149M Logins and Passwords Exposed Online Including Financial Accounts, Instagram, Facebook, Roblox, Dating Sites, and More.

Cybersecurity Researcher Jeremiah Fowler uncovered a data leak of 149 million logins and passwords, and shared his findings with ExpressVPN. We are publishing his report to help the public stay informed and protected as part of our ongoing effort to highlight important security risks.
The publicly exposed database was not password-protected or encrypted. It contained 149,404,754 unique logins and passwords, totaling a massive 96 GB of raw credential data. In a limited sampling of the exposed documents, I saw thousands of files that included emails, usernames, passwords, and the URL links to the login or authorization for the accounts. This is not the first dataset of this kind I have discovered and it only highlights the global threat posed by credential-stealing malware. When data is collected, stolen, or harvested it must be stored somewhere and a cloud based repository is usually the best solution. This discovery also shows that even cybercriminals are not immune to data breaches. The database was publicly accessible, allowing anyone who discovered it to potentially access the credentials of millions of individuals.
The exposed records included usernames and passwords collected from victims around the world, spanning a wide range of commonly used online services and about any type of account imaginable. These ranged from social media platforms such as Facebook, Instagram, Tiktok and X (formerly Twitter), as well as dating sites or apps, and OnlyFans accounts indicating login paths of both creators and customers. I also saw a large number of streaming and entertainment accounts, including Netflix, HBOmax, DisneyPlus, Roblox, and more. Financial services accounts, crypto wallets or trading accounts, banking and credit card logins also appeared in the limited sample of records I reviewed.
One serious concern was the presence of credentials associated with .gov domains from numerous countries. While not every government-linked account grants access to sensitive systems, even limited access could have serious implications depending on the role and permissions of the compromised user. Exposed government credentials could be potentially used for targeted spear-phishing, impersonation, or as an entry point into government networks. This increases the potential of .gov credentials posing national security and public safety risks.
The database had no associated ownership information so I reported it directly to the hosting provider via their online report abuse form. I received a reply several days later stating that they do not host the IP and it is a subsidiary that operates independently while still using the parent organization's name. It took nearly a month and multiple attempts before action was finally taken and the hosting was suspended and millions of stolen login credentials were no longer accessible. The hosting provider would not disclose any additional information regarding who managed the database, it is not known if the database was used for criminal activity or if this information was gathered for legitimate research purposes or how or why the database was publicly exposed. It is not known how long the database was exposed before I discovered and reported it or others may have gained access to it. One disturbing fact is that the number of records increased from the time I discovered the database until it was restricted and no longer available.
Breakdown of Email Providers (estimated)
- 48M - Gmail
- 4M - Yahoo
- 1.5M - Outlook
- 900k - iCloud
- 1.4M - .edu
Other notable accounts included:
- 17M - FaceBook
- 6.5M - Instagram
- 780k - TikTok
- 3.4M - Netflix
- 100k - OnlyFans
- 420k - Binance
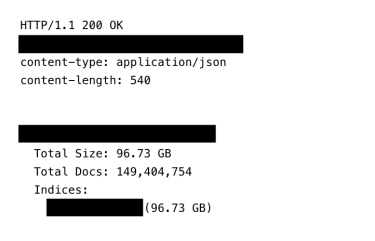 This screenshot shows the total count of records and size of the exposed infostealer database.
This screenshot shows the total count of records and size of the exposed infostealer database.
This image shows screenshots of accounts and credentials including Instagram, Google accounts, and OnlyFans.
This image shows screenshots of accounts and credentials including Facebook, a government account from Brazil, and a WordPress administrative login.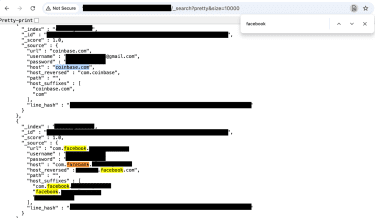
This screenshot shows how the index was searchable using nothing more than a web browser.
The database appeared to store keylogging and “infostealer” malware, a type of malicious software designed to silently harvest credentials from infected devices. These files were different from previous infostealer malware datasets that I have seen because it logged additional information. The records also included the “host_reversed path” formatted as (com.example.user.machine). This structure is used to create an easily indexable way to organize the stolen data by victim and source. Reversing the hostname can also help avoid directory conflicts or as an attempt to bypass basic detection rules that look for standard domain formats. The system used a line hash as the document ID to ensure one unique record per unique log line. In a limited search of these hash and document IDs it was identified that they were indeed unique and returned no duplicates.
Potential Risks of Exposed Credentials
The exposure of such a large number of unique logins and passwords presents a potentially serious security risk to a large number of individuals who may not know their information was stolen or exposed. Because the data includes emails, usernames, passwords, and the exact login URLs, criminals could potentially automate credential-stuffing attacks against exposed accounts including email, financial services, social networks, enterprise systems, and more. This dramatically increases the likelihood of fraud, potential identity theft, financial crimes, and phishing campaigns that could appear legitimate because they reference real accounts and services.
How to Protect Your Accounts, Credentials, and Privacy
By now most of us are aware that malware can be spread through a range of different methods including malicious email attachments, fake software updates, compromised browser extensions, and even deceptive advertisements. Once the device is infected the malware can run undetected and harvest and transmit credentials. If the device is infected with malware simply changing passwords does no good because the new password will also be captured. Having antivirus software installed on your device is a good first line of defense and your best bet in identifying and removing malware. A report published in October identified that only an estimated 66 percent of U.S. adults used antivirus software in 2025. This means there are a large segment of users with unprotected and potentially vulnerable devices to this type of infostealer malware.
Anyone who suspects their device may be infected with malware should take immediate action. On a mobile device, I recommend updating the operating system and security software (if installed). If you don’t have security software, install it and scan the device to remove anything that is identified as malicious or flagged as suspicious. Updating the operating system can patch known vulnerabilities and having the latest versions of security software can also improve detection methods. Additionally, review app permissions, keyboard settings, accessibility, and device admin access. As a general rule, only install apps from official app stores. On a computer Windows/macOS/Linux etc, even non-technical users can conduct a deeper review of programs, browser extensions, and running processes to identify unknown or suspicious activity and software.
Using a password manager can reduce some of the risks from basic infostealer malware and keyloggers. Most password managers store passwords and often auto fill credentials and while this can prevent simple keystroke loggers from capturing typed passwords it is not immune from other more advanced malware. Password managers encrypt data and ensure MFA, while this helps to improve overall account security they do not protect against fully compromised systems. There are additional ways infostealer malware can collect or harvest data. This includes capturing clipboard contents, scraping browser memory, stealing session cookies and tokens, or intercepting form data before it is encrypted. Password managers have many positive benefits and do help improve security against password reuse and basic keylogging, but they cannot defend against all variants of advanced malware. When combined with a good antivirus, endpoint security, and regular OS updates it is a safer option than nothing.
From a privacy perspective, the breach of exposed email addresses and account associations could allow criminals to build detailed profiles of individuals. Knowing where they have accounts, what services they use, and potentially their professional or personal affiliations could hypothetically increase the success rate of social engineering or phishing attempts. Most people keep sensitive documents and communications in their email history without realizing how big of a risk it could be if someone gained unauthorized access. An account takeover could have serious privacy implications depending on the type of the account or service. Unauthorized access to images and chat histories from dating profiles or adult entertainment accounts could potentially create risks years after the incident, including harassment or extortion attempts.
After any data breach or even as a preventative measure it is a good idea to review and update account security measures. This includes enabling two-factor authentication or biometric protections when they are available. Although extra steps are not always convenient, adding an additional verification step can help prevent unauthorized access of accounts by criminals using compromised passwords. It is also a good idea to review login history, login locations, devices, and any failed login attempts. As a general rule never reuse passwords across different sites, applications, or services. Taking these basic steps can help protect against or prevent an account compromise.
While it may seem ironic that cybercriminals themselves would leave such a valuable cache of stolen data unsecured, researchers note that this is not uncommon. Criminal operations often prioritize speed and scale over operational security, storing data in misconfigured cloud servers or databases that can be discovered through routine internet scanning. Once exposed, such datasets are frequently copied and redistributed, making the damage difficult to reverse.
The discovery of this unprotected database serves as another reminder that credential theft has become a large-scale business that will only continue to be a threat. As criminals continue to refine their tools, technology, and methods it is more important now than ever to use antivirus software, strong authentication, unique passwords, and basic cyber hygiene. For hosting providers I would recommend providing effective abuse reporting channels that are reviewed by humans. Failure to respond to responsible disclosure reports of clear violations of terms of service such as hosting malware or stolen credentials only enables malicious infrastructure to remain active, exposing individuals to serious potential risks.
I make no allegations or claims of wrongdoing by the hosting provider or IP owner, nor against any of their staff, representatives, partners, affiliates, or associated entities. I am not asserting that internal systems or user information were ever in immediate danger. Any potential data-exposure scenarios discussed in this report are purely hypothetical and presented solely for educational and informational purposes; they should not be interpreted as evidence of, or implications about, an actual breach or loss of data integrity. Nothing in this report should be taken as an assessment or critique of any organization’s specific security controls, infrastructure, or operational practices.
As an ethical security researcher, I do not download or retain exposed data. My interaction is limited to capturing a minimal number of screenshots strictly necessary to confirm and document the issue. While the database was exposed it was possible to run search queries using only a web browser. I take no actions beyond identifying the vulnerability and responsibly notifying the appropriate parties. I expressly disclaim responsibility for any actions taken by others in response to this disclosure. The publication of these findings is intended only to promote awareness around data protection and privacy risks, with the goal of encouraging organizations to adopt proactive safeguards to prevent unauthorized access to sensitive information.