XDR in cybersecurity: What it is and why it matters

Extended detection and response (XDR) is a cybersecurity framework designed to help organizations keep up with complex, multi-stage attacks. As threats move across endpoints, networks, cloud services, and identities, XDR brings security data together to help teams see attacks earlier and respond more effectively.
This article explains what XDR is, how it works, its benefits and limitations, and why it matters for cybersecurity today.
What is XDR in cybersecurity?
XDR is a centralized cybersecurity platform that detects, investigates, and responds to threats across an organization’s entire IT environment. It continuously collects and correlates telemetry (ongoing, time-based, system-generated data) from endpoints, networks, cloud services, email, and other systems.
Rather than looking at each system separately, XDR connects the dots between these different data points. This helps security teams spot attacks that might otherwise go unnoticed because the activity is spread across multiple places.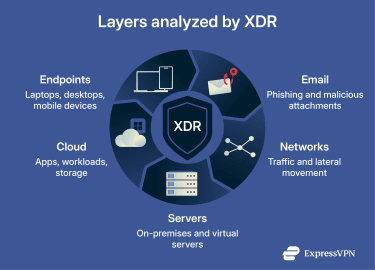
There are two common types of XDR:
- Native XDR: This comes from a single security vendor and works best with that vendor’s own tools. This can make setup easier but may limit visibility to other products.
- Open XDR: This works across many different security tools, no matter the vendor. It brings together data from various sources, making it a better fit for organizations using multiple security products.
Both types aim to give security teams clear, actionable information and make it easier to respond quickly to threats.
Why XDR matters in modern cybersecurity
Modern cyberattacks have grown increasingly sophisticated and difficult to detect. Instead of targeting a single system, attackers often move across endpoints, networks, and cloud services, progressing through multiple stages of the kill chain (common stages of a cyberattack). At the same time, network architectures have grown more complex, spanning on-premises systems, cloud environments, and remote users.
In siloed setups, security tools operate independently, each covering only a specific area. This fragmentation scatters alerts and data across multiple platforms, making it difficult for security teams to get a complete view of an attack or connect related events.
By monitoring multiple environments at once and correlating security signals across them, XDR can help address this problem, enabling teams to detect threats earlier and respond faster.
How XDR works
XDR is commonly offered as a cloud-based service that brings together multiple security technologies in one platform. Here’s how XDR typically detects and responds to threats across an organization’s environment.
Data collection and aggregation
XDR collects and correlates different types of security data, including:
- Logs and telemetry from devices and applications.
- Indicators of compromise (IOCs) like suspicious IP addresses or file hashes.
- User behavior and authentication events.
- Network traffic and connection details.
To gather this data, XDR integrates with a wide range of security tools and systems, including:
- Antivirus and firewall software that protect individual devices.
- Specialized solutions like endpoint detection and response (EDR), network detection and response (NDR), and user and entity behavior analytics (UEBA).
- Platforms that oversee security data aggregation and automate response actions, such as security information and event management (SIEM) and security orchestration, automation, and response (SOAR) systems.
- Various IT environment components, such as laptops, servers, cloud workloads, email systems, applications, and networks.
Correlation, analytics, and AI‑driven detection
After collecting data, XDR applies advanced analytics and machine learning algorithms to identify patterns that match known threats or highlight unusual activity as it happens. By comparing current data against historical activity and established baselines, XDR can detect anomalies like strange user actions or irregular system processes that could signal a breach.
XDR also incorporates threat intelligence from multiple sources (whether from the provider itself, third parties, or community networks) that supply continuously updated information on emerging attack tactics and techniques.
The machine learning models within XDR keep improving by learning from new data, making the system smarter and more accurate over time.
Automated response and remediation workflows
When XDR detects a confirmed threat, it can trigger responses based on predefined policies. These actions can include:
- Triggering an anti-malware scan on other devices on the network.
- Isolating or shutting down an affected device.
- Revoking access to the network for affected users.
- Blocking suspicious network traffic.
- Quarantining malicious files or processes to prevent further execution.
- Resetting compromised accounts or credentials.
- Initiating automated containment flows that coordinate actions across multiple systems (for example, orchestrating SOAR workflows to manage response tasks).
This can help contain and mitigate threats quickly, even before a human analyst intervenes.
MITRE ATT&CK® mapping
Many XDR solutions use frameworks like the MITRE ATT&CK® knowledge base, which categorizes the tactics and techniques commonly used by cyber attackers. Mapping detected activities to the ATT&CK framework can help security teams quickly understand the attack’s techniques and tactics, locate the affected systems, and develop a targeted response.
Key benefits of XDR
Thanks to its ability to bring together a variety of security signals and user identities into a single view, XDR gives security teams a clearer, more connected understanding of threats. This visibility lays the groundwork for several important benefits: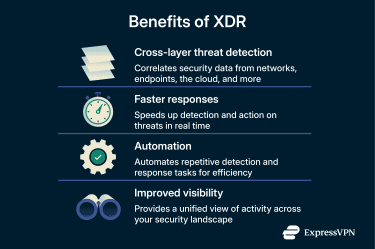
- Faster detection and response: By correlating data from multiple sources and applying analytics, XDR can help reduce the mean time to detect (MTTD), or how long it takes an organization to detect a threat after it’s initiated. In many cases, XDR can also initiate automated responses to contain threats quickly, also reducing mean time to respond (MTTR), or the time it takes to contain a threat after detection.
- Support for proactive threat hunting: In addition to automated detection, XDR provides the consolidated telemetry, behavioral context, and analytic capabilities that security teams use in threat hunting, which is the proactive search for unknown or hidden threats that haven’t yet triggered traditional alerts. The correlated data it offers can give analysts the visibility and context needed to investigate and remediate subtle or emerging threats before they escalate.
- Reduced alert fatigue and improved prioritization: Traditional security tools often generate large volumes of alerts, many of which may be low priority or false positives. XDR is designed to correlate related signals and provide richer context, helping teams focus on the incidents most likely to represent real threats. However, like any security tool, it may still produce some unnecessary or low-priority alerts, especially in the early stages or if it’s not fine-tuned correctly.
- Operational efficiency: XDR platforms can automate repetitive human-in-the-loop (HITL) tasks like monitoring and initial response actions. And by unifying multiple security functions into a single platform, it can generally help streamline your processes.
- Support for hybrid and distributed work environments: XDR provides integrated visibility across devices and locations. This could help your organization detect and address threats in on-premises infrastructure, cloud services, and remote endpoints.
Drawbacks and limitations of XDR
The main drawback to XDR is that it’s primarily reactive rather than proactive. XDR excels at identifying and responding to active threats, but it doesn’t help to fix the vulnerabilities that might let them through. To achieve comprehensive protection, your organization will likely need to combine XDR with other proactive security processes and tools.
These are XDR’s main limitations and some ideas for how to address them:
- Unpatched software and outdated systems: XDR isn’t designed to scan for software weaknesses or to automatically apply updates. Vulnerability scanning and patch management tools can help identify outdated software, missing patches, and configuration issues, complementing XDR’s detection and response capabilities
- Weak system settings and misconfigurations: Misconfigured software or operating systems can create security gaps that XDR can’t fix. One effective way to address this is by enforcing secure defaults. For example, you could ensure that unnecessary services are disabled, administrative privileges are restricted, strong passwords are required, and multi-factor authentication (MFA) is enabled by default.
- Endpoint-level attack prevention: XDR collects and correlates data from endpoints, but it doesn’t provide full device-level protection. Dedicated endpoint protection software can help actively block malware and unauthorized access on individual devices. Software like antivirus programs, next-generation antivirus, and host-based firewalls is still recommended.
- Not guaranteed to detect every threat: XDR monitors for suspicious activity, but it may miss threats that haven’t been seen before. Threat intelligence feeds (lists of known malicious domains, IP addresses, or malware signatures) can supplement XDR by providing continuous updates on the latest threats.
- Integration challenges: XDR depends on collecting data from many different security tools and systems, which can make integration complicated. Since each product may use its own way of formatting and logging data, ensuring consistent data ingestion and normalization can be difficult, especially in environments that combine older legacy systems with newer, specialized security solutions.
- Still dependent on human expertise: Although XDR automates certain tasks, it does not eliminate the need for skilled analysts to tune detection rules, investigate alerts, and validate responses. Without trained personnel, the benefits of XDR can be limited.
When combined with proactive processes and tools, XDR can focus on detecting and responding to threats in real time, while the other measures can reduce the vulnerabilities these attacks want to exploit.
XDR vs. other security solutions
Here’s a comparison of how XDR relates to other common cybersecurity tools and technologies.
- XDR vs. Security Information and Event Management (SIEM): SIEM tools gather and analyze logs from across your organization to help with monitoring and compliance, often focusing on large-scale log management and alerting. While SIEM can provide real-time alerts, XDR pulls data from more sources (endpoints, networks, cloud services, etc.) and can automate responses to threats.
- XDR vs. Endpoint Detection and Response (EDR): EDR only focuses on detecting and responding to threats at the endpoint (and is a key component of XDR). XDR has a broader scope, integrating data across endpoints, networks, cloud, email, and more.
- XDR vs. Data Loss Prevention (DLP): DLP focuses on protecting sensitive data by attempting to protect it from being accidentally or intentionally exposed. While XDR doesn’t replace DLP, it can complement it by detecting broader threats and revealing potential risks that DLP can then address, like unauthorized access to data or systems.
- XDR and zero trust: Zero trust is a security framework focused on continuous verification of all users and access. XDR supports zero-trust principles by continuously monitoring and responding to threats after access is granted.
- XDR and virtual private networks (VPNs): Whether used for remote access or site-to-site connections, VPNs encrypt data and secure communication channels between users and networks. However, they don’t detect or respond to threats. XDR complements VPNs by monitoring for malicious activity within the network and triggering timely responses.
FAQ: Common questions about XDR
What’s the difference between EDR and XDR?
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) are both important technologies used to detect and respond to threats, but they operate at different levels. EDR focuses on monitoring and protecting individual endpoint devices such as laptops, desktops, and servers.
XDR builds on EDR by collecting and correlating security data from many sources, including endpoints, networks, cloud services, and email. This provides broader visibility and more coordinated detection and response across the entire IT environment.
What makes XDR different from SIEM?
Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) are both cybersecurity solutions but have differing levels of scope and involve the use of different types of data. SIEM has a narrower focus, mostly relying on log data from network sources. XDR, meanwhile, involves a broader range of security data from endpoints, networks, and cloud environments.
How does XDR compare to DLP?
Data Loss Prevention (DLP) is focused on policy enforcement. It’s meant to classify and protect sensitive data by preventing unauthorized access, sharing, or transfer across systems, networks, and devices. It helps keep data secure based on predefined policies.
In contrast, Extended Detection and Response (XDR) is focused on the behavior of malicious actors. Its purpose is to help detect, investigate, and respond to cyberattacks by following attack chains across the environment. While DLP focuses specifically on data security, XDR monitors for a wide range of threats. This includes threats that may try to exfiltrate data but also other malicious activities such as credential theft.
Can XDR integrate with existing tools?
Yes, it’s possible to integrate Extended Detection and Response (XDR) with existing security tools. This is a core function and benefit of many XDR platforms, allowing users to layer XDR on top of their existing security stack rather than having to replace it.
What industries benefit most from XDR?
Extended Detection and Response (XDR) is particularly useful in industries that manage large amounts of sensitive or high-value data, operate under strict regulatory requirements, or face broad, complex attack surfaces. Sectors like financial services, healthcare, government, retail and e-commerce, and information technology and telecommunications commonly adopt XDR.
How does XDR improve threat detection?
Extended Detection and Response (XDR) improves threat detection by taking a much broader view of security incidents and attacks than other security solutions. While many traditional tools detect threats independently on individual devices or networks, XDR looks for threat signals across numerous endpoints and platforms at the same time.
Does a VPN still matter if an organization uses XDR?
Yes. A virtual private network (VPN) can encrypt data and secure remote access to the company network, while XDR monitors for threats and coordinates detection and response. They serve different purposes but complement each other in a layered security strategy.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN