What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a cybercrime business model in which ransomware developers create, maintain, and monetize ransomware platforms by leasing them to affiliates, who conduct intrusions and ransomware deployments in exchange for a share of the proceeds.
In this post, we cover how the RaaS business model works, what the risks are, and how businesses can protect themselves against it. We also discuss some of the core challenges of combating RaaS and answer frequently asked questions about RaaS attacks.
Note: RaaS is illegal, unethical, and harmful to both victims and the public. This post is for educational and defense purposes only.
How does Ransomware-as-a-Service (RaaS) work?
The RaaS business model works by separating the creation of ransomware from the act of carrying out attacks. Instead of a single threat actor building malware and deploying it themselves, RaaS divides the work between different parties, each responsible for a specific part of the operation.
This separation allows ransomware campaigns to scale quickly, lowers the skill level required to participate in a ransomware attack, and makes operations more resilient when individual actors are disrupted or arrested.
The ransomware ecosystem
An RaaS ecosystem consists of several distinct roles, each contributing to a different stage of the attack lifecycle. At the foundation of this ecosystem are ransomware developers, who build the ransomware, update it, and tweak it to slip past the latest security tools. They keep the malware working so it’s “attractive” to buyers (other cybercriminals).
RaaS operators take this malware and turn it into a service. They run the platforms that support attacks, including infrastructure for generating ransomware builds, managing encryption keys, hosting payment and negotiation portals, and operating data-leak sites. Operators also recruit and manage affiliates, set usage rules, and define how ransom payments are split. In some RaaS groups, operators and developers may overlap, but in more mature ecosystems, these roles are often distinct.
Affiliates carry out the attacks themselves. They gain access to victim environments using techniques such as phishing, stolen credentials, exposed remote services, or access purchased from brokers. Once inside a network, affiliates expand their access, identify valuable systems and data, deploy the ransomware, and engage in extortion and negotiation with victims. If a victim pays the ransom, the affiliates typically receive the larger portion, reflecting their higher operational risk.
In more mature RaaS ecosystems, initial access brokers (IABs) specialize in the early stages of compromise. These actors focus on breaking into organizations and then selling that access to ransomware affiliates. By purchasing ready-made access, affiliates can bypass the time-consuming intrusion phase and move directly to lateral movement, data theft, and ransomware deployment.
Types of RaaS revenue models
RaaS providers offer a range of pricing models for cybercriminals to choose from. Here are some of the most common options:
- Monthly subscription: Access comes with a recurring fee that covers ransomware tools, updates, dashboards, and basic support, keeping costs predictable for attackers.
- One-time fee: A single upfront payment grants ownership of the ransomware code, usually without ongoing updates or hands-on support.
- Affiliate programs: Affiliates pay a monthly access cost and agree to share a portion of each ransom with the operator.
- Profit sharing: No upfront payment is required, but operators take a significant cut of each ransom in exchange for full access to the platform.
Is Ransomware-as-a-Service legal?
RaaS is illegal. Beyond the fact that ransomware deployment itself constitutes criminal conduct, the RaaS business model independently violates criminal law in the U.S. and most countries around the world. Operating a RaaS program necessarily involves conspiracy to commit computer fraud, aiding and abetting unauthorized access and cyber extortion, and knowingly facilitating and profiting from downstream criminal acts.
That’s why criminal liability isn’t limited to the individual who deploys the ransomware. Developers, operators, infrastructure providers, and anyone who knowingly facilitates or profits from ransomware activity can be charged as principals or co-conspirators, even if they never directly interact with a victim.
Although U.S. prosecutors have applied the Racketeer Influenced and Corrupt Organizations Act (RICO) to other cybercriminal enterprises, such as cases involving bulletproof hosting providers, it has not traditionally been used in major public indictments of RaaS operations.
Known RaaS groups and examples
Hive
The Hive ransomware group was an RaaS operation that first appeared in June 2021. It followed a double-extortion model: it both encrypted victims’ systems to disrupt operations and stole sensitive data, threatening to publish it if the victims didn’t pay.
Hive’s affiliates targeted a wide spectrum of organizations, including healthcare, energy, IT, manufacturing, and other critical sectors, across the United States, Europe, and beyond. Between mid-2021 and its takedown, Hive ransomware affected more than 1,500 victims worldwide and generated over $100 million in ransom payments.
LockBit
LockBit is one of the biggest RaaS groups to date. It operates globally, relies on double extortion, and is known for malware designed to spread rapidly across large networks. The group also runs a highly structured affiliate program, with leak sites, negotiation portals, and even bug bounties for affiliates who improve the ransomware.
LockBit was dealt a major blow in early 2024 when an international law enforcement operation seized its infrastructure, exposed internal data, and publicly identified key operators. That action significantly disrupted the group and caused a sharp drop in activity.
REvil
REvil, also known as Sodinokibi, was a major RaaS that first appeared in 2019. It targeted businesses and public-sector organizations worldwide and operated through a structured affiliate-based model.
One of REvil’s most notable campaigns occurred in 2021, when affiliates exploited a supply-chain vulnerability in remote management software to distribute ransomware at scale. The group demanded ransoms in cryptocurrency and was linked to payments totaling hundreds of millions of dollars.
DarkSide
DarkSide operated as a selective RaaS program rather than a broad, high-volume campaign. The group claimed it avoided certain targets, such as hospitals, non-profits, and schools, while focusing on companies that “can afford it.”
The group was blamed for the ransomware attack on Colonial Pipeline. The group later reportedly shut down after it said it had lost access to the public-facing portion of its online system, including its blog and payment server, and that its cryptocurrency funds were transferred to an unknown wallet.
Dharma
Dharma is a ransomware group that started in 2016 and mostly goes after small and medium businesses. Most of its attacks use weak remote access (RDP) to get in. The affiliates typically use simple scripts to turn off antivirus software, steal passwords, move around the network, and lock files. Ransoms are low (around $8,620 on average), but they make money by attacking lots of places.
What are the risks of RaaS?
Successful RaaS attacks create direct business impact, including: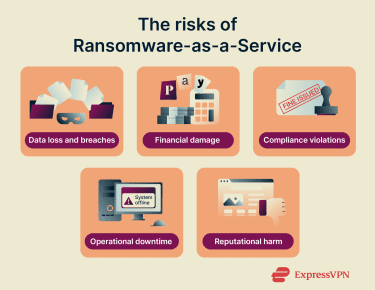
Data loss and breaches
RaaS attacks typically involve data theft as well as encryption. Attackers search for sensitive information and copy it out of the network before locking systems, turning the incident into a data breach. Even if systems are restored, stolen data may still be leaked or sold later, and organizations are often left unsure how much information was taken or misused.
Financial damage
The ransom itself is only one part of the financial damage these attacks can cause. Recovery efforts, system restoration, incident response, and security improvements can significantly increase overall costs. Some organizations also face higher cybersecurity insurance premiums, reduced coverage, or increased scrutiny from insurers following an attack.
Compliance violations
Data breaches tied to ransomware can trigger penalties, especially when personal or sensitive data is exposed. Laws in many regions require organizations to protect customer data and report breaches within strict timeframes. If sensitive information is exposed, regulators may impose fines on top of recovery and remediation costs.
Here are some examples of region-specific laws that protect customer data:
- United States: Data breaches involving personal information can trigger penalties under sector-specific laws such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare data and state breach-notification laws like the California Consumer Privacy Act (CCPA).
- European Union: The General Data Protection Regulation (GDPR) requires organizations to protect personal data and report qualifying breaches within 72 hours; ransomware incidents involving data theft can lead to investigations and fines based on security failures.
- United Kingdom: The UK Data Protection Act 2018 imposes similar rules to the EU framework. Regulators may issue fines or enforcement notices when ransomware exposes personal or sensitive data.
Learn more: Personal data removal laws: Do they protect you?
Operational downtime
RaaS attacks frequently disrupt normal business operations as systems are taken offline for containment and recovery. Downtime can affect critical services, delay business processes, and persist until systems are restored and verified as secure, sometimes lasting days or weeks.
Reputational harm
Public disclosure of a ransomware incident can damage trust with customers, partners, and stakeholders. Reputational impact is often amplified when sensitive or personal data is involved, leading to long-term consequences such as customer churn and strained business relationships.
Cybersecurity challenges posed by RaaS
It’s not always easy to spot, trace, or stop ransomware operations that rely on shared tools and multiple actors. Here are some of the most common cybersecurity challenges posed by RaaS.
- Difficulty in early detection: Affiliates often spend time inside networks using stolen credentials and legitimate administrative tools, making malicious activity blend in with normal IT behavior. Many organizations only discover an attack after encryption or data theft has already occurred.
- Attribution and tracking of threat actors: RaaS groups frequently change names, infrastructure, and hosting providers, making related attacks appear disconnected. Short-lived servers and cryptocurrency payments further complicate efforts to identify operators and disrupt future campaigns.
- Evasion of traditional security tools: RaaS malware is regularly updated to evade signature-based defenses. Attackers also rely on trusted system tools instead of obvious malware files, reducing early warning signals.
- Increasing use of double extortion: Many RaaS campaigns steal data before encryption and threaten public disclosure if victims refuse to pay. This shifts pressure from system recovery to reputational and regulatory risk, even when backups are available.
How to protect your business from RaaS
Effective defenses focus on prevention, early detection, and fast recovery, making ransomware harder to deploy, spread, and profit from.
Regular backups
Regular, well-protected backups help organizations recover quickly if ransomware encrypts their systems, allowing data to be restored without paying a ransom. Backups should run frequently, be stored in locations ransomware can’t easily reach, and include multiple versions in case attackers linger in the network before launching an attack.
Separately, encrypting sensitive data at rest can reduce risk in ransomware incidents that involve data theft prior to encryption. Even if attackers copy files, strong encryption can limit what they are able to read or misuse.
Endpoint protection
Endpoint protection is most effective in detecting early ransomware activity such as credential dumping, abuse of legitimate admin tools, and rapid file-encryption behavior. By identifying these signals on a single compromised device, security teams can isolate endpoints before attackers move laterally or deploy ransomware at scale. Modern endpoint protection platforms monitor processes, file changes, and suspicious activity that often appears before ransomware encrypts data.
Staff awareness training
Many breaches involve human error, like privilege misuse, social engineering, phishing, or stolen credentials. Training staff to recognize suspicious messages and report them early can interrupt attacks before credentials are stolen or malware reaches internal systems. Because attackers continually adapt their tactics, awareness training is most effective when it is ongoing and regularly updated, reinforcing real-world examples that reflect how ransomware is commonly delivered today.
Patch management
Many RaaS attacks begin with the exploitation of known vulnerabilities, particularly in internet-facing systems and outdated software. Affiliates routinely scan for unpatched services because they offer quick, low-effort entry into target environments. Maintaining timely patching across operating systems, applications, and exposed services helps close these common entry points and reduces the likelihood that an initial compromise escalates into a broader ransomware incident.
Threat intelligence
Because RaaS groups reuse infrastructure, tooling, and attack techniques across many affiliates, threat intelligence can be especially effective against ransomware campaigns. By consuming timely, trusted threat intelligence, organizations can proactively block known infrastructure, tune detections, and recognize early signs of campaigns already impacting other victims, which can reduce response time when attacks reach their own environments.
Cybersecurity tools
Security tools help reduce exposure to RaaS attacks and limit damage when something goes wrong. They work best together, not as standalone solutions.
- Antivirus software: Scans files and activity to detect known malware. It helps block common ransomware strains but may miss new or heavily customized attacks that haven’t been seen before.
- Advanced firewalls: Filter network traffic and block connections to known malicious servers. They can stop some attacks at the network level, but it won’t help if attackers log in using valid credentials.
- Endpoint detection and response (EDR): Monitors devices for suspicious behavior like mass file encryption or unusual system changes. It can catch ransomware early, but only if alerts are reviewed and acted on quickly.
- Email security tools: Scan incoming messages for malicious links, attachments, and spoofed senders. They reduce phishing risk, but some scams still reach inboxes and rely on human error to succeed.
- Virtual private network (VPN): Corporate and commercial VPNs play a limited supporting role by protecting credentials and traffic when employees work on untrusted networks. While they don’t prevent phishing or ransomware infections, they can reduce the risk of credential interception that might later be used in an RaaS intrusion.
FAQ: Common questions about Ransomware-as-a-Service
What is a RaaS attack?
A Ransomware-as-a-Service (RaaS) attack is a ransomware incident that involves several groups of bad actors: developers who created the malware, operators who sold it, and affiliates who carried out the attack and deployed it.
Who uses RaaS platforms?
Ransomware-as-a-Service (RaaS) platforms are mainly used by RaaS affiliates. These are attackers who focus on breaking into networks and deploying ransomware.
Can RaaS be prevented?
How effectively you can prevent Ransomware-as-a-Service (RaaS) attacks depends on several factors. This includes how well your systems are maintained, how quickly weaknesses are fixed, and how prepared people and processes are to respond when something goes wrong. While ransomware can’t be stopped entirely, practical steps like solid backups, timely patching, endpoint protection, staff awareness, and threat intelligence can reduce the chances of a serious disruption and make recovery far less painful.
Is it safe to pay the ransom?
The FBI and Cybersecurity and Infrastructure Security Agency (CISA) say victims are strongly discouraged from paying, because payment can encourage more attacks and doesn’t guarantee recovery. Even if a ransom is paid, data may not be fully restored, and stolen information can still be leaked or reused.
Can RaaS attacks be detected early?
Early detection is difficult because attackers often use stolen credentials and legitimate system tools that blend in with normal activity. Many organizations only realize they’ve been compromised once data is stolen or systems are encrypted. Behavior-based monitoring and threat intelligence can improve visibility, but early detection isn’t always possible.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN