What is perfect forward secrecy? Learn how it protects your privacy

Encryption is a crucial part of online security, but what happens if a cybercriminal finds the key to undo encryption and gain access to your data? It’s a scary prospect, but perfect forward secrecy (PFS) helps to ensure that even if someone does find a way to decrypt your data, they’ll only be able to access a limited amount of it.
This guide looks at what perfect forward secrecy is, explaining how it works and the value it brings.
How perfect forward secrecy works
Perfect forward secrecy is a feature of encryption protocols that ensures each session or connection uses a unique temporary key generated for that specific session. These keys are not derived from a long-term, static private key regularly used for authentication, which is critical to the security benefits of PFS.
Because of this design:
- Each session’s data is encrypted separately.
- If a session key is compromised, only that session’s data is exposed, and not any past or future communications.
- Even if a long-term private key is later stolen or leaked, past encrypted sessions remain secure, as their session keys were never derived from that long-term key.
How public-key encryption works
In order for two devices to communicate securely and privately, they have to share encryption keys with each other, and those keys have to be shared securely as well. Public-key encryption solves this issue by creating two keys—one public, one private.
The public key encrypts the data, and the private key decrypts it. You can share the public key around with whoever needs it to encrypt data while maintaining your own private key for decrypting, as and when necessary.
This type of cryptography is called asymmetric, as it differs from symmetric key cryptography, in which the same key is used for both parts of the process—encryption and decryption. In PFS, typically, both asymmetric and symmetric encryption are employed.
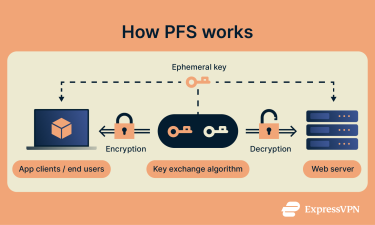
Key exchange and session keys explained
Perfect forward secrecy is built on two core concepts: key exchange and session keys.
Key exchange is the process of securely establishing a shared secret key between two parties—typically a client (like your device) and a server (such as a VPN server or website)—so that encrypted communication can take place.
Algorithms like Ephemeral Diffie-Hellman (DHE) and Ephemeral Elliptic Curve Diffie-Hellman (ECDHE) are commonly used in PFS. These involve the use of ephemeral key pairs—temporary asymmetric keys that exist only for the duration of a single session. Each party generates a private and public ephemeral key, and they exchange public keys to calculate a shared secret. These ephemeral keys are discarded immediately after the session ends, which is what enables PFS.
From this shared secret, a session key is derived. This session key is symmetric—the same key is used both for encrypting and decrypting data. It is this key that’s used to protect the actual content of the communication (such as your VPN traffic, messages, or web activity) for that specific session.
With PFS on a VPN, for example, a new ephemeral key pair is generated each time a user connects to a VPN server. This process results in a fresh session key for that particular connection. If the user disconnects and reconnects, a brand-new session key is generated, ensuring that each session is isolated and secure—even if a previous session key were somehow compromised.
What problem does perfect forward secrecy solve?
Public-key encryption solves the problem of how to encrypt and decrypt data securely if you don’t have a secure channel to share the key beforehand, but it still poses a challenge: what if a user’s or server’s private key is compromised? It could then, theoretically, be used to decrypt large amounts of data, including past, present, and future communications, causing major privacy issues for those concerned.
That’s the problem that perfect forward secrecy solves. It generates new keys all the time, instead of relying on just one of them and repeatedly using it. Thanks to this, even if an individual key is accessed, compromised, or stolen somehow, the cybercriminal who does so will only have access to the data encrypted with that particular key.
Which encryption protocols support PFS?
Multiple encryption and VPN protocols support perfect forward secrecy, including:
- Transport Layer Security (TLS)
- OpenSSL
- Secure Shell (SSH)
- IPsec
- OpenVPN
- WireGuard
- Lightway (ExpressVPN’s proprietary protocol)
To be more precise, for PFS to work, a specific form of key exchange algorithm must be used, such as Ephemeral Diffie-Hellman (DHE) or Ephemeral Elliptic Curve Diffie-Hellman (ECDHE). So, as long as a protocol supports one or both of these algorithms, it should be able to support PFS, also.
Benefits and limitations of perfect forward secrecy
Advantages of using PFS
There are numerous benefits of using PFS in terms of how much it strengthens online security and data privacy. These include:
- Stronger security overall: Cybercriminals can use certain techniques, like brute force attacks, to eventually penetrate secure encryption systems and decrypt data. However, with PFS protection, it becomes far harder and more time-consuming for them to do so.
- Limits the impacts of cybercrime: With PFS enabled, even if a cybercriminal accesses an encryption key, they’ll only be able to obtain a relatively small amount of data, rather than all of your past and future communications.
- Protects various forms of data: PFS can be applied to web data, instant messaging data, emails, and more.
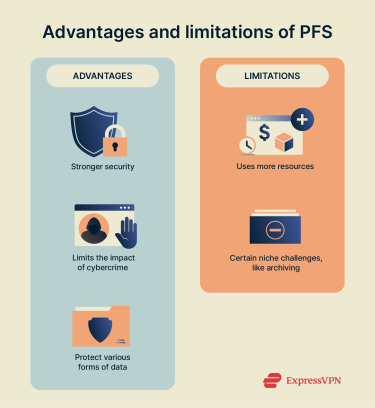
Drawbacks and considerations
There aren’t exactly any “cons” to using PFS, as it’s a very positive force for the cybersecurity landscape on the whole. However, there are a couple of specific challenges it can present, which are still worth considering.
Using PFS demands a certain level of computing power and resources, which can have a slight impact on speed and performance, especially when PFS is deployed at a large scale. However, modern hardware and optimized implementations (e.g., hardware acceleration for ECDHE) have largely mitigated this issue for most applications.
Another issue concerns archiving. Sometimes, organizations might want to archive encrypted data and reserve the ability to decrypt it in the future. But ephemeral keys, produced with PFS, disappear after each session, making the data almost irretrievable. This is not a flaw in PFS but a trade-off by design—prioritizing security over long-term access.
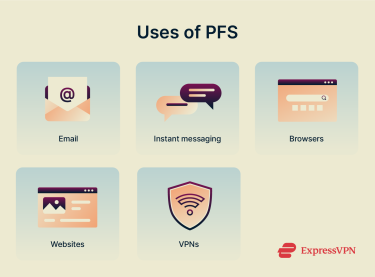
Real-world applications of perfect forward secrecy
To better understand the value and importance of PFS, it’s important to learn how and where it’s being used.
Where PFS is used in practice
PFS is becoming a more integral part of the online experience, featuring in:
- Secure mail providers
- Instant messaging applications
- Web browsers on both mobile and desktop
- Websites, including banking websites and online marketplaces
- VPN services, including ExpressVPN
Adoption across browsers and VPNs
All major internet browsers now support PFS, including Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari. PFS is typically enabled when these browsers negotiate HTTPS connections with servers that support ephemeral key exchange algorithms, such as DHE or ECDHE. In addition, many of the world’s leading VPN clients also make use of PFS to safeguard each individual user session, helping to strengthen the privacy and data integrity of their users.
How ExpressVPN uses perfect forward secrecy
ExpressVPN uses perfect forward secrecy to protect your data, generating unique encryption keys every time you connect to our secure servers around the world.
Whenever you establish a connection to secure ExpressVPN servers, including using our Lightway protocol, a unique encryption key is dynamically generated for your session using the ECDHE algorithm.
New keys are generated at the start of each subsequent session, when changing networks, or at 15-minute intervals.
Even in the very unlikely event that someone was able to obtain a singular key, it would only be useful for a very brief window, and all of your past and future connections would still be entirely secure.
FAQs: Common questions about perfect forward secrecy
Is perfect forward secrecy the same as end-to-end encryption?
No, end-to-end encryption (E2EE) is the process of encrypting data at both ends of a connection, from the sender to the receiver, so that it can’t be accessed or intercepted en route. Perfect forward secrecy, meanwhile, is a process of generating new encryption keys on a regular, recurring basis to safeguard data integrity. PFS can be a part of an E2EE system.
Can I enable PFS on my own server?
It is possible, yes. You will first have to select and implement the relevant cipher suites and ensure they are correctly ordered to run PFS on your server.
Should I enable perfect forward secrecy?
Yes, when given the choice, it’s almost always best to use PFS. It has almost no downsides, apart from using up slightly more resources, and delivers a lot of benefits in regard to security, privacy, and peace of mind.
What is an example of forward secrecy?
An example of PFS in action is when a user connects to a VPN for the first time, a unique encryption key will be generated for that session. If they disconnect or switch to a different server or network, a new key is generated, protecting each individual session independently.
Does PFS slow down internet speeds?
PFS may cause a small delay during session setup due to additional key generation, but this typically takes a fraction of a second and doesn’t noticeably affect browsing or streaming speeds for most users.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN







Comments
Perfect forward secrecy is available only via the proprietary ExpressVPN App, and not through services like OpenVPN standalone, but it should be as easy as adding a simple line of code to the OVPN file on the client and server side. Please add this to your services, it gives users an option to move away from the closed source ExpressVPN proprietary application while still maintaining their security.
Hi Julia, Any VPN based on OpenVPN is going to provide some form of perfect forward secrecy. You also don't need to use our app to make use of our service. Instead, you can download the open-source OpenVPN apps available for your platform, and use the configuration files to connect to our network, or any other network supporting OpenVPN configuration files. Hopefully this article can help: https://www.expressvpn.com/support/vpn-setup/manual-config-for-windows-xp-vista-7-8-with-openvpn/ Lexie
does this apply for lightway?
Thanks you and I not sure please help me
Needing help keeping the world out of my personal business thing that maybe they don't understand