Rainbow table attack: What is it and how to stay safe
When you sign up for a service, your password is typically converted into a hash before it’s stored. A rainbow table is an offline reference that pairs common passwords with their corresponding hashes. Attackers prepare these tables in advance so they can quickly identify passwords if a system’s hashed database is leaked.
Because rainbow tables rely on precomputed matches, they’re most effective against weak, reused, or predictable passwords. If a user’s password appears in the table, it can be cracked quickly and used for account takeover.
This guide explains how rainbow table attacks work and what limits their effectiveness. It also covers key prevention measures and safer sign-in practices.
How does a rainbow table attack work?
Rainbow table attacks work by allowing an attacker to quickly break into accounts after a data leak. Instead of calculating possible password hashes during an attack, attackers rely on work done in advance using a prebuilt rainbow table.
Rainbow tables have a few defining characteristics:
- Precomputed: The table is built before any breach occurs, using common or predictable password guesses.
- Hash-specific: Each rainbow table targets a specific password hashing method. A table built for one hash type won’t work for another.
- Offline: Matching happens on the attacker’s own system, not through a login page.
- Limited in scope: The table only helps if its assumptions match the leaked hashes and the passwords users actually chose.
Why rainbow tables are limited
Rainbow tables are fast because the computationally expensive hashing work is performed in advance. However, this speed comes with strict limitations. The table must closely match the real-world hashing setup. If the hashing method or parameters differ, the table’s assumptions are incorrect, or users chose passwords outside the table’s coverage, rainbow tables provide little or no advantage.
Why rainbow table attacks are dangerous
- They bypass online defenses: Because rainbow table attacks work offline, attackers don’t need to interact with a login page while cracking passwords. Rate limits, account lockouts, and other sign-in protections offer no protection during this phase.
- They enable large-scale account compromise: Once attackers recover real email and password combinations, they often test them on other services using automated tools. This technique, known as credential stuffing, exploits widespread password reuse and can turn a single breach into access across many accounts.
- They’re difficult to detect early: Offline cracking leaves no visible activity for a service to monitor. There are no failed login attempts or unusual sign-in patterns until an attacker tries a cracked password.
Rainbow table attack vs. other password attacks
All password-based attacks aim to steal passwords, but they do so in different ways.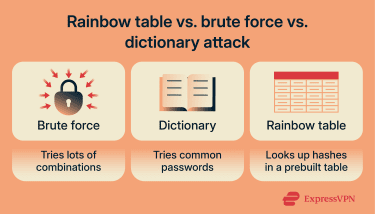
Rainbow table attack vs. brute force attack
A brute force attack is the most direct way to crack passwords. It systematically tests password guesses until it finds one that matches. In practice, attackers rely on automated tools rather than manual attempts, since testing large numbers of combinations by hand isn’t realistic.
Brute force attacks generally fall into two categories. Online brute force submits password guesses through a live login page, where defenses such as rate limiting, captchas, and account lockouts can slow or block an attack. Offline brute force occurs after an attacker has stolen password hashes and tests password guesses by computing new hashes during the attack on their own systems, bypassing login controls and allowing much faster testing.
Attackers may also use more targeted brute force variants, such as password spraying, which tests a small set of commonly used passwords across many accounts. This approach reduces the likelihood of triggering lockouts while still exploiting weak or reused credentials.
Rainbow table attack vs. dictionary attack
A dictionary attack is a password-guessing method that uses a curated list of likely passwords instead of trying every possible combination. That list often includes real words, common passwords, and common patterns people reuse. It’s faster than full brute force because it focuses on guesses that are statistically more likely to work.
In practice, dictionary attacks are almost always automated. Attackers use tools that run through a word list quickly and apply simple variations, such as adding numbers, swapping letters, changing capitalization, or appending a year. This is why weak and predictable passwords fall first.
Like brute force, a dictionary attack can happen online through a login page or offline if an attacker has password hashes. The difference from a rainbow table attack is where the work happens. Dictionary attacks generate hashes as they go, while rainbow tables try to save time by doing a lot of that work in advance.
Risks and consequences of rainbow table attacks
When a rainbow table attack succeeds, the impact can be significant. Cracking plaintext passwords from their hashes can expose personal information, enable account takeovers, and create knock-on risks across other services where the same credentials are reused. The consequences often depend on how the recovered passwords are used and how widely they apply.
Identity theft and data exposure
Identity theft often begins with account takeover. Once an attacker gains access to one account, they typically try to expand control. Email is a common first target because it’s used for password resets. With access to an inbox, an attacker can reset other accounts, change recovery settings, and lock the user out.
This expanded access could lead to data exposure and identity theft. Attackers may collect personal or financial information and use it without permission, such as making purchases, opening new accounts, or impersonating the user.
Corporate security breaches
If a rainbow table helps attackers recover even a single employee password, that access can provide a foothold into business email, internal tools, shared drives, or administrative panels. From there, the damage often comes from what attackers can do while appearing to be a legitimate user, such as reading sensitive messages, exporting data, or changing access settings.
The larger risk is downstream impact. A compromised account can trigger incident response efforts, service disruption, customer notifications, and legal or regulatory obligations.
Research from IBM estimates the global average cost of a data breach at about $4.4 million, reflecting investigation, containment, recovery, and longer-term follow-on costs that extend well beyond the initial intrusion.
It can also erode customer trust. If attackers control a real employee's inbox or internal messaging account, they can send convincing phishing messages from a trusted address, target partners, and keep the incident alive even after the initial password is reset.
Financial loss and reputation damage
Money loss can be direct or indirect. Direct loss happens when an attacker uses a cracked login to make purchases, drain stored value, transfer funds, or abuse saved payment methods. Indirect loss shows up when you spend time recovering accounts, disputing charges, and re-securing everything connected to that password.
For businesses, the financial hit often comes from multiple directions at once: fraud and chargebacks, incident response work, customer support load, legal and compliance effort, and sometimes downtime. Even if the attacker doesn’t steal money directly, leaked customer data can still create expensive follow-up work.
Reputation damage typically comes from loss of trust. Customers stop feeling safe logging in, storing payment details, or sharing personal information. Partners may tighten requirements. Internal teams lose time to verification and cleanup. The business ends up paying, not just in money, but in lost confidence.
How to prevent rainbow table attacks
Preventing rainbow table attacks comes down to two factors: how a service stores passwords and how well accounts stay protected if a password ever gets exposed. Some defenses are controlled by the website (how it hashes and stores passwords). Others are controlled by you (password strength, multi-factor authentication (MFA), and reacting fast to leaks).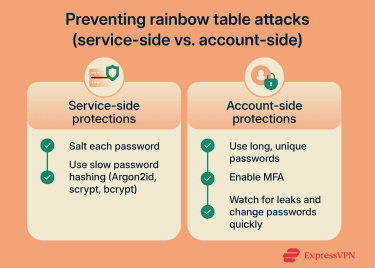
Use of salting in password hashing
Salting is one of the most direct ways to break the “prebuilt lookup” advantage of rainbow tables.
A salt is random text that a service adds to a password before hashing it. The service stores the salt alongside the hash. The key result is that two people who choose the same password will not produce the same hash. That makes precomputed tables far less useful because the attacker would need to account for the salt value, not just the password.
In plain terms, this means attackers can’t use a single rainbow table to match passwords across an entire database, because each stored password includes its own random “extra ingredient.”
Employ strong and modern hash algorithms
A rainbow table attack becomes realistic when a service relies on fast hashing methods or weak password storage practices.
Modern password storage uses password-hashing algorithms that are intentionally slow and resource-intensive. The goal is to make each guess costly for the attacker. The Open Worldwide Application Security Project (OWASP) recommends Argon2id as the first choice, with other options like scrypt or bcrypt when Argon2id isn’t available. These are designed to resist large-scale cracking, including scenarios where attackers have stolen hashes and can crack them offline.
Enforce strong password policies
Strong password rules reduce how many accounts an attacker can crack quickly, even if hashes leak. The core idea is to push passwords away from common patterns and toward unique, hard-to-guess choices. A simple policy that works well in practice looks like this:
- Require length: Longer passwords are harder to guess. Passphrases work well here.
- Block known-bad passwords: Stop “password123”-type choices and passwords already seen in leaks.
- Avoid password reuse: Using the same password across multiple sites can turn one leaked password into many account takeovers.
Use multi-factor authentication (MFA)
MFA helps protect you even when a password is exposed. It combines different kinds of proof, like something known (a password) plus something possessed (a phone prompt or security key) or something inherent (biometrics). If an attacker cracks a password with a rainbow table, MFA could still stop the login.
For the best protection, enable MFA on any account that supports it.
Monitor for data leaks and credential dumps
Rainbow tables are most useful to attackers after a breach, so early warning matters. If an email address or password shows up in a data leak, quick action can cut off follow-up attacks like account takeover and credential stuffing.
What to do when a leak warning appears:
- Change the exposed password anywhere it was reused.
- Turn on MFA if the affected service supports it.
- Review account recovery settings and active sessions.
- Replace weak or reused passwords with unique ones.
FAQ: Common questions about rainbow table attacks
Are rainbow table attacks still used today?
Yes, but mostly in narrower cases. They show up when passwords are stored with older, fast hashing methods and weak storage settings. In modern systems that use strong password hashing plus salting, rainbow tables are usually not the attacker’s best option.
What’s the difference between rainbow tables and dictionary attacks?
A dictionary attack tries a list of common passwords during the attack, hashing each guess as it goes. A rainbow table attack does that work earlier. The attacker precomputes guesses and their hash results in advance, then uses fast lookups later. The goal is to avoid hashing every guess during cracking.
How does password salting help?
Salting adds unique random text to each password before hashing. That means the same password creates different stored hashes for different accounts. This breaks the main advantage of rainbow tables, which is reusing precomputed results across many accounts.
What are the best hashing algorithms?
For password storage, the best options are password-hashing algorithms designed to be slow and resource-heavy: Argon2id (strong default choice), scrypt (strong alternative), and bcrypt (common legacy option, still acceptable when configured well). General-purpose hashes like Message-Digest Algorithm 5 (MD5) or Secure Hash Algorithm 1 (SHA-1) aren’t suitable for password storage.
Can antivirus software detect rainbow table activity?
Usually not. Rainbow table cracking is done offline on the attacker’s machine after hashes have been stolen. Antiviruses might detect related threats that lead to the breach, like malware that steals credentials, but it’s unlikely to “catch” rainbow table cracking itself.
What makes a password resistant to rainbow tables?
A password resists rainbow tables when it’s long and uncommon, so it’s unlikely to be included in precomputed tables. Random passwords from a password manager or a long, unique passphrase work best. Avoid anything built from common words, names, dates, or predictable patterns.
Are rainbow tables still effective with modern hashing?
Usually no. Modern password hashing algorithms are designed to make precomputation expensive and slow. When salting and modern password hashing are used correctly, rainbow tables lose their “fast lookup” advantage.
Can I detect if a rainbow table was used in an attack?
You usually can’t confirm a rainbow table attack. Organizations might infer it during incident response by comparing the password storage setup to the attacker’s speed and patterns, but for individuals, the practical focus is the same: assume the password is compromised, change it everywhere it was reused, and enable multi-factor authentication (MFA).
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN