ExpressVPN blog
Your destination for privacy news, how-to guides, and the latest on our VPN tech

Latest Posts
-

Is hotel Wi-Fi safe? How to browse securely while traveling
Free Wi-Fi has become standard in hotels all over the world, which makes it easy to stay connected while traveling. But is hotel Wi-Fi safe? The short answer is no. Many hotels don’t take the time t...
-

What is a VPN kill switch and how does it work? (+ setup guide for different devices)
A VPN masks your IP address, encrypts your traffic, and conceals your activity from third parties and potential eavesdroppers—until the moment the connection drops. That short gap is all it takes fo...
-
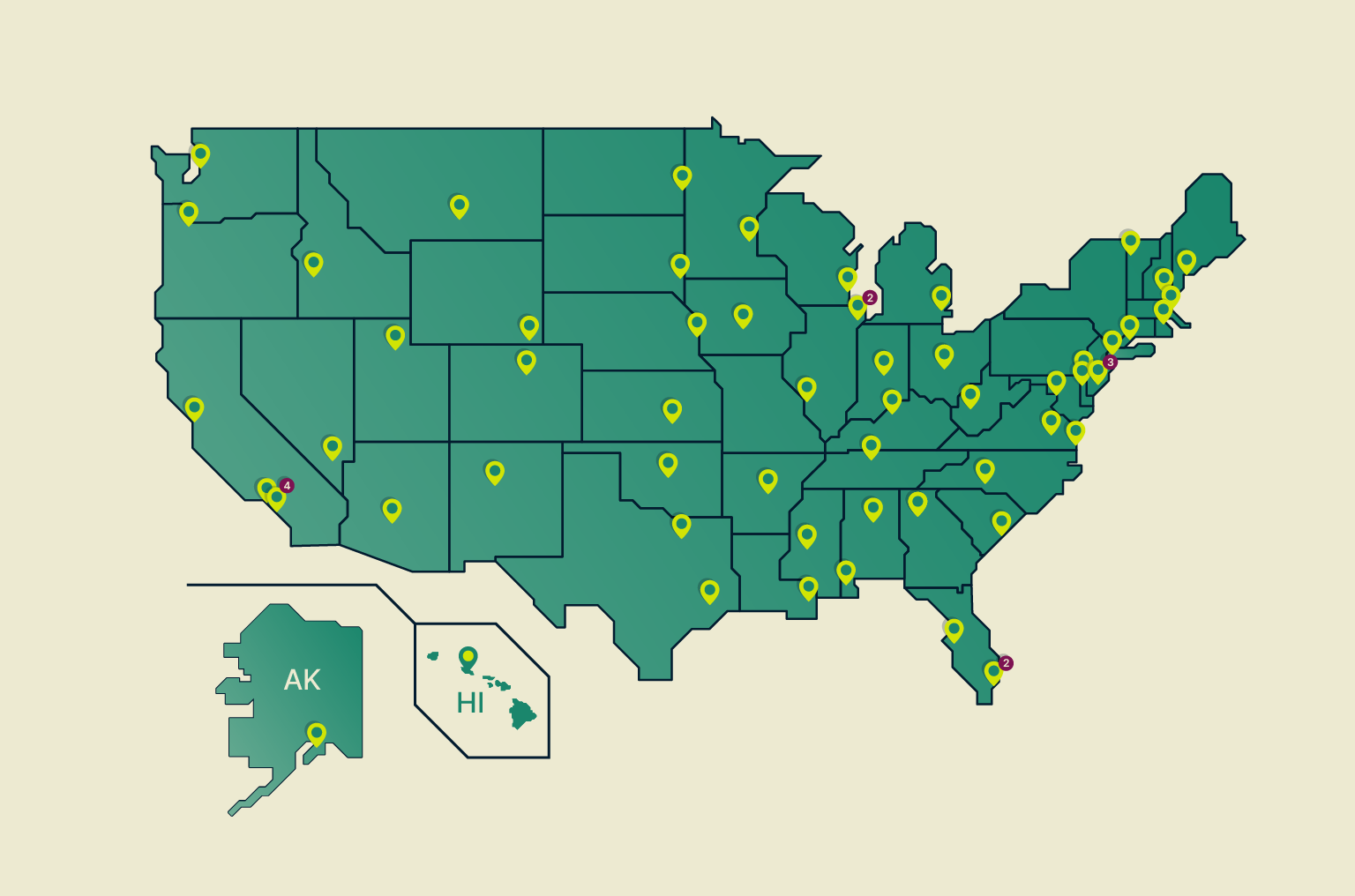
ExpressVPN now has servers in all 50 U.S. states—here’s what that means for your privacy
State laws are reshaping the internet. Rules about data collection, content access, and identity checks now vary depending on where you live. As a result, the online experience in the U.S. is becoming...
Featured
See AllFeatured Video
-

Top 10 video games that will change how you view privacy
If you love online gaming and are interested in privacy, check out these video games that involve hacking, cybersecurity, and surveillance. Not only are they fun, but they’re designed to give...








