The ultimate guide to recursive DNS: Everything you need to know
The internet runs on a complex system called the Domain Name System (DNS) that turns human-readable domain names into machine-readable IP addresses.
A recursive DNS server is a vital part of this system, because it looks up the addresses on your behalf and makes the whole process a lot more efficient than it would otherwise be.
This guide explains why recursive DNS matters, breaks down how it works, and explores the benefits and risks of using it.
What is recursive DNS?
A recursive DNS server (or recursive resolver) is a key part of the DNS hierarchy that handles domain lookups on behalf of users. When you enter a website address in your browser, your device sends the request to a recursive resolver, typically run by your internet service provider (ISP) or a public DNS service like Google (8.8.8.8) or Cloudflare (1.1.1.1). The resolver’s job is to return the IP address associated with that domain name.
If the resolver already has the answer stored in its cache, it immediately responds to your device. If not, it performs what’s known as a recursive DNS lookup: it takes responsibility for finding the answer by querying other DNS servers in sequence: the root server, the top-level domain (TLD) server, and finally the authoritative name server for the domain. Once the resolver gets the correct IP address, it returns it to your device and saves it in its cache for future requests.
Recursive vs. iterative DNS
Behind the scenes, the recursive resolver performs a series of iterative queries to those DNS servers. In an iterative DNS lookup, each server responds with the best information it has: either the final record or a referral to another server that’s closer to the answer. The recursive resolver follows these referrals step by step until it reaches the authoritative source.
From the user’s perspective, it looks like a single, seamless process: you make one recursive query to your DNS resolver and get one final answer. But under the hood, that recursive lookup is made possible by multiple iterative lookups between DNS servers themselves.
In short, recursive DNS describes the client-to-resolver process, where the resolver does all the work on your behalf, while iterative DNS describes how that resolver communicates with the rest of the DNS hierarchy to retrieve the answer.
Step-by-step DNS resolution process
Understanding how recursive and iterative lookups work together is easier once you see the full DNS resolution process in action:
- Your device sends a request to the recursive DNS server: When you type a website URL like www.example.com into your browser, your device sends a request to a recursive DNS server to find the corresponding IP address.
- The recursive DNS server checks its cache: The recursive server looks in its cache to see if it already has the IP address for this website. If it does, it can return the answer immediately.
- Querying the root DNS server: When a recursive server doesn’t have the requested address cached, it may start its search at the top of the DNS hierarchy: the root DNS servers. In practice, however, this happens quite rarely. Root server information, like the locations of the TLD servers, is cached for a long time, so most recursive queries can skip the root level entirely and go straight to the appropriate TLD server. The root servers are only contacted when the resolver’s cache doesn’t contain that information, at which point they direct the resolver toward the correct TLD server.
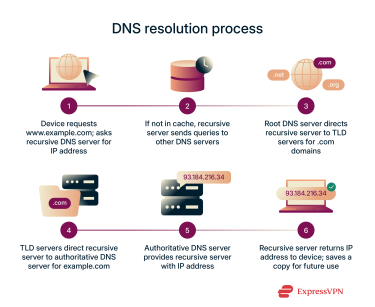
- Querying the TLD server: TLD servers manage domains within a specific extension, such as .com or .org, and direct the recursive server to the correct authoritative DNS server for the domain.
- Querying the authoritative DNS server: Authoritative servers hold the official records for domain names and their corresponding IP addresses. This server responds with the IP address for the requested domain.
- Returning the result to your device: The recursive DNS server gives the IP address to your device, allowing your browser to connect to the website. To speed up future visits, the recursive server may keep a copy of the address for a certain period.
Benefits of using recursive DNS
Recursive DNS delivers several important performance and security benefits that improve everyday browsing.
Speed and efficiency improvements
One of the biggest benefits of recursive DNS is faster resolution. When a domain has been looked up recently, the recursive server can return the result instantly from its local cache, which is stored on the server close to the user. This saves the time it would take to query more distant authoritative servers, reducing response times and network latency and making browsing smoother and more reliable.
Recursive DNS also helps spread out the workload. In the current system, most requests are handled by one of thousands of local recursive servers, rather than having to be managed by authoritative servers. This setup helps keep authoritative servers responsive and allows the DNS system to scale efficiently to handle the enormous volume of queries across the internet.
Security features of recursive DNS
Recursive DNS servers do more than speed up browsing; they also add layers of security that protect users and networks from malicious activity. Below are two major ways they help keep users safe.
DNSSEC implementation
Many recursive DNS servers use DNS Security Extensions (DNSSEC) to verify that the information they receive from authoritative servers has not been tampered with.
DNSSEC works by adding cryptographic signatures to DNS records, similar to placing a seal on a physical letter. When a recursive server receives a response, it “checks the seal” to ensure the data is authentic and hasn’t been altered. If the verification fails, the server can reject the response, protecting users from attacks like cache poisoning or redirection to malicious sites.
This process creates a chain of trust from the root servers down to individual domains, helping ensure that users reach the intended websites safely.
Phishing and malware protection
Some recursive DNS providers offer protective DNS services that actively block access to known malicious domains, including those associated with phishing, malware, and botnets. By filtering these domains at the DNS level, recursive servers prevent connections to harmful sites before any data is exchanged.
Some providers also support encrypted DNS protocols such as DNS over QUIC (DoQ), which encrypt queries between your device and the recursive server. This prevents attackers from intercepting your DNS requests or pretending to be the server by sending fake responses (IP spoofing), which could otherwise redirect you to malicious websites.
Drawbacks of recursive DNS
Recursive DNS servers offer speed and security benefits, but they do have limitations. Awareness of these drawbacks helps users manage these risks effectively.
Potential security risks
Recursive DNS servers handle requests from many users, which makes them potential targets for abuse. Improperly secured servers may leak information about user queries or be exploited to bypass security protections.
Cache poisoning and DNS spoofing
Cache poisoning occurs when a threat actor inserts incorrect DNS records into a recursive server’s cache. This tricks the server into associating a domain with the wrong IP address. The result, sometimes called DNS spoofing, can direct users to fraudulent or malicious websites that steal personal information or deliver malware.
DNS tunneling
Threat actors can embed data inside what looks like normal DNS traffic, using DNS queries and responses to secretly send and receive information. With this technique, criminals can exfiltrate sensitive data, run command-and-control channels, or move malware into a network. Because DNS is essential to internet operation and is often implicitly trusted, DNS tunneling can be difficult to detect without focused monitoring and controls.
Man-in-the-middle (MITM) attacks
In this type of attack, the cybercriminal positions themselves between a user and a recursive DNS server to intercept and manipulate communication. For example, when a device requests the IP address of a bank’s website, the attacker could redirect the device to a fake website designed to steal their login credentials or personal information. The attacker could also redirect the device to a malicious website that infects the device with malware.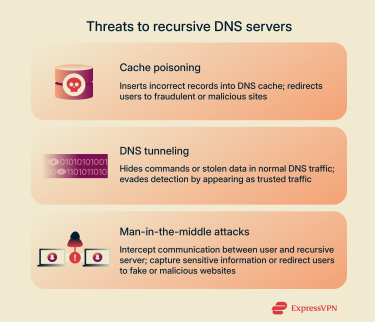
Misconfigurations and performance issues
Recursive DNS servers can experience performance issues due to misconfigurations or network challenges. For instance, improperly configured DNS records, such as incorrect IP addresses or missing essential records, can lead to resolution failures.
Additionally, high time-to-live (TTL) values, which determine how long a DNS record is stored before the server checks it again, can cause outdated records to persist in caches longer than necessary. This can delay updates and potentially lead to users being directed to outdated or incorrect destinations.
For businesses managing their own DNS setup, using a managed DNS service can help reduce these risks. These services host and maintain your DNS records, ensuring that they're correctly configured, automatically updated, and optimized for performance and reliability.
Changing recursive DNS servers
The recursive DNS servers you use by default are usually assigned by your ISP. However, you can change your DNS resolver to another provider. Popular third-party DNS providers include Cloudflare (1.1.1.1 or 1.0.0.1), Google Public DNS (8.8.8.8 or 8.8.4.4), and OpenDNS (208.67.220.220 and 208.67.222.222).
There are several reasons why you might want to change your DNS provider:
- Slow ISP DNS servers: Switching to a faster or better-optimized DNS can reduce latency and improve page load times.
- Outages or reliability issues: If your ISP’s DNS stops working, you might not be able to load websites. Switching to another DNS server can restore access.
- Malware and phishing protection: Security-focused DNS providers automatically block known malicious domains.
- Content filtering: Some DNS providers let you block adult content, social media, or other categories.
- Specialized services or features: Some DNS providers offer features tailored for streaming, gaming, or other online services, which can improve performance or reliability. For example, if you have ExpressVPN, you can use its DNS service, MediaStreamer, to improve your streaming experience.
Best practices for securing recursive DNS servers
As we’ve seen above, recursive DNS servers are critical for fast and reliable internet access, but they’re also prime targets for attacks such as cache poisoning and DNS tunneling. Applying these best practices can strengthen your organization’s DNS infrastructure and reduce security risks.
Monitor DNS traffic
Regularly review your server logs and analyze traffic patterns. Unusual spikes or repeated failed queries can indicate malicious activity, like DNS tunneling. Early detection helps mitigate attacks before they affect users or compromise data.
Apply rate limiting
Rate limiting restricts how many DNS queries a client or network segment can send in a given time. This prevents abuse, protects the server from overload, and reduces the risk of amplification attacks that use your server to flood other networks.
Manage caching
Shorter TTL values ensure records are refreshed frequently, keeping cached information up to date and accurate. Cache locking prevents records from being modified by unauthorized sources, maintaining the integrity of DNS responses.
Restrict open resolver access
Allow only trusted users to access your recursive DNS server. This reduces exposure to external threats and prevents the server from being exploited in amplification attacks or other malicious activities.
Check for DNS leaks
Ensure that your DNS queries are handled only by your trusted recursive server. Queries sent through unauthorized servers could be intercepted by third parties. DNS leak test tools like this one can help identify leaks and confirm that your server is properly configured.
FAQ: Common questions about recursive DNS
Is Google DNS recursive?
Yes, Google Public DNS is a recursive server. It handles the process of finding the IP addresses for the websites you want to visit, performing the necessary lookups on your behalf.
What is an example of a recursive DNS server?
Examples of recursive Domain Name System (DNS) servers include Cloudflare (1.1.1.1 or 1.0.0.1), Google Public DNS (8.8.8.8 or 8.8.4.4), and OpenDNS (208.67.220.220 or 208.67.222.222).
How does DNS caching improve performance?
Domain Name System (DNS) caching improves performance because it allows the recursive DNS server to provide the answer immediately for frequently visited domains without going through the whole lookup process.
What are the risks of using open DNS resolvers?
Open Domain Name System (DNS) resolvers can be vulnerable to cyberattacks, including cache poisoning, which redirects users to malicious sites. Additionally, some open DNS servers log IP addresses and queries, raising potential privacy concerns.
Can recursive DNS be used for business?
Yes, businesses can use recursive Domain Name System (DNS) to improve network performance, security, and control. It can help distribute query loads efficiently, block access to malicious domains, and filter content according to company policies. Some companies rely on managed DNS services to handle setup and maintenance, reducing administrative overhead and minimizing the risk of misconfigurations.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN