Advanced persistent threats (APT): What you need to know
Unlike many cyberattacks that aim for quick data theft or disruption, some are designed to remain hidden for months or even years. During that time, attackers quietly monitor systems, collect sensitive data, and expand their access. These long-running intrusions are known as advanced persistent threats (APTs).
APTs are usually highly targeted attacks, carefully planned and deliberately stealthy, which often makes them difficult to detect using traditional security tools.
What is an APT in cybersecurity?
An APT is a targeted cyberattack where an unauthorized user gains access to a network and maintains that access for an extended period, often without detection.
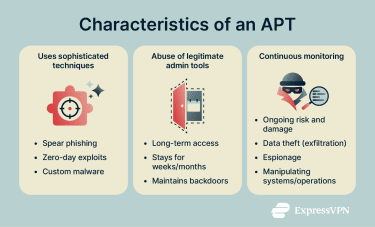
The term "advanced persistent threat" describes the core characteristics of these attacks.
- Advanced: Reflects the use of sophisticated techniques, such as spear-phishing, zero-day exploits, malware, credential theft, and the abuse of legitimate admin tools.
- Persistent: Indicates that the attack is long-term, with attackers maintaining continuous access to the target network.
- Threat: Reflects the sustained risk it poses, especially when attackers are able to observe systems, exfiltrate sensitive data, or manipulate operations over time.
APTs are typically carried out by well-resourced and sophisticated cybercriminal organizations. The attackers usually have specific objectives in mind, such as cyber espionage, intellectual property theft, or disruption of critical infrastructure. Because of this, APTs frequently target high-value entities like government agencies, defense contractors, financial institutions, and large corporations.
How APT attacks work
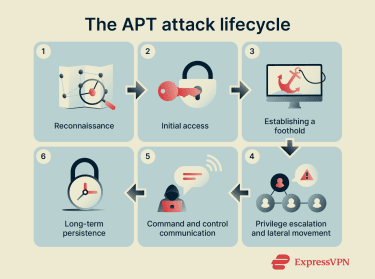
Many APTs follow a recognizable pattern, often referred to as the APT attack lifecycle. A typical APT attack involves the following stages:
- Reconnaissance: Attackers research the target to understand its network structure, security controls, and potential weaknesses.
- Initial access: Attackers gain entry by exploiting a software vulnerability, using stolen credentials, or tricking someone into granting access, such as through a phishing email.
- Establishing a foothold: Malware, backdoors, or other tools are deployed to maintain access without drawing attention.
- Privilege escalation and lateral movement: Attackers attempt to gain higher-level permissions and move through the network to reach more valuable systems.
- Command and control (C2) communication: Compromised systems communicate with external servers to receive instructions, download additional tools, or exfiltrate data. This traffic is often disguised to blend in with normal network activity.
- Long-term persistence: Attackers work to remain inside the organization for as long as possible, adapting their techniques to avoid detection and reestablish access if parts of the intrusion are disrupted.
Real-world implications of APTs
The impact of an APT is often discovered only after attackers have spent significant time inside a network. By the time an intrusion is detected, attackers may have accessed sensitive systems, monitored internal communications, or expanded their reach. This delayed discovery can make remediation more complex and costly.
The consequences may include:
- Data exposure: Intellectual property, trade secrets, internal documents, classified information, or personal data may be quietly exfiltrated over time.
- Operational risk: Long-term access can allow attackers to disrupt critical systems or business processes. For example, the 2015 attack on Ukraine's power grid demonstrated how APTs against critical infrastructure can cause widespread disruptions affecting hundreds of thousands of people.
- Financial and reputational damage: Organizations often incur financial losses and costs related to incident response, system remediation, legal fees, and regulatory fines. Reputational damage may erode customer trust and affect stock prices where applicable.
Notable APT groups and real-world attacks
Several well-documented APT groups have conducted high-profile operations that illustrate the methods and impacts of these attacks. These groups are typically identified by consistent tooling, tactics, and long-running campaigns rather than by a single attack.
APT28 (Fancy Bear)
APT28, also known as Fancy Bear, Pawn Storm, Sofacy, Sednit, STRONTIUM, and others, is a threat actor that has conducted targeted cyber espionage campaigns against various government institutions, military organizations, and political entities since at least 2004.
The group gained significant attention after multiple security firms linked it to the 2016 Democratic National Committee breach.
APT28’s tactics typically involve a combination of credential theft, targeted phishing, exploitation of public-facing services, and long-term persistence inside compromised networks. Rather than relying on a single intrusion method, the group adapts its techniques based on the target environment and gradually expands access over time.
APT29 (Cozy Bear)
APT29, commonly referred to as Cozy Bear, is another threat actor that focuses primarily on long-term intelligence gathering.
The SolarWinds supply chain attack, discovered in December 2020, is one of APT29’s significant operations. By inserting malicious code into legitimate software updates, the attackers gained access to thousands of organizations that installed the compromised software.
Security researchers from Microsoft tracked how APT29 used this access to conduct selective follow-on operations, targeting specific high-value networks for deeper intrusion. The attack remained undetected for months, allowing extensive reconnaissance and data collection.
APT29 has also been linked to campaigns targeting COVID-19 vaccine research. Security agencies in the U.S., U.K., and Canada reported attempts to steal research data from pharmaceutical companies and academic institutions developing vaccines and treatments.
Lazarus Group
Active since at least 2009, the Lazarus Group is linked to a wide range of cyber operations affecting financial institutions, technology companies, and critical infrastructure.
In 2014, the group attacked Sony Pictures Entertainment and exfiltrated confidential data, including unreleased films, employee information, and internal communications.
The group was also responsible for the 2016 Bangladesh Bank heist, which involved compromising the bank's systems and attempting to transfer nearly $1 billion through fraudulent SWIFT messages.
The WannaCry ransomware, which affected hundreds of thousands of computers globally in 2017, showed connections to Lazarus Group tools and infrastructure. The ransomware exploited a Windows vulnerability to spread rapidly across networks, encrypting files and demanding payment.
Cryptocurrency exchanges have become frequent targets of Lazarus. The group has stolen hundreds of millions of dollars' worth of digital assets through exchange compromises.
Recent Lazarus operations have targeted the technology sector, with campaigns against cryptocurrency platforms, blockchain companies, and software developers. The group uses sophisticated social engineering to deliver malware to specific individuals at target organizations.
Protecting against APT attacks
Effective protection against APTs relies on layered defenses, continuous monitoring, and well-prepared response processes.
Effective prevention strategies for APT threats
Preventing APTs from gaining a foothold usually starts with reducing opportunities for initial access and limiting what attackers can do if they gain entry.
Common prevention measures include:
- Attack surface reduction: Keeping systems updated, removing unused services, applying patches, deploying firewalls, and limiting exposed entry points reduces the number of vulnerabilities attackers can exploit.
- Strong identity and access controls: Enforcing least-privilege access (meaning users only get access to the systems and data they actually need for their roles) and using multi-factor authentication (MFA) helps contain damage if credentials are compromised.
- User awareness and training: Many APT campaigns begin with targeted social engineering. Educated users are better equipped to spot suspicious messages or requests.
- Network segmentation: Separating critical systems limits lateral movement, making it harder for attackers to quietly expand access. Even if attackers breach one device or section of the network, they can’t easily jump to more sensitive systems.
- Email security measures: Advanced email gateways can scan links and attachments, block known threats, and, in some setups, sandbox suspicious files. Organizations can also implement domain-based message authentication protocols to prevent email spoofing.
These steps don’t eliminate the risk of APTs, but they make it more difficult for them to establish and maintain stealthy, long-term access.
Advanced detection techniques for identifying APT activity
APTs try to blend in with normal behavior, so early detection often depends on spotting subtle anomalies rather than obvious signs of malware infection. This is where advanced monitoring and behavioral analysis become particularly useful.
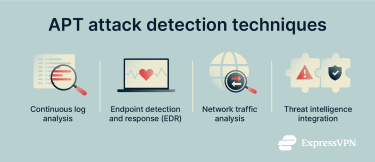
Detection techniques commonly used against APTs include:
- Continuous log analysis: Reviewing authentication logs, file and data activity, and system events can reveal unusual and suspicious patterns. For example, if an employee account starts downloading large amounts of data, logging in from new locations, or accessing systems they have never used before, it could be a sign of compromise.
- Endpoint detection and response (EDR): EDR tools monitor devices such as laptops, desktops, and servers for signs of malicious activity, such as abnormal process execution, registry changes, or attempts to escalate privileges.
- Network traffic analysis: Identifying irregular outbound connections or C2 communication can reveal signs of an active breach. For instance, encrypted traffic to unexpected destinations, unusual data volumes during off-hours, or connections to known malicious infrastructure could point to C2 communication.
- Threat intelligence integration: Comparing internal activity against known APT indicators, such as suspicious IP addresses, domains, or malware behavior, provides additional context for investigation.
Incident response and containment best practices
Even with strong prevention and detection, some threats may still bypass defenses. A clear incident response plan is critical for limiting the impact of an APT once it’s discovered. The incident response plan assigns specific roles to team members, establishes communication protocols, and defines escalation procedures.
Key incident response practices include:
- Rapid isolation: Affected systems should be segmented or taken offline to prevent further movement. However, containment should be balanced with the need to preserve evidence for forensic analysis.
- Thorough investigation: A forensic investigation should be conducted to determine the attack's scope and identify which systems were compromised, what data was accessed, and how long the attackers maintained access. This information guides both immediate remediation and long-term security improvements.
- Eradication and recovery: Backdoors, compromised credentials, and persistence mechanisms must be eliminated before restoring systems. In severe cases, rebuilding compromised systems from clean backups or fresh installations may be necessary.
- Post-incident review: This examines what enabled the attack and what the response revealed about security gaps. The analysis should inform updates to security policies, technology deployments, cybersecurity spending, and response procedures.
How enterprise VPNs reduce exposure to APT threats
Enterprise VPNs can help reduce certain exposure points associated with APTs, particularly during remote access and early-stage intrusion activity. Their role is to limit unnecessary visibility into internal networks, protect data in transit, and reduce overall network exposure in distributed and remote environments.
Encrypting corporate and remote workforce traffic
Remote access increases risk if connections and access controls aren’t properly secured. Without encryption, sensitive data moving between endpoints, cloud services, and internal systems may be exposed to interception or passive monitoring.
Enterprise VPNs encrypt corporate traffic when employees work outside the office, reducing an attacker’s ability to observe internal communications or profile network behavior. This protection is especially relevant during the reconnaissance and early data collection stages of an APT attack, when visibility into traffic patterns can help attackers understand system roles and trust relationships.
Controlling access in distributed environments
Distributed organizations with multiple office locations, cloud services, third-party connections, and remote workers typically present multiple entry points for APT groups to target. This is especially true when these locations contain devices that are easy to overlook, such as internet-connected printers, smart cameras, or access control systems.
To avoid unnecessary exposure, organizations can require authenticated enterprise VPN connections before granting access, making internal infrastructure harder to discover and direct attacks against internal endpoints more difficult.
FAQ: Common questions about advanced persistent threats
Is APT malware?
An advanced persistent threat (APT) isn’t the same as malware. Malware may be used as part of an APT campaign, but an APT refers to the overall approach and characteristics of the attack: advanced techniques, persistent access, and the threat posed to the target organization.
APT attackers typically deploy custom malware tailored to their targets. This malware helps them establish initial access, maintain persistence, move laterally through networks, and exfiltrate data. However, APT campaigns also involve non-malware techniques like exploiting legitimate system administration tools, using stolen credentials, and social engineering.
What is an example of an APT?
The SolarWinds supply chain attack is a notable example of an advanced persistent threat (APT) operation. Attackers compromised software updates for the company’s widely used Orion IT monitoring platform, inserting malicious code that gave them access to thousands of organizations. Once inside target networks, they conducted operations against high-value entities. The attack remained undetected for months.
How long do APT attacks last?
Advanced persistent threat (APT) attacks can last from several months to multiple years. The duration depends on the attackers' objectives and how long they can maintain access without detection. Some APT groups have remained in target networks for over a year before being discovered. The attack lifecycle itself unfolds over weeks or months as attackers progress through reconnaissance, initial compromise, establishing persistence, lateral movement, and data exfiltration.
What is the main characteristic of an advanced persistent threat?
The defining characteristic of an advanced persistent threat (APT) is sustained, stealthy access to a target network over an extended period. Instead of causing immediate damage, attackers focus on staying hidden while steadily pursuing a specific objective.
APTs are also characterized by their targeted nature. Attackers select specific organizations or individuals based on the value of their data or systems. The "advanced" aspect refers to the sophisticated techniques employed, including custom malware, zero-day exploit usage, and adaptation to the target's specific security environment.
How do organizations prepare for APT attacks?
Organizations can prepare for advanced persistent threat (APT) attacks by combining strong prevention, detection, and response practices. This typically includes reducing the attack surface, enforcing least-privilege access, implementing network segmentation, continuously monitoring systems, and maintaining a tested incident response plan.
What tools can prevent APT attacks?
No single tool can prevent advanced persistent threat (APT) attacks, but several technologies can contribute to defense. Protection usually relies on a combination of endpoint security, network monitoring, access controls, email filtering, firewalls, intrusion prevention systems (IPSs), threat intelligence, and user training. These tools work together to reduce risk and improve early detection.
Why are APTs a threat to businesses?
Advanced persistent threats (APTs) pose a threat to businesses by stealing intellectual property, trade secrets, and competitive intelligence. Companies can lose years of research and development work, giving competitors or adversaries significant advantages. Businesses could also face financial losses, disrupted operations, and reputational damage from APT incidents.
The sophisticated nature of APTs means traditional security measures may not detect them, allowing attackers to maintain extended access and cause maximum damage.
Does a VPN help protect against APT-related risks?
An enterprise VPN can reduce certain risks that advanced persistent threat (APT) groups may exploit. For organizations with remote workers, VPNs provide encrypted connections to corporate resources, making it more difficult for attackers to monitor traffic or conduct reconnaissance.
However, VPNs don’t provide comprehensive protection against APTs. They are most effective when used as part of a broader, layered security approach.
How long can an APT remain undetected?
An advanced persistent threat (APT) can remain undetected for extended periods, sometimes months or years, depending on the sophistication of the attackers and the target organization's detection capabilities. This is because attackers intentionally use low-noise techniques that blend in with normal system activity.
Organizations with robust security monitoring, behavioral analysis capabilities, and active threat-hunting programs are more likely to detect APT activity quickly compared to those relying solely on traditional signature-based defenses. Even with strong detection systems, the stealthy nature of APT operations means some level of access may have already occurred before discovery.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN