official sites of the developers of the app you are looking for and follow the links from there.
Don’t leave Bluetooth on
Bluetooth is an often-overlooked attack vector for phones and tablets. It is a potential security flaw as it allows remote connections to your phone. It may also allow others to track you, for example, as you wander around a mall or office. Only turn on Bluetooth when you need to. This helps save battery power, too!
Don’t root your device
Rooting or jailbreaking your phone removes default security features, which may allow apps to access private data such as your SIM card details and which antennas you connect to.
While it’s tempting to root your phone in order to get access to apps outside the official stores and play around with your device as a developer would, we don’t recommend this for ordinary users. If you do need to root a device for whatever reason, don’t keep any personal data on the device.
Use antivirus software
On any modern computing device, you should install antivirus software. Keeping your phones updated at all times is also an important security best practice that fixes bugs, guards against zero-day exploits, and secures your personal information. In fact, we believe you should set your devices to update automatically so that your apps are always patched and systems run as normal.
Be careful with automatic backups
Most phones come with a backup function included, either provided by the manufacturer or an external provider. This is convenient but can also open you up to additional privacy and security issues.
Be selective in what you back up. Some data, such as personal messages, app data, and social media posts, might already exist in the cloud and does not need to be backed up separately. When backing up encrypted messages, be aware that they will not be encrypted in your automatic backup. This may compromise the safety of you or your contacts.
Offline backups, such as using your personal computer or software like iTunes, can be encrypted. Make sure to choose a proper encryption passcode. Only if you are confident that the backup is properly encrypted may you upload it to cloud storage.
As they say, prevention is better than cure.
A little bit of housekeeping can save you from the very real threat of data loss or pilferage. We’re sure that’s the last thing you want.
Part 2: The security threats of mobile Wi-Fi networks

Public Wi-Fi is pretty great, but it’s far from secure and rarely private. Understanding what information you share with whom helps you use Wi-Fi more efficiently, reduces your risk of cyberattacks, and lets you configure your device according to your preferences.
MAC addresses can be used to identify your device
Whenever you connect to a Wi-Fi hotspot, your phone gives away its MAC (media access control) address. Such addresses are included in each network interface, making it possible to identify you as a repeat guest, even across separate networks.
Starting with iOS 8, Apple devices have begun broadcasting a fake, randomized MAC address that makes the practice of tracing users more difficult. This, however, still identifies your device as an iOS device, and the practice is only applied when looking for new networks. When you connect to your known network your real MAC address is broadcasted.
The operating system TAILS randomizes MAC addresses by default. Software like this makes it possible to connect to several Wi-Fi hotspots repeatedly without being tracked.
MAC addresses can also be used to increase the security of your home or office Wi-Fi. You start by identifying the devices that you permit on your network by their MAC address and then white list those devices, essentially blocking all unknown devices from your network.
Another method of ensuring privacy is to change the name of your phone by opening the settings menu. That’s because your device will likely transmit its name to the Wi-Fi access point it’s connected to. By default, this is often either a description of the phone, the name you entered when you set the phone up, or a combination of the two, such as “Patricia’s iPhone.”
Wi-Fi routers can read your data as it passes through
After you’ve connected to a Wi-Fi network, it’s important to keep in mind that the router can read all the data transmitted through it. This always includes the destination IP of all your traffic, allowing system administrators to get a comprehensive look into what services each device is using and which sites everyone on the network is visiting.
Unencrypted connections (those that don’t have a lock icon in the address bar) allow network operators to view everything you are viewing on this site and all the information you transmit to it, whether it’s uploading pictures or filling out forms.
This includes emails, chats, passwords, and other personal information. It’s important to always check for Transport Layer Security (TLS) and always refrain from transmitting any sensitive information via an unencrypted connection.
Using a VPN or Tor eliminates the network provider’s ability to view the contents of your traffic (i.e., the sites you visit or the apps you use), but they could still guesstimate the amount of data consumed.
A VPN is more robust because it encrypts all traffic going to and from your device, including third-party apps. Tor, however, only encrypts your browser traffic.
Unencrypted Wi-Fi networks expose your traffic to everyone
Wi-Fi networks utilize several protocols to encrypt traffic flowing to and from your devices. Unfortunately, not all of them are secure, and many don’t use encryption at all.
For example, remember the time when you connected to a Wi-Fi access point without the need for a password? While this may have saved you some time, the downside is that such access points aren’t encrypted at all.
This means your online activities could be intercepted by malicious entities through man-in-the-middle attacks and other strategies. Unsecured networks are the strongest security risk you might face in a public Wi-Fi setting, as it exposes you to attacks not just from the router but from nearby devices too. Wi-Fi networks that present a log-in screen after you connect to the router are equally at risk.
This risk is particularly applicable to public and free Wi-Fi access points, such as parks, airports, or coffee shops. When setting up your own Wi-Fi—no matter if you’re at home or in a public location—remember to always set a password and choose a secure protocol, preferably WPA2.
Using a VPN will protect you from this threat, and on unencrypted Wi-Fi networks, it becomes especially important to use them.
Wi-Fi networks can guess your location within a building
System administrators can use the signal strength of your device along with multiple access points in relation to other devices on the network to arrive at an accurate estimate of where you might be located.
Not only can the data be used to track your movements inside a building or in a public space, but this information can also be matched with other data that administrators can glean from your connection, such as purchase records at stores or CCTV feeds, giving them an accurate profile of your behavior.
With access to the right information, trained minds can connect an IP to a credit card number or even a face. To defend against that is difficult, especially if you spend a lot of time on the network.
Ideally, we recommend that you always try to blend in with the crowd. Don’t be the last to leave in a cafe, and try to sit at a table that’s in the middle of everyone else. It is also in your best interest to find spots that aren’t under video surveillance, but that’s not easy.
Automatically connecting to a network can be dangerous
If your Wi-Fi is set to connect automatically, then you’re forcing your phone to constantly monitor radio waves to find those networks it has connected to before and make a fresh connection. But the mechanism your phone uses to identify these networks is the network’s name, and that can easily be spoofed.
There is no guarantee that a Wi-Fi network called “Starbucks” is actually operated by Starbucks. In fact, anyone can easily set up a malicious network of that name, making it so that all devices that usually connect to Starbucks Wi-Fi will automatically connect when within range.
Once connected, the device reveals its name to the router, and some of the services you use might automatically activate. If unencrypted, this information can be read by the operator of the Wi-Fi network and others around you.
We recommend you keep your Wi-Fi setting off and only connect when you’re actively looking for one.
Part 3: How to guard your mobile apps and prevent data theft

When it comes to your devices, the information stored on them is only as secure as the apps installed.
As explained above, make it a point to only download apps from their official sources. Ideally, those are F-Droid, Google Play, and the Apple App Store, and any other source you have carefully verified yourself.
Alternatively, advanced users can build the applications themselves if the code is open source, or if you can find and verify installation packages directly from the developers.
App permissions
Both iOS and Android give you the option to be selective about the permissions you grant your apps. Hence, you can restrict access to things like the GPS, camera, microphone, and photo reel.
Make good use of that! Be skeptical with what permissions applications ask for and only grant the ones that you think are absolutely necessary. For example, a messaging app does not always need to know your location, and a payment app does not always need access to your pictures. A flashlight app should not need to ask for access to anything at all.
Keep in mind that most startups and their apps are incredibly data hungry, and selling user data might be the only or most promising monetization strategy for a free app or service. So be careful with what apps you download as they might be looking to profit off you.
It’s in your best interest to occasionally go through the settings of your phone to review what apps you have installed and what permissions they have. If you feel some of them are excessive, you can go ahead and withdraw these permissions or delete the app entirely.
Warning signals your apps might be spying on you
Major red flags include excessive battery drainage, network congestion, or memory usage. While these don’t necessarily mean you are being spied on, they’re certainly side effects of spy applications.
Use both your intuition and the in-built features of your phone to monitor these indicators. Applications that promise to help you optimize your battery, your network, or memory usage are rarely reliable and add an increased risk of data theft to your system.
Does your app encrypt your data?
It’s not straightforward to determine how apps handle your data in the background without access to advanced analytical tools. When dealing with any application, especially one without much reputation, be careful with any information you enter, especially personal details such as your social security number or payment details.
Even if you take all the necessary precautions, there’s always the risk that app developers won’t store your data in the cloud properly. Carefully read the Terms of Service of providers, and favor services and apps that explicitly promise to uphold your privacy. Choose a good password, ideally through a password manager (also have a look at ExpressVPN’s Random Password Generator).
It’s extremely important to make sure that your password is stored in hashed form on the server. A good indicator for an app that does not follow this basic procedure is if you are limited in the length of your password or restricted from using special characters.
Another thing to look out for is whether data in transit is encrypted by HTTPS. But unlike in your browser, it might not be possible for you to manually verify if the connection is encrypted or for you to verify whether certificates are properly checked. Instead, we have to rely on the promises of the app developers, the policies of their platforms (the Apple app store, for example, requires that new apps use HTTPS by default), and the competency of their developers.
To judge the reliability of an application, have a look at its website and how it is presented in the App Store. Is the application updated regularly? Is it well documented, with change logs available?
Two-factor authentication
In addition to your password, you can also use two-factor authentication (2FA) to secure your device. This is a second password that is only valid for a short time. It can be generated on your phone, an external device, or sent to you via text message or email.
It is safest when the code is generated on your phone or an external device, although this can create headaches when these devices are lost.
When the code is sent to you via text message, it is important to note that this information could be intercepted, possibly by someone nearby or another application on your phone. That’s why the best way to use two-factor authentication is through a hardware device using the FIDO U2F standard. If you do not have such a device, you can use an app like Google Authenticator or Duo.
Part 4: How charging your cell phone exposes it to risks
Smartphones use the same physical port to charge their batteries as well as download data. This helps users as fewer cables are needed to accomplish more tasks, but it does elevate the security risk slightly.
For instance, we don’t think twice before plugging our USB cables into the outlets found in malls, train stations, buses, and airplanes. It’s possible that we may inadvertently connect our phone to a computer we do not trust, which in turn may attempt to access our device without our consent.
Airplanes, for example, allow you to charge your devices on board, but the plane’s onboard computer will often try to access your device. This is great if you want to play media on the screen on the seat in front of you, but can we really trust these computers?
To protect yourself, carry your own charger with you and plug it into a regular electrical outlet instead of a USB outlet. You can also find a cable that only carries the electricity, but no data. You can also avail “USB condoms,” which will ensure that there’s no data transmission during the charging cycle.
The hidden risks of your SIM card and SMS messages
Your Subscriber Identity Module (SIM) card opens up a few unknown security vulnerabilities on your phone.
What’s even more devastating is that the SIM card makes it very easy for you to be tracked across the globe. Let’s take a closer look on how that happens:
Phone tracking
As long as your phone has a valid SIM card inserted, it will always try to connect to a base station. Once connected, it will continue to send signals to base stations near you to ensure a stable connection in case you receive a message or a phone call. Removing the SIM card from your phone will not guarantee you anonymity. Most phones will maintain a connection even without a SIM card, for example to be able to make emergency calls. Enabling airplane mode can help, but only physically removing the battery can guarantee that you aren’t trackable through your device.
Mobile phone companies can track what base station you’re connected to and compare that with the strength of the signal to triangulate your location with a fair degree of precision. All it takes it having your phone on and a SIM card inserted. They can also use indicators like your speed and location to deduce whether you’re, say, in a moving vehicle or high up a skyscraper.
Don’t assume that the information gathered is kept private by telecommunication companies. A number of providers fail to secure their systems against intruders, making geo-location almost public knowledge. In fact, some providers have even gone so far as selling their users’ location to advertisers.
What’s more, they can and often do share this information with law enforcement. But in order to track you more precisely, law enforcement will need a device similar to a Stingray.
What are Stingrays?
Stingrays are a popular kind of IMSI-catcher (International Mobile Subscriber Identity). These devices are about the size of a shoe box and can be attached to any vehicle, such as a car or airplane, or even carried in a backpack.
Stingrays work for all devices connected to the GSM network. While Stingrays are not as effective on 3G or 4G networks, they can always retrieve a subject’s cell phone number and location. By tricking the subject into connecting to a less secure 2G connection, they might also be able to intercept phone calls or SMS.
While each phone has to authenticate itself to the base station of the cell phone provider, this is not the case for the other way around. As a result of this commonly known vulnerability in the GSM network, anybody with the resources (Stingrays cost about 16,000 to 125,000 USD per piece) can imitate a base station, with the result that every phone nearby will connect to it unknowingly.
This allows the operator of a Stingray to get a list of all the identifiers of mobile phones nearby. In some cases it can also allow them to listen to all phone conversations and text messages made by the victim, in what is called a man-in-the-middle attack.
We do not know if spy agencies or law enforcement bodies can easily apply similar functionality to read and intercept mobile data as well, but it is certainly within the realms of possibility.
Cracking the encryption on the fly is very difficult, but it’s not unreasonable to believe that a large enough spy agency has already stolen the keys or requested them through a national security letter.
Stingrays are used covertly and their use is so secretive it’s often not even uncovered in court. These devices are tools of mass surveillance, and as such are rarely authorized by courts in investigations. But as their use has become more widespread, the public has become increasingly aware of Stingrays and how they work.
When a law enforcement agency, criminal, or spy has multiple devices at their disposal, they can use them simultaneously to calculate the locations of their suspects’ phones. A similar result can be achieved by moving the devices around, like in a small airplane.
Part 5: How to evade location tracking through your SIM

While flight mode can help, the only way to completely evade tracking is to remove your phone’s battery. For advanced users, there is the possibility to run special software on your phone that detects Stingrays and shuts your phone down if you so choose.
- However, this software is experimental and not thoroughly tested. Using public Wi-Fi, VPNs, and VoIP services paid for with Bitcoin are good alternatives to outgoing calls. Incoming calls over VoIP are less private due to the need to subscribe, but can still be an effective tool if the main goal is to hide your location. It’s important to add that such calls are never encrypted and therefore may be easily wiretapped.
Encrypted calls are possible with software like Signal and FaceTime, but in order to work they require both parties to use the software.
Another approach is to frequently switch SIM cards. While this does not make tracking impossible, it reduces the amount of information snoops are able to gather. It is important, however, that SIM cards aren’t switched too quickly. It might be possible to link two numbers together simply by observing that they are never turned on at the same time.
Another hurdle with this strategy is that the SIM cards need to be purchased independently from each other, at separate stores, and paid for with cash. If they are inserted into the same phone, there might be other serial numbers and identifiers that allow the mobile phone company or spy agency to link them together.
To give yourself the best chance to evade location tracking through SIM cards, make sure that both your SIM cards are purchased from separate providers with cash, are unregistered or registered with separate fake names, and are used with separate devices. They should never be used in the same area, and you must make sure both devices are switched off when traveling between locations.
Hacking a sim card
Unfortunately, the biggest security nightmare isn't the location trackers but the SIM card itself. Essentially, its module is a small computer that comes out of the box, can run and respond to foreign code, and is remotely accessible.
The largest known hack that exploited this problematic architecture was uncovered in 2013, when IT analysts discovered that 750 million cell phones were using obsolete cyphers that could easily be figured out by an attacker.
With this key, the attacker could download new software onto the SIM module, send text messages to contacts in the contact book, or change the user’s voicemail password.
If you have a SIM card issued before 2013, there is about a 10% chance it is still affected by this problem.
But these encryption keys can be compromised in other ways too, especially by well-funded state actors.
As part of the Snowden revelations, The Intercept revealed how American and British intelligence agencies stole the encryption keys of billions of SIM cards produced by Gemalto, a Dutch company that manufactures SIM cards for over 450 telecommunication firms all over the world. These keys would have allowed the intelligence agencies to decrypt intercepted traffic through a more advanced and undetectable version of a Stingray.
SMS messages and contacts
Even if you have full disk encryption set up, your phone might still store text messages and contact details on the SIM card itself, leaving your info unencrypted and accessible to anyone who can get their hands on it.
SIM cloning / SIM card swapping
It is difficult to clone your SIM card, but not impossible. If an attacker has physical access to your SIM card, they might be able to extract the private key from it. Using a reader between your SIM card and your phone, they might also execute a man-in-the-middle attack, for example.
The easiest way to clone your SIM card would be to impersonate the user and approach the service provider directly by asking them for a copy. Some service providers easily provide secondary or replacement SIMs on the spot or via mail with little identification.
This means that you put a lot of trust in your mobile service provider. If someone is able to impersonate you to your service provider and get access to a secondary SIM, they are able to receive text messages and phone calls intended for you, and make phone calls and text messages in your name (and on your bill).
This can have important security ramifications, especially if your two-factor authentication solution delivers such codes over text message.
This technique is also known as SIM card swapping and made headlines after the personal account of Twitter CEO Jack Dorsey was hacked in August 2019.
The ramifications of SIM card swapping are severe—especially when you consider that there’s little you can do to stop it. However, the best way to detect it is if you mysteriously lose all cellphone service and it stubbornly refuses to come back even after you restart your device. That shows something’s amiss and it’s not from your end.
Simjacking
A new SIM card security vulnerability discovered in September 2019 came as a result of malicious text messages that incorporated spyware code. Once a user clicked on the text, the code would spring into action and allow hackers to spy on their calls, messages, and location data.
The vulnerability used a piece of software called the S@T browser, part of the SIM application toolkit. While this browser isn’t commonly used in the developed world, it’s still active in countries across the Middle East, North Africa, and Eastern Europe.
Mobile phone operators were the target of this attack, which was attributed to a private firm operating on the behest of government agencies.
Part 6: Why it’s essential to lock your device
Setting a sufficiently secure password for your lockscreen is the first layer of security and one that you must take very seriously. This will make it more difficult for others to access your phone without your consent.
Contrary to popular perception, using your fingerprint to unlock your device does little to increase your security. A fingerprint can easily be cloned from as little as a picture of your thumb and used to unlock your phone. And while you cannot legally be forced to reveal your password in most jurisdictions, taking your fingerprint to unlock your phone without your consent is perfectly legal in Western liberal democracies.
Encrypt your drive
Apple started to encrypt hard drives by default since iOS 8. This greatly improves protection for the owner from arbitrary searches and from having your personal data abused after losing the device.
Android also offers a feature for the user to encrypt their drive; however, this has to be activated and isn’t enabled by default.
You can find the option to encrypt your device in your settings.
While not particularly easy, it is possible to extract your personal information from your phone without your consent if you do not encrypt your drive. Tech companies have been caught assisting law enforcement agencies to unlock devices too.
Choose a good password
While both Apple and Google take measures to protect your encrypted data from hackers by limiting the number of times a wrong password can be entered, or by erasing the drive after a few failed attempts, the best form of protection remains a strong password.
Pick a password that has at least 12 characters, or use our random password generator. Also be sure to add a mix of numbers as well as uppercase and lowercase characters. Alternatively, use Diceware to generate a password that consists of four to five words.
Part 7: The complete mobile security guide infographic
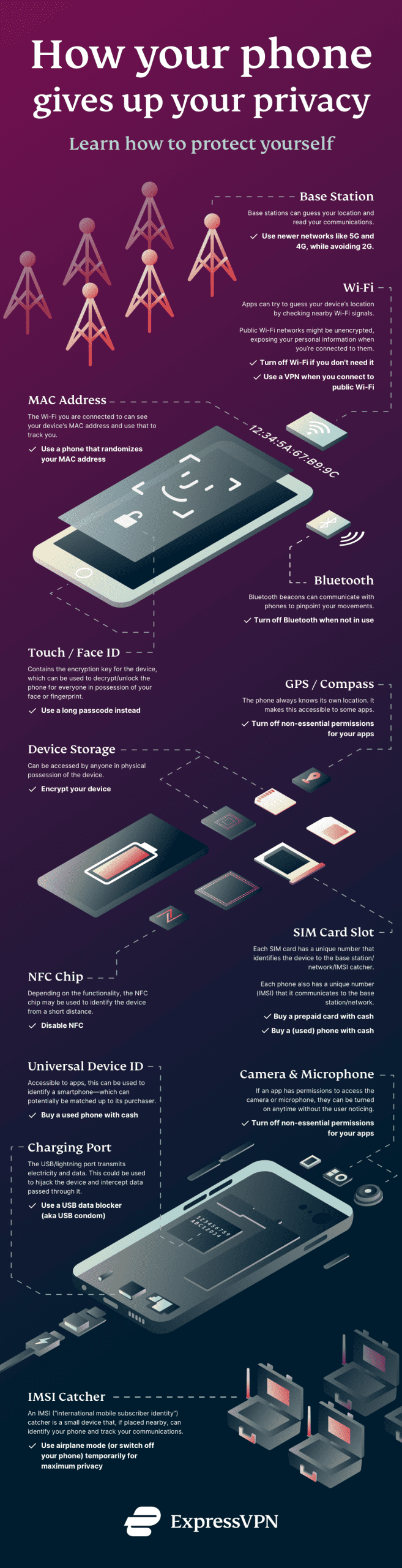
We've created this graphic that comprehensively shows how your phone might be giving away your details.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN




Comments
A question - I purchased a light bulb camera that connects to my home WiFi. When setting up the camera to connect to my WiFi the app asks for my WiFi password. If I do this, does the app have the password to my WiFi and is this a security risk? The camera is made in China and it appears the app is Chinese as well "Yllot" (on the Apps store). Thank you.