How to encrypt your internet traffic and protect your privacy


Your internet traffic consists of a stream of data that travels between your device and the websites and services you use. Today, some of this data is encrypted by default, making it harder for potential eavesdroppers to spy on you. But not all traffic is encrypted, and different levels of encryption offer varying degrees of protection.
In this article, we’ll cover the basics of how encryption works and explain what you can do to increase your privacy. Keep reading to learn how to protect your online activity from both cybercriminals and your internet service provider (ISP).
What does it mean to encrypt internet traffic?
Encryption is the process of converting readable data into an incomprehensible ciphertext. This is achieved by running complex mathematical algorithms that scramble the data.
What is encrypted browsing traffic?
Browsing traffic refers to the data transmitted between your device and websites as you use the internet. Every website that uses HTTPS (Hypertext Transfer Protocol Secure) is encrypted. In contrast, traffic going to sites beginning with HTTP is generally not encrypted.
How encryption protects your online activity
Without encryption, any party intercepting your data could read it. If the data is encrypted, only users possessing the decryption key can read the data. Without a key, a threat actor would have to crack the encryption, which is infeasible with current technology.
Encryption vs. anonymity: What’s the difference?
While encryption creates a barrier to anyone trying to access your data, anonymity implies that none of your activity can be traced back to you. A much higher standard, complete anonymity is nearly impossible to achieve.
Encryption alone doesn't hide who you are, where your traffic is coming from, and where the traffic is going. HTTPS provides some protection from threat actors, but your ISP, network admins, and others can still see a lot of what you do online.
For greater anonymity, you’ll need to take extra steps like using Tor or, more practically, a VPN. Neither will offer perfect anonymity, but both do much to enhance privacy.
Why encrypting your internet traffic matters
Encryption has a long history and plays many crucial roles today, from safeguarding your personal information to guarding your digital privacy.
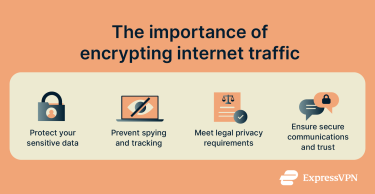
Protecting personal and financial data from prying eyes
If you enter information onto a site with a connection that isn’t encrypted, anyone intercepting the traffic can see exactly what you typed. This could include passwords, financial information, and more. Luckily, the vast majority of websites now require visitors to use HTTPS, offering a default level of encryption.
Defending against surveillance, tracking, and hackers
Encrypting your traffic is an effective way to thwart surveillance and tracking. It creates obstacles for anyone monitoring your connection, hiding many details of what you do online.
Note that while the encryption afforded by HTTPS obscures the content of your traffic, it won’t hide the domains that you connect to. Your ISP still records your connections and the sites you visit.
Whether you’re more concerned with being tracked by cybercriminals, tech companies, or your ISP, basic encryption alone is often not enough. In addition to HTTPS, it’s highly recommended to encrypt your entire connection with a VPN.
Ensuring compliance with privacy laws and regulations
For businesses, encrypting internet traffic may be required to comply with privacy laws and regulations. For instance, the GDPR (General Data Protection Regulation) requires companies to protect user data with (among other things) encryption.
Building trust in business and remote communications
Companies need strong security to maintain their reputation and earn customer trust. By encrypting communications, businesses can assure customers and partners that their private information is being handled with care.
Encryption also becomes vital for remote teams who rely on secure channels for internal communication and access to company resources. Encryption reduces the chance that any of this data will be compromised.
How to encrypt your internet and Wi-Fi traffic
Below are the various ways you can encrypt your web traffic.
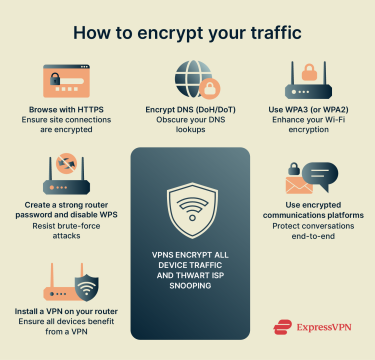
Use a trusted VPN provider
One of the most practical and effective ways to encrypt internet traffic is by using a trusted VPN like ExpressVPN. A VPN creates a secure, encrypted tunnel for all your traffic, shielding your data from potential spies, including your ISP.
Browse with HTTPS and privacy extensions
Websites with HTTPS use Transport Layer Security (TLS) to encrypt the connection between your browser and the site's server. With most browsers, you can ensure that your connection is benefiting from HTTPS by hovering over the address bar.
There are also helpful browser extensions you can use to ensure you’re always directed to the HTTPS version of a website if one is available. Additionally, you can use ExpressVPN’s browser extension to ensure all your browsing traffic is routed through the encrypted VPN tunnel.
Turn on DNS encryption (DoH or DoT)
DNS (Domain Name System) requests translate website names into IP addresses. These requests are unencrypted by default, meaning anyone snooping on your traffic can see the domains you visit. You can enable DNS encryption through protocols like DNS over HTTPS (DoH) or DNS over TLS (DoT) to keep your DNS private.
Choose WPA3 or WPA2 for your Wi-Fi network
If attackers breach your Wi-Fi, they can monitor activity across the entire network. Using a strong Wi-Fi encryption protocol greatly reduces this risk. In most settings, WPA3 is the best, most secure option. If your router doesn’t support WPA3, WPA2 is a good alternative.
Set strong router passwords and disable WPS
Setting a strong router password is an essential defense against brute-force attacks. Additionally, it’s critical to disable WPS on your router, as it is vulnerable to brute-forcing and can give attackers a vector into your network.
Use encrypted messaging and email apps
Choosing end-to-end encrypted messaging and email applications can be a great way to improve your overall security. End-to-end encryption safeguards communications by ensuring only the sender and intended recipient can read the contents of a message.
Install a VPN on your router for whole-home protection
Installing a VPN on your router ensures that every device benefits from extra encryption. Depending on your router, you may be able to install a VPN directly. If this isn’t possible, consider getting a router with a built-in VPN, like Aircove.
Try Tor browser for advanced privacy
The Tor browser adds extra layers of security and privacy by encrypting traffic and routing it through several nodes before it reaches its destination. Your ISP will see that you’re using the Tor network, and the Tor entry node will see your real IP address, however.
Using Tor with a VPN can add extra privacy by encrypting your traffic and masking your IP address before it enters the Tor network.
What does it mean when your network blocks encrypted DNS traffic?
When a network blocks encrypted DNS traffic, it generally means that the ISP or local administrator has blocked DNS query encryption protocols.
Understanding DNS encryption and why it matters
DNS requests are unencrypted by default. This amounts to a privacy vulnerability that third parties can exploit to monitor the domains you visit. Encrypting DNS queries defends against this form of surveillance and also protects you from DNS spoofing attacks, where attackers redirect users to malicious websites.
Why some networks block encrypted DNS
Some networks block encrypted DNS to ensure IT teams have the visibility needed to safeguard a network. With encrypted DNS, IT can’t monitor DNS logs, block malicious domains, and may experience compatibility issues with internal DNS systems.
Other networks block encrypted DNS to ensure regulatory compliance, as the lack of DNS logging could lead to breaches or legal issues.
The other common reason is to enforce content filters, such as those that block adult content.
How to keep DNS encrypted on restricted networks
The most straightforward way to keep DNS encrypted, even if the network restricts it, is to use a VPN that incorporates its own private and encrypted DNS. It doesn’t require any configuration, so all you need to do is install the app and connect to a server.
Another option is to configure DNS settings directly in your browser. For instance, if you use Chrome and enter chrome://settings/security in the address bar, you can enable the Use secure DNS option. Enabling this option will give you multiple DNS options, like Cloudflare, CleanBrowsing, or the option to add a custom DNS provider.
Can encrypted traffic still be blocked or tracked?
Yes, traffic can be blocked even if it’s encrypted. This is usually achieved by blocking specific ports. Additionally, there are also sophisticated NGFWs (Next-Generation Firewalls) that can analyze the patterns of encrypted traffic without actually decrypting it. If it detects something suspicious, the traffic may be blocked.
How ISPs and firewalls detect encrypted traffic
Even if your connection is encrypted with HTTPS, ISPs and firewalls may be able to detect some of what you’re doing. One method involves inspecting metadata. Some metadata remains exposed even if you’re using websites that have HTTPS encryption, and ISPs can use it to piece together your browsing activity.
Tools that help disguise or obfuscate encrypted data
Obfuscation is a technique that disguises encrypted internet traffic as regular traffic. This helps it remain stable on restrictive networks that specifically inspect encrypted data. Not every VPN is capable of this, but ExpressVPN has been built from the ground up to support obfuscation, so it remains reliable even on restrictive networks.
How to improve resistance to restrictions and throttling
Restrictions and throttling can be frustrating to deal with. The former can limit access to information, while the latter slows your connection, making the internet harder to use. A VPN can help reduce these issues by strengthening privacy and preventing throttling.
By encrypting your connection, a VPN can make it harder for ISPs to selectively slow down certain types of traffic, which can help reduce throttling. It also makes it harder for anyone monitoring your connection to see the details of your online activity.
Types of encryption technologies used online
To encrypt your internet traffic effectively, it helps to understand the core technologies that make it possible.
TLS and HTTPS
Most web traffic is encrypted using TLS (Transport Layer Security) and HTTPS. Traffic sent over HTTPS is wrapped in TLS encryption. Websites use TLS to maintain a secure connection. The successor to SSL (Secure Sockets Layer), TLS improves on the older protocol in various ways. TLS has three primary functions:
- Encryption: Shields data from third parties trying to spy on it.
- Authentication: Verifies that the parties exchanging information are who they claim to be.
- Integrity: Ensures the data isn’t tampered with in transit.
AES encryption (Advanced Encryption Standard)
The Advanced Encryption Standard (AES) is a symmetric-key block cipher used to secure all kinds of data, from financial records to classified government information. AES comes in different key lengths, such as 128-bit, 192-bit, and 256-bit, with 256-bit AES being the standard across many industries.
ExpressVPN uses 256-bit AES encryption to ensure that your data is protected with a virtually uncrackable cipher.
DNS encryption protocols (DoH, DoT, DNSCrypt)
As addressed above, unencrypted DNS requests can reveal information about your browsing habits. DNS encryption protocols help address this vulnerability.
DNS over HTTPS (DoH) encrypts DNS queries with TLS and sends them over HTTP, HTTP/2, or HTTP/3. It uses port 443, which is the standard for HTTPS traffic. DNS over TLS (DoT) also uses TLS to encrypt your DNS requests but communicates using port 853, which is specific to this protocol.
Now largely abandoned, DNSCrypt was another common method. It used cryptographic signatures to ensure that DNS responses are from the correct DNS resolver and have not been tampered with.
VPN protocols (WireGuard, OpenVPN, IKEv2)
VPNs use different protocols to establish a secure internet connection. Protocols affect speed, security, privacy, and stability.
OpenVPN is an open-source, highly customizable, and secure protocol that has long been an industry standard. IKEv2, known for speed and stability, is often used for mobile VPNs. WireGuard is a more modern protocol now used by a large number of VPNs.
Another option is Lightway, ExpressVPN’s proprietary protocol. It’s lightweight, fast, secure, and highly reliable, making it one of the most effective protocols available.
Why standard web encryption may not be enough
While TLS and HTTPS improve privacy, they don’t offer complete protection. In some circumstances, you may need further protection.
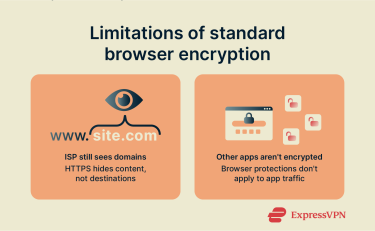
Limitations of HTTPS and browser-only protections
HTTPS encrypts the connection between your browser and the website you're visiting, but it has limitations. Your ISP can still see that you connected to a specific website, even if it can't see the exact details of your activity. Similarly, it doesn’t encrypt DNS requests, another source of potential exposure.
Furthermore, HTTPS only protects traffic in your web browser. Your activity on apps will not benefit from the same encryption. This includes app usage and other background data transfers, all of which may still be monitored.
Why a VPN adds an essential layer of security
Compared to default encryption, using a VPN provides improved privacy and security. In addition to providing system-wide encryption, your traffic will be routed through a secure, remote server. This means your IP address remains hidden, and your traffic is encrypted before reaching your ISP or other potential eavesdroppers.
How businesses encrypt internet traffic for remote teams
Businesses implement several strategies to ensure all team members operate with a secure internet connection, regardless of their physical location.
Encrypting internal chat and file-sharing tools
Secure messaging and file-sharing applications that provide end-to-end encryption are essential for remote teams. Mandating that such tools be used reduces the risk of internal communications being intercepted.
Using VPNs for secure access to company resources
A business VPN provides the network encryption necessary to ensure secure access to company resources. By requiring all remote employees to connect to a VPN, a company can create an encrypted tunnel between their devices and the corporate network, greatly reducing the ability of third parties to monitor traffic.
Protecting remote endpoints and cloud backups
Businesses must also ensure that data stored on employees' remote devices is encrypted. Additionally, sometimes remote employees use less secure personal systems to access company resources, which can put internal files at risk. This can be accomplished through endpoint security methods, such as antivirus software. Meanwhile, encrypted cloud storage services make it harder for sensitive files to be leaked.
FAQ: Common questions about encrypting your internet traffic
How do I encrypt my internet connection completely?
The most effective way to encrypt all the traffic on your home network is to install a VPN on your router. This encrypts all the traffic passing through your router, including all web traffic, hampering anyone trying to spy on your traffic.
Does a VPN encrypt all internet traffic?
A VPN encrypts all internet traffic to and from the device it’s installed on, unless certain apps or settings (like split tunneling) are configured to exclude some traffic. However, installing a VPN on your device doesn’t secure your whole network. To do this, you must install a VPN on your router or get a router with a built-in VPN, such as Aircove.
Is encrypted traffic 100% secure?
No security measure is absolute. While encryption significantly increases protection, advanced firewalls can still analyze patterns in encrypted data without decrypting it. The level of protection also depends on the type of encryption used. For example, with HTTPS, your ISP can still see the websites you visit, even if it can’t see exactly what you do on them.
Can my ISP see my activity if I use encryption?
It depends on the method. With a VPN, your ISP won’t see the specific websites or apps you’re using, though it will know you’re connected to a VPN. With browser-based encryption like HTTPS, your ISP can still see the websites you connect to, even if it can’t see what you do on them.
Should I use multiple layers of encryption?
Using more than one form of encryption can strengthen privacy. For instance, HTTPS secures connections to websites, while a VPN encrypts all traffic from your device, adding broader protection
Why do some websites still show "not secure" with HTTPS?
This generally happens when a website has a misconfigured, expired, or invalid SSL certificate. It can also occur due to "mixed content," where some elements of the site (like images or scripts) load over an unencrypted HTTP connection and others load over HTTPS.
Why am I still seeing ads after using a VPN?
Encrypting your traffic doesn’t block ads, so you’ll still see them even when connected to a VPN. However, some VPNs, like ExpressVPN, include built-in ad blocking to provide a smoother web browsing experience.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN















