VPN vs. firewall: Key differences and when to use each



VPNs and firewalls are both tools that can help you maintain your security and privacy in the face of web-based threats. That said, they work in fundamentally different ways.
This guide will cover the differences between firewalls and VPNs, explaining what both technologies do and how they work. We'll explore the strengths and limitations of each and give advice on maximizing your security.
What is a firewall?
A firewall is a crucial component of any system’s network security. It essentially acts as a digital gatekeeper that monitors incoming and outgoing traffic, blocking or allowing data packets based on a set of predetermined security rules. Their main purpose is to secure a network. Specifically, they prevent unauthorized access and block malicious traffic from entering a system.
Types of firewalls
There are various kinds of firewalls, each designed to protect networks and devices in different ways. Understanding these types helps you choose the right firewall for your specific needs.
Software firewalls
Software firewalls are programs installed directly on a computer or server to protect that individual device. Firewalls are ubiquitous on personal devices, as they come pre-installed on all modern Mac and Windows computers. There are third-party options available, but most home users stick to the default option.
Compared to other options, software firewalls are easier to use, often requiring no more than a few clicks to set or adjust rules. Plus, those that come included with an operating system generally require no setup and work right out of the box.
Hardware firewalls
As the name suggests, hardware firewalls are physical devices. They generally sit between a system and the external network, filtering all traffic that passes by based on predefined rules. They work completely independently from the rest of the system, which means they don’t consume resources from the devices they protect.
While they’re more complex to set up due to the additional hardware, hardware firewalls offer various benefits. For instance, a single hardware firewall can secure an entire network, removing the need for each device to have a software firewall. Having a single point of operation also makes them easy to update.
Stateless vs. stateful firewalls
Firewalls also vary in terms of how they process network traffic. In this area, the main distinction is between stateless and stateful firewalls.
Stateless firewalls focus more on the parameters of data packets (small pieces of data transmitted over a network). They analyze, among other things, a packet’s source and destination. Acceptable parameters are determined by a network’s administrator, and any packet that doesn’t meet these is filtered out.
In contrast, stateful firewalls are much more thorough and thus tend to have higher resource demands. They look more closely at data packets, examining their channels of communication and behavior. This can help determine whether a packet is malicious, in which case it will automatically be filtered.
Both stateless and stateful firewalls can be implemented as either software or hardware solutions.
How does a firewall work?
A firewall operates by enforcing a set of predefined rules to filter network traffic. It serves as a gatekeeper between the system and the external network, ensuring malicious traffic isn’t allowed in. Firewalls can be configured around various criteria, including:
- IP addresses: Firewalls can be configured to filter packets that come from specific IP addresses (the unique identifiers assigned to every internet-connected device).
- Domain names: You can make it so firewalls block packets that come from specific domains that are known to be malicious or that you simply want to block.
- Ports: An admin can set a firewall to block traffic to certain ports, which can be thought of as “door numbers” that identify specific services or applications on a device.
 Benefits of using a firewallFirewalls provide a variety of security benefits in both personal and enterprise settings. Here are some of the most common uses for firewalls:
Benefits of using a firewallFirewalls provide a variety of security benefits in both personal and enterprise settings. Here are some of the most common uses for firewalls:
- Blocking unauthorized access: Firewalls defend against unwanted network intrusions by filtering malicious traffic.
- Preventing data leaks: Firewalls monitor both incoming and outgoing traffic, meaning they can help protect against data leaks by ensuring internal data isn’t transmitted outside the network. This is especially helpful for organizations with sensitive data.
- Enforcing policy: Firewalls can enforce specific rules for network traffic, giving granular control over what data can pass through. For example, you can use a firewall to control who can access a network and when they can access it and restrict access to certain sites or apps.
- Protecting against malware: Some advanced firewalls can detect and block malware and exploits by analyzing traffic patterns.
What is a VPN?
A virtual private network (VPN) is a service that provides a secure, encrypted connection to the wider internet. Connecting to a VPN creates a private tunnel for your online traffic, masking your activity from certain parties that could otherwise try to read your data. Additionally, VPNs hide your real IP address, adding an extra layer of privacy as you surf the web.
Compared to the security afforded by firewalls, VPNs are more privacy focused.
Types of VPNs
Looking more at use cases rather than fundamental technology, it’s possible to identify several types of VPNs. Here are some common categories:
- Personal VPN: Made for individual users to improve their privacy. Personal VPNs encrypt web traffic, increasing anonymity online by reducing your exposure to various privacy threats.
- Remote-access VPN: Designed to enable a secure, encrypted connection between a remote user's device and an organization's internal network. Companies often use these for employees working outside the office.
- Site-to-site VPN: Connect entire corporate networks with other networks using a secure gateway. They’re great VPNs for businesses with multiple offices scattered across various locations.
- Cloud VPN: Provide users with secure access to an organization’s cloud-hosted data remotely, regardless of their location. These are also known as hosted VPNs or VPN as a service (VPNaaS).
VPN Protocols
VPNs operate under various protocols. These constitute sets of rules that govern how data is encrypted and transmitted between a device and the VPN server. Though they accomplish broadly the same thing, different protocols stand out in different ways. Note that many VPNs support multiple protocols.
- Lightway: A proprietary protocol developed by ExpressVPN, Lightway maximizes security and privacy without sacrificing speed.
- OpenVPN: Open-source protocol notable for its high degree of configurability.
- WireGuard: Fast, open-source protocol meant to balance speed and privacy.
- IKEv2: Good speeds and is highly suitable for mobile devices.
- L2TP/IPSec: Secure but outdated and slower than modern protocols.
- PPTP: Outdated and insecure by today’s standards.
How does a VPN work?
VPNs work by routing your internet connection through a remote server operated by the VPN provider. When you connect to a VPN, your traffic passes through an encrypted tunnel that scrambles your data, making it unreadable to anyone trying to intercept it while in transit. This enhances online privacy and security by creating a layer between you and the rest of the internet.
Once your data reaches the VPN server, it essentially re-enters the internet from the server's IP address rather than your own. This effectively masks your real IP address from websites and services you visit.
Benefits of using a VPN
 There are many benefits to using a VPN, such as the following:
There are many benefits to using a VPN, such as the following:
- Enhancing privacy and safety: By masking your IP address and encrypting your traffic, VPNs promote online privacy.
- Avoiding throttling: Since ISPs can’t see what you’re doing when connected to a VPN (they can only see you’re connected to one), it makes it harder for them to throttle your connection speeds.
- Accessing local services: VPNs let you connect to servers in various countries, meaning you can securely access your local services without giving away your real IP address.
- Staying safe on public networks: Protect your data from threats like packet sniffing.
VPN vs. firewall: What's the difference?
While both VPNs and firewalls are essential cybersecurity tools, they’re fundamentally different things. Understanding their distinct functions will help you utilize both to their fullest.
Type of protection
The key difference between VPNs and firewalls is the kind of protection they provide. A firewall acts as a network perimeter defense, monitoring and managing both incoming and outgoing traffic based on security rules. They protect your device or internal network from unauthorized access.
In contrast, VPNs are made to secure data while it’s in transit. They do this by creating secure, encrypted tunnels for internet traffic, protecting data as it travels to and from your network. This obscures your online activities from prying eyes and enhances privacy on the internet.
Network layer
Firewalls operate on various layers of the OSI model, a conceptual model with seven layers that maps how devices communicate over a network. Firewalls can filter packets by destination or origin IP address, operating at layer 3 (network layer), and by TCP or UDP ports, operating at layer 4 (transport layer). They can also work at layer 7 (application layer) by inspecting packet contents and blocking any data deemed malicious.
The layers that VPNs operate on can vary depending on the protocol they use. For instance, VPNs using SSL operate on layer 4, the transport layer, and VPNs using IPSec sit at layer 3, the network layer. However, VPNs that use protocols like PPTP and L2TP operate on the data link level (layer 2). It’s worth noting that VPNs don’t fit into the OSI model as well as firewalls do.
Data encryption
Data encryption is a core function of most VPNs. The best VPNs use 256-bit AES encryption, a standard that has yet to be cracked. When you use an encrypted VPN, all your data will be scrambled as it is transmitted through the VPN tunnel, making it unreadable to third parties. This protects sensitive information from many types of eavesdropping and surveillance.
Firewalls, however, do not inherently provide data encryption. Their role is to filter traffic, not encrypt its content. They inspect packet headers and rules, regardless of whether the data is encrypted or not.
Customizability and access control
Firewalls offer extensive customizability in terms of access control rules. Administrators can define policies based on IP addresses, ports, and even geolocation. This allows a high degree of control over what traffic is permitted or denied access to the network.
Some VPNs offer customizability through choices like server location and protocols. But even the best options don't offer the same granular-level customization options that firewalls come with.
Performance and speed
Firewalls typically have a minimal impact on network performance and speed. Modern firewalls are optimized to process vast amounts of traffic quickly, with throughput reaching up to 1.5Tbps.
VPNs, however, can potentially reduce internet speed due to the encryption and decryption process. Depending on how far it is, the distance between you and the server your traffic is routed through can also be a factor. While top choices like ExpressVPN minimize this, some speed reduction may be expected.
Use cases: Personal vs. business
Firewalls are widely used in both home and business settings. Individual users rely on firewalls for device protection, while businesses implement firewalls to secure larger networks and data centers.
Similarly, VPNs serve both personal and business needs. Individuals use VPNs for privacy, security on public Wi-Fi, and to access the internet without local restrictions, among other things. Businesses may also use VPNs for privacy reasons, as well as for facilitating secure remote access for employees and connecting distributed office locations.
Table: Side-by-side comparison of VPNs and firewalls
The following table highlights the key differences between VPNs and firewalls:
| VPN | Firewall | |
| Primary function | Encrypting data and masking IP addresses | Blocking unauthorized access or network intrusions |
| Type of protection | Secures data during transit | Protects the perimeter of a network |
| Data encryption | Provides an encrypted tunnel for data | Doesn’t have any inherent encryption capabilities |
| Network layer |
|
|
| Impact on performance | Can cause a drop in connection speeds based on various factors | Has a minimal impact on performance |
| Customization | Server location and protocol | Firewall rules, ports, IP addresses, and more |
Should you use a VPN, a firewall, or both?
In most cases, you’ll want to use both. Firewalls and VPNs don’t tend to conflict with each other, and each provides things that the other does not.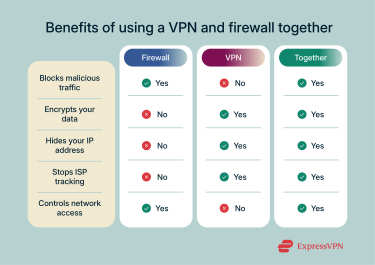
When to use a firewall
A firewall is essential for controlling network access and should be a crucial part of every system or network. As the gatekeeper to your network, a firewall can help prevent intrusions and certain types of web-based threats.
When to use a VPN
You should use a VPN when privacy and secure data transmission are your top priorities. A VPN encrypts your internet traffic and masks your IP address, improving your privacy online and helping prevent third parties from spying on your activity.
It’s also worth considering a VPN when you want to avoid potential ISP content throttling, bypass restrictive network blocks, or defend against DDoS attacks.
Using VPNs and firewalls together
VPNs and firewalls generally do not conflict with each other and are best used in tandem. Both solutions are technically different, improving security and privacy in distinct ways. With a firewall, you can reduce the risk of network intrusions and prevent unauthorized traffic from breaching your system. Alongside this, a VPN ensures that all traffic to and from your system is encrypted, thus safeguarding your privacy.
Limitations and risks of firewalls and VPNs
While both firewalls and VPNs are powerful security tools, they do have limitations. A firewall cannot encrypt your internet traffic or hide your IP address. It only controls access based on its rules, leaving your data vulnerable during transmission if not paired with a VPN.
VPNs primarily protect data in transit and help you stay private by masking your IP address. They do not remove malware or prevent further infections. Also, a VPN will not block unauthorized access to your device if it is directly exposed on a local network.
Fortunately, you can overcome many of the limitations of both these technologies by utilizing them simultaneously.
Are VPNs and firewalls compatible with all devices?
VPNs and firewalls are compatible with most devices, but there are a few caveats. Most Windows and macOS devices come pre-installed with a functional firewall, while mobile devices don’t tend to have them (though most have in-built features that offer similar protection). For many Linux distros, the operating system’s kernel itself will act as a configurable firewall. In any case, hardware firewalls can protect any device connected to the associated network.
High-end VPNs generally work with all devices as well. For instance, ExpressVPN offers native apps for Windows, macOS, Linux, and many other platforms. You can even install it on your router or buy Aircove, a router that comes with ExpressVPN already installed. Either option makes for an easy way to secure your entire network.
Cost comparison: VPNs vs. firewalls
The cost of firewalls can vary significantly. Basic software firewalls are included free with the major operating systems, but there are paid third-party solutions as well. Advanced hardware firewalls or enterprise-grade solutions can be expensive to purchase and maintain.
VPNs also vary in terms of costs. However, it’s wiser to look for one that gives you the best value for money rather than opt for the cheapest option. ExpressVPN, for instance, delivers excellent value for the price, providing a vast server network, reliable encryption, and a strict no-logs policy to ensure privacy.
FAQ: Common questions about VPNs and firewalls
What is the difference between a VPN and a firewall?
A VPN encrypts your internet traffic and masks your IP address, creating a secure tunnel for your data in transit. A firewall, on the other hand, doesn’t encrypt anything and instead acts as a digital barrier for your network, filtering incoming and outgoing traffic for threats based on security rules.
Can a VPN replace a firewall?
No, a VPN cannot replace a firewall. They serve different but complementary security functions. A firewall protects your network perimeter from unauthorized access, while a VPN secures your data and privacy across the internet.
Is a VPN a type of firewall?
No, a VPN isn’t a type of firewall, and they’re entirely different technologies. However, both are designed to improve your digital security, and using them simultaneously can significantly enhance online protection.
What do VPNs do that firewalls cannot do?
VPNs encrypt your online traffic and mask your IP address; firewalls can’t do either of those things. Additionally, they help prevent ISP throttling, prevent DDoS attacks, and more.
Can a firewall block a VPN?
Yes, a firewall could block traffic coming from a VPN. Since VPN servers have specific IP addresses, a firewall’s rules could be configured to stop all traffic originating from these IP addresses. It’s also possible to configure a firewall to block the ports VPNs use.
How do I know if my firewall is blocking my VPN?
Your firewall might be blocking your VPN if it consistently disconnects. If you temporarily disable your firewall and the VPN connects without issues, it’s likely that it’s blocking your VPN. To resolve this, look for rules that might be blocking the VPN client or its specific ports. You may need to add an exception for your VPN application within the firewall settings
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN

















Comments
You failed to mention what VPN's work with a firewall. I do have a ExpressVPN subscription but needed to deactivate the firewall to activate it, which proved to be problematic and destruction to my continued cell phone use.
This seems somewhat helpful but am not sure how to get to the "firewall" itself to address the vpn issue.
I am very disappointed that my vpn is affecting my proper use of my fire stick and my roku device ...this is a really big issue for me. How do I resolve it????