What is REvil ransomware? A complete cybersecurity breakdown

REvil ransomware was a highly prolific ransomware operation active between 2019 and early 2022. It ran a large-scale Ransomware-as-a-Service (RaaS) model, enabling affiliates to launch attacks against hundreds of organizations worldwide.
The group combined data encryption with double extortion tactics, locking victims out of their systems and threatening them with public data leaks if they refused to pay. Stolen files were then published or auctioned on REvil’s leak site, known as the “Happy Blog.”
While the gang is no longer operational, the RaaS model it popularized remains widely used by newer ransomware groups, and many of the attack techniques continue to resurface. This guide breaks down how REvil worked, what made it dangerous, and what we can learn from it to better defend against modern ransomware threats.
What is REvil ransomware?
REvil ransomware refers to both the criminal operation behind the attacks and the malware they deployed.
- The group: REvil was a cybercriminal organization that developed, maintained, and distributed ransomware through a RaaS model. The group was dismantled in 2022, but its affiliates carried out attacks globally while it was active.
- The malware: The ransomware itself encrypted victims’ files and systems to demand ransom payments. Variants of this malware were used in hundreds of high-profile attacks.
Below, we’ll discuss how the hacker group operated, how its ransomware attacks worked, and some of its most infamous campaigns.
Origin and background
Security researchers first spotted REvil (also known as Sodinokibi) in May 2019, quickly identifying it as a sophisticated ransomware operation. It showed a high level of technical maturity and was deployed through a RaaS model, allowing multiple affiliates to carry out attacks using shared infrastructure.
Over time, REvil expanded its technical capabilities and its operational reach. It also adopted a wider range of attack techniques, including exploiting exposed remote access services.
By 2021, REvil had carried out several high-profile attacks. During its lifetime, the ransomware infected over 175,000 computers globally and extorted $200+ million in ransom payments, according to a U.S. Department of the Treasury press release.
In late 2021, coordinated actions involving U.S. agencies, international partners, and private cybersecurity firms targeted REvil’s infrastructure. In January 2022, Russia’s Federal Security Service (FSB) announced arrests and the disruption of REvil’s operations, effectively bringing the group’s known activities to an end.
There’s no evidence that REvil continues to operate as an organized group. However, its tools, techniques, and business model live on, and similar ransomware operations continue to use many of the same methods today.
What are REvil’s key characteristics?
REvil’s RaaS model means the syndicate developed and maintained the REvil ransomware, and then recruited affiliates to buy the ransomware and use it. With this model, they popularized double extortion tactics, where hackers would steal sensitive data and then threaten to expose it if the victim doesn’t pay the ransom.
Their preferred strategy was spear phishing. REvil targeted specific large enterprises, managed service providers (MSPs), and supply-chain hubs where downtime, data exposure, or reputational harm would be especially costly and lead to maximum leverage.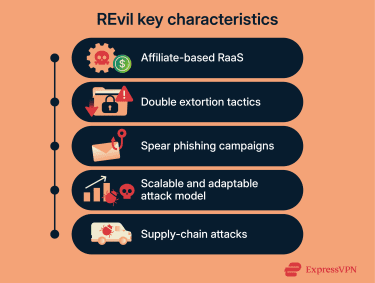
REvil became one of the most infamous RaaS syndicates in the world in less than three years. Alongside others like LockBit, Cl0p, and DarkSide, it normalized supply-chain attacks and RaaS at scale. With a scalable and adaptable attack model, REvil’s campaigns varied wildly, which made detection harder and allowed the ransomware to adapt to new vulnerabilities.
Notable REvil attacks
Some of the most notable REvil ransomware attacks include:
- Travelex, 2020: UK-based foreign exchange firm Travelex was targeted by ransomware later identified as the Sodinokibi/REvil strain. Travelex paid a ransom of around $2.3 million to regain access to its systems. The prolonged outage severely disrupted operations and contributed to significant financial difficulties for the business.
- Grubman Shire Meiselas & Sacks, 2020: Entertainment law firm Grubman Shire Meiselas & Sacks (GSMS) was another high-profile target of REvil. GSMS refused to pay the $42 million ransom, and portions of the stolen data were later leaked publicly.
- JBS, 2021: JBS, Brazil-based multinational meat-processing company and one of the largest food producers in the world, paid a $11 million ransom to REvil. The group is suspected to have obtained leaked credentials of several JBS employees, which enabled it to break into the company’s systems, proceeding to extract data and issue a ransom.
- Kaseya, 2021: REvil’s last major publicly reported attack was against Kaseya, a popular remote network management software. REvil compromised between 800 and 1,500 businesses that were using Kaseya.
No major attacks publicly attributed to REvil have been reported in recent years. However, ransomware gangs often rebrand or operate through affiliates, so attacks using REvil code may happen without the “REvil” name attached. Moreover, smaller incidents or targeted attacks may not be publicly disclosed.
How REvil ransomware works
REvil ransomware spread through a combination of social engineering and technical exploits. The goal was to gain unauthorized access to systems, encrypt valuable files, and pressure victims into paying a ransom.
Infection vectors and entry points execution
The group initially used zero-day vulnerabilities, such as one in Oracle’s WebLogic, to gain full access to systems without user interaction. Over time, REvil expanded its tactics to include phishing emails, which tricked users into downloading and installing the ransomware, and Remote Desktop Protocol (RDP) exploits to gain unauthorized access to exposed systems.
It also exploited other vulnerabilities, including older Windows zero-days and weaknesses in MSPs’ infrastructure.
Payload execution and encryption
Once REvil ransomware infected a device or server, it began a staged execution process. The malware scanned the system to identify valuable files and directories, collected system and user information, and attempted to elevate privileges to gain more control.
With higher-level access enabled, REvil could modify system configurations and registry entries to maintain persistence and prepare the environment for encryption. It then encrypted targeted files and, in many cases, exfiltrated sensitive data to support double extortion.
Although the final encryption often occurred during nights or weekends to reduce detection, the preparation phase could unfold over days or weeks. In this time, attackers moved laterally, escalated privileges, and staged data for exfiltration, leaving warning signs that were often missed until the ransom demand appeared.
Ransom demands and data leak tactics
After encryption was complete, the malware left behind a ransom note demanding payment in exchange for a decryption key and the promise not to leak stolen data. Victims were threatened with permanent data loss or public exposure if they refused to pay (often in Bitcoin).
Ransom demands varied widely based on the size of a company and its ability to pay, from thousands to tens or even millions of dollars. In most cases, a deadline was involved, with threats to release data in stages or increase ransom over time if demands are not met.
This double extortion tactic of data leaking and blackmail via ransom was one of the most common REvil extortion tactics.
How to spot a REvil attack: Warning signs and detection
While REvil itself is no longer active, many ransomware strains still use similar tactics, and some may even reuse REvil code or techniques. Paying attention to the warning signs can help organizations detect attacks early, regardless of which group is behind them.
An attack of this kind takes place across several days or weeks, with warning signs including:
- Suspicious communications: Phishing emails asking for credentials and attachments or links that seem unusual, especially coming from unknown senders.
- Unusual system activity: Unrecognized files or folders appearing on drives, new software installed without authorization (like remote access tools), and disabled antivirus or security tools.
- Network or server anomalies: Unexpectedly high network traffic (especially to unknown IP addresses), and exposed RDP or other remote access points.
- Signs of data compromise: Missing, altered, or encrypted backups, more frequent system crashes or error messages, and suspicious processes consuming high resources or behaving unusually.
If any combination of these signs is observed, the affected devices should be disconnected from the network and the IT or security team should be alerted. Early detection is critical when it comes to mitigating damage.
Tools for detection
Tools like antiviruses and security information and event management (SIEM) solutions can help with detection and mitigation of ransomware attacks.
Antivirus and EDR tools
Anti-malware software can detect and block some ransomware attacks through known blacklists and common malware signatures. Antiviruses automatically search for suspicious files or processes commonly associated with ransomware, and real-time monitoring can also detect registry modifications for escalated privileges. It’s also a good idea to enable automated scanning of emails and flash drives for malicious files and phishing attempts.
However, ransomware operators are constantly looking to bypass antivirus detection by camouflaging malware and making it inconspicuous, and this is where endpoint detection and response (EDR) tools are useful. They can:
- Monitor network connections, process creation, and registry changes.
- Analyze and detect suspicious activities before an attack.
- Use behavior-based detection and AI monitoring to quickly identify threats.
- Watch over all endpoints (like laptops, servers, and cloud-based instances).
Despite these benefits, no solution can guarantee complete protection, so EDR works best as part of a layered cybersecurity strategy.
Network monitoring and SIEM solutions
Network monitoring is a very efficient way to spot ransomware attacks during the pre-attack or execution phases. System admins can look for high volumes of traffic to company servers from unknown IP addresses and an increase in access requests to sensitive data, for example.
Establishing a baseline for normal network behavior can help identify anomalies quicker. The largest spikes in network activity happen when criminals exfiltrate the data. Even at this point, vigilance and quick responses can mitigate some of the fallout.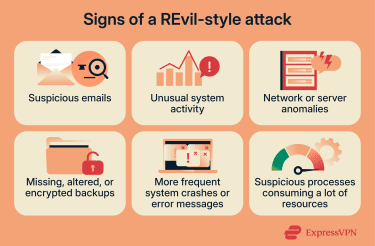
SIEM solutions can help to spot ransomware behavior patterns from the earliest stages of attack (phishing attempts and suspicious files). Many SIEM solutions use the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) knowledge base. Common attack patterns they can detect include:
- File encoding or downloading.
- Attempts to delete on-premise backups or disable recovery in-boot configuration.
- Modification of data transfer size limits.
- Suspicious number of files moved or renamed.
- Creation of ransomware decryption instructions.
- Suspicious communication with a hostile host.
All of the above are known REvil tactics that also apply to other ransomware attacks.
Potential damage from REvil ransomware
REvil-style ransomware can be very damaging on multiple levels, from financial losses to a loss in trust among clients.
Data loss and downtime
The aftermath of a REvil-style ransomware attack can be dire. Victims lose sensitive corporate or customer data that, once exposed, can lead to further intellectual property attacks.
Operational downtime is another important factor to consider. Because REvil encrypts the system’s servers, a business may have to interrupt operations temporarily. In Kaseya’s case, REvil’s attack forced many Coop supermarkets in Sweden to close temporarily until they restored services.
Financial and reputational impact
Businesses going through REvil ransomware attacks often faced massive financial losses, including ransom payments, emergency IT response costs, system downtime, legal fees, and regulatory fines. In some high-profile cases, ransom demands alone reached tens of millions of dollars.
The reputational damage could be equally severe. Companies that suffered breaches risked losing customer trust and damaging partnerships. Tech firms, in particular, were highly exposed because of their collaborations with corporate clients and the potential for leaked intellectual property.
Successful REvil attacks could also trigger downstream consequences, where compromised data enabled attacks on partners, suppliers, or service providers, magnifying the overall impact. In some cases, attackers leveraged leaked information to launch additional fraud, phishing, or ransomware campaigns targeting connected organizations.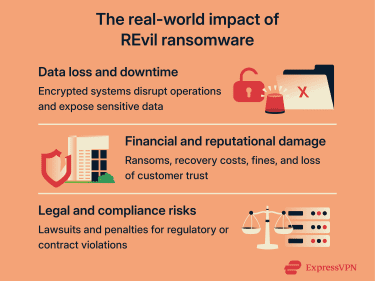
Legal and compliance risks
Legal issues, either due to improper management of the situation or sensitive data leaks, can become a significant obstacle in the business recovery process following a ransomware attack.
Legal liability to customers and partners
If sensitive corporate or customer data is stolen, or services are disrupted, businesses may breach contracts with clients or partners. Affected individuals or organizations could file lawsuits seeking compensation for damages.
Class-action lawsuits are also possible, especially if attackers exploit gaps in security that could be deemed negligent.
Regulatory compliance risks
Businesses may fail to meet obligations under data protection laws like the General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPAA). This includes the requirement to notify regulators and affected parties promptly when a breach occurs. Failure can result in fines or enforcement actions. Theft of personally identifiable information (PII) or other sensitive data may trigger additional penalties.
How to prevent a ransomware infection
Preventing a REvil-like type of attack is a multi-layered process that focuses on internal security, limiting access privileges, and raising employee awareness.
Patch management and updates
Unpatched software is a major factor when it comes to ransomware attacks. These security holes can be:
- Outdated or improperly configured remote-access services (like Screen Connect).
- Unpatched or exposed RDP services.
- Critical unpatched Windows vulnerabilities.
- Unpatched email servers.
Timely updates and patching are a great way to plug security gaps and close down attack vectors that ransomware agents can use.
High-privilege infrastructure (like data servers) should be a priority for patch deployment, as they’re indirectly vulnerable to targeted attacks. Specifically, hackers steal credentials of users with admin access, which gives them access to these servers.
While early patching doesn’t guarantee immunity from ransomware like REvil, failure to patch increases exposure to attacks considerably.
Email protection
Email is perhaps the most common medium for ransomware spreading and infection. Malicious attachments and phishing links are extremely common, and very risky:
- Malicious attachments often come as PDFs, ZIP files, and Word documents. If opened, especially if macros or scripts are enabled, they can install ransomware or other malware.
- Phishing links may lead to fake login pages or trick users into downloading malware. These links may look like invoices or account verification prompts.
Red flags of malicious emails can include unsolicited attachments, emotional language (threats or urgency), misspellings, or grammar mistakes. Email security solutions can detect suspicious domains in email addresses, block executable files, analyze URL rewriting patterns, and sandbox attachments.
These tools help prevent malicious attachments from reaching inboxes and detect suspicious links or domains before users interact with them. However, things can still slip through, so vigilance is still required.
Employee awareness and training
The human factor is often the most dangerous loophole in any security system. Specifically, employees with poor security hygiene, weak passwords, and a high susceptibility to social engineering. Organizations should make employee awareness and training an essential part of their security policies. Good anti-ransomware advice includes:
- Never reusing passwords across multiple systems.
- Always reporting suspicious activities or credential compromise.
- Learning to identify harmful links, malicious attachments, and well-crafted phishing emails.
- Using multi-factor authentication (MFA) consistently across accounts.
Backup and recovery planning
Successful data recovery can make the difference between a major financial loss and a salvageable situation. Even if ransomware encrypts an organization’s data, having a full backup ready mitigates the damage by minimizing business interruption and financial losses.
However, because of this, cybercriminals often prioritize backups during a ransomware attack. Deleting them removes the organization’s safety net. That’s why it’s a good idea to have offline and, ideally, offsite backups that can be regularly tested to ensure they’re viable. Backup redundancy (making more backups than needed) is another effective way to prepare for the worst.
| Best practice | Reason |
| Use MFA | MFA identity verification (especially phishing-resistant MFA like security keys) can slow down or stop unauthorized access from ransomware operators using compromised credentials. |
| Create regular data backups | Efficient data backup strategies can minimize data loss during a ransomware infection. Making backups read-only or storing them off-site (or offline) will improve security further. |
| Implement zero-trust security | Zero-trust security prevents unauthorized access and limits attack surfaces before malware can spread, and limiting admin privileges also helps contain the damage if an infection does occur. |
| Monitor network anomalies | Regular network assessments can find vulnerabilities early and inform security improvements in weaker areas (like an unpatched server that ransomware can exploit). |
| Use anti-ransomware solutions | Antiviruses, EDR tools, and SIEM solutions offer a wide detection spectrum for many known ransomware variants today. |
| Enforce good employee cyber hygiene | Employees should be aware of security risks and best security and data access practices. Regular cybersecurity training (like knowing how to detect a phishing email and using strong passwords) can effectively prevent ransomware infection. |
| Assess third-party vendor security | A ransomware infection can go down or upstream because of privileged access between partner organizations. Regular security audits and risk assessments on partner firms can help keep this under control. |
Immediate steps to take after a REvil infection
Here’s what to do if your organization falls victim to a REvil or similar ransomware infection:
- Report the attack to the IT and security teams.
- Find infected devices and disconnect them from the network. Isolation will slow down the spread of the ransomware.
- Run an anti-malware scan and pair it with EDR tools or professional forensic analysis.
- Determine which systems are critical for backup restoration and data recovery.
- Check other prevention systems (like a SIEM) and logs to check for network compromises and security holes.
- Deleting unauthorized accounts, reset credentials, and validate endpoints and network security.
- Reconnect systems and restore data from backups, if available.
- Document the event in detail to improve security and refine organizational policies for the future.
If there are no backups in place, consult with security experts to decide on the best course of action.
Working with authorities and experts
Reporting a ransomware attack to local authorities and engaging cybersecurity experts is almost always advisable. These steps provide multiple benefits:
- Specialized guidance: Security experts can help restore systems and explore decryption options.
- Regulatory compliance: Reporting demonstrates good-faith efforts to meet legal obligations and may be required in some jurisdictions.
- Coordinated response: Collaboration between internal teams, experts, and authorities helps organizations make informed decisions.
- Legal counsel: Advisors can assist with issues related to data protection, financial liabilities, and breach notification requirements.
Essentially, this helps structure the response, reduce operational and financial impact, and mitigate reputational damage.
FAQ: Common questions about REvil ransomware
What kind of damage can a REvil ransomware attack cause?
A REvil ransomware attack can cause significant financial and reputational damage. If the attack is severe enough and no backups are in place to restore operations quickly, the organization can also lose its customers’ trust. This reputational damage can lead to more financial losses down the line.
What makes REvil different from other ransomware groups?
REvil stood out from other ransomware groups because it ran Ransomware-as-a-Service (RaaS) at scale. Its business model mirrored the operational practices of legitimate Software-as-a-Service (SaaS) companies, like rapid feature development, affiliate onboarding, and constant scaling. It also specialized in double extortion and spearphishing, targeting companies at the supply chain level. The focus was on systemic impact rather than individual payouts.
Is REvil still active today?
The original REvil criminal syndicate was shut down in January 2022, and there have been no signs of attacks in recent years. However, other ransomware groups now employ similar tactics, and the code for the REvil ransomware may live on in other strains today.
Can REvil be prevented with antivirus alone?
No, because antiviruses can only detect known threats. Ransomware gangs often use obfuscation techniques to bypass antivirus detection, which could delay detection until it’s too late and the ransomware has already encrypted files. While good antivirus solutions with real-time protection are helpful, they should be combined with other tools like security information and event management (SIEM) solutions.
Are specific industries more vulnerable to REvil?
REvil was well known for attacking managed service providers (MSPs) and other companies with data-rich operations. They specifically targeted companies where downtime, data exposure, and reputational damage created maximum leverage for blackmail.
What are recovery options after a ransomware attack?
After a ransomware attack, backup recovery is the best option to restart operations as soon as possible. It’s ideal to keep backups offline and off-site to prevent tampering from criminals. If backups aren’t an option, contacting expert security specialists and the authorities swiftly can help contain the attack. Coordinated response efforts focus on minimizing damage, preventing reinfection, meeting legal obligations, and restoring operations.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN