Data theft: What it is and how to protect yourself
Your data travels constantly: between apps, websites, devices, and cloud services. Every stop along the way is a potential point of exposure. Data theft happens when someone intercepts or collects that information without permission, turning ordinary digital activity into a security risk.
This guide explains what data theft looks like today and what you can do to make yourself a harder target.
What is data theft?
Data theft is the unauthorized taking of digital information. It often involves accessing, copying, or moving data without permission. Once taken, that information may be stored, shared, or sold elsewhere, sometimes ending up in breach databases or illegal marketplaces without the owner ever knowing.
Data is taken for various reasons, depending on who is targeted and what type of information is involved. For individuals, stolen data is commonly used for financial fraud, identity theft, or account takeover. For businesses, attackers may seek a competitive advantage by stealing proprietary information or use sensitive data for extortion or ransom demands.
The information involved can range from personal details, such as login credentials or payment information, to business-specific data, including product designs, source code, pricing strategies, customer databases, or internal communications. Regardless of the motivation, the core issue is the same: information is taken from a protected environment and used without consent.
Types of data theft
Data theft can take many forms, depending on who’s targeted and where the information is stored. These differences affect the level of risk involved and the steps needed to protect sensitive information.
Personal data theft (often linked to identity theft)
Personal data theft refers to the theft of personal information that’s commonly used to commit identity theft. In many cases, stealing someone’s data is the first step attackers take before impersonating them, opening accounts, or making fraudulent purchases in their name.
Criminals typically look for details such as names, addresses, birth dates, identification numbers, Social Security numbers, financial details, or login credentials for online accounts.
When this information is misused, the consequences can be significant. Victims may face unexpected charges, account takeovers, or long-term issues with credit reports, along with the time and stress involved in restoring access to their accounts and personal data.
Insider data theft
Insider data theft occurs when someone with legitimate access to an organization’s systems misuses that access to obtain confidential information. Because this activity originates from within trusted accounts, detecting these incidents is often more challenging.
Insiders generally fall into three categories:
- Malicious insiders intentionally misuse authorized access, often for personal gain or retaliation.
- Negligent insiders expose data by ignoring security policies, mishandling sensitive files, or making preventable mistakes.
- Compromised insiders are individuals whose accounts have been taken over after their credentials are stolen, allowing attackers to operate using valid access.
All three scenarios can result in data exposure or theft, even though the intent and level of awareness differ.
Medical data theft
Medical data theft involves the misuse of health-related information, such as insurance details or patient records. It’s often linked to medical identity theft, where stolen information is used to obtain medical care, prescriptions, or submit fraudulent insurance claims in someone else’s name.
Because this type of misuse may go unnoticed for long periods, it can lead to unexpected bills, denied insurance coverage, or further complications when victims seek medical care in the future.
Physical device theft
Theft of physical hardware may seem basic compared with digital attacks, but it remains a common way for sensitive information to fall into the wrong hands. If a stolen laptop, phone, or storage device isn’t protected with a strong passcode, the person who takes it may be able to access the data stored on it.
Online account and credential theft
This type of theft involves taking control of online accounts by obtaining login details. When a username and password are compromised, they can be used to access the associated account. If the same credentials are reused elsewhere, a single breach can expose multiple services, such as email, banking apps, or cloud storage.
Attackers commonly obtain login details through phishing attacks that direct people to fake websites and login pages. Credentials may also come from data breaches, where exposed usernames and passwords later circulate online. In some cases, spyware such as keyloggers is used to record what someone types, including login information.
Data harvesting
Data harvesting refers to the practice of collecting large amounts of personal information from places where it’s already visible or poorly protected, such as public profiles, databases, unsecured sites, or pages that reveal information unintentionally.
While not all data harvesting is conducted with malicious intent, the information collected can be used for scams, impersonation, or other forms of misuse. Separate data points can be linked together to build detailed profiles of individuals, making it easier to craft convincing phishing messages, bypass security questions, or impersonate someone across multiple services.
Corporate and enterprise data theft
When attackers target a company, they usually go after information with clear business value. This can include intellectual property, internal documents, and large collections of customer or employee data.
Stolen data may involve product designs, trade secrets, source code, customer and financial records, operational plans, or other sensitive strategic information. Losing this type of data can weaken a company’s competitive position, expose it to regulatory scrutiny and legal claims, and damage customer trust.
In some cases, attackers use stolen data as leverage, threatening to publish or misuse it unless a payment is made. In others, the data may be sold, used for fraud, or exploited to support further intrusions into the organization’s systems or connected partner networks.
Common methods used in data theft
Attackers use a range of tactics to obtain information they’re not authorized to access. Many of these methods rely on manipulation or weak security controls, which is why understanding them helps reduce exposure.
- Phishing and spear phishing: Attackers send emails or messages that look legitimate, with the goal of prompting recipients to share sensitive details or interact with a malicious link. Spear phishing follows the same approach but targets a specific person, using messages that are deliberately tailored with known details about the target.
- Malware: Some types of malicious software are designed specifically to steal data. Spyware and keyloggers can quietly monitor activity on a device, capturing login credentials, personal information, or keystrokes without the user noticing. Other malware may collect stored files or browser data and send it back to an attacker.
- Brute-force attacks and credential stuffing: Some attackers use automated tools to guess passwords at high speed, which makes these attacks especially effective against weak, short, or commonly reused passwords. Others take login details exposed in earlier incidents and try them on different accounts, hoping passwords have been reused across services.
- Exploiting vulnerabilities: Outdated software or unpatched bugs can create openings that let attackers slip into a system without being noticed. Once inside, they may search for stored files, databases, or account credentials, copying sensitive data or setting up access that allows information to be taken over time.
- Man-in-the-middle (MITM) attacks: On unsecured or malicious networks, attackers may attempt to intercept data moving between a user’s device and a website.
Data theft vs. data breach vs. data leak
Data breaches, data leaks, and data theft are closely related, but they’re not the same. A breach or leak can sometimes lead to data theft, particularly when exposed information is later copied, sold, or misused by unauthorized parties.
| Concept | Typical cause | Malicious intent |
| Data theft | Phishing, malware, vulnerabilities, insider threats, data exposed through a breach or leak. | Yes. The purpose is to steal the information. |
| Data breach | Hacking, abuse of misconfigured systems. | Yes. The incident may or may not include theft, but it nonetheless involves unauthorized access. |
| Data leak | Unsecured databases, misconfigured cloud storage, or accidental publication. | Not usually; while the leaked data can be misused, the leak itself is accidental. |
Consequences of data theft
Data theft can affect people and organizations long after an initial incident. The sections below break down the most common consequences and why they matter.
Personal and financial impact
For both businesses and individuals, data theft can lead to personal and financial consequences such as:
- Unexpected charges or account activity, which often take time to unwind.
- Out-of-pocket expenses for replacing documents, restoring access, or monitoring credit.
- Long-term setbacks, such as credit issues that affect loan applications.
- Losing access to online accounts if attackers change passwords or lock users out after stealing their credentials.
For businesses, the consequences can also include:
- High recovery costs, from technical investigations to system repairs.
- Regulatory fines or legal claims when customer or employee information is involved.
- Operational slowdowns, as teams pause regular work to manage the incident.
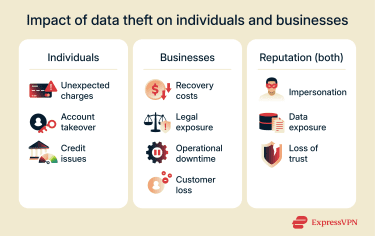
Reputational damage for individuals and companies
For individuals, reputational harm can happen if stolen information is used to impersonate someone or create misleading accounts. When others encounter fake messages, posts, or activity linked to that person’s name, it can damage trust and affect how they’re perceived both personally and professionally.
Exposure of private details can also have lasting effects. If sensitive information such as health records or personal messages becomes public, it can change how friends, family, or colleagues relate to the individual, creating strain or discomfort that persists even after the immediate issue is resolved.
For companies, reputation also plays a significant role. When a data theft incident becomes known, customers may question whether the organization can protect their information, especially if details about poor security practices or delayed responses emerge. That loss of confidence can lead customers to reduce their usage or switch to alternatives they perceive as safer.
Public companies may also see their value drop as confidence fades. Investors tend to react negatively to uncertainty and risk, and concerns about future breaches, regulatory costs, or customer loss can influence market perception. Beyond that, a damaged reputation can affect hiring. Skilled candidates may hesitate to join an organization they associate with weak security practices or ongoing risk, particularly in roles that handle sensitive data.
Signs your data may have been stolen
Detecting data theft early is easier when you know what specific changes to look for. Common warning signs include:
- Alerts about logins you don’t recognize: Notifications mentioning a new device, location, or app you’ve never used.
- New online accounts you didn’t open: Emails welcoming you to services you never signed up for.
- Charges you can’t explain: Even small or “test” transactions can signal that stolen details are being checked for future fraud.
- Passwords suddenly not working: Losing access to an account without making any changes yourself is a strong sign someone else has taken control.
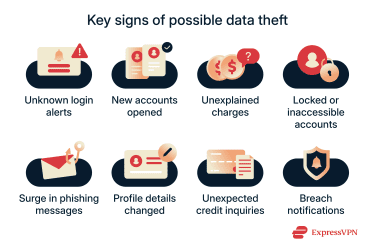
- A spike in targeted scams: More phishing emails, texts, or calls that reference real services you use, often a result of your information being circulated.
- Personal information changed without your input: Addresses, phone numbers, or recovery emails modified in your bank or online profiles.
- Unfamiliar credit inquiries: Loan or credit applications showing up on your report that you never submitted.
- Notifications about external breaches: Alerts from companies or services saying your information may have been exposed.
What to do if you've been affected by data theft
If your information has been misused, there are practical steps to secure your accounts, limit further harm, and reduce the risk of repeat misuse.
Steps to take immediately
Start with the basics and move through these actions as quickly as you can:
- Secure your accounts: Change the password on any account that shows suspicious activity, starting with email and banking. Then update passwords on other important services that use the same or similar details. Use strong, unique passwords for each account, ideally stored in a password manager, to reduce the risk of reuse or weak credentials.
- Turn on extra layers of security: Enable two-factor authentication (2FA) on key accounts such as email, banking, and major apps. Using an authenticator app is usually more secure than SMS codes.
- Contact your bank and payment providers: If you see charges you don’t recognize, call your bank, card issuer, or payment service right away. Ask them to block or replace affected cards and review recent transactions for anything unusual.
- Check your devices for malware: Run a full scan with reputable security software on your phone, tablet, and computer. Remove anything flagged as suspicious and make sure your systems and apps are fully updated.
Reporting to authorities
Reporting what happened helps create an official record that banks, credit agencies, and investigators can reference if fraud continues or disputes arise later.
- File a report with local authorities: In many places, a police report can help when you dispute charges or correct records later.
- Report identity misuse where relevant: In the U.S., you can use IdentityTheft.gov to document the case and receive a guided recovery plan. In other countries, look for your national consumer protection or fraud reporting service.
- Inform affected companies: If the incident is linked to a specific service or retailer, contact their support or security team. They may be able to lock accounts, provide more details, or offer additional protections.
Credit monitoring and risk mitigation
Once the urgent steps are done, focus on protecting your financial identity.
- Set up a fraud alert: In the U.S., you can ask the three major credit bureaus to place a fraud alert on your file. This requires lenders to take extra steps to confirm your identity before opening new credit in your name. Third-party identity protection or credit monitoring services can also help flag suspicious activity and support ongoing monitoring.
- Consider a credit freeze: A credit freeze is more restrictive than a fraud alert. It limits access to your credit file entirely until you lift it, which makes it much harder for someone to open new accounts using your details.
- Review your credit reports: Check your credit reports regularly, look for accounts, loans, or inquiries you don’t recognize, and dispute anything that appears incorrect.
FAQ: Common questions about data theft
What is data theft?
Data theft refers to the unauthorized access, copying, or removal of private information that was meant to remain confidential, such as files, passwords, or personal details. The goal is usually to use that information for financial gain or some other advantage.
What types of data are most commonly targeted?
Attackers often look for information that can be used to impersonate someone or access accounts: names, addresses, login credentials, financial details, identification numbers, or business-related data like internal documents or intellectual property.
Can stolen data be recovered?
Once information has been copied or taken, there’s no way to fully “get it back.” The focus instead is on limiting how it can be used by securing accounts, disputing fraudulent activity, and monitoring for further misuse.
Is data theft the same as identity theft?
Not exactly. Data theft refers to taking information without permission. Identity theft happens when someone uses that stolen information to impersonate you, open accounts, or make fraudulent transactions.
What’s the difference between a data breach and data theft?
A data breach is when information is accessed or exposed without authorization. Data theft is specifically about taking and using that data. A breach may or may not involve theft.
Can a virtual private network (VPN) protect me from data theft?
A VPN can help by encrypting your internet traffic, especially on public or unsecured networks. This makes it harder for attackers to intercept your information. However, it can’t stop data theft that happens through phishing, malware, account misuse, or breaches on a service you use.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN