
- Cyber attacks were expected to have cost the world 8 trillion USD in 2023, with that number expected to rise to 9.5 trillion in 2024 and 10.5 trillion in 2025.
n - IBM's latest Cost of Data Breach report reveals an all-time high in data breaches, with the average cyber attack resulting in losses reaching 4.45 million USD. The healthcare industry reports the highest average loss to data breaches at 10.93 million USD annually.
n - The U.S. loses an average of 9.48 million USD to data breaches globally each year, followed by the Middle East, which loses 8.07 million USD yearly.
n - Individuals are not spared from cyber threats either, and are especially susceptible to phishing and social engineering attacks.
n - Digital countermeasures to combat cybercrime include strong authentication protocols, encrypting your data with a VPN download, regular software updates, and vigilance against common cyber attacks.
Cyber attacks are becoming more frequent and sophisticated, posing significant threats to businesses, governments, and individuals. In 2023, cyber attacks, ranging from data breaches to hostile account takeovers, were estimated to have cost 8 trillion USD globally. This year, that number is expected to rise to 9.5 trillion USD, as reported by research company Cybersecurity Ventures. The rise of AI technology will likely push this cost even higher, with projections suggesting an 11% increase to 10.5 trillion USD in 2025.
A survey conducted by Statista with industry leaders revealed that cyber attacks are one of the biggest threats to a business, followed by business interruptions and macroeconomic developments. According to the survey that ran from 2018 to 2023, 34% of respondents ranked cyber incidents as their top concern.
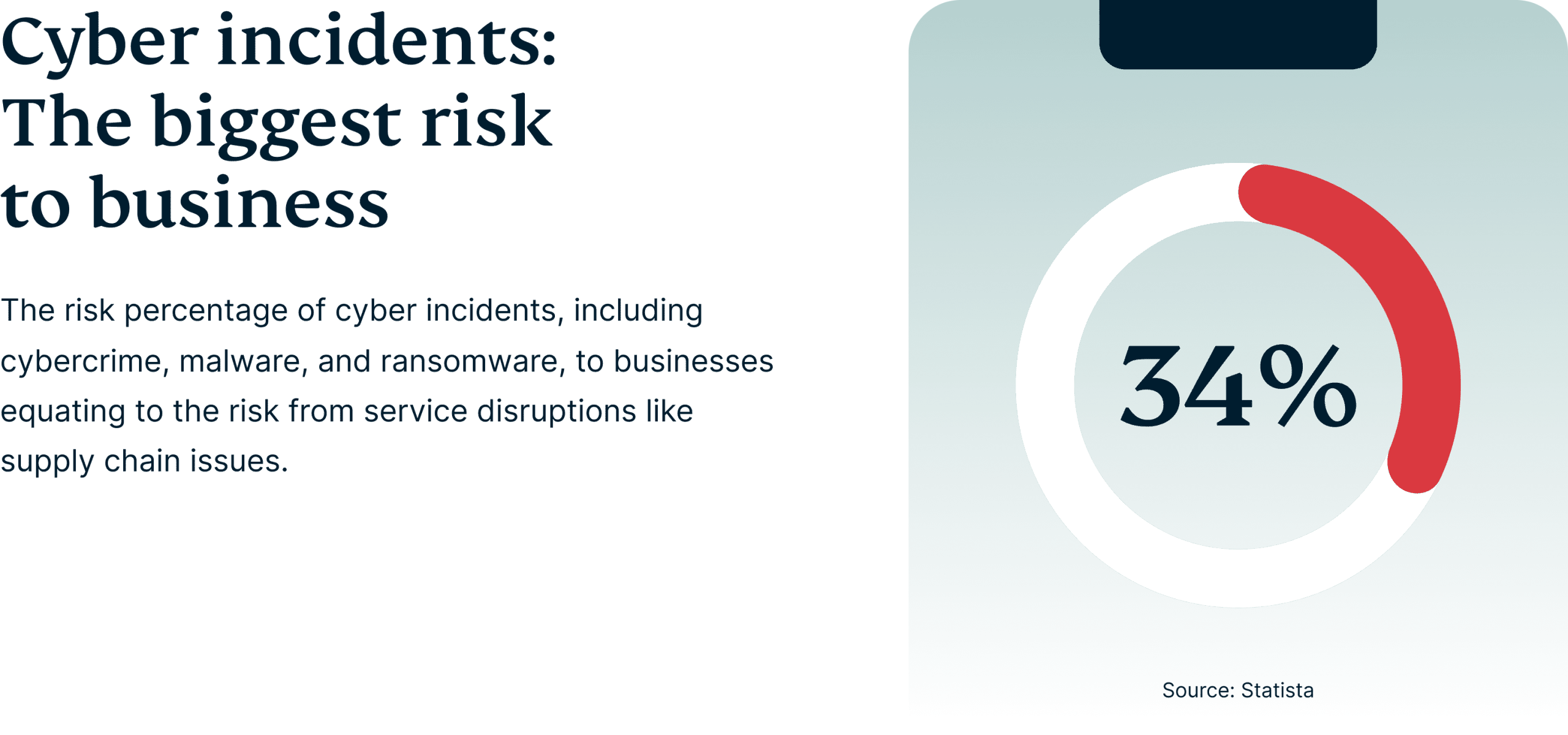
And, while businesses certainly feel the heat, the impact on consumers is equally alarming. Cyber threats such as data breaches, identity theft, and fraudulent transactions directly affect individuals, leading to financial losses, privacy invasions, and long-lasting consequences.
How much could we lose to cyberattacks in the future?
Forecasting the exact financial toll of cyber attacks in the coming years is challenging, owing to the dynamic and complex nature of digital threats. However, insights from Cybersecurity Ventures, reflecting on the last five years, provide a framework for future projections.
| Year | Estimated annual cost of cyber-attacks globally (USD) | Percentage increase from previous year |
| 2024 | $9.5 trillion* | 19% |
| 2025 | $10.5 trillion* | 10.5% |
| 2026 | $11.3 trillion** | 7.6% |
| 2027 | $12.4 trillion** | 9.7% |
| 2028 | $13.8 trillion** | 11% |
| 2029 | $15.6 trillion^ | 13% |
| 2030 | $17.9. trillion^ | 15% |
Sources: *Cybersecurity Ventures **Statista ^Our own projections
These figures take into account technological advancements, industry trends, and possible global events that could impact the cost of cybercrime attacks. Both attackers and defenders constantly develop new tools and techniques, impacting the cost and effectiveness of both attacks and mitigation efforts. At the same time, geopolitical situations and economic conditions can influence the frequency and nature of cyber attacks, making cost predictions even more complex.
But who pays for the damages?
According to IBM’s 2023 Cost of Data Breach report, it’s the customers. Companies that have suffered from cyber attacks generally pass these incident costs to consumers in the form of increased service and subscription prices.
To understand how we can reduce the cost and impact that cyber threats could have on us, it’s necessary to understand the various types of attacks, how they work, and who the biggest victims are.
The evolving landscape of cyber attacks
The rising tide of data breaches
Data breaches are among the most common cyber attacks affecting companies and individuals. In the same IBM report, these incidents reached a new peak last year. The average data breach cost globally increased by 15.3% since 2020, reaching 4.45 million USD.
In America, the situation appears particularly dire. The U.S. recorded the highest average cost for data breaches in 2023, at 9.5 million USD.
December 2023 was notably severe for U.S. consumers, with 443 publicly disclosed security incidents. Over 1.6 billion company records containing personal client and customer information were compromised. Major breaches included Real Estate Wealth Network, with over 1.5 billion records affected; Comcast Cable Communications (Xfinity), impacting nearly 36 million people; Delta Dental of California with 7 million customers affected; and Integris Health, leading to the leak of around 4.7 million individuals' personal information.
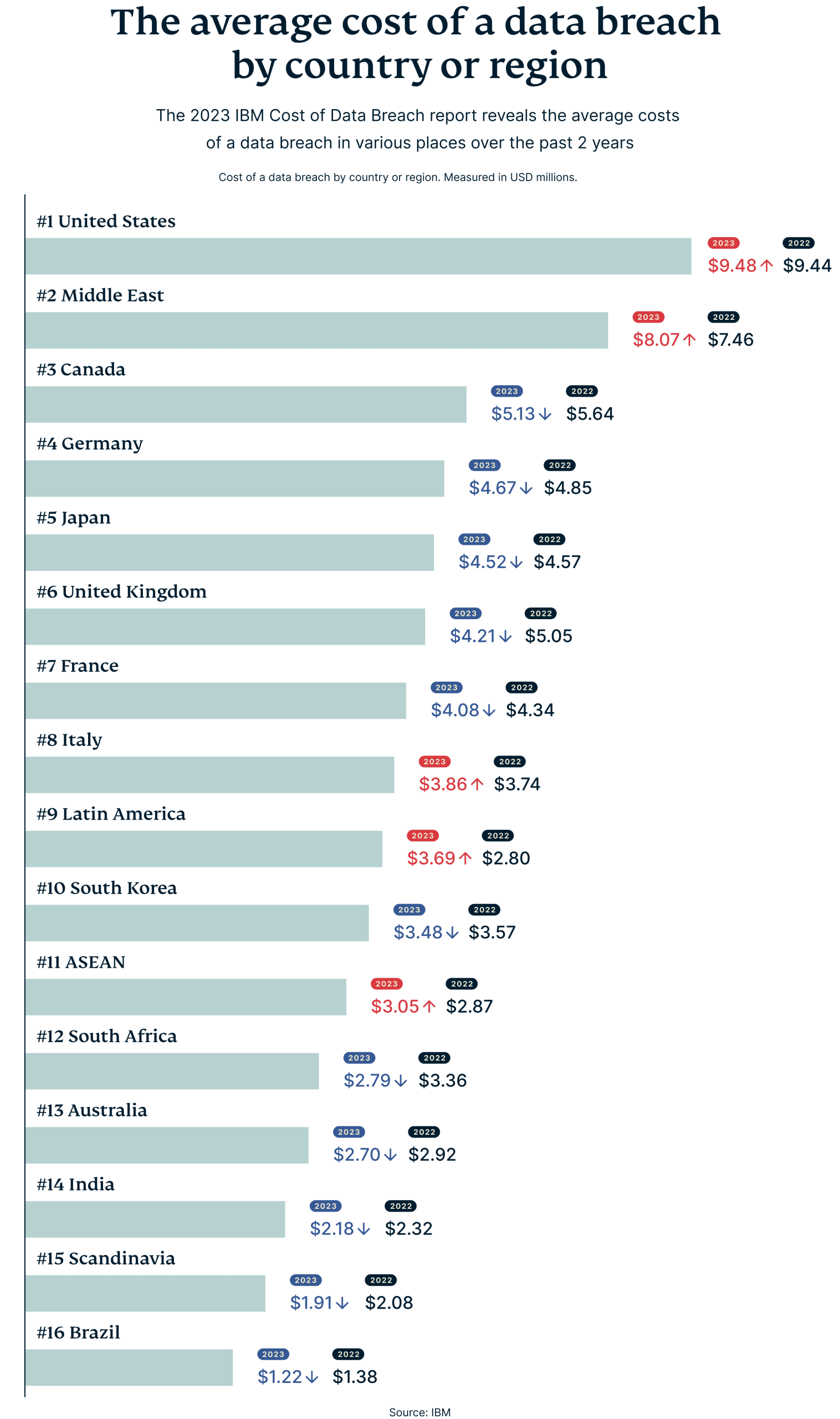
Globally, the Middle East retained its position as the second-most affected region, with an average data breach cost of 8.07 million USD, an increase of 8.2% from 2022. In contrast, Canada and Germany experienced decreases in average costs, with Canada seeing a 9% drop to 5.13 million USD and Germany a 3.7% reduction to 4.67 million USD. Japan also observed a slight decrease. The reduction could be due to new laws and regulations imposed by the various governments to better curb cyber attacks.
While data breaches represent a significant aspect of the cyber threat landscape, the scope of cyber attacks extends far beyond. Today’s cybercriminals and hackers are harnessing the power of advanced technologies like AI and machine learning to execute more sophisticated and elusive attacks.
The escalation of ransomware
Ransomware, a type of malicious software designed to block access to a computer system until a sum of money is paid, has evolved significantly over its 30-year history—and it’s growing. In 2023, there was a 55% increase in ransomware cases from the previous year, with 4,368 cases reported.
But what’s caused this alarming increase in ransomware attacks? Several factors. More on this below.
Mastering minds: The art of social engineering
Social engineering attacks, such as phishing, continue to be prevalent, exploiting human psychology rather than system vulnerabilities. These attacks typically involve deceiving individuals into revealing sensitive information or granting access to restricted systems. The human element often represents the weakest link in cybersecurity.
The transition to remote and flexible work has exacerbated these risks. Cybercriminals exploit vulnerabilities in home networks and inadequately secured company remote access systems. Personal devices used for work purposes also increase the risk of security breaches. For example, a simple phishing email sent to a personal device can lead to unauthorized access to an entire company’s network.
Smart devices and the Internet of Things (IoT) further extend the battleground. These devices, while convenient, often lack strong security, making them susceptible to attacks that threaten both personal privacy and corporate security. For instance, a compromised smart home device can be a gateway for attackers to access sensitive personal and work-related information.
Weak links: How supply-chain attacks topple business security
In 2024, the cybersecurity landscape is increasingly shaped by the threat of supply chain attacks, which are evolving in sophistication and scale. Supply chain attackers usually target and exploit the most vulnerable points in a supply chain.
These are often third-party vendors or suppliers with less stringent security measures. Once a weak point is compromised, attackers use it as a foothold to access larger, more secure systems. This could involve injecting malicious code into software updates or using stolen credentials to access secure networks. MOVEit, a managed file transfer software used for secure data transfer, became a victim of a supply chain attack in 2023. The software is used by 1,700 software companies and 3.5 million developers in industries such as healthcare, finance, technology, and government.
Deepfakes and the emergence of AI cybersecurity threats
As 2024 marks a crucial election year in the U.S., the rise of AI-generated threats, particularly deepfakes, emerges as a major security concern. The September 2023 general election in Slovakia serves as a stark example of how deepfake technology can harm elections.
In the run-up to these highly contested parliamentary elections, the far-right Republika party utilized deepfake audio notes and videos to spread false information about Progressive Slovakia leader Michal Šimečka. These deepfakes altered Šimečka’s voice, falsely portraying him as discussing plans to rig the election and even increase beer prices. While the exact impact of these deepfakes on the final election outcome remains unclear, the incident did highlight the potent disruptive capabilities of this technology.
Corroborating this threat, Google Cloud’s Cybersecurity Forecast for 2024 indicates that generative AI could complicate the detection of phishing emails and potentially enhance the scale and efficiency of criminal activities. The accessibility and ongoing advancement of AI technology make it a formidable tool for attackers.
6 common types of cyber attacks
Understanding the impact of cyber attacks on various industries and individuals is important if we aim to combat them. Here, we delve into the most common cyber attack tactics, how they’re carried out, and their effects on businesses and individuals.
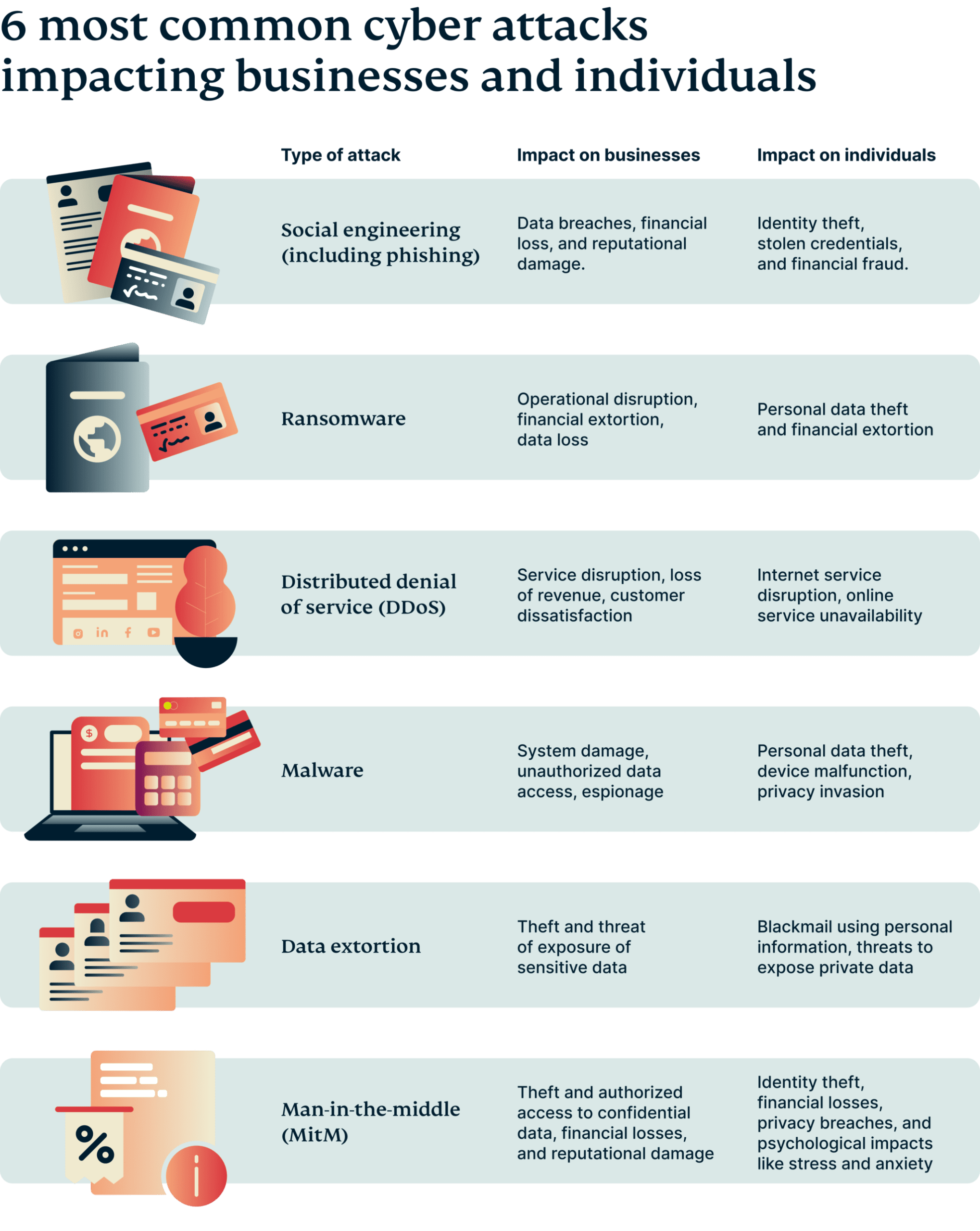
| Type of attack | Impact on businesses | Impact on individuals |
| Social engineering (including phishing) | Data breaches, financial loss, and reputational damage. | Identity theft, stolen credentials, and financial fraud. |
| Ransomware | Operational disruption, financial extortion, data loss | Personal data theft and financial extortion |
| Distributed denial of service | Service disruption, loss of revenue, customer dissatisfaction | Internet service disruption, online service unavailability |
| Malware | System damage, unauthorized data access, espionage | Personal data theft, device malfunction, privacy invasion |
| Data extortion | Theft and threat of exposure of sensitive data | Blackmail using personal information, threats to expose private data |
| Man-in-the-middle (MitM) | Theft and authorized access to confidential data, financial losses, and reputational damage | Identity theft, financial losses, privacy breaches, and psychological impacts like stress and anxiety |
Each of these attacks has a unique method of execution and impact, making them particularly effective against their intended targets.
Phishing
Phishing is when cybercriminals impersonate legitimate organizations via email, text messages, or other communication channels to steal sensitive information. These attacks often bait users into clicking malicious links or downloading compromised attachments, leading to identity theft, financial fraud, or access to secured systems. Phishing is the most common email threat, accounting for 39.6% of all email attacks. It's particularly dangerous because it targets human error rather than system vulnerabilities.
Ransomware
Ransomware is malicious software that encrypts a victim's files, rendering them inaccessible until a ransom is paid. This form of malware has seen a global surge, affecting 72.7% of organizations in 2023. The average ransomware attack cost is around 4.54 million USD, with recovery costs averaging 1.85 million USD.
Cybercriminals continuously enhance their methods, using more sophisticated encryption techniques that make it increasingly challenging for victims to recover their data without paying the ransom. Moreover, the rise of cryptocurrency has facilitated anonymous transactions, making it easier for attackers to receive payments without being traced.
Ransomware attacks have shifted from targeting individual systems to crippling entire networks, including critical infrastructure and major corporations, leading to significant financial and operational disruptions. The impact of these attacks extends beyond the immediate financial loss; they often result in long-term reputational damage and loss of customer trust in the affected organizations.
DDoS attacks
DDoS, or Distributed Denial of Service, attacks are a type of cyber attack where computer systems are used to target a single service, such as a website, server, or network. The aim is to make the online service unavailable by overwhelming it with traffic from multiple sources. It's like a traffic jam clogging up with so many cars that it prevents regular traffic from reaching its desired destination.
In 2023, DDoS attacks saw a significant increase both in frequency and intensity, according to cybersecurity company Cloudflare. Q4 saw a 117% year-over-year increase in network-layer DDoS attacks and overall DDoS activity targeting retail, shipment, and public relations websites during the holiday season.
Malware
Malware, short for malicious software, encompasses various forms of harmful software, including viruses, worms, and Trojans. These programs can infiltrate, damage, or disable computers, systems, and networks, allowing cybercriminals to snoop on your activity.
A common example of a malware attack is a loader attack—stealthy and multi-stage cyberattacks that leverage small, often legitimate-looking programs (such as a PDF reader) called "loaders" to deliver and execute malware on a victim's computer covertly. The program is called a loader as its role is to download malware in the background while giving the appearance of a legitimate tool or software.
The total number of unique malware programs has exceeded 1 billion, with Trojans making up 58% of all malware. Malware can result in unauthorized data access, system damage, and espionage.
Data extortion
Data extortion involves cybercriminals stealing sensitive data and threatening to release it unless a ransom is paid. This tactic was involved in 27% of cyber attacks in 2023. Unlike ransomware, which prevents access to data, data extortion involves actual data theft and poses a threat of public exposure or sale of the stolen data.
Data extortion attacks are usually conducted through data breaches or exfiltration. The first step involves the attackers gaining access to your system and stealing your data. Once the data is stolen, it's transferred to the attackers' servers, creating a copy beyond your reach. The attackers then contact you, revealing that they have your data and making their demands clear. They might threaten to release the information publicly, sell it to the highest bidder, or use it for other malicious purposes such as identity theft or fraud.
Unfortunately, paying the ransom for both data extortion and ransomware attacks doesn’t guarantee that you’ll get your data back or that the perpetrators will delete your data from their servers.
Man-in-the-Middle Attacks (MitM)
MitM attacks occur when a hacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other. These attacks can occur in any form of online communication, such as browsing, emailing, or even secure transactions. MitM attacks can lead to the theft of personal information, login credentials, and financial information, posing a significant risk to both individuals and businesses.
MitM attacks accounted for 35% of Wi-Fi exploitation activity in 2023, demonstrating their prevalence, especially in environments with public Wi-Fi, which are often less secure.
Who is the most vulnerable to cyber attacks?
Cyber attacks can target any individual or business, but certain sectors are more susceptible due to the nature of their operations and the sensitivity of the data they handle. Industries like healthcare, finance, and retail, integral to people's daily lives, are particularly vulnerable.

Healthcare and finance
These industries are prime targets because they hold critical data. Healthcare records contain sensitive personal information, including Social Security numbers and medical histories, making them attractive for identity theft, insurance fraud, and extortion. Payment information, like credit card details, is monetizable and coveted for fraudulent transactions or resale in the criminal underground.
In 2023, the healthcare sector experienced the highest average cost of data breaches for the 13th consecutive year, with costs reaching 10.93 million USD. This emphasizes the sector's vulnerability, not just in terms of potential financial loss but also in the disruption of critical services. The reliance on both cloud and traditional technology platforms increases the risk and cost of breaches.
Manufacturing
The manufacturing industry is another major target, particularly for ransomware attacks, accounting for 30% of all incidents in 2023. This industry's susceptibility stems from its low tolerance for operational downtime, which can make companies more likely to pay ransoms to resume production quickly.
IT sector
The IT sector is also a significant target due to its central role in maintaining essential services and the fact that it’s the backbone of digital infrastructures. The potential for high-impact disruptions makes it a lucrative target for cybercriminals.
High-profile individuals
Beyond industries, politicians, high-net-worth individuals, and influential figures are also at risk, particularly for deepfake and data exploitation attacks. The Slovakian election incident mentioned above illustrates how these types of attacks can be used to manipulate public opinion or discredit individuals.
These escalating threats to various industries underscore the necessity for robust countermeasures, considering that individuals will also be affected, which leads to the question…
What’s being done to combat cyber attacks?
There is a notable increase in cybersecurity investments in response to the growing cyber threat. For instance, DigitalOcean reported that 37% of companies in the U.S. plan to increase their cybersecurity spending. This surge is driven by the adoption of advanced security software, the modernization of legacy systems, and the emergence of new threats from generative AI.
However, the responsibility to combat cyber threats extends beyond corporations. Government rules and policies also shape comprehensive national cybersecurity strategies. This includes developing strong cyber defenses, fostering public-private intelligence-sharing partnerships, and investing in cybersecurity infrastructure.
Additionally, leaders can support education and training programs to build a skilled cybersecurity workforce and introduce legislation that enforces stringent cybersecurity standards. A notable example of international collaboration is a joint initiative by Australia, Germany, Canada, the Netherlands, New Zealand, the UK, and the U.S. to guide software development companies and engineers in creating more secure technological products. Such partnerships are essential as cyber threats often cross borders, requiring coordinated global efforts for effective deterrence and response.
What you can do to protect yourself from cyber attacks
The responsibility for cybersecurity doesn’t just fall on companies and national leaders; it also rests on individuals. Everyone has a part to play in preventing cyber attacks, requiring a comprehensive approach that includes technical measures, awareness, and adherence to robust security policies. As individuals, we have the power to significantly bolster our own cyber defenses through a few key actions:
1. Adopt strong authentication protocols
Strong passwords are your first line of defense against cyber attacks. Most security experts recommend using a password manager to securely generate and store complex, long passwords whether on work or personal accounts.
Enforcing strong authentication measures, such as two-factor authentication (2FA) or multi-factor authentication (MFA), is a great way to add extra security layers to any of your accounts. This ensures that even if login credentials are compromised, unauthorized access is still prevented.
2. Consider using a VPN
While downloading a VPN doesn't make you immune to popular attacks like phishing, it significantly enhances your digital security in several ways. VPNs provide encryption and secure connections, particularly on networks where trust is questionable, such as public Wi-Fi in cafes, hotels, or airports. This secures your connection from Man-in-the-Middle attacks and DDoS attacks.
Thanks to post-quantum encryption algorithms, they are especially effective in safeguarding your data from interceptive threats like "store now and decrypt later" attacks. This offers both immediate and future protection for your online data. We recommend opting for a comprehensive solution like ExpressVPN that often includes tools like password managers, assisting in meeting robust authentication standards and managing your passwords more securely.
3. Update all your software regularly
Software updates and patches are designed to address known vulnerabilities in operating systems, applications, and other software components. Cybercriminals often exploit vulnerabilities in outdated software to gain unauthorized access or deploy malicious code. Organizations can significantly reduce the risk of such exploits by staying current with software updates.
4. Being vigilant could protect you
It’s important to remain vigilant and inform yourself about the latest scam tactics to avoid becoming a victim. Many scams are designed to obtain personal information like names, addresses, and Social Security numbers through phishing emails and malware. Therefore, it’s important to familiarize yourself with the signs of these scams to protect yourself from falling prey to them.
Some signs that you’re being targeted for a scam include receiving text messages or emails from people you don’t know that include unknown links, typos, and grammatical errors.
Companies also need to ensure employees are trained to understand social engineering and phishing techniques.
5. Report any suspicious online activities
Although reporting suspicious activities might seem minor, its impact is far from negligible. According to IBM’s report, it takes organizations an average of 204 days to identify a data breach, followed by an additional 73 days to contain it. By alerting to suspicious activities early, individuals can greatly aid companies in detecting and responding to breaches more quickly. This not only reduces the duration of the breach but also potentially limits the extent of the damage.
FAQ: About cyber attacks
What is a cyber attack?
Who are the most common targets of cyber attacks?
What are the most common types of cyber attacks?
- Social engineering attacks: This includes phishing attacks that trick people into giving up personal information by disguising them as trustworthy entities. For example, a scammer could create a website interface similar to a financial institution that tricks users into entering their details.
- Malware: This encompasses various forms of harmful software, including viruses, worms, trojans, and ransomware. Malware is often delivered through email attachments or software downloads and can damage or disable computers, steal data, or enable attackers to take control over affected systems.
- Ransomware: A type of malware that encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. Ransomware can spread through phishing emails or by exploiting security vulnerabilities.
- Distributed denial of service attacks (DDoS): These attacks aim to make a machine or network resource unavailable to its intended users by overwhelming the target with a flood of internet traffic.
- Data extortion: Although similar to ransomware, data extortion usually involves hackers stealing data and storing it to either reveal it or sell it to others. Essentially, data extortioners are interested in making money off the data they’ve stolen and aren’t necessarily keen on returning them, even if they’ve been paid.
- Man-in-the-middle attacks (MitM): This occurs when attackers intercept and alter or relay communications between two parties who believe they are directly communicating with each other.
What can you do to protect yourself from cyber attacks?
- Use strong passwords and multi-factor authentication: Your first line of defense against hackers is strong passwords that keep malicious actors out. You can fortify this defense using multi-factor authentication methods that secure your logins.
- Use a VPN: Using a VPN like ExpressVPN while using public Wi-Fi, whether in cafes or at airports, helps encrypt your data and protects it from potential spies.
- Keep software updated: Software updates are like chainmail upgrades to any armor. Patch them promptly to stay secure.
- Stay vigilant: Watch for and be aware of phishing, malware, and other digital scams. Being aware of the various scam tactics prevents you from falling victim easily.
- Report any suspicious activity: It might seem small, but it can help alert others and stop attacks faster.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN




