What is OPSEC, and why do you need it?

Keeping prying eyes away from your plans, data, and conversations is hard work. Attackers sift through scraps of information, link them together, and build a surprisingly detailed picture of you or your organization. Operational security (OPSEC) gives you a structured way to stop that from happening.
In this guide, you’ll learn what OPSEC is, why it’s important, and how to apply it in both personal and organizational contexts. We’ll break down the five-step OPSEC process and share best practices (like encryption and access control) that you can implement right away.
💡 Quick guide
- OPSEC is a mindset: Think like an attacker, spot weak points, and close the gaps.
- Five repeatable steps: Identify critical information, study threats, find weak spots, weigh the risks, and add countermeasures.
- ExpressVPN helps: A VPN encrypts your traffic, masks location data, and lowers the chance of network snooping—an easy win for any OPSEC plan.
What is OPSEC (operational security)?
At its core, OPSEC is a mindset of looking at security from an attacker’s perspective. It asks, “If I were trying to steal information from me or my organization, how would I do it?” By asking you to think like a cybercriminal or spy, OPSEC helps you identify weaknesses in everyday operations that you might otherwise overlook.
It started as a U.S. military discipline during the Vietnam War. The Purple Dragon task force discovered that seemingly harmless details—radio chatter, supply-ship schedules, even newspaper stories—helped the enemy foresee troop movements. To counter this, the unit formalized a new approach: list information that truly matters and block every path that could leak it.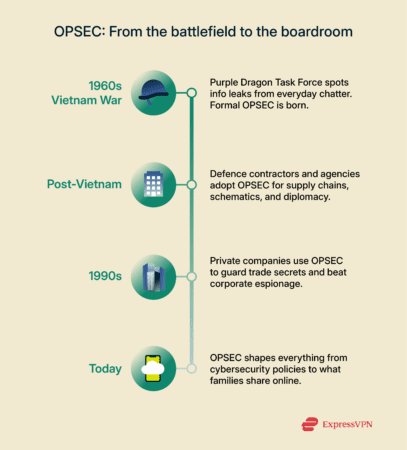 That framework soon spread far beyond the battlefield to businesses, government agencies, and personal life. After Vietnam, OPSEC left the barracks for civilian work. Defense contractors applied the method to protect classified schematics and supply chains, and federal agencies used it to safeguard investigations and diplomacy. By the 1990s, companies borrowed the same logic to shield trade secrets and frustrate industrial espionage.
That framework soon spread far beyond the battlefield to businesses, government agencies, and personal life. After Vietnam, OPSEC left the barracks for civilian work. Defense contractors applied the method to protect classified schematics and supply chains, and federal agencies used it to safeguard investigations and diplomacy. By the 1990s, companies borrowed the same logic to shield trade secrets and frustrate industrial espionage.
The internet age then pushed those ideas into everyday life, where they’re now widely used in cybersecurity and online privacy: mind what you post, limit who sees your transactions, and lock down home networks. The five-step cycle now guides risk briefings in Fortune 500 boardrooms and the privacy settings on family phones alike.
The 5 steps of the OPSEC process
As mentioned above, OPSEC isn’t a one-time checklist—it’s typically thought of as a continuous five-step process that you apply repeatedly as situations change.
Step 1: Identify critical information
This step consists of listing anything that would hurt you if an outsider saw it. For a freelance designer, that might be client drafts and invoices. For a hospital, it’s patient records and drug inventories. For individuals, it could include social media metadata.
Small clues that seem harmless but actually reveal sensitive information can include:
- A skyline in a photo that pinpoints the office floor;
- An out-of-office auto-reply that reveals travel dates;
- A job ad hinting at an upcoming product launch.
Step 2: Analyze potential threats
Ask who benefits if that data leaks. Criminals chasing quick cash? A rival firm seeking market intel? A disgruntled insider eyeing admin rights? Mapping these actors clarifies their patience, budget, and methods. Knowing the “who” shapes the “how.” A casual scammer hunts for open buckets, whereas a state unit may combine phishing with zero-day exploits.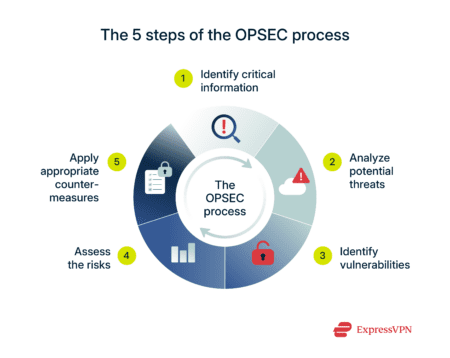
Step 3: Identify vulnerabilities
Walk through every path the data travels. Laptops on café Wi-Fi, API endpoints, SaaS dashboards, even hallway chats. Weak passwords, reused tokens, and idle accounts often appear here. Remember human factors: a polite phone call can still trump any firewall.
Step 4: Assess the risks
Cross-match each vulnerability with each threat. Rate every weak spot by likelihood and damage. Ask, “If this happens, how bad does it get, and how soon could we catch it?” A forgotten admin panel exposed to the web sits high on the list; a locked drawer inside a guarded office sits lower.
Step 5: Apply appropriate countermeasures
Pick fixes that hit the biggest risks first:
- Tighten access controls and add MFA.
- Rewrite policies on photo sharing and auto-replies.
- Roll out staff refreshers on spotting social-engineering tricks.
- Patch or replace outdated smart devices.
Treat the list as a live playbook—edit it after every audit, breach report, or major tech change. After step 5, you monitor and start again: a consistent loop of review and improvement keeps you one step ahead of data leaks, whether you’re running a global enterprise or guarding personal passwords at home.
To sum up:
| Step | Goal | Typical action |
|
Decide what must stay private. | Map data that could harm you if exposed—design files, client lists, location logs. |
| 2. Analyze potential threats | List who might want that data. | Nation-state cyber actors, competitors, disgruntled staffers, opportunistic scammers. |
| 3. Identify vulnerabilities | Spot the weak points they could exploit. | Out-of-date CMS, overshared cloud folders, talkative employees. |
| 4. Assess the risks | Rank likelihood × impact. | High‑risk = easy leak + high damage; fix these first. |
| 5. Apply appropriate countermeasures | Block or reduce the biggest risks. | Patch, segment networks, train staff, and encrypt traffic. |
Why is OPSEC important?
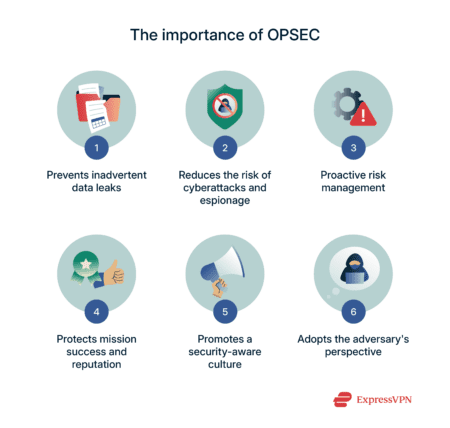
OPSEC gives you a structured way to keep high-value information—yours and that of your business—out of cybercriminals’ reach. It delivers a number of practical benefits:
- Prevents inadvertent data leaks: By viewing day-to-day tasks through an attacker’s eyes, you will spot harmless‑looking habits—an unredacted screenshot, a loose cloud-folder link—that could hand over sensitive details.
- Reduces the risk of cyberattacks and espionage: Classifying and tagging high‑value data means you can lock it down, monitor who touches it, and stop rival firms or ransomware gangs from walking off with trade secrets.
- Proactive risk management: The OPSEC process calls for regular threat and vulnerability reviews, so you close gaps before outsiders—or insiders—discover them.
- Protects mission success and reputation: Whether it’s a product launch or a humanitarian convoy, leaking future plans lets opponents disrupt schedules, undercut deals, or sow public doubt.
- Promotes a security‑aware culture: When everyone understands why small details matter, they become more selective about what they share and where they share it. Fewer casual mistakes, fewer entry points.
- Adopts the adversary’s perspective: Thinking like an attacker uncovers weak spots traditional audits miss—everything from back‑of‑house Wi‑Fi beacons to metadata buried in an employee’s holiday photos.
How to improve OPSEC in your organization
1. Schedule employee training and awareness
Short, frequent sessions beat annual slide decks. Teach staff what phishing looks like today, how social engineering calls unfold, and why badge tailgating matters. A culture of polite verification pays off.
2. Conduct regular audits and policy reviews
Schedule audits, but run a few surprise drills as well. External penetration testers often surface blind spots that internal teams miss. Update policies whenever the threat model, staff roster, or tech stack shifts.
3. Leverage automation for consistency
SIEM rules, log‑based alerts, and scripted compliance checks never tire. Automate the repetitive parts—patch status, account lock reports—so analysts can focus on anomalies.
4. Restrict access with the principle of least privilege
Give every user and application the bare minimum rights needed for daily tasks. Pull back dormant roles, time‑box temporary access, and watch for privilege creep.
5. Implement strong change management controls
Track every alteration to code, infrastructure, or policy. Use tickets, peer review, and automatic rollbacks when tests fail. Sudden, undocumented changes are red flags.
6. Use dual control and separation of duties
Never let one person both set a policy and approve its exceptions. Pair a network engineer with a security engineer when pushing firewall rule sets. Dual control lowers insider‑threat risk and catches simple mistakes before they land.
7. Use secure communication protocols
Always use secure tools to send messages and files. Protocols like TLS 1.3, SSH, and SFTP encrypt your data in transit, blocking eavesdroppers. For messaging, pick apps with end-to-end encryption. Platforms that offer self-hosted encryption keys give you more control—you create and store the keys yourself, so no third party can decrypt your data. Avoid tools that send data in plain text.
8. Create an incident response and disaster recovery plan
Even the best OPSEC setup needs a fallback plan. Draft a clear incident-response playbook that lists likely attack scenarios and assigns who does what, when, and with which tools to curb damage and get systems running again.
9. Encrypt sensitive data and network traffic
Local files: enable full‑disk encryption on laptops and phones. Cloud buckets: turn on managed key services. On the road: use ExpressVPN to wrap internet traffic in strong encryption, hiding metadata from hotspot owners and rogue access points.
💡 Did you know?
ExpressVPN’s Network Lock (kill switch) blocks all traffic if the VPN connection drops—keeping your data safe even during unexpected interruptions.
How to improve OPSEC in your home
1. Turn off location tags
Switch off GPS tagging on your phone camera and skip social media check-ins. When your sunset snapshot or morning-run selfie no longer broadcasts coordinates, snoops lose a key puzzle piece. If you do post memories, limit the audience as far as you can to people you actually know.
2. Strip metadata before sharing
Photos carry hidden details—timestamps, device IDs, and even your exact spot on the map. Run each image through a free metadata remover, rename the file, and then upload. You share the moment, not the backstory, and strangers can’t reverse-engineer a timeline of your life.
3. Tighten friend lists
Every few months, audit your contacts. Remove vague acquaintances, move co-workers to a restricted list, and lock personal updates to a trusted inner circle. Fewer eyes mean fewer screenshots in random group chats, keeping family news right where you want it—private.
4. Use separate email identities
Create one address for banking, another for shopping, and a burner for newsletters. If hackers breach a retailer, the damage stops at that inbox. Add two-factor authentication and unique passwords, and you’ve walled off each slice of your digital life.
5. Lock down smart devices
Change every default password on day one, install firmware updates promptly, and park cameras, speakers, and bulbs on a guest Wi-Fi network. Isolating gadgets keeps a compromised doorbell from reaching your laptop.
6. Use a VPN
A VPN wraps all your traffic in strong encryption, hiding browsing habits from ISPs, advertisers, and snoops on public Wi-Fi. ExpressVPN also adds TrustedServer RAM-only infrastructure, a Network Lock kill switch, and the fast, open-sourced Lightway protocol, giving you privacy without slowing you down.
Common OPSEC failure scenarios
Even with a solid OPSEC mindset, slipups happen. All it takes is one overlooked detail or casual habit to create an opening. Let’s look at some common OPSEC failure scenarios—and how they can quietly expose sensitive information.
Digital footprint and social media
- Oversharing on social media: A casual post about work, travel, or family routines can give adversaries the information they need.
- Geotagged photos: Location tags in selfies expose restricted sites.
- Public profiles: “About me” sections on social profiles, friends lists, and shared interests combine into a dossier when scraped together.
💡 OPSEC lesson: Pause before you post. Could a stranger use this? Your digital crumbs reveal more than you think.
Technology and devices
- Wearables and smart tech: GPS‑enabled watches and apps broadcast daily routines—fitness‑tracker heatmaps even lit up patrol routes inside secret bases.
- Unsecured home networks: Working remotely on a router still using the factory password invites snoops.
- Lost or stolen gear: Phones, laptops, or USB sticks without encryption hand data over freely to whoever finds them.
- Personal devices on work systems: A lightly protected phone that syncs company email can pierce a tight corporate perimeter.
💡 OPSEC lesson: Lock down the tech you rely on—change default passwords, keep firmware patched, and encrypt traffic and storage.
Human factors
- Phishing and social engineering: A convincing “urgent request” can still trick you into handing over credentials. Fake apps are another growing threat—they often mimic real tools but steal login data or spy on your activity once installed.
- Weak or reused passwords; no MFA: Attackers target the lowest bar first. Our guide to stronger passwords and two-factor authentication explains how to set up better defenses that attackers can’t easily guess or bypass.
- Insider slip‑ups or sabotage: A misconfigured cloud bucket or a disgruntled employee can leak gigabytes in minutes.
- Poor physical discipline: Unlocked desks, tailgaters in the lobby, bins of unshredded drafts—all open invites.
- Predictable patterns: Fixed travel routes or call schedules let observers plan around you.
- Limited training: People can’t follow rules they never learned.
💡OPSEC lesson: People leak more than systems. Stay alert, verify unusual requests, and refresh training often.
Data handling and disposal
- Improper disposal: Drives sold online or papers tossed intact give scavengers a data jackpot.
- Data aggregation: Harmless fragments from many places merge into a damaging whole.
- Uploading samples to public tools: Analysts sometimes feed malware or URLs containing client info into open sandboxes, exposing that data.
💡OPSEC lesson: Guard information from creation to destruction. One overlooked file can undo years of protection.
Final word on OPSEC
OPSEC isn’t just a checklist; it’s the habit of asking, “What could an outsider learn from this?” Keep that question front and center, and the five-step cycle starts to flow: name the data that matters, picture who might chase it, trace the weak spots, rate the risk, and plug the gaps.
Whether you’re protecting a global network or a home router, the rhythm is the same—and it works. Add ExpressVPN’s encryption, TrustedServer tech, and Network Lock kill switch, and your online trail fades to a whisper. Stay curious, stay methodical, and leave snoops staring at an (almost) blank page.
FAQ: Common questions about OPSEC
Is OPSEC part of cybersecurity or operations?
What is the difference between OPSEC and InfoSec?
OPSEC covers human behavior, physical procedures, and digital defenses together, reshaping the entire security plan so fragments never combine into a useful picture. InfoSec provides the locks and alarms; OPSEC surveys the site through an attacker’s eyes and points out where extra protection or fresh habits are still needed.
What qualifies as an OPSEC violation?
-
- Posting a project screenshot that shows client names or timelines.
- Discussing sensitive work on a public channel or unsecured Wi‑Fi.
- Reusing a badge, token, or password across multiple systems.
- Leaving an unlocked laptop unattended.
- Even a tiny hint—like geotags in a selfie—can let attackers trace patterns and plan a strike.
Who needs OPSEC training?
Is OPSEC only for deployments?
How long is OPSEC training good for?
What is OPSEC in cyber?
-
- Classifying sensitive files and tagging them inside SaaS tools.
- Scrubbing metadata from documents and images.
- Using VPN encryption to hide browsing patterns and location info.
- Watching for social‑engineering attempts that bypass tech controls.
The aim is to remove every digital breadcrumb an attacker could stitch together.
What are the 5 steps of OPSEC?
- Identify critical information: List the data and activities that would hurt you if exposed.
- Analyze potential threats: Map out who might want that data and why.
- Identify vulnerabilities: Walk through systems and habits to see where leaks can start.
- Assess the risks: Rank each weakness by likelihood and impact to set priorities.
- Apply countermeasures: Patch software, tighten procedures, train staff, and repeat the cycle.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN







Comments
Very happy to see your blog covers OpSec, and your company supports EFF as well as other privacy organizations. Keep up the good work and I shall bookmark this site! Long Live Privacy!!!