Should you pay the ransom? What to consider before deciding
A ransomware attack can feel like a ticking time bomb. Files are locked, there’s a deadline in the ransom note, and paying can look like the fastest solution. But it’s a high-stakes decision, and it’s rarely as simple as “pay, and everything’s fixed.”
Authorities generally discourage ransom payments because such payments support criminal operations and don’t guarantee the recovery of access to affected data.
Weighing whether to pay ransomware involves time pressure, money concerns, and significant stress. This guide breaks down what to consider when facing a ransomware demand and the potential consequences of either decision.
Understanding the ransomware dilemma
Ransomware introduces a brutal trade-off. Paying the ransomware demand might result in a decryptor or key that restores access, but it would fund criminals and signal that cyber extortion works, and it might not fully restore data or systems. Refusing to pay may result in prolonged downtime, loss of access to critical files, and major disruption to work processes.
Why victims consider paying
Ransomware attacks aim to maximize pressure. Several factors can drive victims toward payment:
- No clear recovery path: Without recent backups, or when backups are encrypted or destroyed, paying may seem the only viable option to recover critical files.
- Business-critical downtime: When a shop can’t take payments, a clinic can’t access records, or a team can’t do its work, every hour offline adds financial and operational pressure.
- Data leak threats: Many ransomware groups now threaten to publish stolen data if they don’t receive the ransom, which raises the stakes for organizations handling sensitive information.
- A “numbers” decision under stress: Some organizations do a cost analysis of their options (ransom amount vs. outage and recovery costs) and decide that paying is the cheaper option.
- Stakeholder pressure: Demand for a quick resolution from customers, investors, leadership, or partners can push decision-makers toward paying to avoid immediate damage.
None of these reasons makes paying safe, but they explain why it might feel like a legitimate decision in the moment.
Risks of paying the ransom
While this may seem counterintuitive, paying a ransom can make recovery more expensive and less predictable. Once money changes hands, attackers retain full control over what happens next, and the outcome becomes even more uncertain.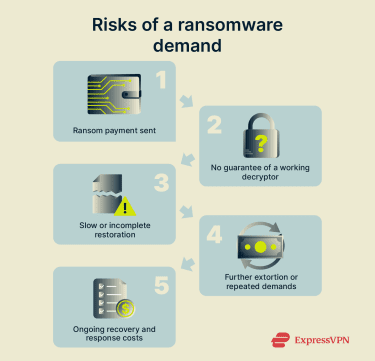
No guarantee of data recovery
Paying the ransom is not a reliable way to get your files back. Attackers may promise a decryption key, but nothing forces them to deliver a working one. In some cases, no key is provided at all. In others, the key only partially decrypts files, leaving data corrupted or unusable.
Even when decryption works, recovery may not be complete. Victims might need to validate files, rebuild systems, and adjust access controls to remove lingering risk. As a result, bringing operations back on track may take longer than expected.
There’s also a timing risk. Decryption tools supplied by ransomware attackers can be slow or unstable, which can mean days or weeks of continued downtime even after payment.
In short, a ransom payment might buy a chance, not a result.
Legal and financial consequences
A ransom payment can create legal and financial fallout that lasts long after systems are restored. Because the legal risks can be complex and depend heavily on the circumstances, it’s important to consult legal counsel early, especially before making any payment or engaging a third party to negotiate or facilitate it.
On the legal side, the big risk is who the victims are paying. In the U.S., sanctions rules can apply to parties subject to U.S. jurisdiction even when a payment is made under pressure. If money ends up going to a sanctioned person or entity, the victim might face penalties, even if they didn’t know the payment went to such a party.
In some scenarios, paying the ransom can be costly in unexpected ways. The payment may not erase the need for incident response, security upgrades, or legal support, all of which require investments.
Funding future attacks
Each payment feeds the wider ransomware economy and helps sustain the groups behind these attacks. Ransomware depends on payments to remain profitable. The success of one operation reinforces the model and signals that targeting similar organizations is worth the effort.
Moreover, attackers might perceive organizations that pay as more likely to negotiate, which increases the odds of repeat incidents, either from the same group (including renewed threats around stolen data) or from others over time.
Alternatives to paying ransomware
Paying may seem like the only way out of a ransomware incident. But it may not be. There are several recovery paths worth trying first.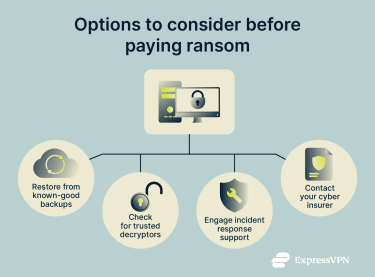
Data recovery options
The right recovery path depends on what the ransomware did (encryption only vs. data theft) and what remains accessible. Consider these options:
- Restore from backups you trust: If you have recent backups that weren’t affected, recovery may be as simple as wiping or rebuilding infected devices after confirming the intrusion is contained, then restoring clean copies.
- Check for free decryption tools: Some ransomware strains have known decryptors. Projects like No More Ransom exist to help victims recover encrypted data without paying, and they maintain free tools for certain infections.
- Confirm what’s actually encrypted: Sometimes only specific folders, drives, or devices are affected. A quick inventory helps you avoid unnecessary rebuilds and focus on what matters most first.
- Preserve what you can before making changes: If you still have access to logs, ransom notes, file extensions, and any indicators of compromise, keep copies of them. This can help with law enforcement reporting and identifying whether a decryptor exists.
None of these steps guarantees successful recovery. Still, they’re worth trying before defaulting to payment.
Working with incident response teams
Ransomware incidents rarely affect just one device or folder. An incident response team helps determine how far the attack actually spread, which systems were affected, and whether attackers still have a foothold in the environment.
That assessment matters because restoring systems too early (before confirming the attackers no longer have access or persistence mechanisms) can reintroduce the threat. Attackers can regain control if teams restore files without first identifying persistence mechanisms, stolen credentials, or remote access paths.
Incident response teams also bring structure to a chaotic situation. They help prioritize what to investigate and restore first, preserve evidence for later review, and coordinate technical actions with business decisions. This reduces guesswork and prevents rushed or uninformed decisions from creating new problems.
Organizations without in-house response teams should work with vetted cybersecurity firms rather than engage unverified third parties.
Cyber insurance
Cyber insurance coverage and conditions vary widely, and understanding what a policy actually supports matters as much as having one in place.
Some policies might cover response efforts, such as cybersecurity consultant services, forensic investigations, legal support, or business interruption losses. This can help to introduce experienced help quickly and offset immediate financial pressure.
However, policies may have caps, exclusions, and procedural requirements that limit what's actually reimbursed. In some cases, insurers may demand notification or approval before teams take certain actions, which can delay critical decisions.
Reporting to law enforcement
Some victims don’t report the incident because they think it would pause recovery. In many cases, reporting can happen in parallel with response and recovery, but it doesn’t guarantee a quick solution either.
The main reason to report such incidents is to provide investigators with details that can prevent future attacks by helping them identify patterns across campaigns and track criminal infrastructure. Reporting may also provide access to technical support, including guidance on specific ransomware variants and, occasionally, decryption assistance if tools or keys exist.
Regardless of location, consider reporting through the most appropriate channel in your country, local law enforcement, a national cyber reporting body, or a relevant regulator. In the U.S., the FBI's Internet Crime Complaint Center (IC3) and the Cybersecurity and Infrastructure Security Agency (CISA) provide dedicated reporting channels for ransomware incidents.
How to help prevent future attacks
Ransomware recovery is usually harder than ransomware prevention. The goal is to make an attack less likely to succeed and easier to bounce back from if it does. That starts with creating backups you can trust and minimizing entry points.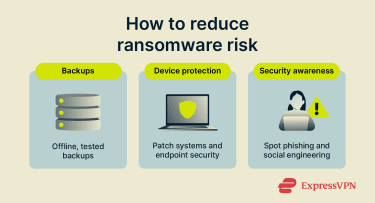
Implementing backup strategy (3-2-1 rule)
Backups can prevent a ransomware incident from becoming a total loss. A widely recommended framework is the 3-2-1 rule:
- 3 copies of important data (one primary copy and two backups).
- 2 different storage approaches to avoid a single point of failure, such as hard drives and tape, or disk and cloud.
- 1 copy stored off-site. For ransomware resilience, ideally offline or otherwise isolated/immutable, so it can’t be accessed or encrypted by malware spreading through networks or cloud connections.
Finally, backups are only useful if they work. Regular testing ensures that when you need to recover, you aren’t surprised by corrupted or misconfigured files.
Maintaining endpoint protection and patching
Regularly updating operating systems, applications, and firmware reduces the number of entry points attackers can exploit. Delays in applying patches often give attackers an easy path in, especially when exploits are already circulating publicly.
Endpoint protection software, like antivirus can identify suspicious activity and known malware. They work best when configured to update automatically and run regular scans so they respond to current threats rather than outdated signatures.
Together, patching and endpoint protection reduce the risk that a single missed update or malicious file escalates into a full-scale ransomware incident.
Building security awareness
Many ransomware infections start with routine interactions, such as a convincing email, a fake login page, or a message pressuring someone to act quickly. Security awareness helps people recognize those signals before they escalate into incidents.
Awareness efforts work best when they’re ongoing and practical. Short, regular reminders, clear examples of current tactics, and a simple way to report suspicious messages can improve response without overwhelming people.
FAQ: Common questions about paying ransomware
Is it ever legal to pay a ransom?
Sometimes, but legality depends on jurisdiction and who ultimately receives the money. In the U.S., paying a ransomware demand isn’t automatically illegal, but victims (and facilitators) may face penalties if the recipient is a sanctioned party, and civil liability can apply even if the payer didn’t know who received the funds. If a victim is considering paying a ransomware demand, they should treat it as a legal decision as much as a technical one and get qualified legal advice first.
What if I don’t pay a ransom?
Not paying a ransom can lead to longer operational disruption, a more difficult recovery, and possible data loss, including the risk that stolen data is leaked or misused. Still, authorities generally discourage paying because it supports attackers and still leaves the outcome uncertain. Paying also doesn’t guarantee the victim will regain access.
Can I recover data without paying?
Sometimes. Recovery without payment is possible through clean backups or by using decryption tools for certain ransomware strains. The first step is to preserve key details, like the ransom note and file extensions, then identify the ransomware family and check whether a legitimate decryptor exists for it, such as those listed by No More Ransom.
Are ransom payments traceable?
They can be, even though ransomware demands are often paid in crypto. Traceability varies by currency and laundering steps, and tracing a payment doesn’t always mean the payer can identify the recipient, but “untraceable” is not a safe assumption.
Who should I contact after a ransomware incident?
In the U.S., it’s recommended that ransomware be reported to federal law enforcement channels. You can report to the FBI, Cybersecurity and Infrastructure Security Agency (CISA), or the U.S. Secret Service, and you only need to report once for the information to be shared across the relevant agencies.
Outside the U.S., report the incident through your national cyber authority and to the appropriate police cybercrime channel. For example, the U.K. routes reports via its National Cyber Security Centre (NCSC), Australia uses the Australian Cyber Security Centre (ACSC) channels, and Canada reports via the Canadian Centre for Cyber Security portal.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN