Zip bombs may look like tiny, harmless files, but they pose a real threat. Imagine receiving a zip file in an email—just a few kilobytes in size—that looks perfectly harmless. Then, when you open it, your computer suddenly slows to a crawl or even crashes completely.
You’ve just triggered a zip bomb, a fiendish compressed file designed to overwhelm your system with an avalanche of data. They’re a reminder that attacks don’t always rely on sophisticated technology. Sometimes, the weapon is a tiny file that bursts into a gargantuan load of repetitive data.
Keep reading for a detailed look at zip bombs, including ways to spot them before they do damage and steps you can take to shield your computer.
Tip: Always be cautious when unzipping files from unknown sources. If a zip file is suspiciously small but promises large content (like a huge video or program), scan it with up-to-date antivirus software before opening. Modern antivirus protection can often detect decompression bombs early and save you from a nasty surprise.
What exactly is a zip bomb?
A zip bomb is essentially a malicious compressed file (often in .zip format, but it can also be in .rar, .7z, etc.) engineered to unpack massive amounts of data when unzipped. This can result in system slowdowns or crashes, as the extreme quantity of junk data that it unpacks can consume all your device’s memory, CPU, and disk space.
Unlike a typical virus or malware that executes code, a zip bomb doesn’t need to run any program. Instead, it disables or disrupts your system by abusing its normal file-handling processes with the sheer volume of data that explodes out of that tiny file when you unzip it.
As it decompresses a huge amount of data, your system continues to use more and more resources until it freezes or shuts down.
Alternate names: Decompression bomb and others
A zip bomb—or, more accurately, a zip file bomb—goes by different names. Some call it a decompression bomb or an archive bomb. Others label it the “zip of death,” underscoring its ability to render a target computer or server useless.
You might also see terms like compression abuse, zip exploit, or even references to “nested archive threats.” All these names speak to the same idea: a malicious file that weaponizes compression to cause chaos.
In many user forums, you’ll see mentions of a recursive zip file (because each layer “calls” the next, just like a recursive function in programming) or, in technical circles, a “zip quine,” describing a structure in which the archive includes clones of itself (a “quine” in programming is a program that outputs its own source code). This repeated layering can trigger an exponential chain of expansion once unzipped.
Whether you label it a “zip bomb,” “archive bomb,” or “decompression bomb,” you’re talking about a file that can cripple your system through compression trickery.
The history behind zip bombs
The idea of the zip bomb has been around for decades, almost as long as file compression itself. Created in 1989, the zip file format became popular in the 1990s, and by the early 2000s, hackers and researchers had discovered they could abuse compression algorithms to create denial-of-service (DDoS) attacks.
One of the earliest and most well-known examples is the 42.zip file, which measures around 42KB when compressed. Inside, though, it holds multiple levels of nested archives. A zip contains other zips, those zips contain more zips, and so on. Once unpacked, it balloons to 4.5 petabytes. It has been circulating since the early 2000s as a proof-of-concept zip bomb.
Back in the early 2000s, many antivirus programs weren’t sophisticated enough to detect these bombs efficiently. Some scanners tried to unpack every layer, eventually stalling and opening a window of time for various malware threats to slip in.
Over time, security software improved; security vendors and operating systems started implementing checks to limit the depth of recursive archive extraction (e.g., 10–20 levels max). This makes high-profile zip bomb attacks rare in modern environments.
Even so, researchers continued to tinker with the zip bomb concept. In 2019, a programmer named David Fifield introduced a new twist on the zip bomb: a method to achieve higher compression ratios without relying on multiple nesting layers. He did this by exploiting a known property of the zip format—the fact that zip files store metadata separately from actual compressed data.
Fifield’s creation managed to compress 4.5 petabytes into a 46MB zip file by creating many ZIP entries that point to overlapping or identical blocks of data, where each one pretends it’s something separate. The decompressor sees thousands of “different” files, all pointing to slightly offset chunks of the same actual data. Each one decompresses to a large output—say, a gigabyte—but the compressed data only exists once.
At this point, you may be wondering how a 46MB zip file that unpacks to 4.5 petabytes can have a higher compression ratio than a 42KB file that decompresses to the same size. The difference lies in how the two bombs are structured.
The classic 42.zip uses a recursive design, where each zip file contains other zip files, which in turn contain more zip files. This layered unpacking causes the total output to accumulate to 1,048,576 copies of the same 4.3GB file, totaling up to 4,508,876GB (4.5PB).
In contrast, Fifield’s bomb skips the recursion entirely. It uses a non-recursive method to generate the full 4.5PB output directly from a single 46MB zip file. It does this by creating thousands of entries that point to overlapping compressed data blocks, tricking the decompressor into inflating the same data many times. This structure allows for a dramatically higher compression ratio without deep nesting.
How do zip bombs work?
Zip bombs draw on simple compression mechanics by exploiting compression algorithms to an extreme degree. The basic trick is to pack a huge amount of repetitive or redundant data into a compressed file, such that it decompresses into an absurdly large payload. Let’s look at how exactly this works.
Compression exploitation: The basic idea
Traditional archive formats like .zip or .rar use compression algorithms to reduce file size by eliminating redundancy. Zip bombs exploit these algorithms by feeding them extremely repetitive data or by structuring archives in a way that forces massive expansion during decompression.
A zip bomb might contain thousands of identical files or huge blocks of repeated characters—like a text file with nothing but “AAAA…”—which compress down to nearly nothing. Algorithms like Deflate, commonly used in zip files, are especially vulnerable to this kind of extreme compression.
In some cases, as mentioned, attackers go further by nesting compressed files within other compressed files, creating recursive archive structures. This nesting multiplies the decompression work exponentially, making the system repeatedly unpack the same compressed content in layers.
The result? As soon as your system begins decompressing the zip bomb, it starts allocating memory and disk space uncontrollably. On older machines, this can lead to a near-instant crash. On newer systems, it may cause severe lag, antivirus failure, or even forced reboots.
That’s the core mechanism of a zip bomb: it doesn’t execute malicious code—it weaponizes data compression itself to overwhelm and disrupt.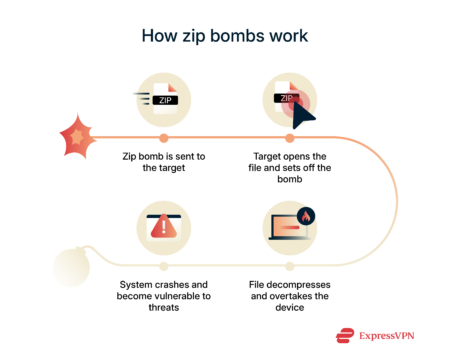
Real zip bomb file sizes that crash systems
Zip bombs are known for jaw-dropping expansion ratios. A 10KB file can turn into gigabytes. Some bombs expand into terabytes or even petabytes. The classic 42.zip is one example. It’s about 42KB when compressed, yet it can bloat to more than 4 petabytes when fully extracted. A home computer user who tries to unpack that file would likely see the system freeze quickly.
To put things in perspective:
- A 10KB zip bomb can decompress into 500MB—a 50,000:1 ratio.
- 42.zip expands to over 4.5PB—that’s roughly a 100 million to one expansion.
- Even a 50MB zip bomb might swell into 10–20 terabytes, or more.
These ratios show how zip bombs can easily overwhelm your system. When your device tries to allocate space for decompression, it may exhaust available memory or disk space—leading to memory errors, antivirus failures, or system instability.
Zip bomb as part of a multi-stage attack
There is another way a zip bomb can be dangerous, aside from overwhelming your system resources, but this risk is much lower today with modern antivirus programs than it was just a decade or two ago.
This type of attack takes advantage of the fact that a zip bomb usually doesn’t contain malware itself—which makes it a perfect distraction. Its purpose is to overload antivirus engines or file scanners by triggering massive decompression tasks. This causes systems to freeze, crash, or disable scanning functions temporarily.
While defenses are down, attackers follow up with a second-stage payload—the actual malware—such as ransomware, spyware, or Trojans. Since the system’s protections are busy or disabled, the real threat can slip through undetected.
Thankfully, mass-scale zip bomb attacks are rare today, thanks to better antivirus protections.
How to detect and protect against zip bombs
Let’s now go over how you can detect a potential zip bomb and best practices to protect yourself from this threat.
Modern antivirus techniques that stop zip bombs early
Antivirus vendors recognized the zip bomb tactic years ago. Many solutions now set scanning limits. If an archive tries to expand beyond a certain threshold, the antivirus halts the process and flags the file. This might pop up as a warning or prompt you to remove or quarantine the file.
Some advanced antiviruses use machine learning and behavior analysis. They don’t just rely on file signatures—they watch how the decompression behaves. If the ratio of compressed to uncompressed data shoots up beyond typical values, the software aborts the process. That helps block new variants that might not have matching signatures in the antivirus malware database.
To prevent endless recursion, antivirus scanners also impose limits on how deep they will go into nested archives. They might only unpack, say, 2 or 3 levels deep. If an archive is nested beyond that, the antivirus will either stop or carefully scan one layer at a time without full extraction. This avoids the exponential explosion from multi-layer bombs.
Many security tools have a safety timeout or resource limit. If scanning a file is taking an absurd amount of CPU time or memory, the scanner can abort the operation. This way, even if it started to open a bomb, it won’t grind indefinitely. It may then mark the file as suspicious. Essentially, they fail-safe.
File and email safety tips to avoid zip bomb traps
You can dodge a zip bomb attack by applying a few simple habits when handling files:
- Inspect source and context: Verify the email sender or website. A zip file arriving from an unknown address is a red flag.
- Scan with antivirus software: Right-click and scan the zip with a reputable tool before opening.
- Use a sandbox: Run suspicious files in a controlled environment. Virtual machines or specialized sandbox utilities can help you examine the file without risking your main system.
- Don’t turn off safety limits: Power users sometimes disable built-in limits (like recursion depth in unpackers) for convenience. Avoid doing this unless absolutely necessary. Those limits are there to protect you from things like zip bombs.
 The combination of these methods means that, these days, you’ll rarely accidentally trigger a zip bomb if you have a decent security setup. The antivirus will likely catch it at the scanning stage, or at worst, your system will halt the extraction before catastrophe.
The combination of these methods means that, these days, you’ll rarely accidentally trigger a zip bomb if you have a decent security setup. The antivirus will likely catch it at the scanning stage, or at worst, your system will halt the extraction before catastrophe.
Still, no security measure is foolproof. The best defense starts with safe online habits. If you stay skeptical about odd files and run updated antivirus tools, you cut the risk of a zip exploit significantly.
How to configure your system to block zip bombs
For those who want to go a step further, there are configurations and settings that can harden a system or network against zip bombs:
- Limit decompression depth: Some unzip utilities or security suites allow you to limit the depth of nested archives. Once the limit is reached, the program stops unpacking further layers.
- Set disk space quotas: On shared systems or servers, enforce quotas that keep one user or one process from consuming an entire disk with an inflated archive.
- Use advanced mail filters and intrusion detection systems: Solutions that parse attachments at the gateway stage can spot unusual compression sizes. They often block these files before they reach end users.
- Apply file size policies: On mail servers or gateways, you can implement rules like “block compressed attachments smaller than X KB” or “flag any archive that contains files larger than Y MB inside.” These policies can catch bombs. For instance, if an attachment is 50KB but claims to contain a 5GB file, the gateway could drop it.
- Regularly update operating systems: Modern OS updates might include new measures to handle zip files more gracefully. This includes security patches that address file-handling routines.
- Update and patch archive utilities: Ensure the tools you use for compression/decompression (WinZip, 7-Zip, your OS’s built-in extractor, etc.) are up to date. Developers occasionally update these tools to better handle unusual archive structures and to fix any bugs that bombs might exploit.
- Disable automatic archive handling: Some applications and services automatically extract archives for convenience (for example, certain email clients might preview zip contents, or some upload services automatically unzip files). If you don’t absolutely need this feature, consider disabling it. Manual control means you can decide when and how to extract something. Automatically unpacking archives is exactly what a zip bomb creator hopes your system will do.
 By fine-tuning your system, you create multiple lines of defense. A zip bomb may slip through one layer, but additional safeguards can catch it at the next.
By fine-tuning your system, you create multiple lines of defense. A zip bomb may slip through one layer, but additional safeguards can catch it at the next.
Are zip bombs ever useful in cybersecurity?
It might surprise you, but yes—zip bombs do have some niche uses in cybersecurity aside from causing trouble. While they are a malicious concept, security professionals and researchers have repurposed them in a few ways.
How zip bombs help test antivirus limits and robustness
Security researchers and software testers use zip bombs to stress-test antivirus and antimalware engines. The idea is to make sure that these security tools can handle malicious archives safely without crashing or hanging.
For instance, quality assurance teams at an antivirus company will throw known zip bombs like 42.zip at their product to verify that it detects the threat. Or at least fails gracefully rather than, say, the scanner itself freezing up. If the antivirus can smoothly catch or stop the bomb, that’s a pass; if it chokes, the developers know they have a problem to fix. In this way, zip bombs contribute to making security products more robust.
This is part of a broader approach to system hardening. Organizations that run high-traffic servers want to confirm that routine scanning won’t fail under an unusual load. By intentionally deploying a known, controlled zip bomb, security professionals like penetration testers can study whether scanning halts gracefully.
For example, they might test if a company’s email filter catches a bomb or if a web application will accept and try to process an uploaded bomb file. The results of such tests can guide organizations in hardening their defenses. If it doesn’t, they have a direct warning sign that a real attacker might succeed in distracting or harming the system.
Academic research and real studies involving zip bombs
Researchers have explored the dangers of compression abuse in various academic papers and real-world experiments. For example, the study “In the Compression Hornet’s Nest” by Pellegrino et al. (2015) examines how data compression, when poorly implemented, can become a serious security liability. Their work highlights the risk of denial-of-service (DoS) attacks stemming from compression-based exploits—including zip bombs—and emphasizes the need for more robust handling in networked applications.
Other research, like the “Detection Algorithm for Non-recursive Zip Bombs” (2020) by Maoyang Chen and Mingyu Fan of the University of Electronic Science and Technology of China in Chengdu, focuses on identifying malicious archive structures without full decompression.
Zip bombs have also served as valuable tools in academic experiments to expose weaknesses in older mail servers and legacy operating systems. By observing how zip bombs triggered denial-of-service incidents, the research community was able to refine antivirus scanning logic and strengthen OS-level safeguards. Today’s system software often incorporates these improved protections by default.
FAQ: Common questions about zip bombs
What happens if I open a zip bomb?
If you open a zip bomb, your system will begin decompressing a massive amount of data, which can quickly overwhelm your computer’s resources.
In practical terms, you’ll likely experience your system becoming extremely slow or unresponsive. The decompression may consume all available memory (RAM) and start eating up disk space, and the CPU will be under heavy load.
Shortly after, the program doing the extraction may crash, and in the worst cases, your whole system can freeze or crash as well. You might see an error like “Out of memory” or “Disk full,” or the system might simply hang until a reboot.
Can zip bombs infect my computer with a virus?
No, a zip bomb by itself does not infect your computer with a virus. Zip bombs contain no executable malware code—their “payload” is the extreme amount of data produced when they unzip, not a hidden Trojan or virus.
So, they won’t implant malware or allow someone remote access to your machine in the way a typical virus or worm would.
However, they are considered malware variants in a broader sense because they are designed to harm or disrupt your system’s operation. They may also be used to distract you while an attacker tries to slip something else onto your device while your system is busy.
Are zip bombs illegal to create or use?
Creating or possessing a zip bomb file for your own testing or curiosity is generally not illegal. After all, it’s basically just a bunch of compressed data.
However, creating or sharing a zip bomb with malicious intent may violate computer crime laws. If you send someone a zip bomb with the intent to crash their system or disrupt a service, that could be considered an attack (denial-of-service) or unauthorized impairment of a computer system, which is illegal in many jurisdictions.
In short, it’s the intent and usage that determine legality.
How can I test if a file is a zip bomb safely?
Experts do this in a controlled environment, such as a virtual machine or sandbox. They also rely on bounded scanning or advanced antivirus checks. If you’d rather not risk it, skip the manual approach and just rely on your antivirus program’s malware engine.
Under no circumstance should you double-click and freely extract an unknown tiny archive just to see what’s inside—that’s exactly what you don’t want to do with a potential bomb.
How to detect a zip bomb download?
Look for mismatched file size and content claims. If you’re downloading something that should be large (like a video) but the archive is just a few kilobytes, that’s suspicious.
Pay attention to any antivirus or browser warnings. Real-time protection might block the download or quarantine the file. Once it’s on your system, scan it or inspect its contents without full extraction. If the uncompressed size is suspiciously high, it’s likely a bomb. Avoid opening it, and either delete it or keep it quarantined for further checks.
How do I recognize a zip bomb if I come across one?
Zip bombs often appear as tiny compressed files claiming to hold massive or unusual data. If you preview the archive, you may see huge uncompressed files or multiple nested archives inside. Some bombs contain repetitive files or a suspicious number of identical items. Antivirus programs may label them as “decompression bomb” or archive bomb.” The main giveaway is the massive discrepancy between the compressed size and the stated uncompressed size.
Are zip bombs dangerous?
Zip bombs are dangerous in the sense that they can cause real damage or downtime, but their danger is limited to resource disruption. They won’t steal your information or permanently infect your system like other malware.
Instead, the danger is immediate and technical: they can crash critical programs, cause system reboots, and potentially make you lose unsaved work or corrupt data. If a zip bomb were deployed on a server or in a business environment at the wrong time, it could certainly cause financial or operational harm due to the service outage it triggers.
How can I stay safe from zip bombs?
There are several steps you can take. Use caution when opening any compressed file from unknown sources. Always run a virus scan before unzipping. Keep your antivirus program updated and make sure it’s configured to spot suspicious archives.
If your email or web filter blocks small attachments claiming large content, leave those settings in place.
Don’t override recursion or size limits in your decompression tools. If something still looks suspicious, open it in a sandboxed environment—like a virtual machine with limited resources. Train yourself (and others) to recognize unusual file size discrepancies and nested archives.


























