SSL VPN vs. IPsec: Which VPN protocol is right for you?
The debate between Secure Sockets Layer (SSL) VPN and Internet Protocol Security (IPsec) is often framed as an enterprise IT question: how to securely connect corporate networks or remote employees. But it’s just as relevant for everyday VPN users, since many consumer VPN apps also rely on one of these two protocols for encryption and stability.
This guide breaks down what SSL VPN and IPsec actually are, how they differ, and when to use each, whether you’re managing a company network or simply choosing the best protocol in your VPN app.
What is IPsec?
IPsec is a suite of protocols developed in the 1990s by the Internet Engineering Task Force (IETF) to maintain the principles of confidentiality, integrity, and authenticity when accessing public networks. IPsec is usually implemented at the infrastructure level, ensuring it’s able to secure all the data that’s transmitted within a network.
In a VPN app, you’ll typically see it as Internet Key Exchange version 2 with Internet Protocol Security (IKEv2/IPsec) or Layer 2 Tunneling Protocol with Internet Protocol Security (L2TP/IPsec), two implementations that use IPsec for encryption and authentication. Many VPNs rely on IPsec for its stability and speed, especially when switching between Wi-Fi and mobile networks.
How IPsec works
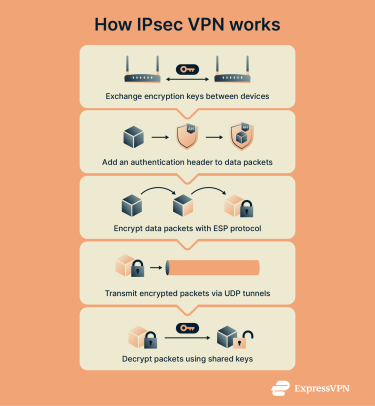 IPsec VPNs work via the following process:
IPsec VPNs work via the following process:
- Key exchange: Keys are strings of randomized data characters needed to encrypt and decrypt messages, which is why the first step in an IPSec connection is setting up keys between connected devices to ensure they can decrypt each other’s messages.
- Authentification: The authentication header (AH) protocol inserts a header* to each data packet that helps ensure integrity and authenticates the sender.
- Encryption: The Encapsulating Security Payload (ESP) protocol adds both a header and a trailer to each packet, encrypting and optionally authenticating them. Encryption and authentication parameters are negotiated and defined with protocols like IKEv2.
- Transmission: The encrypted packets are transmitted to their destination. IPSec typically uses User Datagram Protocol (UDP) instead of Transmission Control Protocol (TCP). This helps the packets pass through devices that perform Network Address Translation (NAT): a process that modifies IP addresses as data moves between private and public networks. Using UDP prevents these changes from breaking the secure connection.
- Decryption: Once the packets are received on the other end, they can be decrypted using the key that was set up initially, and the information can be viewed or used as needed.
*All data sent over a network is divided into small packets containing a payload (the data itself) and headers (routing information). IPSec adds extra headers, as well as a trailer placed after each packet’s payload that marks its end.
Learn more: Read our guide on TCP vs. UDP to better understand the difference.
IPsec modes
It’s worth noting that IPsec can operate in the following two modes. The particular mode determines how encryption is applied to data packets:
- Tunnel mode: It encrypts all data, including the information within a data packet and the IP address header, ensuring thorough protection. This makes it a good choice for public networks.
- Transport mode: This mode only encrypts the information within a data packet but not the IP address header, meaning the packet’s destination can be identified. It’s mainly used within closed and trusted networks.
Use cases and advantages of IPsec
- Comprehensive security: Because IPsec operates at the network layer (Layer 3), it encrypts all traffic from a device, regardless of the application generating it. This protects everything from web browsing and email to gaming and streaming without needing to configure individual apps.
- Strong authentication and integrity: The use of protocols like AH ensures that you are connected to the correct server and that your data hasn't been altered along the way.
- High stability: IPsec-based protocols like IKEv2 are known for their stability, especially on mobile devices. IKEv2 can quickly re-establish a secure connection if you switch between Wi-Fi and cellular data, making it a reliable choice for users on the go.
It’s also suited for an array of applications:
- Compliance-sensitive domains: IPsec is the preferred choice for corporate use within the healthcare and finance industries, since the data protection laws for such corporations and organizations require reliable security measures.
- Legacy systems: IPsec’s compatibility with various encryption types makes it effective for securing networks with older technology.
- Site-to-site VPNs: IPsec is considered the go-to choice for site-to-site VPN connections. For example, a company could use an IPsec VPN to connect its New York and London offices, allowing them to function as a single, secure network.
What is SSL VPN?
An SSL VPN uses the Secure Sockets Layer (SSL) / Transport Layer Security (TLS) protocol to create a secure, encrypted tunnel for data transmission. Operating at the application layer, it provides a flexible method for users to securely access a private network.
While the term “SSL VPN” is still widely used, the underlying technology evolved from the original SSL to the more secure TLS in 1999. The most common version you’ll see in VPN apps is OpenVPN, which uses TLS for encryption.
Learn more: Read our detailed guide on SSL vs. TLS.
It’s worth noting that there are two distinct kinds of SSL VPNs: SSL portal and SSL tunnel. SSL portal VPNs offer web-based interfaces where users can authenticate themselves to access authorized resources. In contrast, SSL tunnel VPNs require client-side software or browser plugins that enable the creation of a VPN tunnel for secure access to a network.
How SSL VPN works
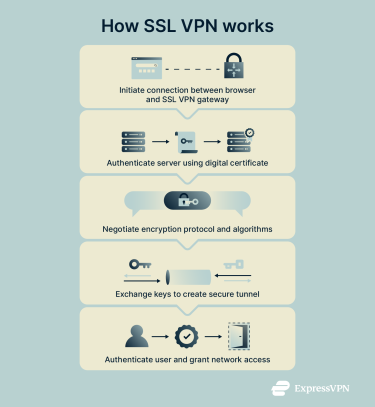 SSL VPNs operate via the following steps:
SSL VPNs operate via the following steps:
- Initial handshake: A user's web browser connects to their company's SSL VPN gateway.
- Server authentication: The gateway server sends a digital certificate to the user's browser, which validates its authenticity with a trusted certificate authority. This step confirms the user is connecting to the correct server.
- Encryption negotiation: After authentication, the server and the browser determine the cryptographic protocol and algorithms they will use for the session.
- Key exchange: The server and browser exchange either a shared secret or public keys to establish a secure, encrypted tunnel, ensuring that all data transmitted between the user and the network is safeguarded.
- User authentication and access: After a secure tunnel is established, the gateway presents the user with a login portal. The user's credentials are authenticated with the company's systems, granting them access to protected network resources with full end-to-end encryption.
Use cases and advantages of SSL VPN
SSL VPNs offer several key benefits that make them a strong option for both organizations and individual users:
- Granular access control: SSL VPNs enable granular access control management, allowing IT admins to grant access to specific resources or applications instead of a whole network.
- Ease of use: For clientless portal VPNs, there is virtually no setup required for the end-user beyond navigating to a website. For client-based SSL VPNs like OpenVPN, the software is typically straightforward and easy to install and use.
- Modern encryption: SSL/TLS is the backbone of web security and benefits from continuous updates. It uses reliable modern-day data encryption standards to keep data confidential.
They’re also widely used across different scenarios, including:
- Commercial VPNs: SSL/TLS is the foundation for OpenVPN, one of the most trusted and versatile VPN protocols available. It's often the default choice in consumer VPN apps due to its excellent balance of security and speed.
- Bring Your Own Device (BYOD) policies: SSL VPNs don’t require dedicated software, making them good options for organizations with BYOD policies. They enable employees to connect to company networks and resources without installing additional software on their system.
- Short-term access: The quick setup process of SSL VPNs makes them optimal for granting short-term access to temporary employees or contractors.
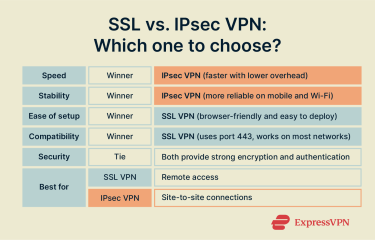
SSL VPN vs. IPsec: Key differences
They’re both meant to secure your data, but SSL and IPsec VPNs have key differences in terms of their security, what layer of the Open Systems Interconnection (OSI) model they operate at, how they interact with firewalls, how they perform, and how easy they are to set up.
Security and encryption methods
IPsec and SSL secure data at different points in the network stack. IPsec provides comprehensive security by authenticating and encrypting every IP packet, ensuring confidentiality and data integrity at a low level. IPsec can also maintain encryption between multiple network nodes, making it the preferred choice for companies that want to establish secure connections between multiple sites.
In contrast, SSL provides application-level security. It’s designed to secure data within a specific session. While effective for its intended use, an SSL VPN cannot secure all traffic within a network the way IPsec can.
Both IPSec and SSL VPNs support an array of data encryption standards. IPsec works with 128-bit or 256-bit Advanced Encryption Standard (AES), Blowfish, and Triple Data Encryption Standard (3DES) algorithms. On the other hand, SSL VPNs support 128-bit AES, 192-bit AES, 256-bit AES, 3DES, and Blowfish.
Network vs. application layer
IPsec functions at Layer 3 of the OSI model, similar to modern VPN protocols like WireGuard. This means it creates a secure tunnel that automatically encrypts all data leaving a device, regardless of the application generating it.
Learn more: Read our detailed comparison of WireGuard and IPsec.
An SSL VPN operates at the application layer (Layer 7) to encrypt specific apps or browsing sessions. This offers greater flexibility, as SSL VPNs can be configured to provide access to specific applications through a web browser or, like IPsec, create a full tunnel to encrypt all device traffic. However, full-tunnel SSL VPNs are more complex to set up and may not perform as efficiently as IPsec.
Firewall traversal
SSL VPNs have much better firewall compatibility, as their traffic goes through TCP port 443, the same port used for all standard HTTPS web traffic. Since blocking this port would effectively break secure access to most of the internet, it’s almost always left open, allowing SSL VPNs to connect reliably on nearly any network.
IPsec, on the other hand, uses specific ports like UDP 500 and 4500. These ports aren’t required for general web browsing and might be blocked by firewalls on private or public networks as a security precaution. This can make establishing an IPsec connection challenging in certain environments.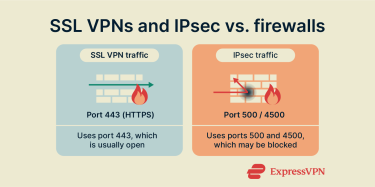
Deployment and ease of use
SSL VPNs are generally considered more straightforward, especially for large and diverse user groups. Their ability to function in a “clientless” mode through a web browser means users can get a secure VPN connection without installing any software.
In contrast, IPsec has a higher VPN configuration complexity. It requires client software installation and the configuration of encryption algorithms, authentication methods, and key exchange parameters between both ends of the tunnel. Any configuration issues can cause the connection to fail. IPsec also demands specific firewall rules to allow IPsec traffic, which adds another layer of complexity, especially when dealing with NAT.
Performance and speed
In a VPN performance comparison, IPsec typically delivers faster speeds and lower latency. This speed advantage comes from being processed in the operating system's kernel space, which is more efficient than the user-space processing required by SSL/TLS. This can make IPsec-based protocols like IKEv2 a better choice for activities requiring a faster connection, like gaming or high-quality streaming.
SSL VPNs can have slightly more overhead due to their user-space operation, but the performance gap has narrowed significantly thanks to modern, powerful processors. While the performance overhead won’t matter much for activities like day-to-day browsing, you may want to consider a different option if you need a gaming VPN with the fastest possible speeds.
Summary of key security and performance differences
The following table provides a summary of the key differences between IPsec and SSL VPNs:
| IPsec | SSL | |
| Primary function | Provides broad, network-level security for all traffic | Specializes in flexible, application-level security for specific web sessions |
| OSI layer | Network layer (Layer 3), encryption all traffic to and from the device | Application layer (Layer 7), securing traffic for specific apps or sessions |
| Firewall traversal | Uses ports (UDP 500/4500) that may be blocked by firewalls | Uses the standard web port (TCP 443), making it highly firewall-friendly |
| Deployment | More complex initial setup that requires client software and significant configuration | Simpler setup with a clientless browser-based option |
| Performance | Generally faster and has lower latency due to kernel-space processing | Has slightly more overhead and can be marginally slower due to user-space processing |
| Encryption algorithms | AES (128/256-bit), 3DES, DES, and Blowfish | AES (128/192/256-bit), 3DES, and Blowfish |
Learn more: Check out our article that explains and compares other VPN protocols as well.
Which VPN is better: SSL or IPsec?
There isn’t a single “better” VPN protocol. Each serves different needs depending on your use case, infrastructure, and security priorities. Understanding what you want to achieve with the VPN will help narrow down the right option.
Choose an IPsec-based VPN (like IKEv2) if performance and network-level integration matter most, since it:
- Offers high throughput and low latency, ideal for data-intensive tasks such as video conferencing or cloud access.
- Maintains stable connections when switching between networks (for example, cellular and Wi-Fi), which is great for mobile workers.
- Works well for both site-to-site and device-to-network communication, commonly used in enterprises and remote offices.
Choose an SSL-based VPN (like OpenVPN) if flexibility and accessibility are key, since it:
- Runs over standard web ports, improving compatibility with most networks and devices.
- Simplifies remote access setup by leveraging browser-based frameworks, making it easy for individuals to connect to private networks securely without complex configuration.
- Enables granular access control, letting administrators connect users to specific applications or internal services (ideal for business environments).
Many modern personal VPNs, such as ExpressVPN, support both OpenVPN (SSL-based) and IKEv2 (IPsec-based) protocols, allowing users to switch between them depending on their needs.
Learn more: Our IKEv2 vs. OpenVPN comparison provides more insight on how SSL-based protocols vary from IPsec-based ones.
FAQ: Common questions about SSL VPN vs. IPsec
What are the disadvantages of SSL VPN?
Disadvantages of Secure Sockets Layer (SSL) VPNs include the slight performance overhead that comes from encrypting and decrypting traffic at the application layer, and the fact that SSL VPNs often secure only specific types of traffic (like web or remote-access apps) instead of the entire network. Although full-tunnel SSL VPNs exist, they’re more complex to set up and may not perform as efficiently as Internet Protocol Security (IPsec).
Is SSL VPN outdated?
No. While the name refers to the older Secure Sockets Layer (SSL) protocol, modern SSL VPNs use its successor, Transport Layer Security (TLS), which is the current standard across the internet.
What is the primary advantage of SSL over IPsec?
The primary advantage of Secure Sockets Layer (SSL) over Internet Protocol Security (IPsec) is firewall traversal. By using Transmission Control Protocol (TCP) port 443, the same port as secure websites, SSL VPN traffic blends in with normal internet traffic and is almost never blocked by firewalls.
Is IPsec the most secure VPN?
It’s extremely secure, but it isn’t inherently safer than a properly configured Secure Sockets Layer (SSL) VPN. Both can use the same strong encryption ciphers, like 256-bit Advanced Encryption Standard (AES). The overall security of a connection depends more on the implementation and encryption standards used than the choice between the two protocols.
Do all VPNs use IPsec or SSL?
No. While many popular protocols are based on Internet Protocol Security (IPsec) or Secure Sockets Layer (SSL), like Internet Key Exchange version 2 (IKEv2) using IPsec and OpenVPN using SSL/TLS, there are various other options as well. These include older, less secure protocols like Point-to-Point Tunneling Protocol (PPTP) and newer, high-performance ones like WireGuard.
Why is SSL VPN more firewall-friendly than IPsec?
Secure Sockets Layer (SSL) VPNs are firewall-friendly because they use Transmission Control Protocol (TCP) port 443, which must remain open on almost all networks to allow access to secure websites (HTTPS). IPsec uses specific ports, like User Datagram Protocol (UDP) 500 and 4500, which aren’t essential for general browsing and are often blocked by network administrators as a security measure.
Is SSL VPN slower than IPsec?
Yes, because Internet Protocol Security (IPsec) operates at the kernel level, allowing faster packet processing and lower latency, while Secure Sockets Layer (SSL) works at the application level, introducing additional encryption and data-handling overhead that can slow performance.
Can IPsec and SSL be used together?
Yes, Secure Sockets Layer (SSL) and Internet Protocol Security (IPsec) can be used together in a multi-layered cybersecurity approach. A company might use IPsec for secure site-to-site connections to provide broad, network-layer protection while simultaneously using SSL VPNs to grant remote users application-level access.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN