What is malware? How viruses, trojans, and ransomware work


Malware, or "malicious software," is a term for a variety of viruses, spyware, or ransomware (cryptolockers) that cause harm to a user, their data, or devices.
The term malware implies malicious intent on the side of the software developer, as opposed to, for example, unintentional software bugs, which can also cause loss of data or damage to a device.
[Keep up with the latest in privacy and security. Sign up for the ExpressVPN blog newsletter.]
Previously, malware was described more precisely, using terms like virus, trojan, worm, or keylogger. These terms have fallen out of fashion as they are overly precise and often used incorrectly in popular usage.
The different types of malware
Today, most malware comes in the form of a virus and is named differently based on its function. But malware can also be introduced inadvertently through a software vulnerability.
How malware is spread
We categorize malware by how it spreads. Viruses and worms both replicate themselves on an infected machine, for example, by finding other machines on the same network with the same vulnerability.
But while worms are mainly designed to damage the network itself (for example through a denial of service attack), viruses inflict damage on the users’ device.
Trojans do not replicate themselves. Rather, the user is tricked into installing the malware, for example, through social engineering or phishing. A trojan can come disguised as other software or even be part of apparently legitimate software and will make use of vulnerabilities to install itself with minimal user interaction. Trojans can also come as a plug-in to popular software or as a fake update.
How malware works and what it does
Whether dealing with a worm, a trojan or a virus, we can differentiate malware by their functions. Today, the most common kind of malware tends to be ransomware, adware, spyware, and scareware.
Ransomware (a.k.a. cryptolockers)
Ransomware, or cryptolockers, is a type of malware that encrypts your files upon infection. Ransomware makes all of your personal files inaccessible and can even render the entire computer unusable. The software will demand a payment, typically in gift cards or Bitcoin, to decrypt your storage. As ransomware have become highly profitable compared with other types of malware, many vulnerabilities are typically exploited by this type of malware.
Spyware
Spyware refers to any malware that collects your data without consent and can come bundled with free apps, or it can infect your computer through a virus or trojan.
Spyware can also be directly installed on your devices by somebody attempting to control you. Some spyware, like Predator spyware, is designed to continuously collect your location data, app usage, passwords, and contact list. The most common types of spyware are keyloggers, which record all your keystrokes, and screen-scrapers, which regularly take screenshots of your device.
The ExpressVPN Digital Security Lab has published extensive research on spyware.
Adware
Before ransomware, adware was a common kind of "less harmful" malware that would monetize itself by showing advertisements to the user, for example, in the form of a toolbar in the browser.
Scareware
Another type of malware is scareware, which does not actually harm the users’ device. Instead, it attempts to scare the user into purchasing expensive subscriptions to remove a nonexistent or hypothetical threat. Today, most anti-virus solutions can be regarded as scareware.
How to protect yourself from malware
There are three easy actions you can take to protect yourself from malware right now.
1. Always keep your device up to date
Viruses and many trojans rely on software bugs and vulnerabilities to spread. Install patches whenever they become available and enable automatic updates on your device when possible.
2. Always verify the source of software before installing
Protect yourself from malware bundled in with software by only downloading it from the official source, and verifying the integrity of the software, for example, by checking its hash or PGP signature.
3. Use a firewall
Your personal computer should never accept incoming connections. Your machine should come with a simple firewall installed that you should not disable. If you are behind a router, you likely enjoy some firewall privileges too. Running a VPN on your machine will also act as a firewall.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN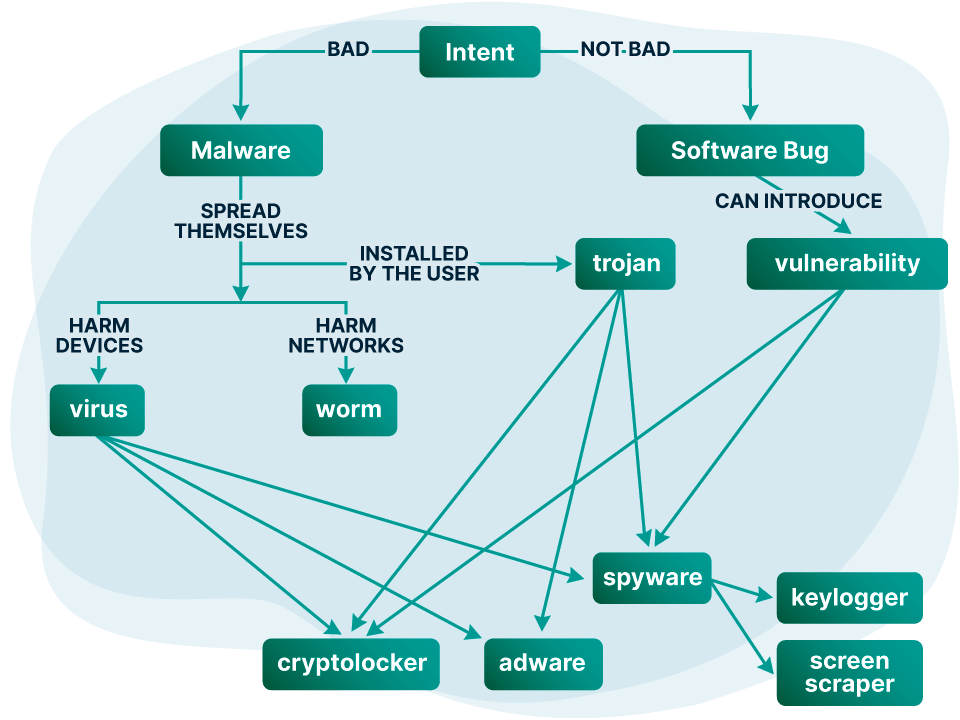





Comments
Tiktok fans
Ok
checking its hash or PGP signature. Can you please provide some examples of that? What or how should I look to find it?
My privacy problem is there are two accounts added to my boot up in my system app. I see my name then a /*name and another one after. So even if I upgrade, they get protection too. What do I do to fix this or will this VPN fix this?
How do I get static ip from this connection
If you mean ExpressVPN, we only offer dynamic IP.
Can anyone help us track down someone's who using VPN to be untraceable he's or she's leaking harmful information on social media