Blue team vs. red team cybersecurity: Comprehensive guide
Organizations often invest heavily in cybersecurity controls, yet still struggle to test how these controls hold up against adversary-style activity and turn findings into sustained improvement. A common way to structure that testing is through red team and blue team exercises, which help teams move beyond assumptions and checklist compliance toward evidence of how defenses perform.
This guide explains when and why to use red and blue teaming, how to plan and govern exercises safely, and what outcomes and deliverables to expect. It also covers which metrics help track progress over time, so results translate into prioritized remediation and measurable security improvements.
What are red and blue teams in cybersecurity?
In cybersecurity, red teams and blue teams are two complementary functions used to evaluate and strengthen an organization’s security posture.
A red team takes an attacker’s perspective to test how well systems, people, and processes perform against real-world attack techniques. A blue team focuses on defence, detecting, responding to, and preventing security threats as part of ongoing operations.
Together, they support the same goal of reducing risk by identifying weaknesses, improving detection and response, and hardening defenses over time.
Definition and roles of red teams
According to the U.S. National Institute of Standards and Technology (NIST), a red team is an authorized and organized group that simulates how a real attacker might attempt to compromise an organization’s security.
The objective of a red team is to demonstrate what a determined attacker could achieve and to reveal which defenses work in practice and which do not. Red teams may be internal staff or external specialists conducting authorized, ethical attack simulations. They typically gather intelligence on the environment, identify potential weaknesses, and attempt to exploit them using tactics that mirror those of real adversaries.
After an engagement, red teams typically deliver a report documenting the attack paths, techniques used, and the conditions that enabled success, often accompanied by recommendations for mitigation. These outputs provide concrete, evidence-based guidance for security and engineering teams to address the most consequential gaps.
Because red team activity can carry legal and operational risk, it is governed by defined rules of engagement, scope boundaries, and explicit authorization. Engagements are usually time-bounded (often structured as a short campaign over days or weeks), and success is measured against agreed objectives, such as reaching sensitive data, escalating privileges, or demonstrating control over a critical system.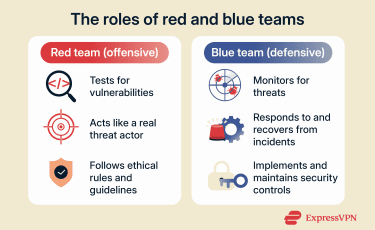
Definition and roles of blue teams
The NIST defines a blue team as “the group responsible for defending an enterprise’s use of information systems by maintaining its security posture against a group of mock attackers (i.e., the red team)”.
Blue teams operate continuously, often from a security operations center (SOC), and are responsible for day-to-day defense. Their core work includes monitoring telemetry (a system that collects, retrieves, and analyzes data to provide insight into how a system is performing), detecting suspicious activity, investigating alerts, coordinating incident response, and supporting recovery and hardening efforts.
During exercises and real incidents, blue teams follow documented processes to triage, contain, eradicate, and recover. They also document gaps and areas for improvement. Remediation is usually implemented by the teams that own the affected systems (security engineering, IT, platform, or product teams), with leadership helping prioritize and fund the work.
Importantly, blue team responsibilities extend beyond red team engagements. The same capabilities used to respond to simulated activity are also used to detect and respond to real threats in production.
Learn more: Read our simple guide on cybersecurity.
Red team exercises
Red team exercises often simulate realistic threat campaigns to assess an organization’s defenses. These engagements chain multiple techniques to emulate how real adversaries operate.
Types of red team exercises
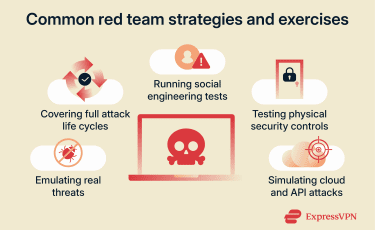
Red team activities vary based on the environment, threat profile, and the engagement's objectives. While there is no universal set of exercises, common red team formats include:
- Adversary emulation: Red teams model the behavior of specific threat actors using publicly documented tactics and procedures, often mapped to frameworks such as MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK), to assess how defenses perform against realistic campaigns. Scenarios may focus on ransomware, nation-state activity, insider threats, or other relevant adversaries.
- Full‑scope engagements: These exercises cover the end-to-end attack lifecycle to identify complex attack paths across networks, applications, and cloud environments. They often test coordination across multiple teams and may include tightly controlled use of tooling to simulate advanced techniques.
- Social engineering tests: Phishing and related techniques assess how employees respond to suspicious messages and requests. These exercises are common because social engineering remains one of the most frequent and effective initial access methods.
- Physical penetration: Some engagements assess physical security controls by attempting to access facilities, bypass entry procedures, or place unauthorized devices. These activities require explicit authorization and strict safety and legal controls.
- Cloud and API exercises: Red teams evaluate cloud-specific risks such as misconfigurations and overly permissive identity and access management (IAM) policies. Exercises may include attempts to abuse cloud permissions, expose APIs, and weak credential controls to validate the cloud defensive posture, particularly in environments designed around zero-trust cloud security principles.
Common red team tools and techniques
Red teams use a mix of open-source and commercial tooling to evaluate security controls across common attack surfaces. The exact tooling varies by scope, environment, and objectives, but activities often fall into the following categories:
- Reconnaissance and enumeration: Identifying exposed services, configurations, and pathways that may increase attack surface.
- Access and execution: Testing whether security controls prevent or detect unauthorized actions under defined conditions.
- Privilege and lateral movement simulation: Evaluating segmentation, identity controls, and monitoring by simulating how access could expand across systems.
- Credential exposure assessment: Assessing whether credential material can be accessed or misused, and whether detection and protection measures are effective.
- Reporting and evidence collection: Documenting observed gaps, defensive blind spots, and prioritized remediation actions with supporting evidence.
Blue team strategies
Blue team defense is built on preventive controls, continuous monitoring, and coordinated incident handling.
Defensive security measures
Blue teams use multiple strategies, often in parallel, to reduce the attack surface and limit the impact of successful compromise:
- Defensive cyber operations: Layered controls to reduce exposure across identity, endpoints, and networks.
- Patch and configuration management: Regular patching and secure configuration baselines to address known vulnerabilities and reduce preventable misconfigurations.
- Identity and access controls: Role-based access control (RBAC), multi-factor authentication (MFA) on critical systems, secure remote access, and least-privilege policies to limit the impact of a compromised account.
- User training and awareness: Ongoing training and simulations focused on phishing and social engineering, paired with clear reporting channels and verification practices for unexpected requests.
Monitoring and detection tools
To support detection and response, blue teams commonly rely on:
- Security information and event management (SIEM): Platforms that collect and normalize security telemetry, correlate events across systems, and support alert triage and investigation.
- Intrusion detection system/intrusion prevention system (IDS/IPS): Tools that detect suspicious activity and, for prevention systems, block or disrupt malicious traffic or behavior. These can be network-based or host-based, depending on deployment.
- Endpoint detection and response (EDR): Tools that collect endpoint telemetry, raise alerts on suspicious behavior, and support investigation and response actions.
- Cloud activity and audit logging: Native cloud logs are used to detect suspicious API calls, unusual administrative activity, and risky configuration changes.
- Threat intelligence platform (TIP): Systems used to collect, organize, and share indicators and threat context to improve detections and investigations.
Incident response and recovery
Incident response typically follows a structured lifecycle from preparation through recovery, with post-incident improvement as a core outcome.
Blue teams coordinate incident handling across triage, containment, eradication, and recovery, using documented playbooks and communication paths. Effective recovery goes beyond restoring services: it includes root-cause analysis, control improvements, and follow-up actions to reduce the chance of recurrence.
Outputs from red team exercises (such as timelines, alert data, and observed response actions) can help validate which processes hold up under realistic conditions and where procedures need refinement before a real incident occurs.
NIST Cybersecurity Framework (CSF) 2.0 emphasizes governance and preparation activities, alongside the identify, protect, detect, respond, and recover functions, with continuous improvement embedded across them.
The role of VPNs in red and blue team cybersecurity
Corporate virtual private networks (VPNs) are commonly used to provide secure remote access for distributed teams, supporting both day-to-day defensive operations (blue teams) and authorized security testing activities (red teams).
How corporate VPNs protect network traffic from interception
A corporate VPN creates an encrypted tunnel between a user’s device and the organization’s VPN gateway. This helps protect sensitive data in transit across untrusted networks (e.g., public Wi-Fi) and reduces the risk of interception between the device and the corporate VPN endpoint.
Traffic is encrypted up to the VPN gateway; protection beyond that point depends on additional controls, such as Transport Layer Security (TLS), used for the destination connection.
From a blue team perspective, corporate VPN authentication and session telemetry can also support monitoring and investigation of remote access activity. From a red team perspective (during authorized engagements), corporate VPN configurations and logging may be assessed to validate remote access controls and visibility.
Securing remote testing and pentesting operations
Both red and blue teams often work remotely when conducting assessments or responding to incidents. A corporate VPN provides a controlled remote-access path that helps protect security tooling traffic from interception on untrusted networks and supports consistent authentication and logging.
For example, red teams connecting to a client environment through a corporate VPN can reduce exposure when working off-site. Blue teams can use a corporate VPN to maintain secure access to internal monitoring systems and administrative consoles when operating from external locations.
Benefits of red and blue team integration
Integrating red and blue teams helps organizations turn testing into measurable defensive improvement. Instead of treating exercises as “us vs. them,” teams align on shared objectives and use results to strengthen detection, response, and remediation.
Many organizations describe this collaboration as purple teaming: a structured way for red and blue teams to coordinate during exercises, share observations in real time, and validate that changes actually improve detection and response.
Enhanced security posture
Integrated exercises create faster learning cycles. Red team activity provides concrete examples of attacker behavior, while the blue team validates what was detected, what was missed, and how response actions were performed. This makes it easier to tune detections, improve playbooks, and address gaps while the context is still fresh.
Over time, organizations can show progress using evidence-based metrics such as mean time to detect (MTTD), mean time to contain (MTTC), detection coverage improvements, and remediation closure rates.
Continuous improvement mechanisms
Red and blue team work is most effective when it is ongoing. Each engagement should build on previous findings, focusing on whether prior fixes reduced risk and whether monitoring and response capabilities improved. Tracking results across engagements helps identify persistent weaknesses and supports targeted investment decisions.
Strengthening organizational security culture
Integration also reduces friction between teams by normalizing shared planning and clear communication. When findings are treated as inputs for improvement rather than performance failures, teams are more willing to surface issues early and prioritize remediation, reinforcing a continuous-improvement mindset.
FAQ: Common questions about blue team vs. red team
Is the security operations centre (SOC) analyst red team or blue team?
SOC monitoring analysts are part of the blue team. They don’t conduct offensive testing like the red team; instead, they analyze networks for malware and suspicious activity and coordinate recovery in the event of attacks.
What are the roles and responsibilities of red and blue teams?
Red teams simulate realistic attacks to uncover weaknesses and provide evidence that helps organizations understand risk. Blue teams defend the organization by monitoring, detecting, investigating, and responding to threats, then improving controls based on what they learn.
How do red and blue teams perform exercises?
Red team exercises typically involve structured phases such as planning, reconnaissance, exploitation, post-exploitation activities, and agreed-upon cleanup steps. Blue teams monitor for and respond to these simulated attacks during or after the exercise, depending on its design, documenting observations and, where applicable, detection and response metrics.
What tools do red teams use?
Red teams use a range of tools to identify potential entry points, attempt access through techniques such as credential abuse or vulnerability exploitation, and simulate defense-evasion behaviors to evaluate the effectiveness of blue team detections and controls.
What measures can blue teams implement to strengthen defenses?
Blue teams employ layered defenses such as identity hardening, least privilege, and endpoint detection. They also handle patch management (prioritizing updates for known risks), user training, and configuring network tools, such as corporate VPNs, for secure remote access.
How can organizations facilitate better communication between red and blue teams?
Organizations can improve red–blue communication by setting shared objectives and success criteria up front, agreeing on clear rules of engagement and escalation paths, and creating regular touchpoints during and after exercises to compare what was attempted, what was detected, and what actions were taken.
The most effective programs also standardize reporting and handoffs so that findings translate into tracked remediation work, and they reinforce a security culture in which issues are treated as improvement opportunities rather than as blame.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN