How to secure your iPhone from hackers before it’s too late

iPhones have a strong reputation for security, but that doesn’t mean they’re hack-proof. Like any connected device, they can still be targeted through phishing attempts, malicious apps, unsecured Wi-Fi, or weak account settings. Many users assume the default protections are enough—until something goes wrong.
As iPhones store more personal and financial information than ever, taking a few minutes to strengthen your iPhone security settings is no longer optional. Whether it’s adjusting app permissions, enabling two-factor authentication, or simply knowing what to watch for, these small changes can make a big difference.
This guide shows you how to secure your iPhone using expert tips and Apple’s built-in tools. You’ll also learn how to spot warning signs of a hack and what to do if your phone is compromised.
Why iPhone security matters
iPhones come with strong built-in protections, but that doesn’t mean they’re completely safe. Cybercriminals can still trick users with phishing links, take advantage of weak passwords, or exploit outdated software to gain access.
Most security risks come from small things, like using public Wi-Fi without a reliable VPN or giving apps more access than they need. Taking a few minutes to adjust your settings can help stop these threats and keep your data private.
Are iPhones safe from hackers?
iPhones are built with strong security features, and Apple does a good job of keeping tight control over its software and App Store. That makes iPhones safer than many other devices, but not unhackable.
Cybercriminals can still find ways in, especially through phishing links, fake apps, or sketchy profiles that trick users into giving access. In most cases, it’s not the iPhone itself that’s the problem—it’s how the user sets it up or uses it. Things like skipping software updates, using weak passwords, or clicking on suspicious messages can open the door to an attack.
So yes, iPhones are secure by design, but that only goes so far. Staying safe means using the tools Apple provides and paying attention to how you use your device day-to-day.
What hackers can access if your phone is compromised
If a cybercriminal manages to compromise your iPhone, the amount of data they can access may be more than you expect. Messages, call logs, contacts, and photos can all be exposed, along with your browsing history and social media accounts. In some cases, spyware can also track your real-time location and even access your microphone or camera without your knowledge.
If your Apple ID is part of the breach, synced data like iCloud backups, emails, and stored files may also be at risk. Some forms of spyware can even monitor what you do on your device, reading texts, seeing app activity, or intercepting login credentials. That kind of access can quickly lead to stolen accounts, financial loss, or identity theft.
Common iPhone security mistakes
Some iPhone users are more exposed to risks because of how they use their devices. You should pay extra attention to your iPhone’s security if you:
- Jailbreak your device: This removes Apple’s built-in protections and makes it easier for malware to get in. Jailbreaking is not recommended, as it weakens the security of your iPhone and exposes it to serious risks.
- Ignore iOS updates: Skipping updates leaves your phone open to known vulnerabilities.
- Download apps from outside the App Store: These apps haven’t been vetted and could contain hidden threats.
- Use public Wi-Fi without a VPN: Cybercriminals can intercept your data on unsecured networks.
- Share too much personal info online: The more you reveal, the easier it is to be targeted.
Step-by-step guide to securing your iPhone
Securing your iPhone doesn’t have to be complicated. Most of the tools you need are already built in. This guide will show you easy steps you can take right now to protect your data and keep your device safe.
1. Set a strong alphanumeric passcode
A simple 4- or 6-digit code is easy to guess or crack, especially if someone gets hold of your phone. Switching to an alphanumeric passcode makes your device much harder to access.
Here’s how to set one:
- Go to Settings and tap Face ID & Passcode.
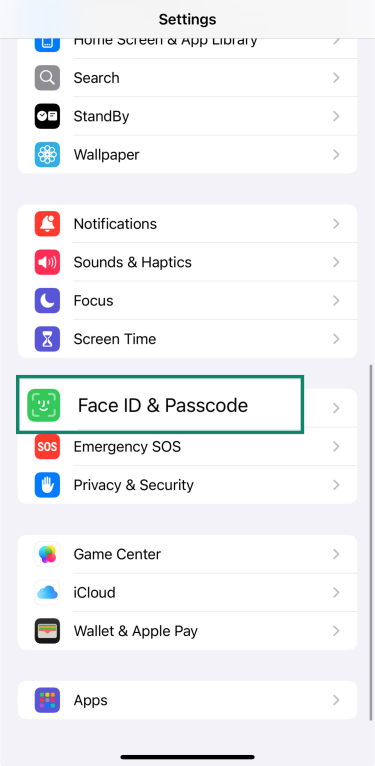
- Enter your current passcode and tap Change Passcode.
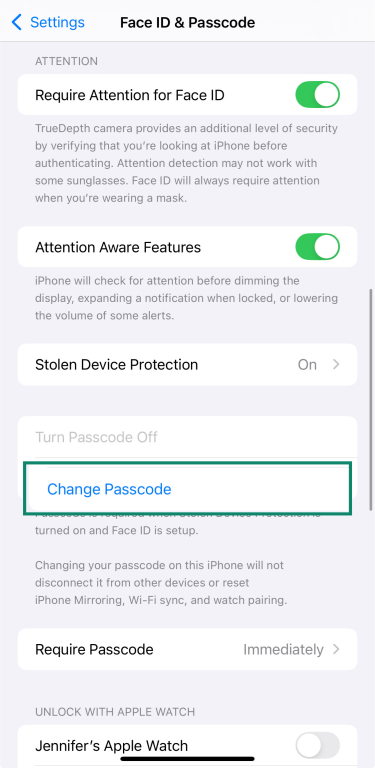
- Enter your current passcode again.
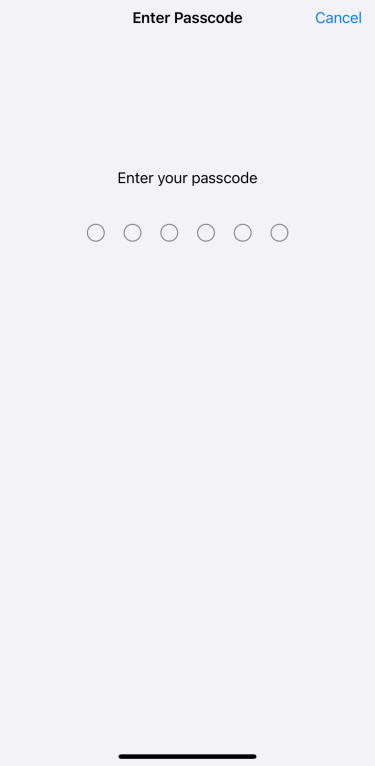
- Tap Passcode Options.
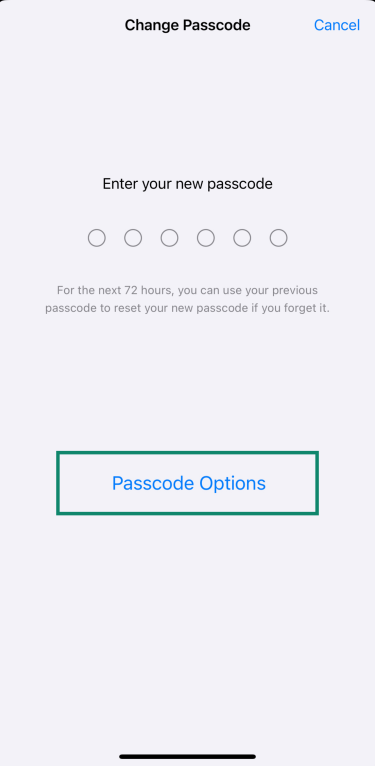
- Choose Custom Alphanumeric Code and create a new passcode using a mix of letters, numbers, and symbols. Re-enter it to confirm.
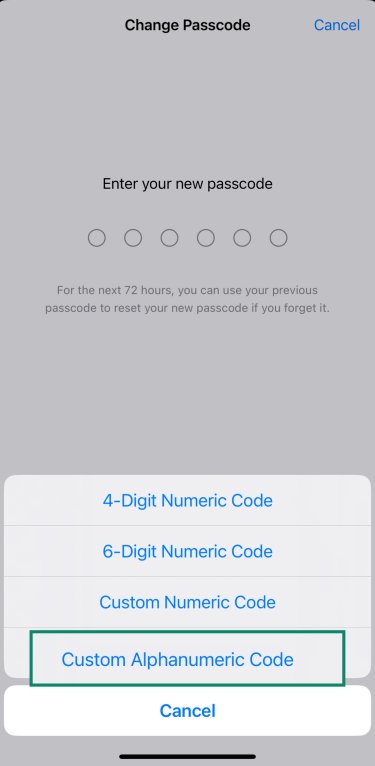
Just keep in mind that a longer, more complex passcode can be harder to remember. Consider storing it securely using a tool like ExpressVPN Keys, which supports encrypted notes as well as safely storing all your logins.
2. Enable Face ID
Adding Face ID enhances your iPhone's security because it uses your biometric information to unlock your device, authorize purchases, and sign into apps. Here’s how to set it up:
- Open Settings and tap Face ID & Passcode.

- Enter your passcode.

- If Face ID isn’t set up yet, tap Set Up Face ID and follow the steps to scan your face.
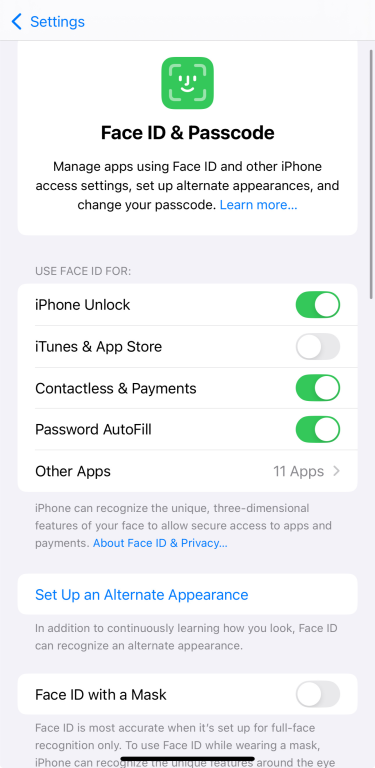
If Face ID is already set up, you won’t see the setup option again. Instead, you’ll see settings for what Face ID is used for and the option to reset it.
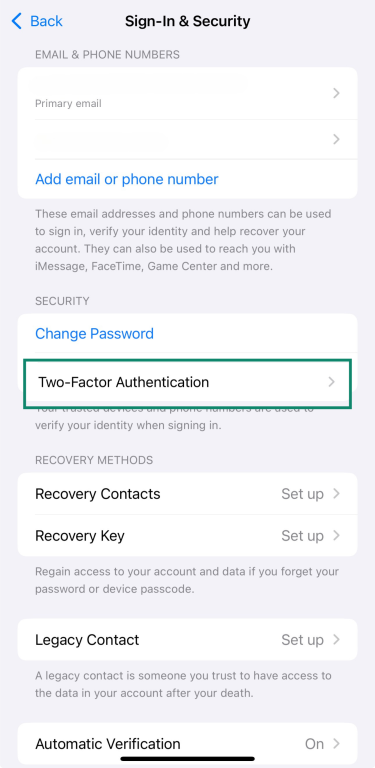
3. Turn on two-factor authentication
Two-factor authentication helps protect your Apple ID by requiring a code in addition to your password when you sign in.
To turn it on:
- Open Settings and tap your name at the top of the screen.
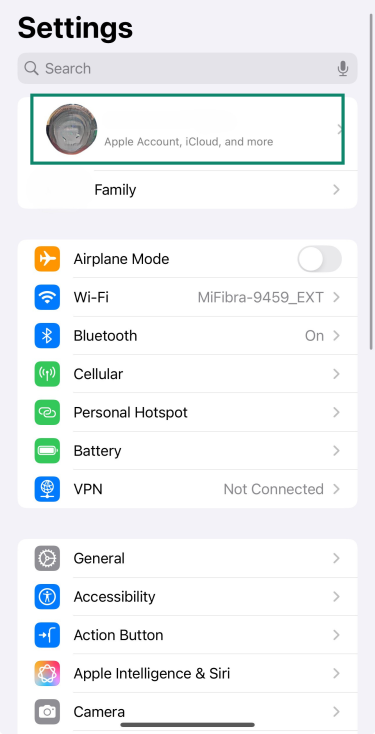
- Tap Sign-In & Security.
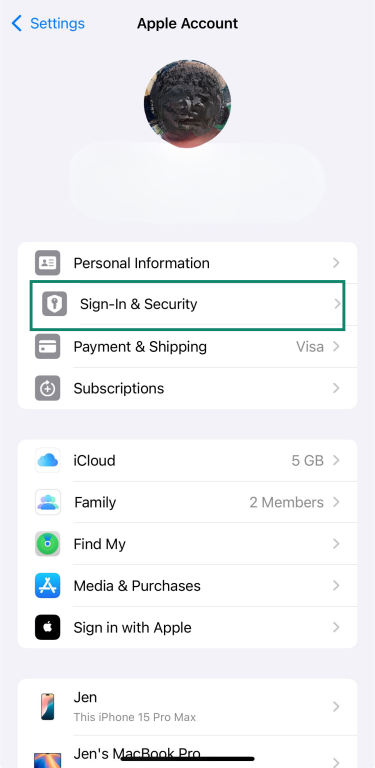
- Tap on Two-Factor Authentication and turn it on.
4. Keep iOS and apps updated
Software updates aren’t just about new features—they often fix security issues that could leave your iPhone vulnerable. Keeping both iOS and your apps up to date is one of the simplest ways to stay protected.
To update your apps manually:
- Open the App Store and tap your profile picture at the top right.
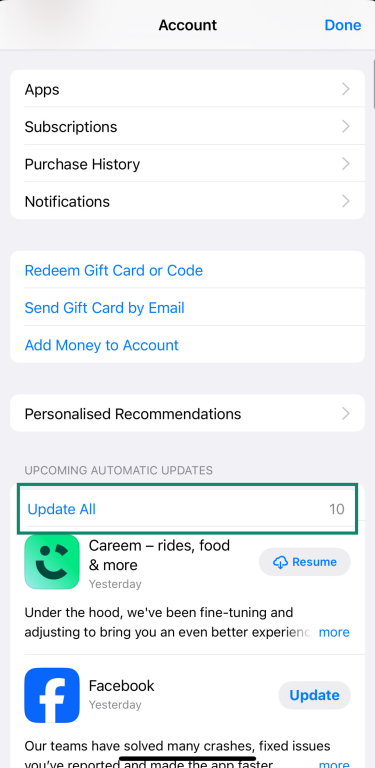
- Scroll to see available updates and tap Update All or update apps one by one.
To update iOS manually:
-
- Open Settings and select General.
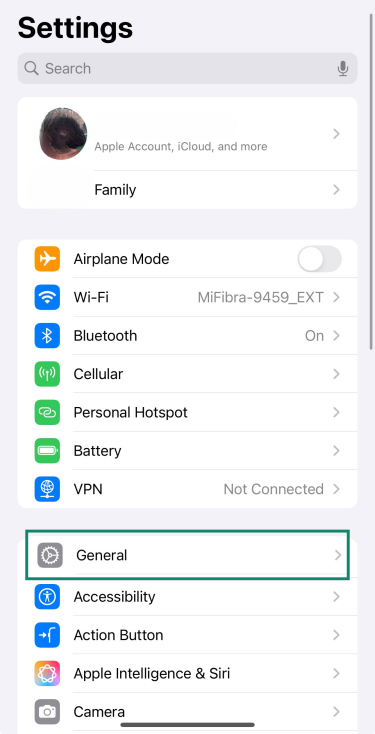
- Go to Software Update.
- If an update is available, tap Update Now and install it.
- If you want to keep it automatic, make sure Automatic Updates is switched on.
- Open Settings and select General.
5. Use Find My iPhone and enable “Erase Data”
Losing your iPhone doesn’t have to mean losing your data. Apple’s Find My iPhone feature helps you locate your device if it’s lost or stolen and lets you erase it remotely to keep your information safe.
To make sure it’s turned on:
- Go to your account and select Find My.
- Make sure Find My iPhone, Find My network, and Send Last Location are enabled.
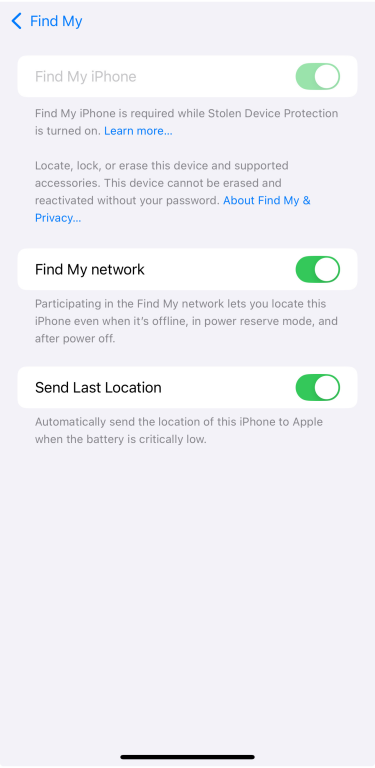
You can also add an extra safeguard: erase data after 10 failed passcode attempts. This means that if someone tries to guess your code and fails too many times, your iPhone will automatically wipe all its data.
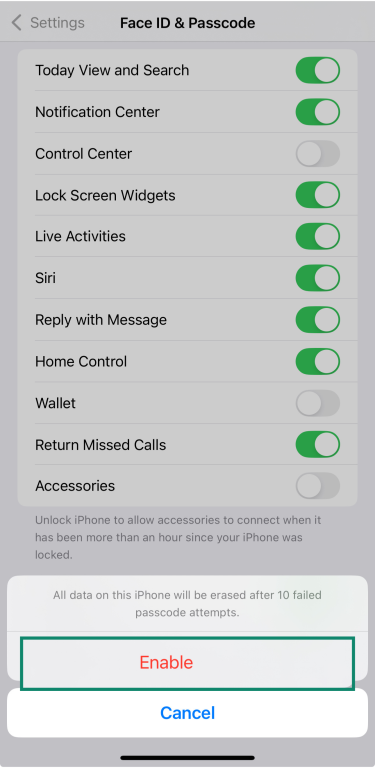
To enable it:
- Go to Settings and tap Face ID & Passcode.

- Enter your passcode.

- Scroll down and turn on Erase Data.
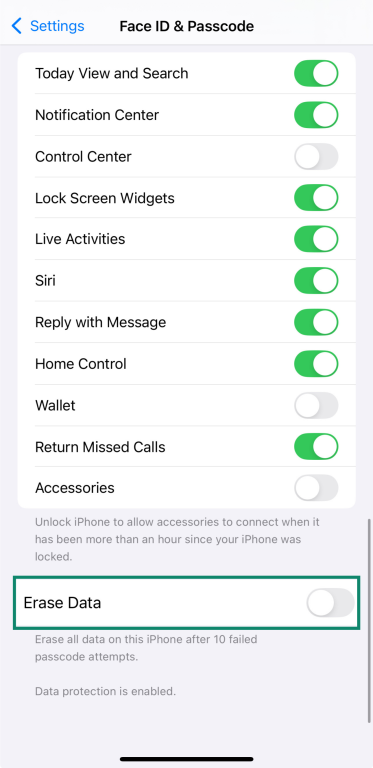
- Then tap Enable.
6. Review and limit app permissions
Your iPhone allows you to control which apps have access to your personal information, such as your location, contacts, photos, microphone, and more. Regularly reviewing these permissions helps protect your privacy and ensures that apps only access information necessary for their functionality.
To review and adjust app permissions:
- Open Settings, then tap Privacy & Security.
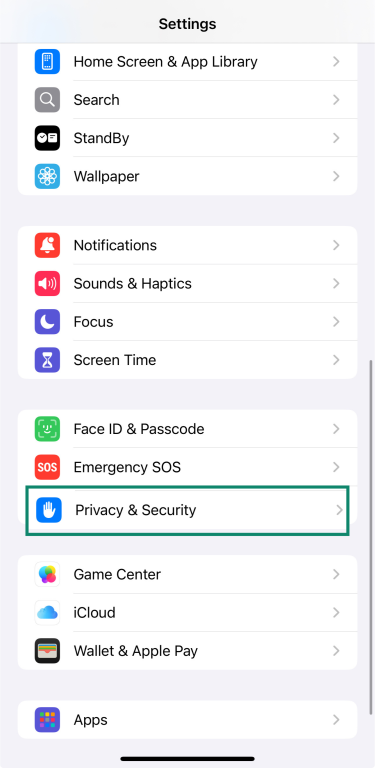
- Tap on an app to change its permission settings.
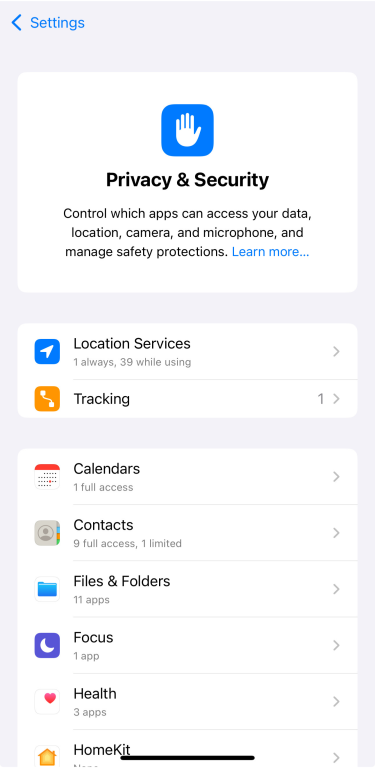
To monitor how apps use the permissions you've granted:
- Go to Settings and tap Privacy & Security.

- Select App Privacy Report and tap Turn On App Privacy Report.
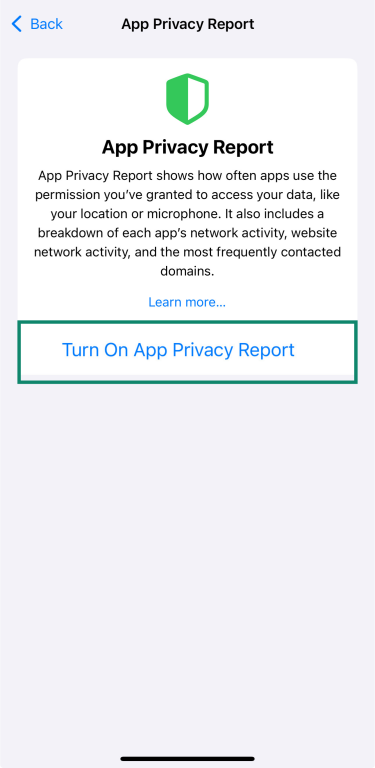
Once it’s turned on, the App Privacy Report shows which apps access things like your location, camera, and microphone, and which websites they contact most often.
7. Disable Lock Screen access to Siri and notifications
Your iPhone’s Lock Screen is meant to give you quick access to useful tools, but some of those shortcuts can also be security risks. If someone gets hold of your phone, they could interact with Siri or view sensitive notifications without needing your passcode.
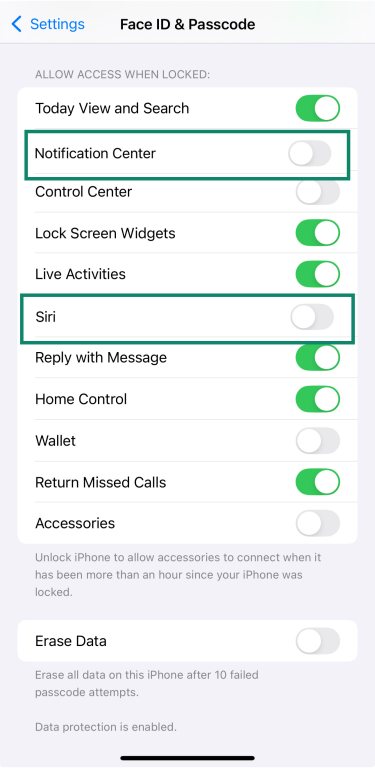
To tighten your security, you can turn off access to Siri and the Notification Center from the Lock Screen:
- Open Settings, then tap Face ID & Passcode.

- Enter your passcode.

- Scroll down to Allow Access When Locked and turn off Siri and Notification Center.
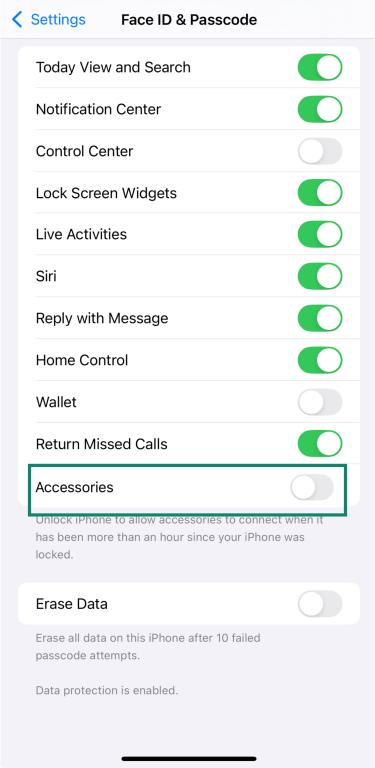
8. Turn on USB Restricted Mode
To help protect your data, your iPhone can block USB accessories from connecting when your device has been locked for over an hour. This feature, known as USB Restricted Mode, adds an extra layer of security, especially if your iPhone is lost or stolen.
To check or enable it:
- Go to Settings, then tap Face ID & Passcode.

- Enter your passcode.

- Scroll to Accessories and make sure the switch is off—this means USB Restricted Mode is on.
9. Turn off automatic Wi-Fi connections
By default, your iPhone will automatically join known Wi-Fi networks. While convenient, this can be risky on public or unsecured networks. To turn it off:
- Go to Settings, then tap Wi-Fi.
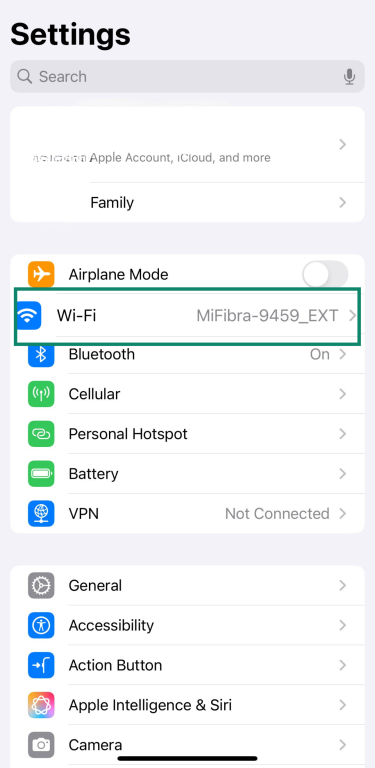
- Tap the info icon (i) next to the network you want to stop auto-joining.
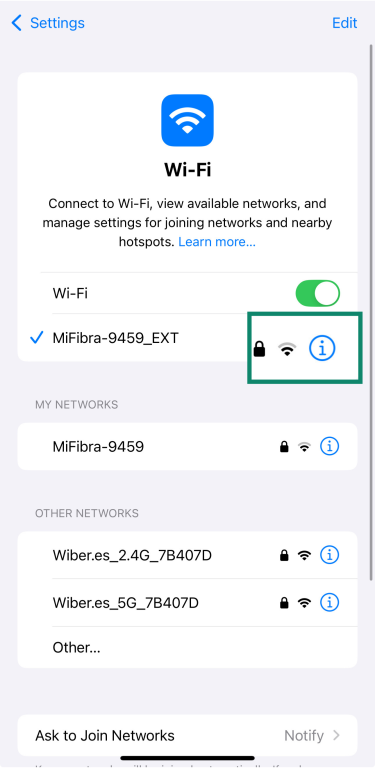
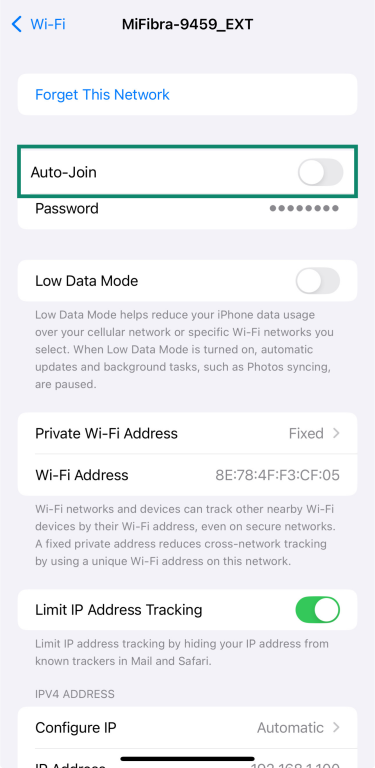
- Toggle Auto-Join off.
10. Use a VPN on public Wi-Fi
Public Wi-Fi networks are convenient but can be risky, especially if they’re open—cybercriminals can intercept your data if you’re not protected. A VPN encrypts your connection, keeping all your personal info safe while it’s in transit.
ExpressVPN’s iPhone app makes it easy to stay safe—just open the app, connect to a server, and you’re protected in seconds.
11. Avoid jailbreaking your device
Apple designs iOS to be secure and stable, and regular updates help keep it that way. Jailbreaking removes built-in protections and can stop your iPhone from receiving important security updates. That leaves your data more exposed to risks like malware, app misuse, or system crashes.
The best way to keep your iPhone protected is simple: stick with official iOS updates and avoid any tools or modifications that bypass Apple’s security.
12. Be careful with public charging stations
Researchers have shown that some public iPhone chargers can be compromised. If your device is unlocked and you plug it into one of these chargers, even briefly, malicious apps could be installed without your knowledge.
Once installed, these apps may be able to access sensitive information, intercept calls, and even take control of your device.
To protect yourself, avoid using public USB charging stations. Stick to your own charger and power adapter whenever possible.
13. Be cautious with links and unknown messages
Cybercriminals can send fake messages that look completely legitimate, sometimes by text, email, or via messaging apps. These messages might try to get you to tap a link or share something sensitive without realizing it, and they could contain malware.
If a message feels off, don’t click anything—just delete it. And if you’re not sure, here’s a quick guide to spotting and avoiding phishing attacks. For an extra layer of safety, ExpressVPN’s Advanced Protection tools can help block malicious links before you get the chance to open them.
Extra tips to improve your iPhone privacy
There are a few extra privacy settings worth checking if you want more control over your privacy. They don’t take long to adjust, but they can make a real difference in what your iPhone shares and with whom.
Revoke location tracking where not needed
Not every app needs to know where you are. To check which ones have access:
- Go to Settings, then tap Privacy & Security.

- Tap Location Services.
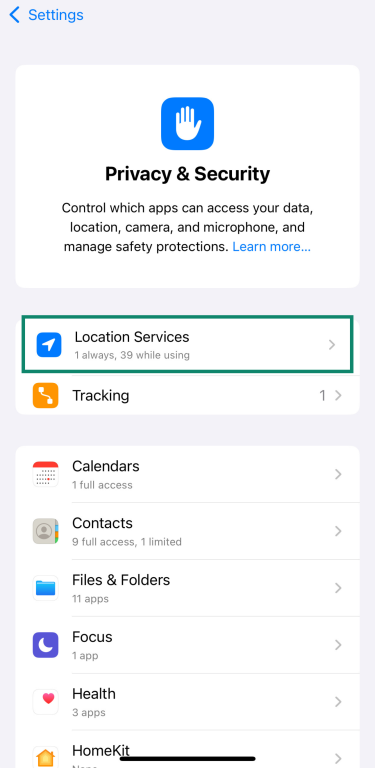
- Tap any app to adjust when it can access that info or turn it off completely.
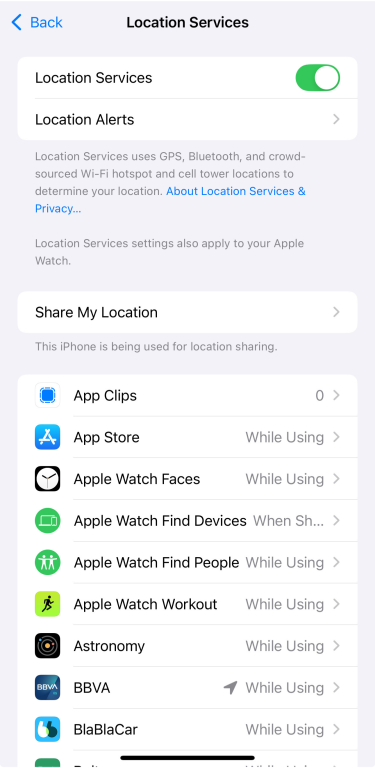
If you want to share only your general location (not your exact spot), you can also turn off Precise Location for specific apps once you click on any of them.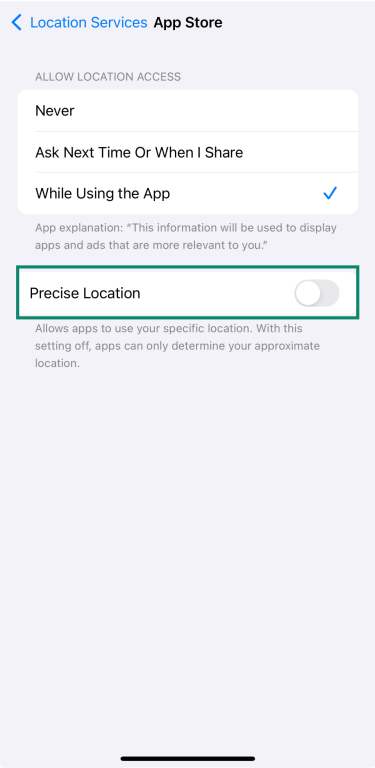
Clean up unused apps and services
Unused apps can take up storage without you realizing it, and more importantly, they can introduce potential security risks if they’re outdated or no longer supported.
To delete or offload apps manually:
- Go to Settings and tap General.

- Tap iPhone Storage.
- Scroll through the list of apps.
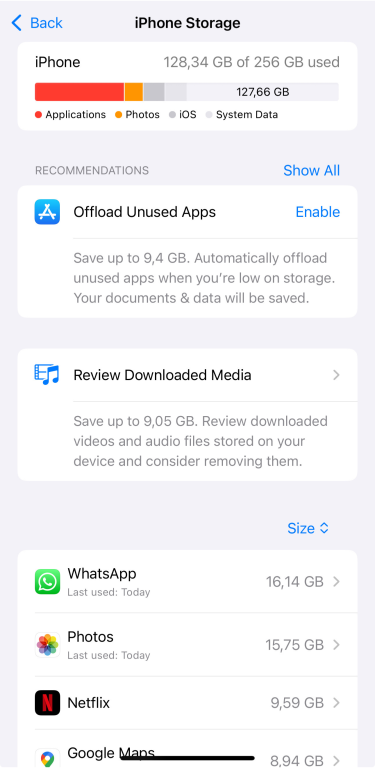
- Tap any app to see its storage details, and choose Offload App (keeps documents and data) or Delete App (removes everything).
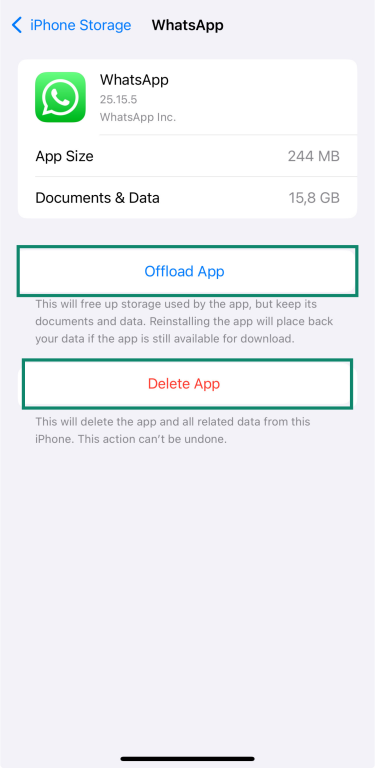
Secure iCloud account settings
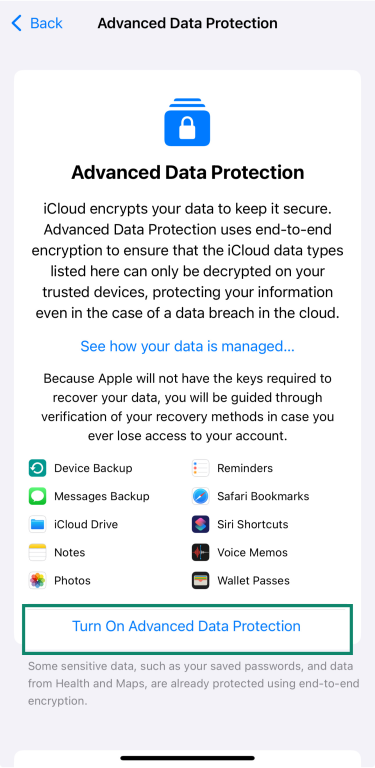
Advanced Data Protection adds an extra layer of security to iCloud by using end-to-end encryption for more of your data, like photos, notes, and iCloud backups. It's not turned on by default, but it only takes a few steps to enable it.
To turn it on:
- Go to Settings, then tap your name at the top.

- Tap iCloud.
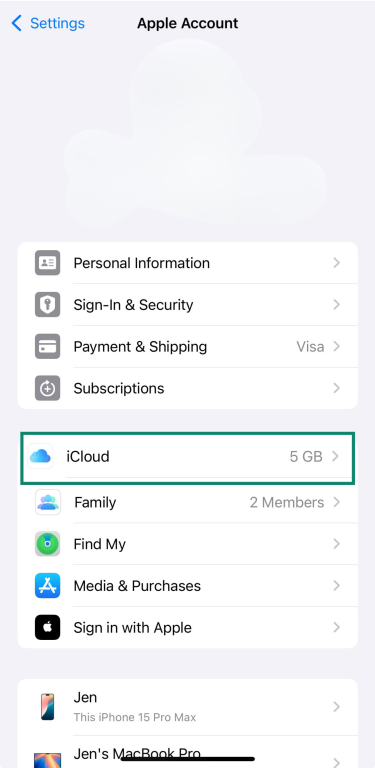
- Tap on Advanced Data Protection.
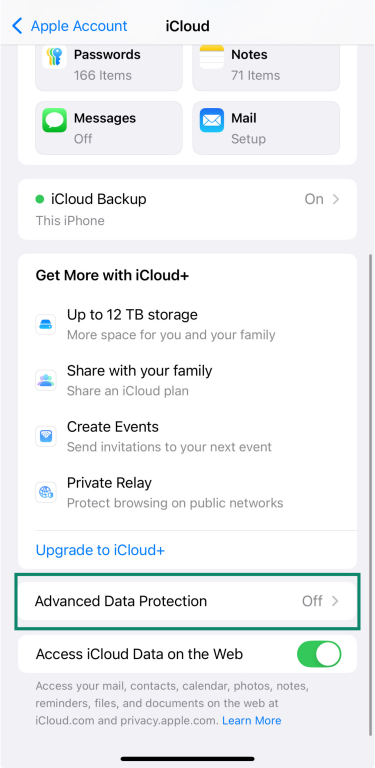
- Follow the prompts to set up a recovery method—either a recovery contact or a recovery key.
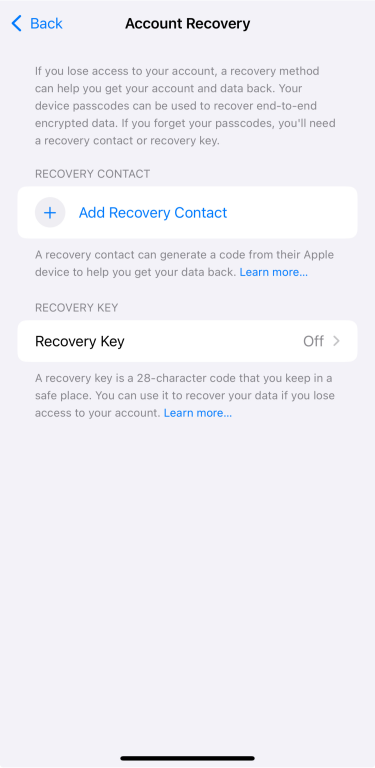
- Once that’s done, tap Turn On Advanced Data Protection.
Use privacy-focused apps and browsers
Some apps collect far more data than they need, often without making it obvious. If you want to reduce tracking, switching to privacy-focused alternatives is one of the simplest changes you can make.
Apps like Signal or Telegram offer secure messaging without tying your data to big tech platforms. But you don’t always need to switch—Apple’s own apps like iMessage are also strong privacy choices.
For email, ProtonMail is a good option if you want end-to-end encryption and less data collection. And when it comes to browsing, choosing a privacy-first browser makes a big difference. This guide to the best private browsers compares options like Brave, LibreWolf, and Tor Browser—all designed to minimize tracking and protect your data.
You don’t need to change everything overnight, but using apps that collect less data helps to protect your privacy in the long run.
What to do if you suspect your iPhone has been hacked
If something feels off with your iPhone, like unusual activity on your account or devices you don’t recognize appearing under your Apple ID, it’s important to act fast. This section walks you through how to spot the signs and what to do to secure your device.
Warning signs of a compromised iPhone
Be alert for the following indicators that may suggest unauthorized access to your Apple account:
- Unexpected password changes: Receiving notifications that your Apple ID password has been altered without your initiation.
- Unrecognized devices: Seeing devices you don't own listed under your Apple ID.
- Strange account activity: Observing unfamiliar changes to your personal or security information on your Apple Account.
- Unusual messages: Getting emails or messages about account activities you didn't perform.
- Inability to sign in: Being locked out of your Apple account or finding that you’re unable to access certain services.
Check for unauthorized access to your Apple ID
If you think someone else may have access to your Apple ID or iPhone, follow these steps:
- Go to your profile and scroll down to see all devices signed in with your Apple ID.
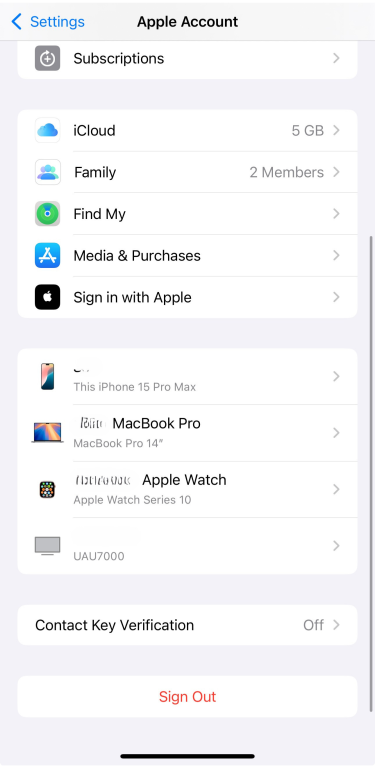
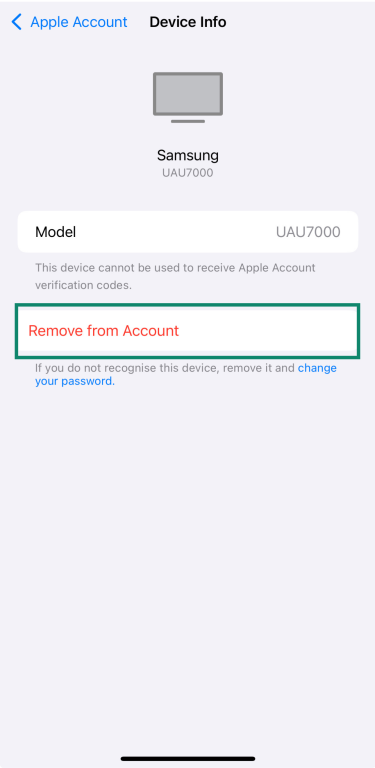
- If you see one that you don’t recognize, tap it and select Remove from Account. Then, change your Apple ID password to prevent further access.
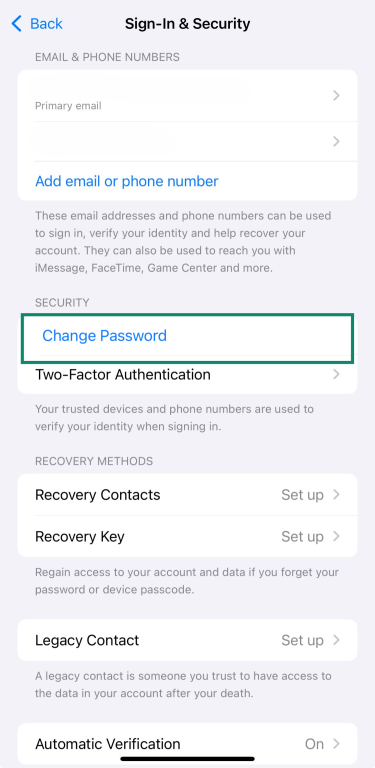
Recovery steps to take immediately
If you think someone has access to your Apple ID, don’t wait. Here’s what you need to do right away:
- Go to your profile, tap Sign-In & Security, and then tap Change Password. Update your password to lock out anyone else using your account.
- If you haven’t already, review the list of devices linked to your Apple ID and remove anything you don’t recognize.

- Check if two-factor authentication is on, as it adds an extra layer of protection. You can find it under Sign-In & Security.

- If you can’t sign in or need help regaining control of your account, get in touch with Apple Support directly. They’ll guide you through account recovery.
FAQ: Common questions about iPhone security
How do I completely secure my iPhone?
The best way to secure your iPhone is by turning on Advanced Data Protection, using two-factor authentication, and sticking with trusted apps. It also helps to review your location settings and delete anything you don’t use.
How do I stop someone from accessing my iPhone?
Start by setting a strong passcode and turning on Face ID or Touch ID. Then make sure two-factor authentication is on and remove any devices you don’t recognize from your Apple ID.
Is the iPhone protected from hackers?
iPhones have strong built-in security, but no device is fully immune. To stay protected, it’s important to keep your iPhone updated, use a passcode, enable two-factor authentication, and avoid risky habits like jailbreaking.
Can I scan my iPhone for hackers?
There’s no built-in scanner, but you can still check for anything suspicious. Look at the devices signed in to your Apple ID, remove anything you don’t recognize, and make sure your settings and apps look right. If something feels off, change your password right away.
Does Apple have built-in antivirus?
iPhones don’t have antivirus like computers do, but Apple’s built-in protections, like sandboxing, App Store review, and system updates, help block most threats. These are usually enough unless the device is jailbroken or you fall for a phishing attempt, which can bypass those layers of security.
Can someone access my iPhone remotely?
It’s unlikely if your iPhone is updated and not jailbroken. But if someone gets your Apple ID and password, they could access your account or data from another device. That’s why it’s important to use two-factor authentication, check for unknown devices, and remove anything you don’t recognize.
Is iPhone more secure than Android?
Generally, yes. Apple controls both the hardware and software, so iPhones get regular security updates and only allow you to download apps through the App Store. That makes it harder for malware to slip through. Android is more open, which gives users more freedom but also means a higher risk if updates aren’t installed or apps come from untrusted sources.
How often should I update my iPhone?
As soon as a new update is available. Apple releases updates to patch security issues and keep your device protected, so it’s best not to wait. Turn on automatic updates to stay covered without having to check manually.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN






