What is a watering hole attack, and how do you stop it?
Watering hole attacks are a type of cyberattack in which attackers compromise a legitimate and trusted website to deliver malware or collect sensitive information. These sites are usually chosen because they’re regularly visited by a specific group, such as employees, professionals, or members of a shared community.
The name, watering hole attack, comes from a hunting strategy seen in nature. Some predators wait where they know prey will visit, such as a watering hole. In a watering hole attack, the compromised website plays the same role. Instead of pursuing individual victims, attackers wait for them to arrive through normal, routine browsing.
These attacks are effective because users typically trust the sites they visit as part of their daily routine. By compromising a familiar website, attackers reduce the likelihood that malicious activity will be noticed.
This article explains how a watering hole attack works, how attackers select and exploit trusted websites, and the warning signs to watch out for. It also outlines practical ways to reduce risk and prevent these attacks from causing harm.
How does a watering hole attack work?
A watering hole attack begins when cybercriminals identify a specific group they want to target. They then attack the legitimate websites that the group regularly visits, such as industry forums, partner portals, or niche informational sites.
After identifying a suitable site, attackers exploit vulnerabilities in the site or its supporting infrastructure to inject malicious code or set up redirects. When members of the target group visit the compromised site, that code can execute in the background or direct them to further exploits, potentially leading to malware installation or credential exposure.
These attacks are often used when direct targeting is difficult or unreliable. By compromising a shared resource instead of interacting with users individually, attackers can deliver malicious activity through routine browsing.
Compared to techniques like email phishing or man‑in‑the‑middle (MITM) attacks, watering hole attacks allow malicious actors to reach multiple high-value targets without interacting with them individually or intercepting traffic in real time.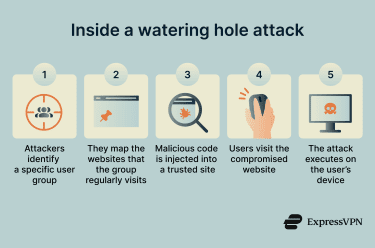
Intelligence gathering
Attackers begin by gathering information about the group they want to target. They analyze common roles, routines, and the websites members of that group visit most often. This may involve reviewing public information, observing activity on industry forums, or analyzing network traffic patterns to understand typical browsing behavior.
During this stage, attackers may use ad tracking or analytics services. When users browse the web from corporate networks, automated systems can collect data such as traffic sources, visit frequency, and commonly accessed sites.
Attackers can identify which websites are most frequently visited by the target group and which sites would be most effective to compromise as watering hole targets.
Attackers also examine how the target group behaves online. This can include identifying commonly used browsers, preferred languages, and typical interaction patterns. These details help attackers tailor malicious code so it’s more likely to run successfully on the devices and systems the group uses.
Infiltrating a legitimate website
Once attackers identify a website that their targets trust and visit regularly, they focus on compromising that site. This often involves scanning for security weaknesses such as outdated software, unpatched plugins, or weak access controls, then exploiting those gaps to gain access.
After gaining control, attackers inject malicious code directly into the site’s pages or scripts. This code may include embedded elements that load automatically when a page is opened.
Exploiting the target
After a site is compromised, attackers wait for members of the target group to visit. When a visitor loads the watering hole site, the hidden code executes and checks the visitor’s browser or operating system for known vulnerabilities.
If a weakness is detected, the code can trigger a drive-by download attack, silently installing spyware or other malicious software.
Once installed, the malware may allow attackers to collect login credentials, establish persistent access, or move laterally within a network. This can enable long-term monitoring, data theft, or further compromise of connected systems.
Real-world examples of watering hole attacks
Real-world examples show how watering hole attacks have been used to compromise trusted websites and silently target specific groups of users.
Internet Explorer zero-day vulnerability exploit
In a series of watering hole attacks, attackers exploited a previously unknown flaw in older versions of Microsoft Internet Explorer to compromise well-known websites. They injected hidden malicious code into pages on trusted third-party sites so that when someone using a vulnerable browser visited the page, the exploit executed automatically.
Because the flaw was a zero-day vulnerability, no patch was available at the time, and security tools had a limited ability to detect the attack. This allowed the exploit to run unnoticed while attackers selectively targeted specific visitors.
One compromised site was the U.S.-based policy think tank Council on Foreign Relations, the publisher of Foreign Affairs, whose website was infected in December 2012. The malware payload was delivered only to Internet Explorer users whose systems met specific criteria, including language settings, reducing the chance of detection.
In April 2013, the U.S. Department of Labor website was also compromised. In that case, the malicious code targeted visitors who accessed certain nuclear-related pages, demonstrating how watering hole attacks can be tailored to narrow audiences within otherwise legitimate sites.
Attack on industrial control systems via Havex Trojan
In 2014, attackers used a watering hole attack to distribute a remote access Trojan (RAT) known as Havex. They compromised several industrial control system (ICS) vendor websites that hosted legitimate software downloads.
When engineers and technicians visited those sites to download trusted tools, the installers had been replaced with trojanized versions. Once installed, the ICS malware enabled the attackers to gather sensitive data from the infected systems.
The campaign affected multiple organizations across Europe and North America and combined watering hole techniques with other methods, including phishing and redirects from compromised websites.
Government network investigative techniques (NITs)
Government agencies have also used watering-hole-style techniques as part of network investigative techniques (NITs) to identify users accessing illegal websites hosted on anonymity networks such as Tor. One widely cited example is the FBI’s 2015 Operation Pacifier, which targeted a dark website known as Playpen.
After taking control of the site, the FBI modified its server to deliver investigative code to visitors’ devices. When a visitor accessed certain pages, the code collected identifying technical information, including IP addresses, and transmitted it back to investigators.
The operation led to hundreds of arrests in the U.S. and abroad and resulted in the conviction of Playpen’s creator and administrator Steven W. Chase, who received a 30-year prison sentence in May 2017.
Hands-on Holy Water campaign in Asia
The 2019 Holy Water campaign differed from many watering hole attacks because it required user interaction to succeed. Instead of exploiting visitors automatically, the attack relied on users clicking a fake software update prompt to initiate a malware download.
Attackers compromised websites operated by local organizations, charities, and religious figures across parts of Asia, selecting sites that their intended targets were likely to visit regularly. By combining trusted websites with a convincing prompt, the campaign increased the likelihood that users would trigger the infection themselves.
APT29’s watering hole campaign on Amazon
In 2025, Amazon identified a watering hole campaign linked to a threat actor known as APT29 that compromised legitimate websites and redirected visitors to malicious domains. The campaign attempted to steer users into Microsoft device code authentication flows using spoofed verification pages that mimicked Cloudflare prompts.
Amazon worked with Cloudflare and Microsoft to disrupt the activity before any user accounts were compromised.
How to prevent a watering hole attack
Preventing a watering hole attack requires a proactive mindset and consistent internet security habits. Attackers rely on trusted websites, outdated systems, and untrained users to succeed. Organizations can greatly reduce their risk by combining technical safeguards with educated employees who understand how these attacks work and how to avoid them.
Technical prevention methods
Technical controls can reduce the likelihood that attackers successfully exploit systems or websites. When combined, these measures can block malicious activity, limit exposure to compromised sites, and stop some threats before they reach users.
However, no single control can fully prevent watering hole attacks. Effective protection relies on a defense-in-depth approach, where multiple safeguards work together so that a failure in one layer doesn’t expose users or systems outright.
Keep software and browsers updated
Keeping software up to date is one of the strongest lines of defense against watering hole attacks. Attackers often take advantage of outdated software to deliver malware, so it’s critical to install updates and security patches promptly on all operating systems, web browsers, apps, and plugins.
Enable automatic updates where possible, and regularly check application settings to confirm updates are current. Keeping everything updated closes known vulnerabilities that watering hole attacks try to exploit.
Use DNS/web filters and endpoint protection
Domain Name System (DNS) and web filtering can help disrupt watering hole attacks when compromised websites attempt to load additional malicious resources. If the injected code tries to contact known malicious domains or redirect users to exploit infrastructure, these filters can block that connection before further harm occurs.
Endpoint protection adds another layer by monitoring behavior on the device itself. If malicious code executes or attempts to exploit the system, endpoint tools can detect and contain the activity even when the initial site appears legitimate.
Together, these controls reduce the impact of watering hole attacks by interrupting different stages of the attack chain.
Implement network segmentation
Watering hole attacks often begin with the compromise of a single user device, rather than a direct attack on core systems. Network segmentation limits the damage from that initial foothold by restricting how far an attacker can move inside the network.
By separating user endpoints from servers, administrative systems, and other high-value assets, segmentation reduces the risk that malware delivered through a watering hole can spread laterally or escalate into a broader intrusion.
Organizations typically implement segmentation using network switches, virtual local area networks (VLANs), and firewall rules to isolate different parts of the network based on risk and function.
Digitally sign code to detect tampering
Some watering hole attacks work by replacing legitimate downloads or updates on trusted websites with modified versions that include malicious code. Digital code signing helps counter this by allowing systems to verify that software comes from the expected publisher and hasn’t been altered.
When a signed file is modified, the signature check fails, alerting the system or blocking execution. This makes it harder for attackers to silently distribute tampered installers or updates through compromised websites and helps users and security tools distinguish legitimate software from malicious substitutes.
Verify software integrity with cryptographic hashes
Cryptographic hashes provide a second way to detect file tampering when software is distributed through trusted websites. While code signing verifies the publisher and integrity of a file, hashes allow independent verification that a downloaded file matches a known, unmodified version.
Vendors can compare hashes from secure internal repositories with hashes of files served publicly to identify unauthorized changes. Publishing these hashes also enables customers or automated systems to verify downloads and detect silent modifications introduced through a compromised site.
Scan installation files with updated antivirus software
Another prevention technique is to scan installation files stored on public servers using current antivirus software. Regular scanning helps detect malware that attackers may insert in a file after compromising a trusted website. This step adds a simple but effective layer of defense before users download the files.
User awareness and training
Watering hole attacks don’t always rely on fully automated exploits. In many cases, attackers introduce phishing-style elements into otherwise trusted websites, such as fake update prompts, login requests, or download links, to persuade users to take an action that triggers the attack.
User awareness training helps people recognize phishing-style behavior even when it appears on a trusted website. In watering hole attacks, attackers often reuse familiar phishing techniques such as fake login requests, update prompts, or download links. These elements are sometimes reinforced with email lures or redirects that guide users toward a compromised page, making the attack harder to detect.
Training users to verify unexpected requests, even on familiar websites, reduces the likelihood that these hybrid attacks succeed.
Safe browsing habits for employees
Because watering hole attacks rely on normal browsing behavior, everyday habits can influence how exposed a user or organization is to this type of threat. While no single behavior can prevent an attack, safer browsing practices can reduce the likelihood of exploitation or limit its impact.
- Endpoint protection: Keeping endpoint protection active and up to date helps detect malicious activity that may be triggered when a compromised site attempts to deliver malware.
- Separation of work and personal browsing: Mixing personal and professional activity on the same device can make it easier for attackers to profile browsing habits. Using separate devices, browsers, or accounts reduces this visibility.
- Reduce passive tracking and targeting signals: Attackers sometimes make a watering hole “selective,” showing malicious content only to visitors who match certain traits (like location, network, or browser setup). Using privacy protections like tracker blocking and limiting third-party cookies can reduce the signals used to pick targets. It won’t stop a compromise, but it can lower the odds you’re singled out.
Watering hole attacks compared to other threats
| Attack type | How it works | Key difference from watering hole attacks |
| Phishing | Uses deceptive emails, messages, or websites to trick users into clicking links, downloading files, or sharing information. | Phishing relies on direct interaction and deception, while watering hole attacks compromise trusted websites that users already visit as part of their routine. |
| Pharming | Manipulates DNS settings or system configurations to redirect users to fake websites without their knowledge. | Pharming redirects users away from legitimate sites, whereas watering hole attacks compromise legitimate sites that targets already trust and use. |
| Supply chain attacks | Injects malicious code into software, updates, or services distributed by third-party vendors. | Supply chain attacks exploit vendor relationships and distribution channels, while watering hole attacks exploit trust in commonly visited public websites. |
| Business email compromise (BEC) | Spoofs or takes over trusted email accounts to trick users into sending money or sensitive information. | BEC attacks exploit trust in email communication, whereas watering hole attacks exploit trust in frequently visited websites. |
Watering hole attacks vs. phishing
Phishing attacks rely on deceptive emails, messages, or prompts that try to persuade individuals to click a malicious link or share sensitive information. The attacker directly contacts the victim and depends on social engineering to trigger an action.
Watering hole attacks don’t rely on direct messages. Instead, attackers compromise websites that a target group already trusts and visits, allowing malicious code or redirects to take effect during normal browsing.
While phishing focuses on convincing individuals to act, watering hole attacks focus on compromising shared resources used by a specific group.
Phishing techniques, however, do appear in watering hole attacks:
- Unexpected prompts on trusted sites: Fake software updates, security warnings, or login requests embedded into compromised pages.
- Redirections to look-alike pages: Users may be silently redirected from a trusted site to a malicious page that imitates a legitimate service.
- Follow-up emails or messages: Attackers may reinforce a watering hole attack with phishing emails that encourage users to revisit a compromised site or download software.
Watering hole attacks vs. pharming
Pharming attacks manipulate DNS settings or system configurations so that users are redirected to fraudulent websites, even when they enter the correct web address. The goal is to divert traffic away from legitimate sites and toward attacker-controlled pages.
Watering hole attacks work differently by compromising legitimate third-party websites that the target group already visits. Rather than redirecting users elsewhere, malicious code is embedded directly into trusted pages and runs when they’re loaded.
In short, pharming sends users to fake sites, while watering hole attacks turn trusted sites into the delivery mechanism.
Watering hole attacks vs. supply chain attacks
Supply chain attacks target vendors or service providers that an organization depends on. Attackers tamper with software updates, services, or hardware at the supplier level to gain access to downstream customers.
Watering hole attacks also exploit third-party trust, but they focus on public or industry websites rather than vendor-delivered products or services. Both approaches take advantage of systems outside the direct control of the victim.
The key difference is scope and delivery. Supply chain attacks distribute compromised products broadly, while watering hole attacks compromise specific websites to target particular groups of users.
Watering hole attacks vs. BEC attacks
BEC attacks target employees through spoofed or compromised email accounts, using trusted communications to trick recipients into sending money or sensitive information.
Watering hole attacks don’t depend on email deception. Instead, they exploit trust in commonly visited websites, allowing attackers to reach users when they browse those sites as part of their normal routine.
While BEC exploits trust in individual communications, watering hole attacks exploit trust in shared online destinations.
FAQ: Common questions about a watering hole attack
What are the symptoms of a watering hole attack?
Watering hole attacks don‘t have distinct or easily identifiable symptoms. However, users may notice warning signs that indicate a malware infection originating from a compromised website. These signs include slow system performance, unexplained crashes, unwanted pop‑ups or malicious redirects to unknown sites, and changes to browser security settings.
How is spear phishing different from a watering hole attack?
Spear phishing sends crafted emails or messages directly to specific individuals to trick them into clicking a link or revealing data. Watering hole attacks compromise a trusted website that targets visitors so malware can infect them without direct messaging.
What does “watering hole” mean in cyber slang?
In cyber slang, a “watering hole” refers to a legitimate, trusted website that attackers deliberately compromise because they know their intended victims frequently visit it. Once compromised, the site is used to quietly deliver malware or other malicious payloads to those visitors.
How can businesses protect against watering hole attacks?
Businesses can prevent watering hole attacks by keeping software and browsers updated, using web filters and secure gateways, running endpoint detection tools, training staff about suspicious sites, and monitoring web traffic for anomalies.
Why are watering hole attacks so effective?
Watering hole attacks work well because they exploit the victim’s trust in familiar sites and avoid direct contact with them.
What tools can help detect and prevent these attacks?
Tools that can help detect and prevent watering hole attacks include web application firewalls, antivirus software, secure web gateways, and endpoint detection and response (EDR) solutions.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN