What is a site-to-site VPN, and how does it work?

When businesses operate across different offices, countries, and time zones, keeping networks connected and secure can be challenging. A site-to-site virtual private network (VPN) helps by creating an encrypted tunnel between locations. That means people can share resources and communicate as if they’re on the same local network.
In this guide, we’ll explain what a site-to-site VPN is, how it works, the main types and protocols, and why it’s become a trusted way for businesses to keep their networks secure.
Understanding site-to-site VPNs
A site-to-site VPN connects entire networks rather than individual devices, acting like a secure tunnel between multiple locations.
How a site-to-site VPN connection works
Think of a site-to-site VPN as a secure underground tunnel between offices. It runs beneath a public road (the internet), and it’s fully sealed so only authorized traffic can pass through it.
Each location uses a VPN-compatible network gateway (often a router or firewall) to handle encryption, decryption, and tunnel management. When one office sends data, the gateway encapsulates and encrypts each data packet before it travels through the VPN tunnel. At the other end, the receiving gateway decrypts and unpacks the data and transmits it to the local network.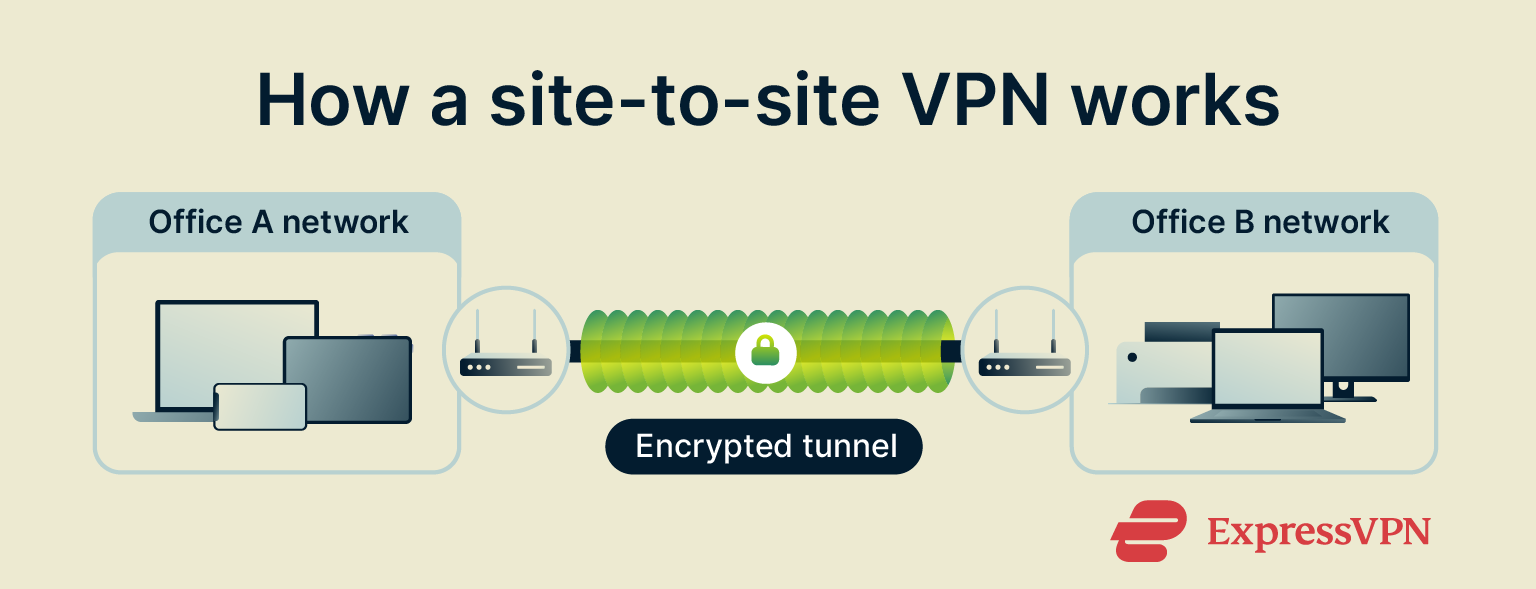
These gateways negotiate and maintain the tunnel, ensuring it stays encrypted and authenticated while traffic moves from point A to point B. For anyone using it, the entire process is invisible. It feels like they’re on the same local network, even though the traffic travels across the internet from each site.
Larger organizations can also connect multiple branch offices through these tunnels, either by setting up individual tunnels or by using a hub-and-spoke topology, where all locations connect through a central gateway.
Intranet and extranet site-to-site VPNs
Site-to-site VPNs are generally either intranet or extranet. Both types are commonly used VPNs for work and rely on encrypted tunnels to share data securely across locations. The main differences between them lie in who has access to the connected networks and what kind of information is shared.
An intranet VPN connects multiple locations within the same organization. For example, a company might link its headquarters in New York with regional offices in London so employees can securely access shared drives, databases, or applications from wherever they are. Everything stays within the company’s private network, even when the data travels across the internet.
An extranet VPN connects networks from different organizations. Businesses often use these when they need to collaborate securely with third parties or clients. Each side keeps its own systems private while using the VPN to share data or access common resources safely.
Site-to-site VPN vs. remote access VPN
A remote access VPN is designed for individual users and connects individual devices to a private network. For example, if someone is working from home or traveling, they might connect to their company’s network through a remote access VPN app or by using a remote desktop. The VPN encrypts their traffic, giving them secure access to internal resources on the network.
A site-to-site VPN connects entire networks instead of single devices. Once it’s set up, anyone within the connected offices can use shared servers or applications automatically, without needing to turn on a VPN themselves. It’s designed for always-on, network-to-network communication rather than individual logins.
Site-to-site VPN vs. point-to-site VPN
Site-to-site and point-to-site VPNs both connect remote locations to a private network, but they differ in scale and setup.
A point-to-site VPN is a specific type of remote access VPN that’s typically used in cloud or hybrid environments. It creates a secure link between one device and a company network, for example, an employee’s laptop to company resources stored in the cloud. Because it’s managed through centralized VPN gateways, it’s ideal for remote staff who need safe access from home or while traveling.
A site-to-site VPN connects whole networks instead of single devices. It links offices together, so people in each location can share files and applications easily and securely. There’s no need for individual logins, as everything between sites stays connected and encrypted by default.
Site-to-site VPN vs. commercial VPN services
Commercial or consumer VPNs are built for everyday internet privacy. They encrypt a user’s traffic, mask their IP address, and route their connection through a secure server before it reaches the web. It’s a simple way for people to protect their data or browse safely on public Wi-Fi.
Site-to-site VPNs are different. They’re used for branch office connectivity, linking entire networks directly to one another. They’re less about browsing or streaming privately, and more about maintaining secure communication between networks and giving people access to shared resources across locations.
Why businesses use site-to-site VPNs
For organizations with multiple offices or data centers, a site-to-site VPN helps maintain a private network across locations, letting teams work together as if they were under one roof.
Secure inter-office communication
Site-to-site VPNs create a protected channel for communication between offices. Messages, file transfers, and application traffic all travel through an encrypted tunnel instead of the open internet. That means sensitive data stays private, even when employees connect from different parts of the world.
Data protection and encryption benefits
Every packet of data that passes through a site-to-site VPN is encrypted, preventing outsiders from reading or tampering with it. This protection is especially important for businesses handling sensitive data, such as financial information or customer records. Even if someone manages to intercept the data, encryption ensures they can’t read it or understand it.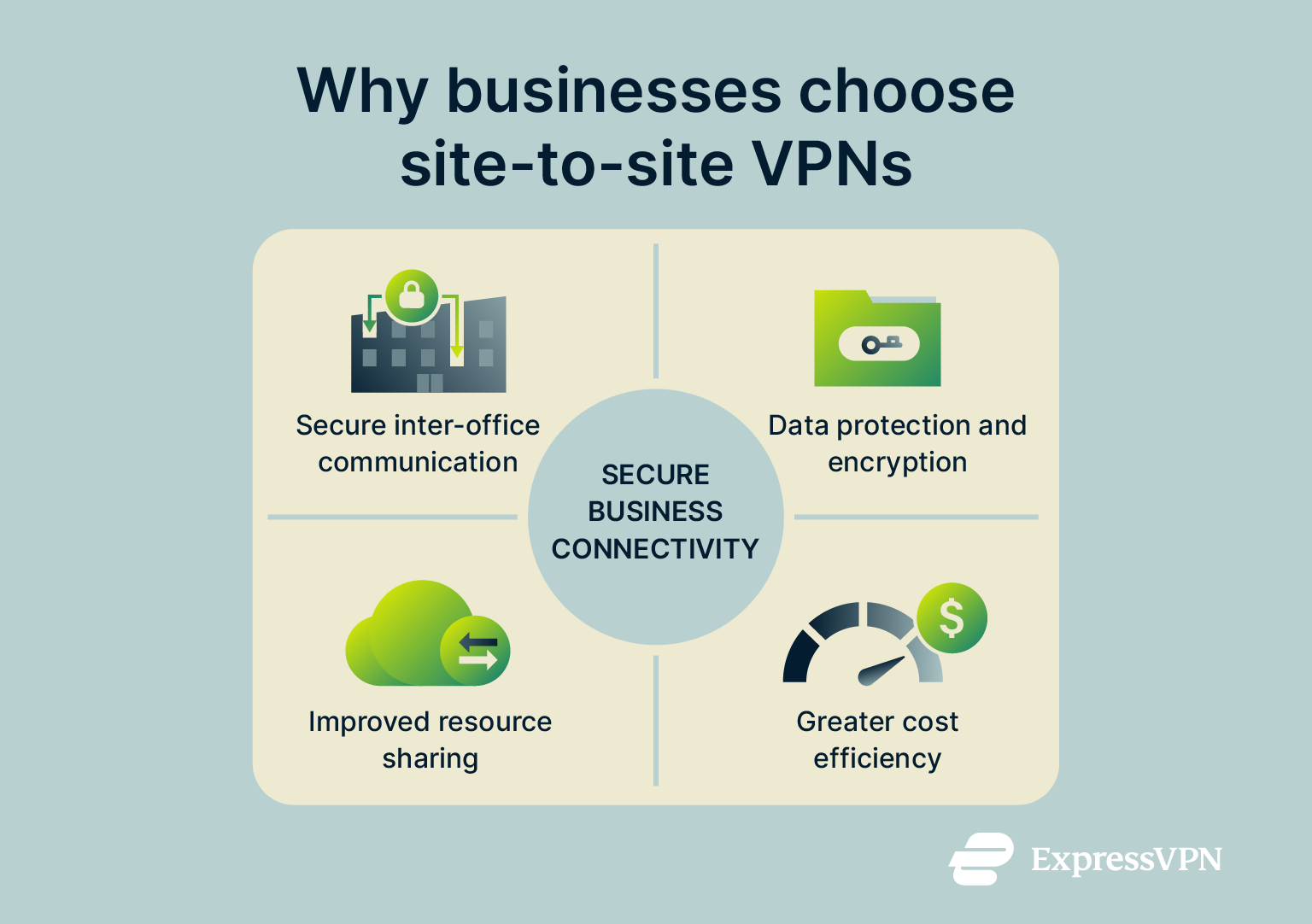
Improved resource sharing across locations
Because the VPN links entire networks, employees in one office can easily access shared drives, databases, or internal tools hosted elsewhere. Teams can collaborate in real time, use the same systems, and share updates instantly, even across countries. There’s no need to set up separate logins or connections for each person.
Cost efficiency compared to dedicated links
Before VPNs, companies often relied on leased lines or other dedicated connections to link offices. Those options were secure but expensive and inflexible. A site-to-site VPN provides similar security at a reduced cost, using the public internet as the transport layer while keeping data encrypted end-to-end. It also scales more easily as businesses add new offices or cloud resources.
Site-to-site VPN protocols and security standards
Behind every site-to-site VPN is a set of protocols that decide how the connection is built and protected. These standards control how data is encrypted, authenticated, and sent between networks, ensuring privacy and reliability for every exchange.
IKEv2/IPsec explained
Most site-to-site VPNs use the Internet Protocol Security (IPsec) protocol to keep data secure as it moves between networks. IPsec encrypts every data packet that passes through the tunnel, so it can’t be read or modified in transit. It also checks each data packet’s integrity, ensuring that it’s not been tampered with along the way.
Internet Key Exchange version 2 (IKEv2) works alongside IPsec to establish and manage the secure connection. It authenticates both ends of the connection, negotiates which encryption algorithms and keys to use, and sets up the parameters of the IPsec tunnel.
Once the connection is active, IKEv2 continues to manage session keys automatically. It also re-establishes the connection if it drops or if a network’s IP address changes, such as when switching between different connections or ISPs.
Together, IKEv2 and IPsec form a secure, reliable connection that’s built into most business routers and firewalls. They’re fast, stable, and trusted by enterprises that need consistent, always-on protection between sites.
GRE tunnels and MPLS integration
Most VPN tunnels based on IPsec only encrypt and transport IP traffic. When businesses need to carry multiple types of traffic, including non-IP protocols, they often use Generic Routing Encapsulation (GRE).
GRE encapsulates various protocols by wrapping them in IP packets so they can travel across the internet. On their own, GRE tunnels don’t encrypt data, so they’re often paired with IPsec to add encryption.
For larger networks, multiprotocol label switching (MPLS) can work alongside VPNs to manage how traffic moves between sites. It doesn’t handle encryption, but it helps make sure important applications like voice or video calls run smoothly, even with limited bandwidth. It directs packets along predefined, high-priority paths based on labels, so that time-sensitive data always follows the fastest and most reliable route. When combined with a site-to-site VPN, MPLS can add more speed and consistency for communication between networks.
Common encryption algorithms (AES, SHA, RSA)
Every VPN connection uses several cryptographic tools to keep data private and verify its integrity. The most common are:
- Advanced Encryption Standard (AES): Encrypts the data itself. It’s fast, secure, and used by governments and enterprises alike to protect sensitive information.
- Secure Hash Algorithm (SHA): Ensures data hasn’t been tampered with by creating a unique fingerprint of each packet. If that fingerprint changes, the system knows the data was altered.
- Rivest–Shamir–Adleman (RSA): Handles authentication and securely exchanges encryption keys between VPN gateways before the tunnel starts.
How to choose the right protocol for your network
The right choice depends on the size and complexity of the network. For most organizations, IKEv2/IPsec offers the best balance of security, speed, and compatibility. Businesses with more demanding setups might pair GRE with IPsec or use MPLS to manage large-scale traffic.
The goal is to protect data without adding unnecessary complexity. A well-chosen protocol should keep communication secure while allowing everyday operations to run smoothly.
How to set up a site-to-site VPN (step-by-step)
Setting up a site-to-site VPN involves configuring the gateways at each location to communicate securely with one another. The exact steps vary depending on hardware and software, but most setups follow the same general process.
Initial requirements
Before you begin, make sure you have:
- Two or more networks with unique local IP address ranges
- VPN-compatible routers or firewalls at each site
- Stable internet connections and static public IP addresses for the gateways
- Administrative access to configure both devices
Step 1: Configure network interfaces
Start by checking that each gateway’s network interfaces are correctly assigned. You’ll need one for the internal network and one for the external internet connection. This ensures that internal traffic meant for the other office is routed through the VPN tunnel instead of the public internet, keeping data secure between locations.
Step 2: Create the VPN tunnel
Next, create the tunnel responsible for encrypted data transmission between gateways. Define the public IP addresses for each endpoint and specify the tunnel type, usually IPsec. At this stage, you’ll also need to decide which subnets or networks will communicate through the tunnel.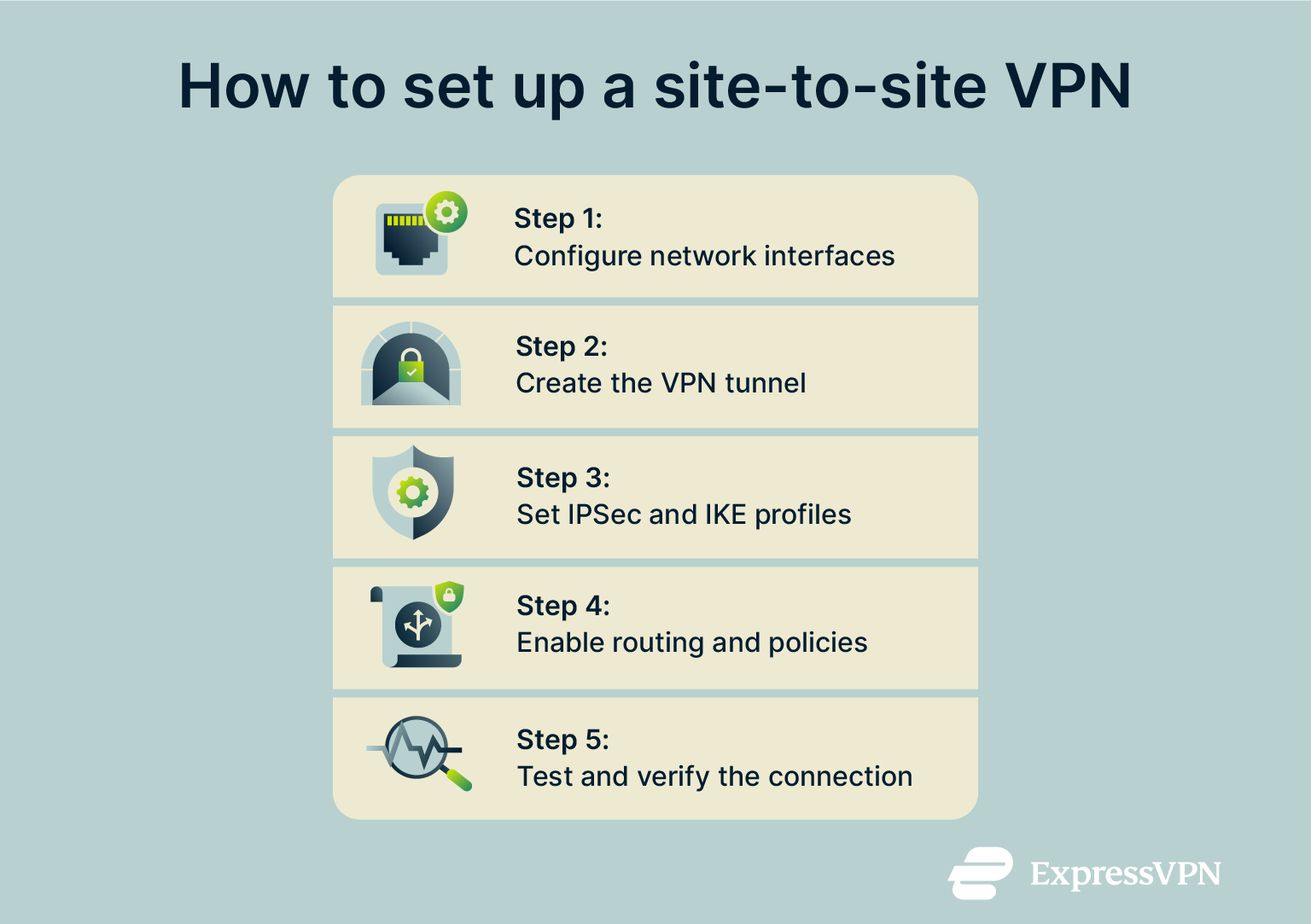
Step 3: Define IPsec and IKE profiles
Once the tunnel is in place, set up your encryption and authentication settings. Set the IKE version to IKEv2 for greater stability and automatic reconnections. Make sure the settings match on both sides (if they don’t, the connection won’t establish).
Step 4: Enable routing and policy rules
After defining the security profiles, enable routing between the connected networks. Add policy rules that determine which traffic can use the VPN. For example, you might allow only traffic from specific IP ranges or business applications. This helps keep the connection secure while giving your team the access they need.
Step 5: Test and verify the connection
When everything is configured, test the VPN to confirm that both gateways can reach each other. Try accessing shared resources across sites to make sure traffic is flowing correctly. If the connection fails, mismatched configurations could be causing issues. Double-check your encryption settings, IP ranges, or firewall rules to ensure everything is set up correctly.
How to configure the site-to-site VPN
Most modern business routers and firewalls include a built-in interface that simplifies the configuration process. You’ll usually find a VPN or site-to-site section in the admin panel where you can create and manage tunnels. Many devices also include setup wizards or templates for common IKEv2/IPsec configurations.
If you’re using cloud platforms like Amazon Web Services (AWS) or Azure, you can use their built-in VPN tools. These typically involve entering your site gateway details and downloading a preconfigured IPsec template to apply to your router or firewall.
Whatever platform you use, document your settings before you let others use it. You should maintain a clear record of IP addresses, encryption parameters, and shared keys so you can easily troubleshoot issues if they come up.
Troubleshooting common setup issues
Even with careful configuration, site-to-site VPNs can fail to connect or work inconsistently. Most problems come down to mismatched settings or network conflicts. Here are some of the most common issues and how to resolve them.
Phase 1 or Phase 2 negotiation failures
If the VPN tunnel doesn’t establish, the gateways may not agree on encryption or authentication settings. Even a single mismatch can prevent the entire connection from working correctly. Check that both sides use the same IKE version, encryption algorithm, hashing method, key exchange group, and authentication method.
Incorrect or overlapping subnets
A site-to-site VPN can’t route traffic correctly if both networks use the same local IP range. Make sure each site has a unique subnet, for example, 192.168.1.0/24 for one office and 192.168.2.0/24 for another. If there’s an overlap, change one of the networks to a different range before re-establishing the tunnel.
NAT or firewall blocking
If your VPN tunnel won’t connect, your firewall or Network Address Translation (NAT) settings might be getting in the way. Some routers block the traffic that VPNs rely on. Check that User Datagram Protocol (UDP) ports 500 and 4500 are open for IKE and IPsec, and that Encapsulating Security Payload (ESP) packets aren’t being filtered. If the connection still fails, try temporarily turning off NAT to see if it fixes the issue.
Route configuration errors
If your VPN tunnel is connected but you still can’t access files or servers on the other network, the issue might be with your routing setup. Each VPN gateway needs to know where to send traffic for the other network, usually through a static route or a dynamic routing protocol. If those routes aren’t in place, your data might try to go over the public internet instead of through the secure VPN tunnel.
DNS resolution problems
If the VPN tunnel connects but you can’t reach other devices by name, the issue could be with the Domain Name System (DNS). Make sure your DNS settings include the internal DNS servers used by each network. If needed, set up conditional forwarding so that local domain names are resolved by the right site.
Tunnel drops or unstable connections
If your VPN keeps disconnecting, it’s often due to a weak internet connection or how the tunnel is set to refresh its encryption keys. Firewalls that close idle connections too quickly can also cause drops. Make sure both sides use similar timeout and refresh settings, and turn on options like Dead Peer Detection (DPD). This checks that both sides of the VPN tunnel are still connected and restarts if one side is inactive.
Cloud platform or vendor-specific issues
If your VPN runs through a cloud service like AWS or Azure, check the platform’s website for detailed error messages. Cloud providers often have stricter setup rules than on-premises hardware, so even small differences can stop the connection from working, like a mismatched password or missing security settings.
Best practices for a secure site-to-site VPN
Once your site-to-site VPN is running, it’s important to maintain it so it stays secure. Here are some top tips to ensure it’s protected.
Use strong authentication and encryption
Stick with modern encryption standards like AES for data protection and SHA for integrity checks. Avoid outdated protocols like Point-to-Point Tunneling Protocol (PPTP) and weak algorithms like the Data Encryption Standard (DES), and pair encryption with secure authentication and strong, complex pre-shared keys. Even better, use digital certificates for extra trust and easier management across multiple sites.
Regularly rotate keys and certificates
Keys and certificates don’t last forever; make sure to update them regularly to reduce the risk of them being compromised and ensure you’re meeting security policy requirements. Automating renewals can save time and prevent mistakes that might cause downtime.
Implement network segmentation
A VPN tunnel shouldn’t give blanket access to everything. Split internal resources into zones so that people only reach what they need, like certain documents and files, while keeping other systems and servers separate. This limits the impact of any breach and makes network monitoring simpler.
Monitor logs and set up alerts
Keep an eye on your VPN logs to spot issues early. Turn on logging for both gateways and check for failed connections or unusual traffic. You can also set up automated alerts for repeated errors to help you respond quickly before small problems become major outages.
Combine with firewall and IDS/IPS tools
A VPN encrypts traffic, but it doesn’t block attacks on its own. Combine it with firewalls and intrusion detection or prevention systems (IDS/IPS) to catch and stop suspicious activity. A layered approach makes it harder for anyone trying to infiltrate your network to get through. Even if one defense fails, the others can keep your network protected.
Limitations and challenges of site-to-site VPNs
While site-to-site VPNs provide secure and reliable links between networks, they’re not perfect, especially when it comes to management across huge networks.
Scalability constraints
A site-to-site VPN is great for connecting a few offices, but things get complicated as more locations are added. Each new location needs its own tunnel setup, which takes time and adds room for error. Larger organizations often rely on centralized management tools or software-defined networking (SDN) to keep everything organized.
Performance and latency issues
Because VPNs encrypt and reroute traffic, they can slow things down slightly. The effect is usually small, but distance and connection speed matter. Offices that are far apart or rely on slow internet links may notice delays when trying to access files or applications on other servers. Network hardware quality and heavy data use can also affect performance and create latency issues.
Complex configuration and maintenance
Managing several VPN tunnels isn’t always straightforward. A single typo, mismatched encryption setting, or outdated firmware can break a connection. It’s important to stay on top of updates and keep detailed configuration notes to help prevent downtime and keep the network running smoothly.
Limited cloud integration
Traditional site-to-site VPNs were built for fixed, on-premises networks. As more businesses shift to the cloud, connecting those VPNs with cloud services can be tricky. Platforms like AWS and Azure include built-in VPN gateways, but linking them with older systems often takes extra setup and know-how.
Depends on static locations
Site-to-site VPNs work best when each network has a stable, known IP address. That’s fine for offices with fixed internet connections, but it’s less ideal for temporary or mobile setups. If an IP changes often, the tunnel might drop or fail to reconnect. In those cases, cloud-based or zero-trust models can offer a more flexible alternative.
Modern alternatives to site-to-site VPNs
As business networks evolve, newer technologies have emerged that offer more flexibility and scalability than traditional site-to-site VPNs.
Software-defined WAN (SD-WAN)
SD-WAN uses specialized software to manage how traffic moves between offices, data centers, and cloud platforms. Instead of relying on fixed VPN tunnels, it automatically routes data based on performance, availability, and security. This helps keep connections fast and reliable, especially for companies with many branch offices or heavy cloud use.
Unlike traditional VPNs, SD-WAN can use several types of connections at once, such as broadband, fiber, or LTE, and switch between them to maintain speed and uptime. It also offers centralized management, which makes it easier to scale and monitor large, distributed networks.
Secure Access Service Edge (SASE)
SASE combines networking and security in a single, cloud-based framework. It brings together tools like SD-WAN, firewalls, and secure web gateways under one platform to connect people and offices safely without relying on physical VPN gateways.
With SASE, traffic is authenticated and inspected as it moves between users, devices, and applications, wherever they are. This makes it a strong fit for organizations with global teams or hybrid environments that mix on-premises and cloud systems.
Cloud-native zero-trust solutions
Zero-trust networking takes a different approach. Instead of assuming that traffic inside a VPN tunnel is safe, it checks every connection individually. The system verifies each person’s identity, device, and security status before granting access.
This model removes the need for a single, broad network connection. Instead, it secures each session separately, which makes it suitable for companies with remote employees, contractors, or workloads spread across multiple cloud platforms.
FAQ: Common questions about site-to-site VPNs
What are the two types of site-to-site VPNs?
The two main types of site-to-site VPNs are intranet and extranet VPNs. An intranet VPN connects networks within the same organization, while an extranet VPN links networks between different organizations, such as business partners or clients.
Is a site-to-site VPN encrypted by default?
Yes. A properly configured site-to-site VPN encrypts traffic automatically, usually through Internet Protocol Security (IPsec). This ensures that data moving between locations stays private and protected from interception, even when it travels across the public internet.
How do I know if my site-to-site VPN is working properly?
You can check the VPN’s status in your router or firewall dashboard. A stable connection should show active tunnels with no recent negotiation errors. To confirm traffic is flowing securely, review the VPN logs or use network monitoring tools to verify encryption status, uptime, and throughput. You can also test connectivity by pinging or accessing shared resources between sites.
What are the disadvantages of a site-to-site VPN?
Site-to-site VPNs can be complex to set up, especially for large or dynamic networks. They require compatible hardware, stable internet connections, and ongoing maintenance. Other limitations include potential latency, difficulty integrating with cloud environments, and reliance on static IP addresses.
Which VPN protocol is best for business environments?
For most organizations, Internet Key Exchange version 2 with Internet Protocol Security (IKEv2/IPsec) offers the best balance of speed, compatibility, and encryption strength. It’s widely supported across enterprise hardware and provides automatic reconnection if the network drops. Larger networks may also use Generic Routing Encapsulation (GRE) or multiprotocol label switching (MPLS) alongside IPsec for added flexibility.
Can a site-to-site VPN connect multiple branch offices?
Yes. You can configure multiple tunnels between branch offices or use a hub-and-spoke topology, where all sites connect through a central gateway. This setup makes it easier to manage traffic and maintain consistent security policies across locations.
What’s the difference between IPsec and SSL VPNs?
Internet Protocol Security (IPsec) VPNs protect traffic at the network layer and are ideal for connecting entire networks, such as in site-to-site setups. Secure Sockets Layer (SSL) VPNs operate at higher layers of the network and use Transport Layer Security (TLS) encryption to protect data. They’re typically used for remote access, allowing people to securely reach internal resources through a web browser or VPN app, often without needing full network-level access.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN