SSL vs. TLS: Key differences and why TLS is better

Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are both encryption protocols used for secure internet communications. They help ensure that sensitive data you enter into online forms remains inaccessible to cybercriminals and other third parties.
That said, there are substantial differences between the two protocols. For various reasons, SSL has been deprecated and is no longer in use. This article will go into more detail, explaining how these protocols work, how they’re distinct, and the vital role TLS now fulfills.
What is SSL and how does it work?
SSL was first developed by Netscape in 1994 to establish a secure communication channel between two users, devices, or applications on a network. When data is transmitted, there’s always a risk that it might be intercepted by third parties. SSL was created to keep such data safe from unauthorized access and tampering.
Key features of SSL
The SSL process can be divided into three major parts:
- Handshake authentication: The two parties exchange messages to confirm their compatibility and identities and set parameters for the interaction.
- Encryption: SSL encrypts data in transit, ensuring that no one intercepting the data can read its contents.
- Message integrity: SSL adds a message authentication code (MAC) to every sent message, allowing either side of a conversation to determine whether a message has been tampered with while in transit.
Protocol versions and timeline of deprecation
 Before SSL was deprecated (discontinued), it went through several updates, each of which closed security vulnerabilities. Here’s a rough outline:
Before SSL was deprecated (discontinued), it went through several updates, each of which closed security vulnerabilities. Here’s a rough outline:
| Version | Release year | Notes |
|---|---|---|
| SSL 1.0 | 1994 | Never publicly released |
| SSL 2.0 | 1995 | Launched and publicly released |
| SSL 3.0 | 1996 | Deprecated due to security flaws in 2015 |
What is TLS and how is it different?
TLS serves the same broad function as SSL but represents a substantial upgrade. Though SSL has fallen out of use, its legacy is still evident in terms like TLS/SSL (sometimes given as SSL/TLS). In some cases, SSL is actually referring to TLS (as in “SSL certificates”).
Like SSL, TLS is designed to secure communications between clients. It is deployed whenever someone visits a website beginning with HTTPS and is a default feature in platforms like Gmail.
TLS evolution and security improvements
TLS encryption has had three major updates since it was released in 1999, each aimed at improving security and performance. Here’s an overview of the TLS version history:
| Version | Release year | Vulnerabilities | Deprecation year |
| TLS 1.0 | 1999 | Weak encryption algorithms, no support for perfect forward secrecy (PFS), susceptibility to Browser Exploit Against SSL/TLS (BEAST) attacks | 2021 |
| TLS 1.1 | 2006 | Weak hash functions, static key exchanges, protocol downgrade attacks | 2021 |
| TLS 1.2 | 2008 | Protocol downgrade attacks, PFS not mandated, algorithms are quantum-susceptible | N/A (still in use) |
| TLS 1.3 | 2018 | None (so far) | N/A (the current standard) |
TLS 1.2 vs. TLS 1.3: What's changed?
The earliest TLS versions (v1.0 and v1.1) have now been deprecated, leaving only TLS 1.2 and TLS 1.3 still in use.
Here’s how the non-deprecated versions differ:
- PFS: Though it can accommodate it, TLS 1.2 doesn’t offer PFS by default, meaning anyone who compromises your security key can also see past data secured with the key. With TLS 1.3 connections, this is no longer possible.
- Legacy system vulnerabilities: TLS 1.2 was designed with compatibility for legacy systems. While practical, this opens the door for potential issues. TLS 1.3 may cause issues in much older systems, but it is more secure as a result.
- Faster performance: In TLS 1.3, the handshake process was reduced to a single round (which is sometimes skipped entirely if communication has already been established). This results in faster performance compared with TLS 1.2.
- Post-quantum considerations: TLS 1.3 mandates the use of Authenticated Encryption with Associated Data (AEAD) ciphers, like Advanced Encryption Standard in Galois/Counter Mode (AES-GCM) or ChaCha20-Poly1305, which improves integrity and confidentiality. Though not inherently secure against potential quantum attacks, TLS 1.3’s modular design and support for hybrid key exchange mean that in the future, post-quantum algorithms can be easily integrated.
Backward compatibility with SSL
Earlier TLS versions maintained compatibility with SSL in order to support legacy systems. This flexibility exposes systems to potential downgrade attacks, such as Padding Oracle On Downgraded Legacy Encryption (POODLE). By forcing a downgrade, threat actors could exploit old vulnerabilities to compromise a connection.
TLS 1.3 solves this issue by not being backward compatible, preventing threat actors from executing the downgrade attack.
SSL vs. TLS: Core differences explained
 SSL introduced allowed for generally secure online communications, but TLS brought major improvements. Here’s a quick outline:
SSL introduced allowed for generally secure online communications, but TLS brought major improvements. Here’s a quick outline:
- Handshake: SSL handshakes were poorly optimized, leading to performance issues, which TLS solves by using faster methods.
- Enhanced authentication: TLS greatly reduces the risk posed by man-in-the-middle (MITM) attacks by using stronger message authentication systems.
- Secure alert messages: SSL and TLS both throw warning alerts (indicating a non-critical error) and fatal alerts (indicating a critical error). But unlike SSL, TLS 1.3 encrypts all alert messages once a connection is established.
- Message authentication approach: SSL primarily authenticates messages using the Message Digest Algorithm 5 (MD5) algorithm, which is outdated and not as cryptographically complex as TLS’s Hash-Based Message Authentication Code (HMAC) system.
- Cipher suites: SSL and TLS support a range of cipher suites (a collection of encryption algorithms) for data encryption, key exchange, and secure data transfers. Some of the cipher suites used by SSL are weaker than what TLS offers.
Which is better, SSL or TLS?
TLS is an improvement over SSL in virtually every sense. It introduces improvements in a few key areas.
Performance and security comparison
TLS (especially version 1.3) improves on SSL’s performance by modifying the way handshakes are handled. On top of that, by encrypting all alert messages once a connection is established, TLS 1.3 is more secure. These are transmitted in plaintext data with SSL.
SSL is restrictive when it comes to encryption, with older versions even susceptible to modern conventional attacks. In comparison, TLS 1.3 mandates higher standards and is made to be adaptable.
Once they’re available, post-quantum encryption standards can be readily integrated into the latest version of TLS. This is significant, as many aspects of cybersecurity may be threatened as quantum computers emerge. For similar reasons, ExpressVPN’s Lightway and WireGuard protocols have been updated with quantum-safe algorithms.
Support across modern browsers and platforms
No modern browser or platform still supports SSL. Some of today’s systems may sometimes reference SSL certificates, but they actually use TLS.
Why TLS is now the default standard
Due to these security and performance improvements, TLS has long been the standard. In fact, the Internet Engineering Task Force (IETF) has determined that SSL ought no longer be used. This matters, as the IETF plays a key role in setting standards for the global internet.
From secure messaging apps to virtually every modern website, the modern world relies on TLS for encrypting connections.
Does HTTPS use SSL or TLS?
SSL was once used in Hypertext Transfer Protocol Secure (HTTPS), but, as everywhere else, it has been overtaken by TLS. Less than 1% of websites support any form of SSL, while nearly 100% use TLS 1.2 and upwards of 75% also support TLS 1.3.
How SSL/TLS powers secure web browsing
While using the internet, it’s sometimes necessary to input sensitive information on websites. For example, you may need to provide your credit card information on an e-commerce site or give out sensitive personal information when booking hotels and flights.
Without a protocol like SSL or TLS, that data could be intercepted as it moves between your device and the target server. This means anyone with the right tools can intercept that data in plaintext and, for example, use your credit card information to make an online purchase.
Under SSL and now TLS, that sensitive data is encrypted as it travels between devices, ensuring that only the intended people can read it.
Furthermore, SSL/TLS offers authentication and verification. This means that users are alerted of what they’re interacting with. While this offers some protection against phishing attacks, it is by no means a surefire defense due to the fact that cybercriminals can still create malicious sites with authentic certificates.
The role of SSL/TLS certificates in HTTPS
SSL certificates, which today are actually TLS certificates, enable websites to use HTTPS connections, which are more secure than those using HTTP.
 An SSL certificate also confirms the identity and authenticity of the online servers (generally websites) you visit. It does this by recording and cross-checking information such as:
An SSL certificate also confirms the identity and authenticity of the online servers (generally websites) you visit. It does this by recording and cross-checking information such as:
- Associated domain name (e.g., www.example.com)
- Associated subdomains (e.g., www.test.example.com)
- The issuing certificate authority (CA)
- To whom the certificate was issued (individual, organization, or device)
- Certificate issue and expiration dates
- Public key
How browsers validate HTTPS connections
 Browsers validate HTTPS connections by checking the underlying SSL certificate of the contacted website. The process occurs in mere milliseconds but requires a series of steps:
Browsers validate HTTPS connections by checking the underlying SSL certificate of the contacted website. The process occurs in mere milliseconds but requires a series of steps:
- Certificate integrity verification: Every SSL certificate is signed with the private key of a CA. The browser first verifies this signature using public key cryptography. This may involve multiple signature checks along a chain of trust to the root CA. If modifications have been made, the connection is rejected.
- Certificate validity checks: SSL certificates have a validity date and time. Browsers check to confirm that the certificate has not expired. If it has, the connection is rejected.
- Revocation status check: A certificate may be invalidated before its expiration date (for example, if its private key is compromised). Browsers typically check revocation using Online Certificate Status Protocol (OCSP), sometimes relying on stapling for greater efficiency.
- Issuer verification: The browser confirms that each certificate in the chain has actually been issued by the stated authority. This prevents spoofing a fake certificate with a legitimate CA’s name.
- Name constraint checks: The browser identifies that a certificate has been issued to a verified user. For instance, if the website www.example.com is legitimate, a scammer might set up www.scam.example.com to trick users into thinking it’s the same company. Name constraints keep this from happening.
- Policy constraint checks: Where CAs have specified policies under which a certificate has been issued, the browser must check those policies for compliance. However, this is a very rare occurrence in real-world situations.
- Path length verification: CAs can define maximum path lengths for certificates, preventing users from forging valid certificates. Otherwise, anyone with the right knowledge can create a fraudulent certificate to impersonate a trusted entity and scam unsuspecting users.
- Key usage verification: A usage policy is defined for every key contained in a certificate, which must also align with the browser’s key usage constraints. If it doesn’t, the browser rejects the certificate.
At this point, the browser processes any other critical extensions defined on the certificate and establishes a secure connection if successful. However, if there’s a single error in the processing path, a secure connection won’t be established. Generally, this leads to an error screen explaining the issue.
In most modern browsers, you can check for an alert in the address bar if HTTPS is not active.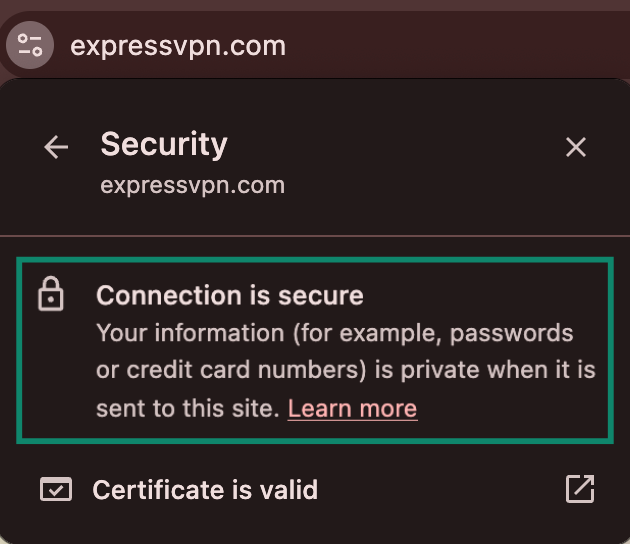
What is the difference between SSL and TLS certificates?
For various reasons relating to security and performance, SSL certificates have been phased out and replaced by TLS certificates. But by convention, TLS certificates are sometimes called SSL certificates.
Despite the name and crucial updates, the primary function of both certificates is the same: securing web communications by encrypting data in transit.
Should you replace SSL certificates with TLS certificates?
Since SSL certificates have been discontinued. It is all but certain that your certificates are all TLS, even if you may see them referred to as SSL.
That said, you should still check to confirm what version of TLS you’re using. Some older systems may still rely on TLS 1.0 and TLS 1.1 protocols, which were deprecated in 2021.
Common use cases for SSL/TLS today
SSL/TLS is widely used today, especially in the following settings:
- VPNs: Some VPN protocols rely on TLS/SSL to protect data while it’s in transit and ensure secure connections. OpenVPN is a widely used example. That said, some advanced protocols (such as ExpressVPN’s Lightway) achieve an equivalent level of security using other means.
- Securing websites, emails, and apps: TLS/SSL encrypts email, website, and app data while in transit, adding protection against anyone trying to intercept the data. It also adds protection when you back up your files to the cloud.
- Compliance and data protection standards: TLS/SSL can help organizations meet data protection regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
Best practices for implementing SSL/TLS
Follow the best practices below to optimize your SSL/TLS implementation.
Disabling outdated protocols
To get the highest level of protection and best performance, use TLS 1.3 or 1.2 rather than SSL or earlier versions of TLS.
Keeping up with TLS updates and patches
Always implement TLS updates and patches to benefit from security and performance upgrades. For instance, the jump from TLS 1.2 to TLS 1.3 entrenched PFS, preventing attackers from accessing past communication if they ever decrypt an encryption key.
Monitoring certificate validity and renewal
Regularly checking the validity of your certificates is crucial to prevent erroneous revocations or spoofing. Otherwise, you may put any data shared with your servers (including sensitive financial information) at risk of being intercepted by a third party.
You can automate certificate validity checks using OCSP stapling. With OCSP stapling, your server periodically obtains a signed validity response from the CA and presents it to clients during the TLS handshake. This allows clients to verify the certificate’s revocation status efficiently without contacting the CA directly.
How to test your TLS configuration for security

You can test the validity and security of your TLS configuration by entering your domain name into online tools like SSL Labs.
The complexity of your TLS integration will determine what else you need to test. Depending on the circumstances, you may need to look into:
- HTTP Strict Transport Security (HSTS)
- TLS Fallback Signaling Cipher Suite Value (SCSV)
- Encrypted Client Hello (ECH)
- Session resumption
- OCSP stapling
- TLS compression
- Certificate pinning
- Secure renegotiation
- Client-initiated renegotiation
FAQ: Common questions about SSL vs. TLS
Which is better, SSL or TLS?
Transport Layer Security (TLS) offers better security and performance and has fully replaced all versions of Secure Sockets Layer (SSL). That said, the term SSL is still sometimes used to refer to TLS.
Does HTTPS use SSL or TLS?
HTTPS uses Transport Layer Security (TLS). As a means of securing internet traffic and web communications, TLS is an improvement over Secure Sockets Layer (SSL) in every meaningful regard. HTTPS originally used SSL, but this protocol is now deprecated due to security vulnerabilities.
Why is SSL no longer used?
Secure Sockets Layer (SSL) pioneered internet communication security but is no longer used due to its susceptibility to vulnerabilities and performance issues. In its place, Transport Layer Security (TLS) has been developed to fix security vulnerabilities, improve performance, and, particularly with TLS 1.3, provide smoother adaptability to future threats.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN