Understanding cyberterrorism: Definition, types, and preventive measures

Cyberterrorism sits at the intersection of cybersecurity and global security, which has led to it being used as a label for some ordinary cyberattacks that don’t necessarily meet the criteria.
This guide explains what “cyberterrorism” typically refers to, outlining its key characteristics and describing the most common attack methods involved. It also gives an overview of security measures organizations can use to reduce damage from a potential attack.
Note: The information in this article is for educational purposes only. Trying to recreate any of the attack methods described here outside an approved and controlled environment is illegal and unethical.
What is cyberterrorism?
Cyberterrorism is a term used by governments, security analysts, and media to describe certain cyberattacks that are intended to cause widespread disruption or fear for ideological or political purposes. The term doesn’t have a universally accepted legal definition, and its use can vary significantly depending on political, legal, and regional context.
Key characteristics
Cyberterrorism is commonly associated with the following characteristics:
- Ideological or political intent: Attackers are usually seen to have political, ideological, or religious motives, aiming to influence behavior, demonstrate power, or advance a cause.
- Focus on high-impact targets: Acts of cyberterrorism often have targets with strategic or symbolic value, typically systems and services whose disruption would have widespread consequences, such as government institutions, critical infrastructure, or essential public services.
- Use of disruptive digital methods: Operations often rely on cyber techniques that interfere with normal functioning, including service disruption, system intrusion, data manipulation or destruction, malware deployment, website defacement, or coordinated information manipulation.
Cyberterrorism vs. cybercrime
Cyberterrorism is often discussed as a type of cybercrime, but it’s generally distinguished by the motivation or intent behind an attack rather than by the technical methods used.
Cybercrime involves using the internet, software, or hardware to compromise networks, systems, or data for personal or financial gain. Typical cybercriminals carry out these cyberattacks for personal or financial gain, and they generally try to stay under the radar so they don’t get caught.
Cyberterrorists, on the other hand, are associated with cyberattacks for political, ideological, or religious reasons. They’re typically classified as intentionally performing visible attacks in order to reinforce their supporters’ beliefs or demonstrate their power. While hostile actors, technically, might still profit, it’s generally not their primary objective.
Types of cyberterrorism
Cyberterrorism can take different forms depending on the goal of the activity involved. The most common forms include:
Cyber espionage
Cyber espionage involves gaining unauthorized access to digital systems to collect sensitive or classified information. The information obtained through cyber espionage can support planning, reveal vulnerabilities, or strengthen future operations. In some cases, this can lead to compromised security, damaged infrastructure, or risks to human life.
Some discussions of cyberterrorism include cyber espionage when it’s carried out by non-state actors and framed as part of an ideological campaign. However, similar techniques are also widely used in state-led cyber operations and intelligence gathering, which are typically classified separately as cyber espionage or cyberwarfare.
Attacks on critical infrastructure
Attacks on critical infrastructure involve targeting digital systems that support essential services such as energy, water, transportation, healthcare, and communications. These systems often depend on interconnected networks, which makes them vulnerable to cyber disruption.
Disrupting critical infrastructure can cause service outages, economic losses, and public safety risks, with effects that extend beyond the digital environment.
Disruption of critical infrastructure is also a feature of other types of cyber conflict, and classification as “cyberterrorism” depends heavily on attribution and intent.
Attack techniques used in cyberterrorism
Cyberterrorism can involve a range of cyberattack techniques, many of which aren’t unique to it and are also widely used in cybercrime, cyber espionage, and other cyber operations. Commonly used attack techniques include: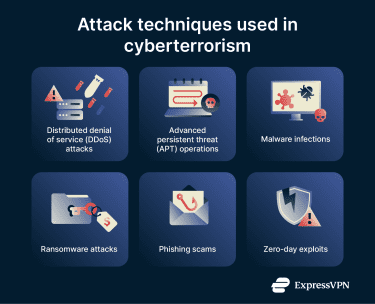
Distributed denial-of-service attacks
A distributed denial-of-service (DDoS) attack is a large-scale cyberattack that uses a network of hijacked devices, known as a botnet, to flood a target with traffic and force it offline for hours or even days. Extremist groups may use these attacks to take down major websites or essential public services and cause major financial losses during downtime.
Advanced persistent threat attacks
An advanced persistent threat (APT) attack happens when malicious actors secretly break into a system and stay there for a long time without being detected. While inside, they quietly watch networks and systems, gather valuable data, and expand their access. Attackers may use these tactics to pull high-value information from defense, financial, manufacturing, or medical organizations.
Malware infections
Malware infections happen when hostile actors deliver malicious software to high-value systems, devices, or networks. They may use different types of malware, such as trojans, computer worms, or polymorphic viruses, to compromise sensitive data or target critical assets like power grids, military systems, or government departments.
Ransomware attacks
Ransomware is malicious code that uses encryption to lock access to important data and sometimes even steal it. Threat actors spread ransomware to block people from using valuable systems or assets. They may do this to cause panic and damage or to demand payment as part of a cyber extortion campaign.
Phishing and scams
Malicious actors use phishing attacks that rely on fake emails or spoofed websites to trick people into handing over sensitive information, such as login credentials, which they then use to reach valuable data. Attackers may also try to get targets to open malicious files, which can lead to malware spreading across the system.
Zero-day attacks
Some threat actors target critical infrastructure with zero-day exploits that take advantage of unknown and unpatched cybersecurity vulnerabilities. They use these gaps to secretly gain unauthorized access, avoid detection, change account privileges, and deploy malware.
How to protect yourself from cyberterrorism
Cyberterrorist threats are becoming more complex as attackers adopt advanced tools and automation. Organizations that operate critical systems can reduce risk by building layered cybersecurity defenses and addressing weaknesses before they are exploited.
Adopt an operational security (OPSEC) approach
Operational security (OPSEC) focuses on identifying what information is sensitive, how it could be exposed through everyday activities, and what the impact would be if it were compromised. In cybersecurity, this often involves examining communications, workflows, and public-facing information to understand what they reveal to adversaries.
By improving awareness of information exposure and reinforcing secure behaviors, organizations can reduce unintentional leaks, limit actionable intelligence available to attackers, and strengthen overall security culture.
Implement strong authentication
Weak passwords have played a role in some of the biggest cyberattacks in history, since they’re easy to crack. That’s why organizations should enforce strict password policies that require strong credentials. Passwords should be at least 12 characters long, include a mix of numbers, symbols, and letters, and avoid common words. Password managers are also worth using, since they securely store logins in one place and autofill details on trusted sites.
Organizations should also require multi-factor authentication (MFA), which makes it much harder for malicious actors to take over accounts by adding extra identity checks during login. Phishing-resistant MFA is ideal because it uses cryptographic verification to help protect against phishing attempts.
Enforce access controls and zero-trust policies
Strong access controls add another layer of protection by making sure only authorized accounts can reach high-value assets. Role-based access control (RBAC) is especially important because it grants or limits system access based on defined user roles. For example, a customer support account wouldn’t have access to high-level operational data. This approach helps reduce insider threats and limit lateral movement, so attackers can’t take over low-level accounts and use them to raise privileges or steal sensitive information.
Additionally, organizations should consider a zero-trust architecture, which is a security framework built on the idea that no device, user, or account is automatically trusted. Access is granted and maintained only through continuous identity verification, which helps contain breaches and reduce the impact of compromised accounts.
Keep systems and software updated
Outdated systems often contain unpatched weaknesses that threat actors can exploit. Along with enforcing policies that require mandatory updates, organizations should use automated updates whenever possible. This usually involves centralized tools that detect and roll out upgrades across operating systems, firmware, drivers, and applications.
Secure your network infrastructure
The following measures can help organizations and institutions strengthen network security:
- Deploy firewalls: A firewall monitors network traffic for suspicious activity. If it detects anything unusual, it flags the issue and blocks the abnormal traffic. Next-generation firewalls (NGFW) are the ideal option because they can safeguard against advanced malware and application-layer attacks.
- Secure Wi-Fi networks: All wireless networks should use Wi-Fi Protected Access 3 (WPA3), which is the latest Wi-Fi encryption standard. It helps prevent malicious actors from freely joining the network and monitoring traffic.
- Segment the network: Dividing the network into smaller sections, called subnets, reduces the attack surface. Even if an attacker compromises one subnet, they can’t immediately access every connected system.
- Require corporate virtual private networks (VPNs) for remote access: VPNs encrypt internet connections, which makes it harder for attackers to monitor or intercept traffic. Remote users should always use a VPN when accessing internal resources. Please note that corporate VPNs are designed for large organizations and differ from commercial VPNs, which help individuals and small teams secure their online data.
Deploy endpoint protection and monitoring
Every device that connects to internal resources should be checked first to make sure it meets security requirements, such as using the latest operating system version and having security tools installed. IT teams should also keep a close eye on connected endpoints and review collected data for signs of potential threats.
To ensure effective endpoint protection and monitoring, organizations should use comprehensive security solutions that include the following:
- Endpoint detection and response (EDR): Provides real-time detection, analysis, and response. It flags suspicious activity on endpoints and gives security teams actionable insights to respond quickly to active threats.
- Endpoint protection platform (EPP): Focuses on preventing malicious threats by equipping devices with malware protection and firewall capabilities.
- Extended detection and response (XDR): Gathers data from endpoints and other security layers, such as email, cloud services, and servers. This improves visibility and context around advanced threats, helping security teams analyze and stop malicious activity more effectively.
Practice safe email and communication habits
Organizations should put email security measures in place, such as requiring MFA during login, enforcing strong passwords, encouraging password manager use, and encrypting emails so only the intended recipient can read them. Employees should also receive regular training on how to spot and report suspicious emails.
Email authentication protocols can help stop threat actors from sending fake emails in your name:
| Email authentication protocol | What the protocol does |
| Sender Policy Framework (SPF) | Helps receiving mail servers verify that messages come from authorized sources, reducing the chance they’ll be flagged as spam. |
| DomainKeys Identified Mail (DKIM) | Uses a digital signature to verify your emails and protect against domain spoofing. |
| Domain-based Message Authentication, Reporting, and Conformance (DMARC) | Tells receiving mail servers what to do if messages fail SPF or DKIM checks and provides reporting to help monitor abuse. |
Offer cybersecurity awareness training for employees
Regular training sessions are crucial, as they teach staff how to recognize and avoid digital threats that can create security gaps even with advanced protections in place. Cybersecurity awareness training programs often focus on:
- Teaching employees how to properly secure devices.
- Promoting strong password habits.
- Explaining how malicious actors steal logins.
- Covering common phishing and social engineering tactics.
- Explaining company cybersecurity policies and best practices.
Common training formats include workshops, webinars, and interactive sessions. Workshops provide hands-on learning, while webinars work well for larger groups. Interactive sessions can place employees in simulated threat scenarios within controlled environments, giving them practical experience without real-world risk.
Establish incident response procedures
An incident response procedure is essential because it lays out clear steps to follow during a security incident. It helps reduce risk and allows designated teams to deal with threats as soon as they’re detected to limit the damage attackers can cause.
Plans may vary in detail, but many organizations typically implement the following steps:
- Identify where critical network components are located and create backups of stored data.
- Find single points of failure in hardware, software, and staff roles, then address them with backups. This can include adding redundancies, using software failover features, and assigning backup personnel who can step in.
- Develop a workforce continuity plan so employees stay safe and can keep working remotely if needed.
- Build the incident response plan. This often means forming a response team, assigning roles and responsibilities, listing critical recovery processes, and setting up internal and external communication channels.
- Train staff on the incident response plan to ensure smooth coordination with IT and the response team.
FAQ: Common questions about cyberterrorism
What are the top 3 types of cyberattacks?
The top three most common types of cyberattacks are phishing, malware infections, and distributed denial-of-service (DDoS) attacks, which disrupt online services by flooding them with traffic until they go offline. These threats are often used by regular cybercriminals, but cyberterrorists may also rely on them. They use these methods, along with other tactics, to target critical infrastructure, break into high-value institutions and facilities, and spread panic and fear.
How can organizations prepare for cyberterrorism?
Organizations can safeguard against cyberterrorism by implementing various security models and measures, such as operational security (OPSEC) and zero-trust frameworks. These approaches enforce strict practices, including using strong passwords, requiring multiple identity checks at login, keeping systems updated, strengthening network security, deploying endpoint protection, improving email security, training employees in cybersecurity, and maintaining a clear incident response plan.
What are the legal implications of cyberterrorism?
The legal implications of cyberterrorism vary because the term is defined differently across countries. Activities described as cyberterrorism may be prosecuted under existing criminal, national security, or cybersecurity laws, depending on the jurisdiction and circumstances involved. Because cyberattacks often cross national borders, international cooperation and extradition laws may also apply.
How is cyberterrorism evolving?
Cyberterrorism is advancing alongside technology and global connectivity. As digital systems become more widespread and interconnected, threat actors have greater access to tools and opportunities that can be used for disruptive or harmful purposes.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN