Reconnaissance in cybersecurity: Everything you need to know

Reconnaissance in cybersecurity plays a dual role. Attackers use it to gather intelligence and prepare attacks, while security teams use it to understand their exposure and strengthen defenses.
In this article, we’ll explain what reconnaissance involves, how attackers use it, and how security teams can leverage it to identify security vulnerabilities and fix them before attackers can exploit them.
What is cybersecurity reconnaissance?
Reconnaissance in cybersecurity is the process of collecting information about systems, networks, and organizations to understand what assets are visible from outside and how they can be reached. It specifically focuses on identifying internet-facing resources, mapping how they are configured, and observing how they respond to external interaction.
Understanding the purpose of reconnaissance
The purpose of reconnaissance is to develop a clear understanding of an environment before taking further action. It’s commonly used to:
- Identify security weaknesses: Reveals exposed services, misconfigurations, and unpatched vulnerabilities that may introduce risk.
- Understand network and system structure: Provides visibility into how systems, applications, and devices are connected, including how data flows between them.
- Guide next steps: Helps determine which actions are most appropriate based on current exposure.
How does reconnaissance fit into cybersecurity?
In cybersecurity, reconnaissance is the first step of the Cyber Kill Chain, a framework developed by Lockheed Martin that describes how cyberattacks occur in stages. This stage covers information gathering about a potential victim’s assets that are visible from outside an organization.
From an attacker’s point of view, reconnaissance is about learning how a target works before attempting to break in. Attackers collect information about systems, users, and exposed services to plan how they will gain access while avoiding detection. This information may include technical details such as open ports, software versions, and network structure, as well as contextual data like employee names or email addresses.
From a defensive standpoint, reconnaissance helps security teams assess their attack surface. This includes reviewing publicly available information, scanning internet-facing assets such as websites and IP addresses, and identifying exposed or misconfigured services. Finding these issues early allows teams to fix them before attackers can take advantage.
Types of cyber reconnaissance
Cyber reconnaissance generally falls into two categories based on how information is gathered: passive reconnaissance and active reconnaissance. The key difference is whether information is collected indirectly or by directly contacting the target’s systems.
Passive reconnaissance
Passive reconnaissance involves collecting information without making direct contact with the target’s systems. Both attackers and security teams use it at the very beginning of an assessment to establish an initial view of exposure before moving on to more direct methods.
Common passive reconnaissance techniques include:
- Reviewing publicly available Domain Name System (DNS) records to identify domains and subdomains.
- Analyzing WHOIS records to obtain domain registration and ownership details.
- Collecting information from company websites, job postings, documentation, and public repositories.
- Gathering data from social media platforms, forums, and breach databases.
- Examining metadata from publicly accessible files and resources.
Because passive reconnaissance doesn’t involve sending traffic to the target’s systems, it’s less likely to generate logs or trigger security alerts. As a result, it is difficult to detect using traditional network monitoring tools.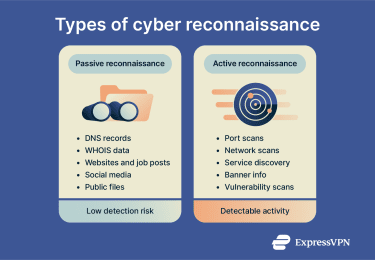
Active reconnaissance
Active reconnaissance involves direct interaction with a target’s systems in order to gather information. In the Cyber Kill Chain, it often follows passive reconnaissance by providing more precise and technical detail.
Common active reconnaissance techniques include:
- Port scanning to identify open ports and exposed services.
- Network scanning to discover live hosts and network structure.
- Service enumeration to determine software types and versions.
- Banner grabbing to extract identifying information from running services.
- Vulnerability scanning to detect known security weaknesses.
Because active reconnaissance generates traffic toward the target environment, it’s more likely to be logged or flagged by security controls such as firewalls, intrusion detection systems (IDS), or intrusion prevention systems (IPS). These activities often leave detectable traces in network and system logs.
Four core methods of reconnaissance
Both attackers and security researchers and teams use various tools and methods for reconnaissance. Here are the four core methods used during the process.
Open-source intelligence (OSINT)
Type of reconnaissance: Passive
Open-source intelligence (OSINT) is a reconnaissance method that involves collecting and analyzing information from publicly available sources. OSINT sources include any data that an organization, its employees, or third parties have made publicly accessible, either deliberately or inadvertently.
Here are common open sources used during OSINT analysis:
Website and blogs
Public websites and blogs often contain a wide range of information, including business reports, security announcements, technical documentation, and organizational updates. Public records such as government filings, court documents, registration databases, and regulatory disclosures can also reveal details about legal issues, ownership, or administrative activity.
Together, these sources help build an understanding of how an organization operates and presents itself publicly.
Social media platforms
Social media OSINT, sometimes referred to as SOCMINT, involves analyzing information shared on platforms such as LinkedIn, Facebook, Instagram, and X (formerly Twitter). These platforms can reveal professional roles, organizational structure, relationships, and behavioral patterns.
Information gathered from social media often provides context that cannot be obtained through technical analysis alone.
WHOIS lookups
WHOIS is a public directory system that stores information about domain name registrations. When someone registers a domain name, basic details about that registration are recorded in a WHOIS database.
In cybersecurity reconnaissance, WHOIS data helps identify who owns or manages a domain, how long it has been active, and whether multiple domains may be linked through shared registration details. This information can be useful for mapping related infrastructure or identifying patterns across domains.
DNS enumeration
DNS enumeration is a technique that involves querying publicly accessible DNS infrastructure to discover how a domain is set up and what services it supports. These records describe where traffic is routed and which services are in use. This helps build a clearer picture of an organization’s external infrastructure and the services it exposes to the internet.
Network mapping and port scanning
Type of reconnaissance: Active
Network mapping is a process of discovering and documenting the systems, devices, and services that make up a network and how they are connected. In reconnaissance, network mapping works by sending controlled requests to a network and observing which systems respond and how.
Port scanning is commonly used alongside network mapping to provide insight into a system’s function and risk profiles. Because services communicate through specific ports, scanning reveals which services are reachable and where closer security review may be needed.
Together, network mapping and port scanning provide visibility into:
- Which hosts and devices are reachable.
- How systems are grouped or segmented.
- Which services are exposed on which systems.
- How systems communicate with each other.
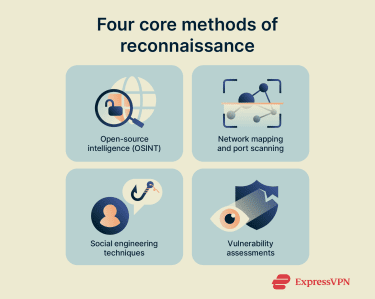
Social engineering techniques
Type of reconnaissance: Both passive and active
Social engineering involves gathering information by interacting with people rather than systems.
Attackers use social engineering to gather information by manipulating human interaction and learn details such as internal procedures, access patterns, communication norms, and trust relationships. Security teams use controlled social engineering to test awareness, policies, and response before those weaknesses are exploited.
Common social engineering techniques include:
- Phishing: Email-based communication designed to prompt recipients to take an action, such as clicking a link or providing information.
- Smishing: Similar to phishing, but conducted through SMS or mobile messaging platforms.
- Vishing: Voice-based interaction, typically involving phone calls, where conversation is used to elicit information.
Vulnerability assessments
Type of reconnaissance: Active
Vulnerability assessment is a method used to identify weaknesses in systems, applications, and configurations that could be exploited. A typical vulnerability assessment process includes:
- Scanning systems and services to detect known vulnerabilities and insecure configurations.
- Identifying affected assets and software components.
- Mapping findings to Common Vulnerabilities and Exposures (CVE) identifiers when applicable.
- Evaluating potential impact and exploitability based on exposure and context.
- Prioritizing vulnerabilities according to severity and risk.
Real-world examples of reconnaissance in security incidents
Reconnaissance has played a major role in some of the biggest hacks in the cybersecurity space. In each case, reconnaissance did not cause the breach by itself. It provided information that made subsequent exploitation easier when security gaps were present. Here are some examples:
- Third-party vendor reconnaissance before a major retail breach: Attackers who broke into a major U.S. retailer were reportedly able to gain access by first compromising a third-party vendor with network connectivity to the company, then using that foothold to access internal systems.
- Internet-wide vulnerability scanning prior to data compromise: Investigations into a major credit reporting agency breach found that attackers scanned public-facing web servers for a known vulnerability in widely used web application software. After identifying an unpatched system, they exploited the flaw and maintained access for an extended period, exposing sensitive personal data.
- Organizational profiling prior to destructive corporate attack: Analyses of a high-profile entertainment industry breach indicate that attackers conducted extensive reconnaissance on corporate structure, employee roles, and internal systems before deploying malware and leaking data.
- Social engineering reconnaissance before account takeovers: In an incident involving a large social media company, attackers reportedly researched internal roles and help-desk processes before conducting phone-based social engineering. By understanding internal tools and identifying employees with privileged access, they were able to take over high-profile accounts and promote fraudulent cryptocurrency schemes.
Best practices for strengthening cybersecurity against reconnaissance
Defending against reconnaissance involves reducing visibility, limiting exposure, and detecting early signals.
Reduce the attack surface
Reducing the attack surface limits how much information reconnaissance can uncover in the first place. Any system, service, or interface exposed to the internet becomes a potential source of intelligence.
Start with an external-facing inventory: List every public domain and subdomain, public IP, and internet-exposed service your organization runs, then validate that each one is still required.
Once you have the list, take the “default closed” approach: Shut down unused services, close unused ports, and limit what remains exposed to only what’s necessary for business operation. You can then build this into a repeatable program that revisits the external inventory regularly as part of your risk management process.
Limit publicly available information
A significant portion of reconnaissance relies on information that organizations publish unintentionally, including domain and DNS data.
To protect your domain, most domain registrars offer a domain privacy or WHOIS privacy option that can be enabled in the registrar’s management console when registering a domain or updated later through the domain’s settings. When turned on, the registrar replaces the registrant’s personal or organizational details in public WHOIS records with proxy information.
DNS configuration is another common source of information leakage. Using Split Horizon DNS (also called split-brain DNS) allows organizations to keep internal DNS records separate from public records. With this configuration, DNS queries from internal IP addresses and private hosts return internal records, while queries from external or public sources receive only minimal public DNS data. This prevents internal hostnames, services, and network structure from being exposed through DNS lookups.
To protect DNS integrity, organizations should also enable DNS Security Extensions (DNSSEC). DNSSEC adds cryptographic signatures to DNS records, allowing resolvers to verify that responses originate from authoritative DNS servers and have not been altered. While DNSSEC does not hide DNS data, it prevents attackers from injecting false DNS responses or redirecting users to malicious destinations during reconnaissance.
Segment networks and isolate sensitive systems
Network segmentation protects your environment by ensuring that the discovery of one system doesn’t automatically reveal or grant access to others. Even if reconnaissance identifies a public-facing component, segmentation limits what can be learned about the rest of the network and restricts how far access can extend.
This is achieved by dividing the network into smaller segments based on function or sensitivity and tightly controlling how those segments communicate. Public-facing systems should be placed in isolated segments with explicit rules governing any communication with internal systems.
Sensitive assets such as identity services, databases, administrative tools, and management planes should be isolated from user networks and from the public edge. Access to these systems should only occur through managed interfaces with strong access controls. By enforcing clear boundaries and limited communication paths, segmentation reduces lateral movement and limits the usefulness of reconnaissance data.
Detect and monitor reconnaissance activity
You can’t reliably block reconnaissance, but you can detect it early by monitoring for the behaviors it produces. Active reconnaissance typically generates patterns that stand out from normal traffic when they are observed over time.
Use intrusion detection and prevention systems (IDS/IPS) to monitor both network and host activity. Network-based systems analyze traffic flows to identify behaviors commonly associated with reconnaissance, including repeated connection attempts across multiple ports or hosts, scan-like traffic patterns, and unusual protocol usage. Host-based systems complement this by monitoring individual systems for signs such as abnormal service queries, unexpected process activity, or suspicious log events.
IDS/IPS tools rely on a combination of signature-based detection and behavioral analysis. Signature-based detection allows systems to recognize known reconnaissance techniques, such as TCP SYN scans or malformed connection attempts. Behavioral detection focuses on deviations from normal activity, such as repeated ping requests or systematic port probing, even when no known signature is present.
More advanced detection strategies may include honeypots or decoy services. These are intentionally exposed systems or services, such as a fake Secure Shell (SSH) endpoint, that have no legitimate use. Any interaction with them is a strong signal of reconnaissance activity and provides early warning without exposing production assets.
FAQ: Common questions about reconnaissance in cybersecurity
What is reconnaissance in cybersecurity?
Reconnaissance is the process of gathering information about systems, networks, or organizations to understand their structure and exposure. This includes looking for information from public sources as well as technical information such as network maps, unpatched vulnerabilities, open ports, and outdated applications.
Reconnaissance is used by security teams to identify these gaps, prioritize patch management, and strengthen the security posture before attacks can take advantage of them.
What is the purpose of reconnaissance?
The primary purpose of reconnaissance is to gather relevant information about a potential target through both active and passive means. This reduces the guesswork in planning an attack and allows attackers to identify entry points and plan post-compromise attack paths. Defensive teams use reconnaissance as a proactive measure to scan their systems and networks to fix vulnerabilities.
How can organizations protect against reconnaissance?
Organizations can employ various methods to reduce the impact of reconnaissance. These include limiting publicly available information, network segmentation, and using intrusion detection systems.
What tools are used for reconnaissance?
The tools used for reconnaissance include network and port scanners, OSINT collection APIs, network protocol analyzers, vulnerability scanners, and banner-grabbing utilities. These tools help identify exposed systems, map infrastructure, and detect vulnerabilities. Security teams use many of the same tools to validate exposure and strengthen defenses.
How does reconnaissance fit into the cybersecurity lifecycle?
Reconnaissance is often the first step in frameworks such as the Cyber Kill Chain and is used by both attackers and security researchers. Attackers use it to observe and collect intelligence about a potential victim using various tools and techniques, while security teams use it for asset discovery, vulnerability management, identifying misconfigurations and potential weaknesses, and strengthening their security posture.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN