Ryuk ransomware: Attack methods, impact, and prevention

Ryuk was a Windows-focused ransomware that spread through email spam (malspam) and phishing. After infection, it encrypted files on the victim’s system and demanded a ransom to decrypt them.
Ryuk attacks were carefully targeted, and they often caused severe operational disruption and significant recovery costs for businesses and public institutions.
In this guide, we’ll explain how Ryuk-style attacks infiltrate a system, describe attack patterns, and help you stay safe from a similar ransomware attack.
What is Ryuk ransomware?
Ryuk was a type of ransomware that targeted Windows systems, encrypted files on infected devices, and demanded a ransom for their decryption. Unlike opportunistic malware attacks, Ryuk attacks were often carefully planned.
The group behind Ryuk focused on what later became known as “big game hunting,” deliberately targeting organizations where operational disruption or data exposure would be especially costly. Common victims included hospitals, healthcare systems, large enterprises, and municipal infrastructure.
This approach helped establish a shift away from mass ransomware campaigns toward fewer, higher-value targets and larger ransom demands.
Ryuk was most active between 2018 and 2021. Activity linked to Ryuk declined after 2021 as law enforcement pressure and infrastructure takedowns disrupted operations.
How Ryuk infiltrates systems
The Ryuk ransomware payload was the final stage of a multi-step infiltration process. Below, we’ll explain how Ryuk ransomware took hold.
Common infection vectors
Ryuk’s initial access vector was generally email phishing, usually sent from spoofed addresses to appear legitimate. The emails contained malicious attachments, which could be Word documents, PDFs, or embedded links.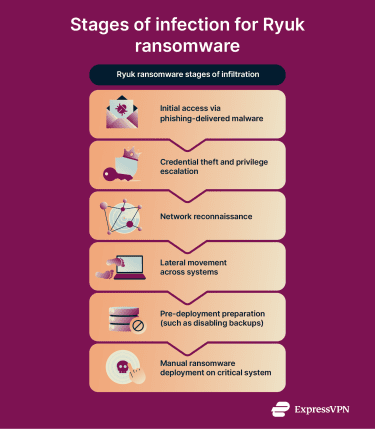
Once downloaded or clicked, these malicious attachments installed Trojans, loaders, and credential-stealing malware. This initial infection phase allowed attackers to map the network, steal credentials, and identify high-value systems and potential ransomware targets. Only after this reconnaissance phase was complete did threat actors manually deploy Ryuk ransomware to selected victims.
A less common infection vector consisted of compromised credentials from previous data breaches. The group used these to access networks directly, install additional malware, and ultimately deploy Ryuk ransomware.
Reconnaissance and network mapping
Ryuk infections often unfolded over extended periods (sometimes weeks or months) rather than being deployed straight after initial access. Attackers would assess compromised environments to decide which victims were worth deploying Ryuk ransomware against.
A targeted attack like this required customization after access was gained, including lateral movement, privilege escalation, and careful timing of the ransomware deployment.
During the reconnaissance period, Ryuk operatives would scan the network to identify:
- Weak points and vulnerabilities
- Domain controllers
- High-value systems to target
- File servers, backup servers, and databases
Ransomware deployment and extortion
Once attackers decided to proceed with the ransomware attack, Ryuk was deployed manually across the network, often during periods of low activity, like nights or weekends, to maximize disruption. The ransomware was generally pushed to multiple systems simultaneously, targeting servers, endpoints, and shared network drives.
Ryuk ransomware encrypted files using strong cryptography, but the group deliberately avoided encrypting certain system files to keep devices operational enough for ransom communication. The malware also commonly deleted Windows shadow copies and disabled recovery features to prevent easy restoration.
After encryption, ransom notes were delivered to affected systems. These notes instructed victims to contact the attackers to negotiate payment, which was usually demanded in cryptocurrency. Ransom amounts were tailored to the victim’s perceived ability to pay, reflecting Ryuk’s focus on high-impact, high-value targets rather than mass infections.
How Ryuk fits into the modern ransomware ecosystem
Where earlier ransomware attacks often relied on mass phishing campaigns, Ryuk’s attacks typically involved careful planning and targeting after initial access was gained. Ryuk attacks were typically human-operated and centrally coordinated.
Although the Ryuk group is no longer active, it helped popularize practices that later became common in modern ransomware operations, including big-game hunting, human-operated deployments, and extensive post-compromise planning. Later groups, such as Conti, expanded on this approach.
Notable Ryuk ransomware attacks
Here are two of the most notable Ryuk attacks, which demonstrate how the malware operated, its impact, and how the authorities responded.
Universal Health Services (2020)
In September 2020, Universal Health Services (UHS), a major U.S. health system operating hundreds of facilities across the U.S. and the U.K., suffered a widespread ransomware attack that cybersecurity analysts attributed to Ryuk.
The attack caused broad IT outages at many hospitals and clinics. Phones died, the electronic systems went offline, and the UHS had to redirect ambulances and patients needing surgery to other healthcare providers. It took more than three weeks for the healthcare system to restore operations.
Billing procedures also suffered a delay for more than two months after the attack, and the UHS faced significant labor costs in restoring connectivity. The total pre-tax losses from the attack amounted to $67 million.
Volue incident (2021)
In May 2021, Volue Technology, a Norway-based green energy solutions provider, reported an attack by Ryuk that disrupted infrastructure management systems. The attack affected some customer-facing platforms and encrypted data, but backups weren’t affected.
The company acted quickly to shut down operations and advised clients to log out from Volue applications and change their passwords. Like UHS, Volue did not pay the ransom, but the overall costs of the incident were nonetheless extensive, with the company receiving an insurance payout related to the incident of 20 million Norwegian Krone (about $2.1 million).
Signs of a Ryuk infection
Below are the most important red flags that might indicate a Ryuk-style ransomware attack.
Early warning indicators
The following warning indicators will tell you if an attack might be underway against your organization. At this point, encryption might not have taken place, but the criminals could be conducting reconnaissance and preparing the way.
Here’s what to look for:
- Suspicious phishing emails with attachments (like PDFs or Word documents)
- Unusual outbound connections or unexpected network scanning activity (can be signs of lateral movement)
- Unexpected PowerShell or executable activity querying Active Directory or directory services, especially from unexpected hosts or accounts
- Unrecognized .exe apps
- New local admin accounts appearing
- Tools or scripts interfering with security processes or uninstalling antivirus components.
- Valid credentials being used from unrecognized hosts and devices
At this stage, isolating affected systems, disabling compromised credentials, and removing attacker tooling may prevent data encryption and stop the ransomware deployment altogether.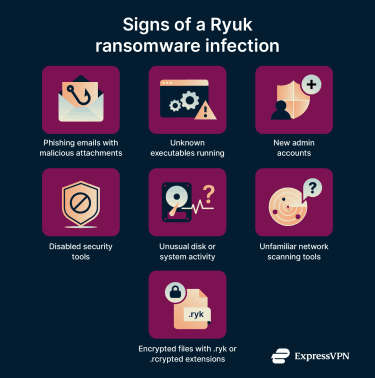
How to confirm an active infection
Confirmation of a Ryuk-style infection focuses on determining whether the ransomware payload is actively executing and encrypting files. Indicators include rapid spikes in CPU usage, disk I/O, and accelerated file modification activity.
Ryuk operators typically avoided encrypting system executables and critical Windows files to keep affected systems operational during the attack while encrypting user and business data. However, this amount of encryption activity can still degrade system performance or cause instability.
Clear signs of an active ransomware attack include widespread file encryption, the appearance of ransom notes, security services being stopped or disabled, and the deletion of backups or shadow copies. Once these indicators are present, prevention is no longer possible, and the response should shift immediately to containment, recovery, and formal ransomware incident response procedures.
How to remove Ryuk ransomware
Removing Ryuk-style ransomware is a complex matter that needs to involve security professionals. Alerting your organization’s IT team, the relevant authorities, and third-party cybersecurity companies is a good idea at this point.
It’s important to know that Ryuk ransomware removal doesn’t decrypt already encrypted files. The goal here is to stop the encryption process and halt the further spread of the ransomware.
Immediate actions to take
Once you confirm a Ryuk-style ransomware infection, immediately do this:
- Disconnect the affected devices from the network to limit the spread of the infection.
- Alert the IT and security teams so they can begin analyzing the malware and the extent of the infiltration.
- Block all malicious IPs and domains to halt the infiltration (though note that attackers often use legitimate services or rotate infrastructure, so this may only partially help).
- Disable local admin accounts to remove any higher privileges from the attackers.
- Scan all endpoints (devices) to identify malware and determine the scope of the infection.
- Change all compromised credentials for users and admins to prevent another attack.
In the U.S., you can contact the FBI’s Internet Crime Complaint Center (IC3), or the Cybersecurity and Infrastructure Security Agency (CISA) to report a ransomware incident. Based on your jurisdiction and other factors, you may also need to report the incident to the affected parties.
The only “clean” method to get rid of Ryuk-style ransomware after encryption has begun is via system restore or a full operating system reinstallation. Attempting to remove the ransomware manually (using malware tools, for instance) may leave hidden persistence mechanisms that allow attackers to regain access.
System restoration and data recovery
Recovery from a Ryuk ransomware attack depends on having clean backups created before the attack. Best-practice ransomware defenses include maintaining offline and off-site backups.
When restoring, prioritize backups from before the suspected intrusion window, though identifying the exact start of the attack can be challenging.
Note that while backups can restore encrypted data, they don’t resolve compromised credentials, persistence mechanisms, or network access used by attackers. Systems shouldn’t be reconnected until the initial access vector has been identified, all compromised credentials have been changed, and any malware or backdoors have been fully removed across the network.
Preventing future Ryuk infections
Preventing Ryuk-style ransomware infections is a far better option than responding after the infection has already happened. Taking the right preventative measures can help your organization to avoid significant service disruption and financial impact.
Best practices and security measures
- Staff awareness and phishing resilience: Employees should learn to recognize suspicious messages, unusual links or attachments, and attempts at psychological manipulation. Simulated phishing exercises can help identify gaps before ransomware attackers exploit them.
- Zero-trust access controls: Adopting a zero-trust security model can limit the impact of Ryuk-style ransomware attacks. By continuously verifying access requests, no user or device is implicitly trusted, whether inside or outside the network, meaning it’s harder for attackers to move laterally using stolen credentials.
- Network segmentation: Segmenting your network can restrict attackers’ movements by isolating the network into separate zones, each with individual controls. For instance, staff working in manufacturing systems shouldn’t automatically have access to product design or administrative resources. This makes lateral movement more difficult, reducing the attacker’s ability to reach high-value systems or deploy ransomware across the entire network.
- Account protection and authentication: Multi-factor authentication (MFA) adds another layer of security for email accounts and remote access tools, making it harder for attackers to reuse stolen credentials.
- Patch management and system updates: Keeping software and devices fully updated reduces the likelihood of known vulnerabilities being exploited by Ryuk-style attackers. Consistent patching also helps close security gaps that may be used as entry points for ransomware.
- Backup strategy: Offline and off-site backups play an important role in ransomware preparation. While backups can’t prevent attacks, they may reduce data loss and support recovery efforts if systems are compromised.
Most security specialists also recommend having a quick incident response checklist to protect against ransomware like Ryuk.
Tools and services for defense
Ryuk-style ransomware protection requires a multi-layered approach, including:
- Endpoint detection and response (EDR) tools: Monitor all endpoints (devices) on a network to investigate, detect, and respond to threats in real time. This includes pre-infection malware that can lead to a Ryuk-style infection.
- Antivirus suite: Traditional signature-based antivirus is often insufficient for Ryuk-style infections, but modern behavioral detection can catch some malicious activity. Ryuk’s human-operated nature, however, meant it could evade many automated defenses.
- Secure email gateways: Help to block malicious attachments and links with filtering features.
- Security information and event management (SIEM) tools: These platforms offer centralized monitoring for suspicious activity, with real-time incident response capabilities if a ransomware infection occurs.
Consistent security behaviors and a strong suite of protection tools should form the foundation of a good defense against ransomware.
Is Ryuk ransomware still active in 2026?
While the Ryuk group is no longer considered active, its source code, tooling, and techniques have been reused and adapted by other groups. There’s no evidence of ongoing, large-scale Ryuk campaigns, but some Ryuk-related components occasionally appear in malware telemetry. That said, these instances are typically residual or repurposed rather than part of coordinated operations.
Ryuk’s lasting impact isn’t the malware itself, but the operational model it helped popularize. It normalized human-operated ransomware, long dwell times before encryption, integration with credential theft and lateral movement, and enterprise-focused targeting.
These tactics continue to shape modern ransomware campaigns, even when the Ryuk name is no longer used.
FAQ: Common questions about Ryuk ransomware
What makes Ryuk different from other ransomware strains?
Ryuk stands out from other ransomware strains thanks to its human-controlled, multi-stage attacks, where attackers spent days or weeks inside a compromised network using stolen credentials and legitimate admin tools. The ransomware was then deployed as a final, targeted action. Instead of spreading automatically or encrypting a single device, Ryuk launched deliberately across large parts of an organization to maximize operational disruption and ransom pressure.
Can Ryuk ransomware be removed without paying the ransom?
Yes, Ryuk-style ransomware can be removed by wiping or restoring compromised systems, which eliminates the malware itself. However, this does not recover files that were already encrypted. Unless clean, pre-infection backups exist, encrypted data is generally unrecoverable, and paying the ransom does not guarantee successful decryption or protection from future compromise.
Where should Ryuk ransomware incidents be reported?
In the U.S., you can report a ransomware incident to the FBI’s Internet Crime Complaint Center (IC3), or the Cybersecurity and Infrastructure Security Agency (CISA). Depending on your jurisdiction and data policy requirements, you might have to report ransomware incidents to affected individuals or organizations as required by law.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN