Heartbleed vulnerability: Understanding and mitigating risks
Heartbleed was a security flaw that allowed malicious actors to read sensitive memory from servers running vulnerable versions of OpenSSL. By exploiting it, attackers could silently extract passwords, private communications, and even encryption keys used to secure HTTPS connections.
The flaw was assigned the identifier CVE-2014-0160 in the Common Vulnerabilities and Exposures database. Although it was introduced into OpenSSL in 2012, it wasn’t publicly identified until 2014.
The vulnerability was patched quickly, and the affected OpenSSL versions are now considered obsolete. That said, systems that haven’t been updated since that period would still be vulnerable today.
This article explains how the Heartbleed vulnerability worked and why it was so impactful, as well as the steps that were required to reduce exposure.
What was the Heartbleed bug?
The Heartbleed bug was a security flaw in OpenSSL versions 1.0.1 through 1.0.1f, a cryptographic library that some applications and websites used to secure data in transit over the internet. This bug allowed attackers to read small pieces of protected memory from vulnerable systems without authorization.
How did Heartbleed work?
Heartbleed exploited a feature called Heartbeat. Heartbeat is a simple keep-alive mechanism built as an extension to the Transport Layer Security (TLS) protocol. It allows a client, such as a web browser, and a server to confirm that their connection is still active.
In normal operation, a user’s browser sends a small packet of data to the server as a Heartbeat request. The server responds by sending back the same data. This response confirms that the server received the message and keeps the connection alive.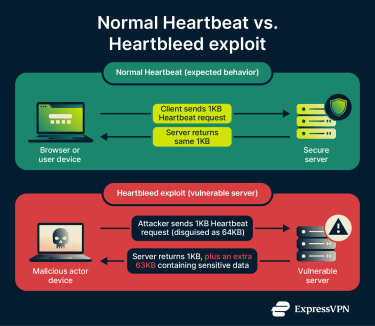
A Heartbleed vulnerability occurred when an unpatched server failed to properly validate Heartbeat requests. In the Heartbeat protocol, the client states how much data they’re sending, but a vulnerable server doesn’t check whether this value matches the actual payload. As a result, the server responds with the payload plus extra bytes pulled from its own memory, potentially exposing sensitive information.
Because OpenSSL doesn’t enforce limits on the returned data, attackers could exploit this flaw repeatedly to request different chunks of server memory. These requests didn’t require authentication and left no clear traces in standard logs, making the resulting data exposure difficult to detect.
This unintended leaking of memory during routine Heartbeat responses gave the vulnerability its name. The bug effectively caused systems to “bleed” memory contents.
Was the Heartbleed vulnerability high-impact?
Heartbleed was a significant vulnerability in OpenSSL software. It let attackers quietly steal pieces of a server’s working memory without needing special access or leaving obvious signs of an attack.
Cost and impact of Heartbleed
The Heartbleed bug had far-reaching consequences for both organizations and users. Its impact affected financial, operational, and reputational aspects of businesses worldwide:
- Global reach: According to the U.K.-based cybersecurity company Netcraft, 17.5% of web servers with SSL certificates surveyed in 2014 were vulnerable to the Heartbleed bug, which accounted for about 500,000 websites back in 2014.
- Sensitive data exposure: Attackers could steal usernames, passwords, emails, chat messages, and even encryption keys directly from server memory.
- Financial fallout: Organizations incurred significant costs related to emergency security audits, patching and software updates, TLS certificate revocations and reissuance, and broader infrastructure remediation efforts.
- Operational disruption: IT teams had to work under pressure to patch systems, rotate encryption keys, and reset user passwords. Many services experienced downtime or forced logouts while teams fixed the issue.
- Loss of trust: Customers lost confidence in affected companies, especially when breaches involved personal or financial data. Some organizations faced long-term reputational damage even after they fixed the technical problem.
- Legal and compliance risk: Companies in regulated industries faced legal scrutiny and compliance concerns when Heartbleed exposed protected data.
Why should I care about Heartbleed?
Heartbleed matters because it shows how personal data can be exposed without a user making a mistake.
While most major websites patched the flaw quickly, not every system was updated at the time. Security researchers have since identified isolated cases of forgotten websites, internal tools, or legacy devices that continued running vulnerable software. In those environments, credentials could be exposed without obvious signs of compromise.
For users active in 2014, the impact could also be long-lasting. Passwords or encryption keys captured then may have been reused, resold, or exploited years later.
More broadly, Heartbleed reshaped how online security is understood. It showed that HTTPS or a lock icon in the taskbar doesn’t guarantee safety. Security depends not just on user behavior but on whether services consistently maintain and protect their systems.
Why many users had to reset their passwords
Users were asked to reset passwords because Heartbleed could expose login credentials directly from a server’s memory. Even strong, unique passwords could be compromised without a user’s knowledge if they were in memory at the time of an attack.
Once the vulnerability became public, service operators began patching affected systems and replacing exposed encryption keys. After those fixes were in place, many companies advised users to change their account passwords to ensure any potentially leaked credentials were no longer valid.
Security experts recommended waiting until a site confirmed it had applied the patch before resetting passwords. Resetting a password before a site applied the fix could actually put users at risk, because attackers could still capture the new password using the same vulnerability.
Were VPN services impacted by Heartbleed?
Yes, some virtual private network (VPN) services were affected by the Heartbleed vulnerability.
By sending malformed Heartbeat requests, attackers could extract valid session data from the memory of affected VPNs. They then reused those tokens to take over active sessions, allowing them to impersonate legitimate users and access internal network resources without re-authenticating.
Because these session tokens represented already authenticated connections, the attacks could bypass multi-factor authentication (MFA) and device checks that were normally enforced during login.
The root cause was the vulnerable OpenSSL library used by the exploited VPNs for cryptographic functions. Once attackers obtained sensitive memory contents, the VPN system could treat them as legitimate users, potentially allowing further movement within the network.
VPN services that promptly patched OpenSSL, rotated cryptographic keys, and enforced session resets, including ExpressVPN, are no longer affected by Heartbleed.
How ExpressVPN responded (and why it still matters today)
When the Heartbleed vulnerability was publicly disclosed in April 2014, ExpressVPN responded the same day, patching all affected systems that relied on OpenSSL within hours. At a time when large parts of the internet remained exposed, this rapid response helped limit risk to users and set an internal standard that still defines how we handle critical security events today.
As an immediate precaution, ExpressVPN also rotated server certificates and cryptographic keys and briefly disconnected active sessions to ensure that any potentially exposed secrets could not be reused. This step acknowledged a key lesson of Heartbleed: patching the vulnerability alone is not enough if sensitive material may already be in memory.
Importantly, ExpressVPN’s OpenVPN servers already used tls-auth, an additional authentication layer that restricts which packets a VPN server will even process. This helped mitigate certain Heartbleed attack paths before patches were applied, giving users a head start while the broader ecosystem was still reacting.
How users detected Heartbleed
Detecting the Heartbleed vulnerability involved finding out if your server or SSL/TLS service used a version of OpenSSL that leaked memory when it responded to specially crafted heartbeat requests.
There are still online scanners available today that test whether a server is affected by Heartbleed. These tools typically allow a domain name or IP address to be checked and report whether the vulnerability is still present. Examples include SSL-Tools and Filippo Heartbleed tester.
Was there a Heartbleed fix?
Security teams patched the Heartbleed vulnerability a few days after it was discovered. The fix involved several steps.
- Updated the OpenSSL library: Replaced vulnerable versions of OpenSSL (1.0.1 through 1.0.1f) with a patched release such as OpenSSL 1.0.1g or later.
- Restarted affected services: Restarted all services that relied on OpenSSL, as running processes could continue using the vulnerable code in memory.
- Reissued SSL/TLS certificates: Generated new certificates and revoked existing ones, since private keys may have been exposed.
- Reset potentially compromised credentials: Required users and systems to change passwords and other data that could have been exposed.
Long-term strategies for mitigating Heartbleed-like vulnerabilities
To reduce the risk of future vulnerabilities like Heartbleed, organizations should adopt long-term, proactive security strategies such as:
- Automating patch management: Use patch management tools to establish a process that regularly checks for security updates and applies them quickly. This helps you fix vulnerabilities like Heartbleed before attackers can exploit them.
- Regularly auditing cryptographic libraries: Track which versions of critical libraries your systems use. You can check installed library versions via package managers, system inventory tools, or scripts that scan your servers. Update or replace outdated ones so you reduce the window of exposure when new bugs are discovered.
- Implementing defense-in-depth controls: Add protections such as intrusion detection systems (IDS) to detect suspicious traffic or memory anomalies. These controls help you catch exploitation attempts even if a patch is delayed.
- Implementing perfect forward secrecy: Configure servers to use perfect forward secrecy (PFS) so past encrypted traffic stays safe even if a private key gets exposed later. This approach creates a unique session key for every connection, which prevents attackers from decrypting old data captured during incidents like Heartbleed.
- Educating and raising user awareness: Security awareness programs help users recognize abnormal behavior, certificate warnings, or connection issues that may indicate underlying security problems. While vulnerabilities like Heartbleed operate at the infrastructure level, informed users can still play a role in early detection and incident reporting.
Current landscape of encryption vulnerabilities
Encryption protects most online communications, but risks continue to emerge as vulnerabilities are discovered in the software that implements it. Security researchers regularly find flaws in widely used cryptographic libraries such as OpenSSL, showing that even trusted tools can contain weaknesses.
Similar issues have also appeared in popular JavaScript cryptography libraries, where implementation flaws could enable signature forgery or data manipulation.
At the same time, many old and weak encryption standards exist in legacy systems, creating easy targets for attackers. For example, Microsoft is finally phasing out Rivest Cipher 4 (RC4), an outdated cipher with decades of known weaknesses. Meanwhile, other protocols like Secure Shell (SSH) and TLS have faced downgrade and side-channel attacks that expose encrypted connections.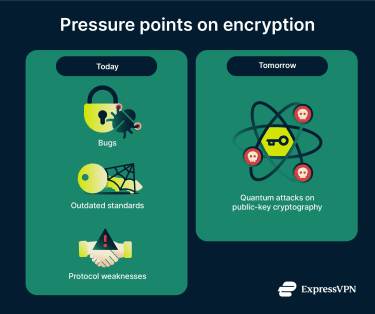
Beyond software bugs and outdated cryptographic algorithms, encryption also faces pressure from future advances in computing. Security researchers warn that sufficiently powerful quantum computers could eventually weaken the mathematical foundations of some widely used public key encryption systems.
How VPNs and encryption standards evolved after Heartbleed
After Heartbleed, many VPN services quickly moved to patched versions of the affected cryptographic libraries and also chose stronger cipher suites and larger key sizes to protect user data.
At the same time, the broader encryption ecosystem moved toward newer versions of the TLS protocol like TLS 1.2 and TLS 1.3. These standards include stronger cryptographic algorithms and more secure handshake processes that limit the kind of memory exposure Heartbleed used. TLS 1.3 especially improves security and performance for encrypted connections by simplifying protocol flows and removing outdated features in earlier versions.
For ExpressVPN, Heartbleed wasn’t just a crisis: it was a turning point. The ability to patch an entire global fleet rapidly and consistently became a non-negotiable security requirement. That experience directly informed the design of ExpressVPN’s modern TrustedServer architecture, which allows the entire server fleet to be rebuilt, patched, and redeployed from a verified source image on a rolling basis, typically within hours. What was exceptional in 2014 is now routine.
The same proactive mindset continues today. Just as defense-in-depth and rapid response reduced risk during Heartbleed, ExpressVPN now integrates protections before emerging threats become mainstream, such as its early adoption of post-quantum cryptography to prepare for a future where classical encryption may no longer be sufficient.
FAQ: Common questions about the Heartbleed vulnerability
Why is it called Heartbleed?
It was called Heartbleed because the bug existed in OpenSSL’s implementation of the Transport Layer Security (TLS) Heartbeat feature and caused systems to “bleed” memory data when handling those handshake heartbeat messages.
Is TLS 1.2 vulnerable to Heartbleed?
Transport Layer Security (TLS) 1.2 itself is not the cause of Heartbleed. The bug is in OpenSSL versions 1.0.1 to 1.0.1f that support heartbeat, and any protocol using any of these versions could be affected.
How can I test my server for Heartbleed?
You can test your server using online Heartbleed checking tools like SSL-Tools that probe for the old, vulnerable OpenSSL versions.
What are some notable Heartbleed attacks?
One notable Heartbleed attack was the breach of the Canada Revenue Agency (CRA), where attackers stole about 900 Social Insurance Numbers. In another case, attackers compromised the hospital group Community Health Systems and stole sensitive data from roughly 4.5 million patients, including names, birth dates, Social Security numbers, and addresses.
How does Heartbleed compare to other vulnerabilities?
Heartbleed let attackers read sensitive memory from servers and steal keys or data without crashing the system. This made Heartbleed more dangerous than other bugs that cause crashes or denial of service, as these can be noticed and fixed quickly.
Can I still be vulnerable to Heartbleed today?
Yes, you can still be vulnerable if you use a server that runs an old, unpatched OpenSSL version containing the Heartbleed bug, but it’s unlikely. That said, before visiting a website, you can use online checking tools to confirm if it runs an outdated OpenSSL version.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN