What is cryptojacking? How to detect & prevent hidden crypto mining


Cryptojacking is when hackers run cryptomining malware on your device without you knowing. This lets them secretly mine cryptocurrency without your knowledge or consent. Unlike other types of malware, the goal isn’t to spy on you, steal your data, or hack your accounts.
Cyber sleuths use your device’s power to mine cryptocurrency—making you pay the energy costs while they make money. Crypto mining uses a lot of power, which is costly. Research from Cambridge found that mining Bitcoin uses more energy than some entire countries. Cryptojackers get victims to pay the running costs by illicitly installing crypto mining code on their computers.
Victims of cryptojacking get saddled with all the costs—high electricity bills and computer performance issues—without reaping any reward. When the cryptocurrency is mined, it goes straight to the hacker's wallet.
In this article, we cover everything you should know about cryptojacking, how it works, and how to prevent it from happening to you. You’ll also find out how to detect cryptojacking malware on your device.
Using a VPN with advanced security features like ad-blocking and IP masking helps you reduce the risk of cryptojacking. When you use it with a strong anti-malware program, you’re less likely to fall victim to this nefarious cybercrime. ExpressVPN’s ad blocker makes browsing the web safer.
How does cryptojacking work?
Cryptojacking is a type of cyberattack where hackers secretly use your computer, mobile device, or cloud resources to mine cryptocurrency. They embed crypto mining scripts onto your device, forcing it to perform mining processes in the background. This leads to poor performance, high CPU usage, and even system crashes.
Cryptojacking can happen in different ways, from browser-based attacks to network intrusions. It often goes undetected for long periods, making it highly unlikely the criminals will be caught. Cryptojacking can take different forms. Here are two of the most common ways hackers use your device for mining:
In-browser cryptojacking
In-browser cryptojacking is when a hacker embeds malicious JavaScript code into a website. When you visit the site, the script runs automatically, using your CPU power to mine cryptocurrency. This method was once popular with services like Coinhive, which lets websites monetize traffic through browser-based cryptomining.
While most browsers try to block these scripts, some attackers find ways to inject malicious crypto mining code into compromised sites. In-browser cryptojacking relies on you visiting infected websites and keeping your browser open.
In-host cryptojacking
This type of attack often spreads through phishing emails, trojans, or fake software updates. Once inside, the malicious code runs in the background, hijacking CPU or GPU resources to mine coins like Monero (XMR)—a cryptocurrency favored by hackers. They prefer Monero because it’s easier to mine on regular computers and keeps them anonymous.
Some attacks use fileless malware, which makes detection even harder. Over time, the infected system shows poor performance, overheating, and crashes. The complex calculations needed to mine crypto push the device to maximum capacity.
Common cryptojacking attack methods
Beyond in-browser and in-host cryptojacking, hackers have other ways to get mining scripts onto devices and networks. Some methods rely on tricking users, while others take advantage of security flaws. Here are some of the most common cryptojacking attack methods:
Drive-by cryptojacking
Drive-by cryptojacking happens when hackers plant hidden mining scripts inside a website or use drive-by downloads to install malware on a visitor’s device. In some cases—like in-browser cryptojacking—the mining only runs while the user is on the infected page. But drive-by cryptojacking can also involve malware that stays on the device, continuing to mine even after the person leaves the site.
Cloud cryptojacking attacks
Cloud cryptojacking happens when hackers hijack cloud servers to mine cryptocurrency on a large scale. Unlike attacks on personal computers, cloud cryptojacking takes advantage of high-performance cloud computing power, allowing criminals to mine more efficiently. Some attacks involve stolen credentials, while others exploit vulnerabilities in cloud software or services. One common sign of cloud cryptojacking is a sudden spike in CPU usage or unexpected cloud billing increases.
Network-based cryptojacking
Some cryptojackers attack entire networks instead of just one device, letting them use the power of many machines at once. They infect servers, endpoints, or IoT devices and spread malicious cryptomining through network traffic.
When attacks use fileless malware, it hides in RAM instead of saved files. This makes detecting and removing it quite tough. Since hackers try to stay hidden, real-time network monitoring is key if you want to spot unusual CPU usage or unauthorized mining activity.
In memory jacking
Malicious cryptojacking code runs in a computer’s RAM instead of being saved as a file. This makes it hard for antivirus programs to detect. Hackers spread it through phishing emails, software bugs, or infected websites. This lets them quietly use the CPU or GPU for cryptocurrency mining.
Since the malware disappears when the system restarts, attackers often find ways to reinfect the device. To stay safe, users should keep software updated, use real-time monitoring, and watch for signs like high CPU usage or a slow computer.
Malicious ads & hidden scripts
Some cryptojacking attacks come through online ads—a tactic called malvertising. Hackers put crypto mining code into advertisements that appear on legitimate websites. Even if a site isn’t infected, an ad on the page could secretly mine crypto in the background—using your computer’s juice.
Hackers also hide scripts inside infected software downloads or browser extensions, making them harder to detect. The scripts can continue mining until you close the browser or remove the infected software. To reduce risk, get an ad blocker and use cryptojacking protection extensions.
Social engineering & phishing for cryptojacking
Phishing emails and social engineering can trick you into installing crypto malware. Hackers send deceptive messages containing dangerous links, fake software updates, or email attachments that run mining scripts when you open them.
Once installed, the malware operates in the background, using your resources to mine digital money. Many victims don’t realize something is wrong until their device slows down or their electricity bill rises. Both of these things happening at the same time is not a good sign.
Never click suspicious links and always double-check email senders before opening attachments. Also, don’t download software from untrusted sources.
Exploiting cloud services & misconfigured servers
Many cloud cryptojacking attacks succeed because of weak security settings. Hackers often target misconfigured servers that leave open ports, use default passwords, or run outdated software. These small mistakes can give attackers the access they need to install mining scripts. Organizations that rely on cloud services should regularly audit security settings, monitor resource usage, and enforce strict access controls to prevent cryptojacking.
Examples of real-world cryptojacking incidents
Hackers take advantage of security gaps to mine cryptocurrency without being noticed. And they’re not just targeting individuals—businesses, cloud services, and even major tech platforms have been hit. Here are some real-world examples of cryptojacking in action:
- Atlassian Confluence servers targeted. In mid-2024, Trend Micro discovered that threat actors exploited a vulnerability in the Atlassian Confluence Data Center and Server. Attackers used cryptojacking malware to download and execute XMRig miners for illicit cryptomining.
- Ukrainian cryptojacker arrest. In January 2024, Ukrainian police (aided by Europol) made a high-profile cryptojacker arrest. Authorities believe they illicitly mined $2 million worth of cryptocurrencies. This shows growing law enforcement efforts against cryptojacking.
- Record-breaking cryptojacking surge. In 2023, cryptojacking incidents reached an all-time high. SonicWall reported a 399% increase, totaling 332.3 million attacks in the first half of 2023. This surge shows a steep rise in cryptojacking activity.
- GitHub cryptojacking attack. Hackers misused GitHub’s servers to run illegal mining. They created fake projects to exploit GitHub’s automation tools and secretly mine crypto. This attack showed how hackers can hijack vulnerable cloud resources.
- Linux and IoT cryptojacking malware. Microsoft found cryptojacking malware targeting Linux users and IoT devices. The malware infected endpoints and forced them to mine Monero (XMR) without consent. Since IoT devices often lack strong security, hackers can easily get control of them.
How to detect cryptojacking on your device & network
Cryptojacking often runs silently in the background, which makes it hard to spot. But certain red flags can signal that malicious crypto mining is happening on your computer or network.
Here’s what to look out for:
1. High CPU usage & overheating
One of the biggest red flags of cryptojacking is high CPU usage when no heavy programs are running. You may notice your fan running loudly, your computer overheating, or your performance slowing down.
You can check your task manager (Windows) or Activity Monitor (Mac) to see if unknown processes are consuming excessive CPU power.
- For Mac users, simply navigate to Launchpad > Activity Monitor > CPU.
- On Windows, open up Task Manager > Processes > CPU.
A CPU running at normal levels should look something like this:
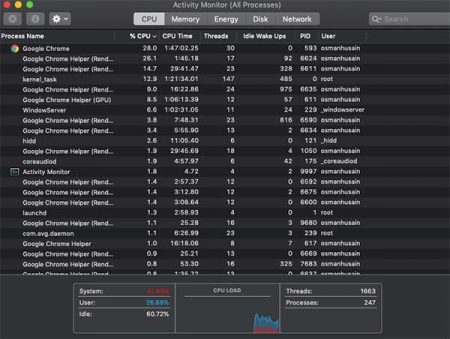
If your system usage is at a high percentage despite minimal use of programs and apps, you may be a victim of a cryptojacking scheme.
2. Increased electricity consumption
Since cryptocurrency mining needs constant processing power, infected systems consume more electricity than normal. If you notice unexplained spikes in your electricity bill, you could have cryptojacking malware on your desktop or network.
3. Poor system and network performance
Cryptojacking drains CPU, GPU, and network resources. This causes slow computers, lagging apps, and sluggish internet. If your browser freezes, web pages take longer to load, or your network struggles with high traffic, it could be due to illicit crypto mining.
4. Suspicious browser activity & unknown processes
If your device slows down a lot on certain sites or your browser stays active after you close it, the reason could be crypto mining or other malware. Check your task manager for processes you don’t recognize running in the background.
Tools to scan and detect cryptojacking scripts
To protect your devices and network, use cybersecurity tools capable of detecting cryptojacking malware in real time.
Some recommended solutions include:
- Task Manager / Activity Monitor. Check for high CPU usage from unknown programs.
- Network monitoring tools. Identify unusual network traffic spikes or resource usage.
- Anti-malware software. Programs like Malwarebytes and Windows Defender can detect cryptojacking scripts.
- Cryptojacking browser extensions. Tools like No Coin and MinerBlock can block malicious JavaScript on websites.
- Endpoint detection & response (EDR) solutions. Enterprise-level tools that use machine learning to flag unauthorized mining processes.
Read more: How to check if your computer has a virus
How to prevent cryptojacking attacks
Since cryptojacking can be difficult to detect and remove, it’s best to avoid letting it happen in the first place. Here are some preventative steps to lower your chances of getting infected with crypto mining malware—and malware in general.
1. Secure your browser
Many cryptojacking attacks start right in your browser and you may not even realize it’s happening. To stay safe:
- Turn off JavaScript on websites you don’t trust to block hidden mining scripts.
- Use a privacy-focused browser like Brave—some automatically block cryptojacking attempts.
- Clear your browser cache often to get rid of lingering malicious code.
- Be cautious with pop-ups and sketchy ads—some may launch crypto mining scripts in the background.
Read more: Private browser: Your best options for online privacy
2. Harden your network and router security
Hackers don’t just target individual devices—they go after entire networks. If they gain access to your router or Wi-Fi, they can spread malicious crypto mining across multiple connected devices. Protect yourself by:
- Change your router’s default password to something strong and unique.
- Enable WPA3 encryption on your Wi-Fi network to block unauthorized access.
- Use network monitoring tools to catch unusual traffic spikes— they could mean
someone is secretly mining on your network. - Set up a firewall to block connections to known cryptojacking servers.
3. Implement cloud and server security best practices
Cryptojackers love targeting cloud infrastructure because they can mine cryptocurrency at scale without paying for electricity. If you're running cloud-based services or managing servers, be extra cautious:
- Use strong passwords and multi-factor authentication (MFA) to prevent unauthorized logins.
- Monitor CPU and resource usage.
- Regularly check server logs for suspicious activity like unknown processes or file changes.
- Limit permissions so only you or other authorized people can install software or change system settings.
4. Use anti-cryptojacking browser extensions
Some cryptojacking scripts don’t require malware downloads—they just run in your browser when you visit infected sites. It can help to install browser extensions to prevent scripts from hijacking your CPU power.
5. Train employees & IT teams on cryptojacking threats
Many cryptojacking attacks start when someone clicks a bad link or accidentally downloads malware. Teaching employees and IT teams how to spot red flags can prevent attacks before they happen:
- Show employees how to recognize phishing emails that could contain malicious cryptojacking scripts.
- Warn people to only download from trusted sources to avoid infected systems.
- IT teams should regularly check for high CPU usage, slow performance, and unknown mining processes on company devices.
- Run cybersecurity awareness training so everyone stays up to date on cryptojacking threats.
6. Keep software, firmware, and OS updated
Hackers can exploit security holes in outdated software, operating systems, and firmware to install cryptojacking malware. It’s important to keep everything updated to block them.
- Enable automatic updates for your OS, antivirus, and browsers to patch security gaps before hackers can exploit them.
- Keep your router firmware updated to close vulnerabilities hackers could use to access your network.
- Regularly update cloud-based services to protect against supply chain attacks.
- Use endpoint detection tools that use machine learning to catch unusual CPU spikes and unauthorized mining processes.
Is cryptojacking a serious cybersecurity risk?
Yes, cryptojacking is a real threat, and anyone who uses the internet can be a target—not just crypto traders. Some businesses have faced huge losses. For example, the U.S. Agency for International Development (USAID) lost about 500,000 USD in cloud fees due to cryptojacking.
Just visiting a compromised website can start mining in the background without you noticing. Cloud servers are attractive to attackers as they offer massive computing power—which leads to bigger profits. It’s a low-risk, high-reward crime as it lets hackers mine cryptocurrency for free while victims pay the price.
FAQ: About cryptojacking
Is cryptojacking illegal?
What is the meaning of cryptojacking?
Why do hackers use cryptojacking?
Can antivirus software detect cryptojacking?
What are the methods of cryptojacking?
- Hiding scripts on websites that start mining when you visit.
- Embedding cryptojacking code in online ads.
- Tricking people into downloading fake software or clicking on phishing emails.
- Breaking into cloud accounts with weak security settings.
- Installing infected browser extensions or apps that mine in the background.
How do you detect cryptojacking?
- Your computer is slower than usual or crashes often.
- Your fan is running loudly even when you're not doing much.
- Your electricity bill is unexpectedly high.
- Your browser lags or stays open longer than normal.
- Your task manager shows high CPU usage from unknown programs.
How can I protect my business from cryptojacking?
- Use cybersecurity tools that detect unauthorized mining.
- Monitor networks for unusual CPU usage.
- Train employees to recognize phishing emails and suspicious downloads.
- Keep software and servers updated to patch security weaknesses.
- Install browser extensions that block cryptojacking scripts.
- Secure cloud accounts with strong passwords and multi-factor authentication.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN



