-

How to delete your WeChat account (complete guide)
This step-by-step guide will show you how to delete your WeChat account without hassle. We’ll also cover what you should consider before going through with the process and what happens to your data ...
-

What is the Signal app and how does it keep your messages private?
Signal is a messaging app that’s known for its privacy, but what does it actually offer? This guide covers everything you need to know about Signal and its core features. We took a deep dive into ho...
-

Is Brave browser safe? Everything you need to know about its privacy and security
Brave positions itself as a privacy-focused browser, but does that mean it’s any safer than more popular options like Chrome and Firefox? In this overview, we’ll analyze how Brave handles tracking...
-
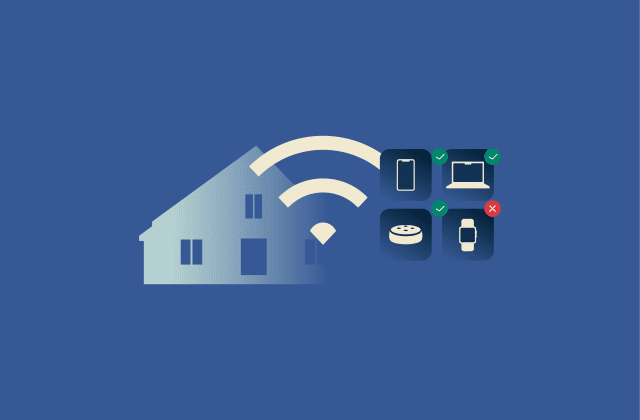
How to control internet access at home
Many households struggle to keep their home network controlled and organized. New devices connect every day, kids begin to spend more time online unsupervised, and unwanted activity can slip through w...
-

How to block someone on WhatsApp (step-by-step guide for all devices)
Blocking a person or business on WhatsApp stops their messages, calls, and status updates from reaching you. It also hides whether you’re online, when you were last active, and any profile photo cha...
-

Military romance scams: How to protect yourself
If someone you’ve met online claims to be in the military and is asking for money, gift cards, or sensitive information or photos, pause before sending anything. These are common red flags of a mili...
-
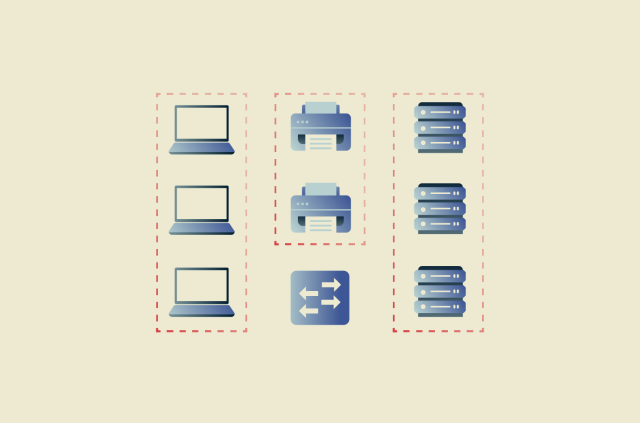
What is a VLAN? A complete guide to virtual LANs
A virtual local area network (VLAN) is a method of segmenting a single physical LAN into multiple separate networks through software. This guide covers how VLANs work, the possible benefits they bring...
-

Hinge scams: Protect yourself from fake profiles
Not every match on Hinge is genuine. Cybercriminals create fake profiles on the platform to exploit trust and emotion. Such scams can have a significant impact on finances and overall wellbeing. This ...
-

Data sovereignty: What it is and compliance considerations
Every digital interaction generates data. Often, it moves across borders; a login request in Paris might be processed on servers in California and stored in Singapore. Given this constant global excha...
-

SSL VPN vs. IPsec: Which VPN protocol is right for you?
The debate between Secure Sockets Layer (SSL) VPN and Internet Protocol Security (IPsec) is often framed as an enterprise IT question: how to securely connect corporate networks or remote employees. B...
-
- Pricing
- VPN for Teams
-
-
ExpressVPN Intudstry-leading, ultra-fast VPN with secure servers in 105 countries.
-
ExpressMailGuard Private email relay service to protect your inbox and identity.
-
ExpressKeys Secure password management, multi-factor authentication, and more.
-
ExpressAIComing soon The first consumer AI powered by confidential computing for privacy-led intelligence.
-
Identity Defender Powerful suite of ID protection, monitoring, and data removal tools
- View All Products
-
- My Account

