Twofish encryption: What it is and why it matters
Twofish is a secure, efficient, and flexible block cipher created for the Advanced Encryption Standard (AES) competition run by the U.S. National Institute of Standards and Technology (NIST) in the late 1990s. Although it didn’t win the competition, it remains a reputable cipher. This article explains what exactly Twofish is, how it works, and how it compares to other popular ciphers.
What is Twofish encryption?
Twofish is a symmetric encryption algorithm that protects data using a shared secret key. It’s also an open algorithm, meaning anyone can freely implement, test, and analyze it without licensing restrictions.
Developed in the late 1990s by Bruce Schneier and his team at Counterpane Labs, Twofish builds on ideas from Blowfish, Schneier’s earlier block cipher, but was redesigned to meet the stringent technical and security requirements of the AES selection process.
It was one of five AES finalists in the competition because of its strong security model and good performance across both software and hardware environments. It ultimately lost to Rijndael, which is now known as AES encryption.
Key design principles of the Twofish algorithm
Twofish was designed to make encrypted data difficult to analyze or predict, even if an attacker studies large amounts of encrypted information. To achieve this, the algorithm mixes data thoroughly during encryption so that even small changes in the input data or the encryption key produce completely different encrypted results. This makes it harder for attackers to identify patterns they could exploit.
Twofish also changes how it encrypts data based on the key being used. In practice, this means the algorithm doesn’t follow the exact same internal behavior for every key, which limits an attacker’s ability to reuse the same attack techniques across different keys.
In addition to security, Twofish was built to work efficiently across different environments, giving developers flexibility to use it in a wide range of systems without sacrificing security.
Key features of the Twofish algorithm
Twofish includes several defining features that shape how the algorithm operates and where it can be used.
- 128-bit block size: Twofish encrypts data in fixed-size blocks of 128 bits, which helps reduce predictable patterns in encrypted output.
- Flexible key lengths: The algorithm supports key sizes of 128, 192, and 256 bits, allowing different trade-offs between performance and resistance to brute-force attacks.
- Feistel-based structure: Twofish uses a Feistel network, a common and well-studied encryption structure that processes data by repeatedly splitting and recombining it.
- Whitening: Twofish mixes key material into the data before and after the main encryption rounds.
- Structured key schedule: Twofish derives multiple subkeys from the main encryption key so that different parts of the algorithm use different key material.
How Twofish works
Twofish encrypts data by transforming it through a sequence of key-controlled operations that remove patterns and obscure relationships in the original information. Before encryption begins, Twofish prepares the encryption key: it expands the main key into multiple subkeys and generates key-dependent substitution tables, known as S-boxes. These tables replace parts of the data with different values during encryption.
Encryption starts with input whitening, where key material is mixed into the data immediately. This step helps hide simple relationships between the original data and the encrypted output from the very beginning.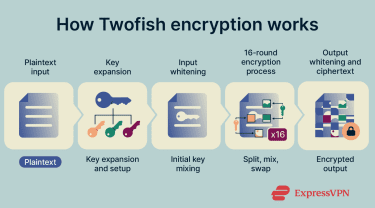
The data then moves through a 16-round Feistel structure. In each round, Twofish splits the data into two halves. One half is transformed using substitutions and mathematical mixing, then combined with the other half before the halves swap roles. As this process repeats, small changes in the input or key spread throughout the entire block, producing a very different result.
After the final round, output whitening applies another layer of key mixing. This further obscures the encrypted data and adds protection against attacks that target the start or end of the encryption process. To decrypt the data, Twofish performs the same steps in reverse order using the same key, which allows authorized users to recover the original information.
Benefits of Twofish encryption
Twofish offers several practical benefits that make it a reliable encryption option in scenarios where flexibility, transparency, and long-term security are important.
Strong security against analysis
Twofish was designed to resist advanced cryptanalytic attacks, including differential cryptanalysis, a technique where attackers study how tiny changes in the input affect the encrypted output. Its conservative design and lack of known practical attacks have contributed to its long-standing reputation as a secure block cipher.
Flexible key sizes and design
The algorithm’s support for multiple key lengths gives developers freedom to choose what fits their situation best. Shorter keys can reduce computational overhead in environments where speed or resource constraints matter, while longer keys increase resistance to brute-force attacks in higher-security contexts.
Because this flexibility is built into the algorithm’s design rather than added later, organizations can adjust security strength without changing how Twofish operates or how it is implemented. This makes it easier to deploy the algorithm consistently across systems with different requirements while maintaining a predictable security model.
Predictable and stable long-term use
Twofish follows a fixed and fully defined specification, meaning the algorithm’s structure and behavior don’t change over time. This reduces the risk of unexpected behavior due to specification changes or shifts in security assumptions, making it easy to maintain for organizations protecting data over long periods.
Openly available and royalty-free
Twofish is openly available and free to use, with no patents or licensing barriers, making it easy for developers to build it into security software. Because the full design is public, cryptographers can freely examine how the algorithm behaves and test its security assumptions, which helps build long-term confidence in the algorithm’s reliability.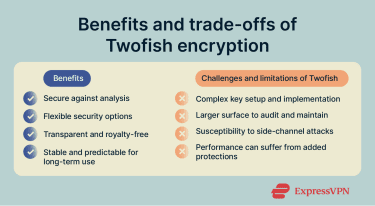
Challenges and limitations of Twofish
Twofish is a solid encryption algorithm, but like any technology, it has some drawbacks:
Complex key setup and implementation
Twofish requires additional setup before encryption can begin, which increases the effort needed to implement and test the algorithm correctly. Plus, because Twofish changes how it operates based on the encryption key, developers must ensure that all key-derived components are generated and applied correctly. Any mistake in this process can alter the algorithm’s behavior, making errors harder to detect and increasing the risk of flawed implementations.
Larger surface to audit and maintain
Twofish combines several moving parts. While each component is well defined, the overall design requires more code and logic than simpler ciphers, which makes auditing, debugging, and long-term maintenance more demanding.
Susceptibility to side-channel attacks
Like many block ciphers, Twofish uses basic mathematical operations, such as addition and table lookups, which can make some implementations more vulnerable to side-channel attacks. These attacks don’t break the encryption mathematically, but instead extract information by measuring characteristics like execution timing or power consumption on physical devices, such as smart cards or embedded systems.
Performance trade-offs from added protections
Defending against side-channel attacks can introduce performance trade-offs. Protective techniques like masking may slow down encryption and increase memory usage, sometimes requiring hundreds of additional bytes of RAM. As a result, performance may drop compared to simpler designs or algorithms with more built-in resistance to these attack vectors.
Where Twofish is used in practice
Twofish is in use today, but it’s almost never the default encryption algorithm. It is primarily offered as an optional cipher, not a system default, including in:
- Disk and file encryption tools: Some full-disk encryption software give you the option to manually select Twofish when creating encrypted drives or volumes.
- Password vault software: Certain password managers support Twofish for encrypting vault databases.
- Cryptographic libraries: Developer-focused crypto libraries include Twofish as an available block cipher for custom applications that require an alternative to AES.
- OpenPGP implementations: OpenPGP, the open standard behind Pretty Good Privacy (PGP)-encrypted email and file exchange, lists Twofish as a supported symmetric cipher for encrypting emails or files.
Learn more: What are encryption protocols and how do they work?
Comparing Twofish to other encryption algorithms
To understand where Twofish stands today, it’s useful to compare it with other widely used encryption algorithms.
Twofish vs. Blowfish
Twofish is essentially the modern upgrade of Blowfish. Blowfish encrypts data using a 64-bit block size, which limits how much data can be safely encrypted under a single key. When large volumes of data are involved, this increases the risk of pattern-based attacks. Twofish addresses this limitation by using a 128-bit block size and supporting stronger key options. For current applications, Twofish is generally considered the safer choice: even Schneier has advised moving away from Blowfish toward more modern ciphers.
Twofish vs. AES
AES is the dominant encryption standard today and is widely used in virtual private networks (VPNs), operating systems, and secure communications. Its main advantage is performance: modern processors include dedicated hardware acceleration (AES-NI), which makes AES significantly faster and more energy-efficient.
Twofish offers strong security and greater flexibility in software-only environments, but it lacks widespread hardware acceleration and is more complex to implement. That said, Twofish maintains a strong security margin and remains a secure alternative in scenarios where hardware acceleration is unavailable or algorithm choice flexibility is required.
Performance considerations: Twofish, Blowfish, and AES
Here’s an overview of some key performance indicators of all three encryption algorithms.
| AES | Twofish | Blowfish | |
| Block size | 128 bits | 128 bits | 64 bits |
| Key sizes | 128, 192, 256 bits | Up to 256 bits | 32-448 bits |
| Speed on modern hardware | Fastest | Good in software, slower than AES without hardware support | Can be fast in software |
| Battery usage | Low | Moderate | Low-to-moderate |
| VPN use | The best standard for VPNs | Not typical, possible in rare niche setups | No |
| Safety margin | High | Very high | Lowest |
How to avoid typical Twofish encryption pitfalls
Using Twofish securely depends less on the algorithm itself and more on how it’s implemented and integrated into a broader encryption system. Most real-world issues come from configuration or implementation mistakes rather than weaknesses in the cipher. Here are the best practices to follow: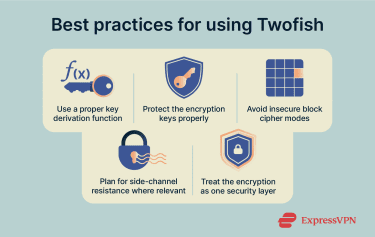
- Use a proper key derivation function (KDF): When you encrypt data with Twofish using a password, derive the encryption key with a KDF such as PBKDF2 or Argon2 to slow down brute-force attacks.
- Protect encryption keys properly: Store Twofish encryption keys in secure systems such as key vaults or hardware security modules and never embed them directly in application code. Anyone who gains access to the key can decrypt the data, regardless of how strong the algorithm is.
- Avoid insecure block cipher modes: Always pair Twofish with a secure mode of operation and avoid the Electronic Codebook (ECB) mode, which exposes data patterns.
- Avoid custom implementations: Twofish is complex to set up. Writing your own implementation increases the risk of subtle errors that weaken security.
- Plan for side-channel resistance where relevant: In hardware, embedded, or high-assurance environments, you should apply constant-time operations or masking techniques to protect Twofish implementations against timing and power-analysis attacks.
- Treat encryption as one security layer: Use Twofish alongside strong authentication, access controls, and monitoring. Encryption protects data confidentiality, but it can’t prevent misuse or key exposure on its own.
Twofish and VPNs: Is it used today?
Twofish sees limited use in VPNs nowadays. The gold encryption standard today is AES for nearly all major commercial providers, because of its security, speed, and hardware support. Today, the most common ciphers in VPNs include:
- AES-256-GCM: The top choice for most providers using OpenVPN or Internet Key Exchange version 2 (IKEv2). It’s fast with hardware acceleration and has strong security.
- AES-128-GCM: A lighter version of AES in Galois/Counter Mode (AES-GCM), often used for better performance on lower-power devices.
- ChaCha20-Poly1305: Popular in WireGuard and some OpenVPN setups. It has great speed on mobiles and devices without AES hardware support.
ExpressVPN defaults to AES-256-GCM on most devices but has ChaCha20-Poly1305 as a faster alternative for phones. This gives you top-level security without slowing down your connection.
OpenVPN, the popular open-source protocol, still supports Twofish technically. Some niche or self-hosted OpenVPN setups might enable Twofish for its strong security margin. However, modern configurations and providers have largely dropped it in favor of other ciphers.
FAQ: Common questions about Twofish encryption
Is Twofish more secure than AES?
Twofish and Advanced Encryption Standard (AES) are both secure. The main difference between them is that AES is faster and better at preserving energy (or your battery).
What are the disadvantages of Twofish?
Twofish’s main disadvantages include its complex key setup and implementation. It’s also susceptible to side-channel attacks, and its performance can suffer in environments that require adding protections, such as masking.
Is Twofish still used today?
Yes, but more as an optional encryption cipher, not the standard. You can find Twofish as an option in some password managers, file encryption tools, OpenPGP implementations, and cryptographic research.
What is the “hardest” encryption to crack?
There isn’t a single “hardest” encryption algorithm. Real-world security depends on the algorithm, key size, implementation quality, and threat model. Well-implemented ciphers like Advanced Encryption Standard (AES) and Twofish are both considered practically unbreakable with current computing capabilities.
Can Twofish handle high volumes of data?
Yes. Twofish uses a 128-bit block size, which allows it to safely encrypt large volumes of data without repeating patterns too quickly. This reduces the risk of block collisions, a known issue with older 64-bit ciphers like Blowfish when encrypting lots of information. As a result, Twofish is suitable for tasks like file encryption, backups, and secure storage where large datasets are involved.
What key sizes does Twofish support?
Twofish supports variable-length keys up to 256 bits. Most uses employ 128-bit, 192-bit, or 256-bit keys. Shorter keys offer better performance, while longer keys provide stronger protection against brute-force attacks. This flexibility lets developers choose a key size that fits their security needs without changing the encryption algorithm itself.
How does Twofish perform on mobile or low-power devices?
Twofish runs well in software but is generally slower than Advanced Encryption Standard (AES) on modern and mobile devices. That’s because it lacks hardware acceleration, which AES has and delivers better speed and battery efficiency as a result. This is why AES is preferred for VPNs and mobile-heavy use cases.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN