Privilege escalation explained: Types of attacks and prevention
A compromised user account or system breach is serious enough on its own. However, attackers often try to turn limited access into broad control by increasing what that account, or the code running under it, can do.
Privilege escalation is the step that can change a minor foothold into access to sensitive data, security settings, or administrative functions. Below, we’ll explore what privilege escalation is, the most common ways it occurs, and practical steps to reduce the risk.
What is privilege escalation?
Privilege escalation occurs when someone gains permissions beyond what was originally granted or intended. This can enable actions that their current role shouldn’t permit, such as accessing restricted data, changing system settings, or taking administrative control.
User privileges may be elevated for legitimate reasons, such as when someone temporarily needs additional rights to install software or adjust settings. However, it becomes a security issue when the elevation is unauthorized, such as a contractor who should only edit website content, gaining access to the database or server administration functions.
Malicious actors commonly pursue privilege escalation after initial access because it expands what they can reach and change, which can increase the impact of a cyberattack. Common paths include exploiting vulnerabilities or misconfigurations to elevate privileges, or abusing identity mechanisms (for example, stolen credentials or token impersonation) to obtain higher-privilege access.
Types of privilege escalation
Attackers often pursue two common types of privilege escalation depending on how authentication and authorization controls are designed.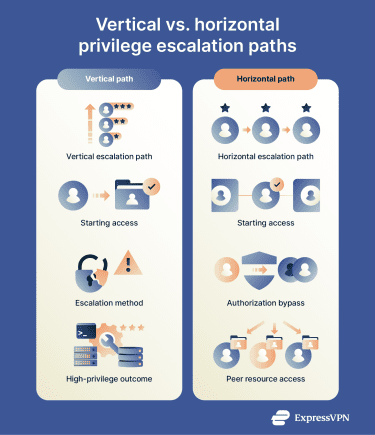
Vertical privilege escalation
Vertical escalation occurs when attackers gain higher-level privileges starting from a lower-provileged account. This can happen by exploiting a flaw or misconfiguration to elevate privileges (for example, from a standard user to local admin), or by obtaining access that effectively grants higher privileges. Examples of high privilege include root on Unix-like systems or NT AUTHORITYSYSTEM on Windows.
For example, an attacker might compromise a standard user account through phishing, then exploit a software vulnerability to gain local administrator rights. From there, they could steal domain administrator credentials to control the entire network.
Horizontal privilege escalation
Rather than increasing privileges, horizontal escalation focuses on unauthorized access to resources owned by other users at a similar privilege level. For example, an employee might be able to access other employees’ files or records that should be restricted to the owner or to a specific team.
Horizontal escalation can be easy to miss when monitoring focuses mainly on detecting explicit privilege increases rather than validating authorization checks and spotting unusual access to other users’ resources.
How privilege escalation attacks work
Privilege escalation methods vary, but attackers often follow a similar pattern, with steps that may overlap:
- Initial access: Threat actors first compromise a low-privilege account via phishing, stolen credentials, or vulnerability exploitation. This foothold allows them to explore the system and identify escalation opportunities.
- Escalation: Attackers exploit vulnerabilities or misconfigurations to gain higher privileges. Common techniques include abusing permission settings, exploiting unpatched software, or stealing credentials from memory.
- Persistence: Attackers establish mechanisms to maintain their access. They might create hidden accounts, install backdoors, or modify system configurations to survive restarts and evasion attempts.
- Lateral movement: With elevated privileges, attackers often compromise additional accounts or systems to expand access across the network.
- Impact: Attackers use elevated access to achieve objectives, such as deploying malware, accessing connected systems or data, or tampering with security settings.
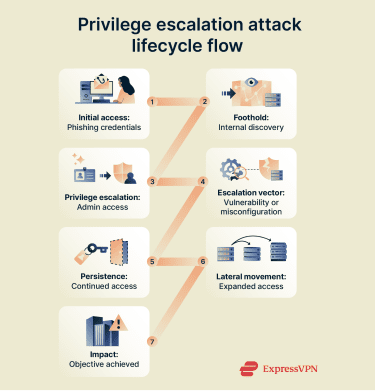
Privilege escalation is rarely the end goal. More often, it enables follow-on actions that can lead to financial gain, data theft, or operational disruption.
Common privilege escalation techniques
Understanding how threat actors escalate privileges is key to preventing attacks and mitigating damage.
Attackers may attempt multiple strategies in a single intrusion. Common routes include exploiting software vulnerabilities or misconfigurations, and abusing credentials or tokens to obtain higher-privilege access.
Exploiting software vulnerabilities
Once inside a system, attackers exploit software vulnerabilities to gain higher privileges. Targeting known, already-documented bugs can be faster than developing custom exploits, especially when reliable exploit code already exists.
Software vendors work to patch newly discovered issues, but attackers often exploit the gap between vulnerability disclosure and widespread patch deployment.
Vulnerabilities in high-privilege components such as the OS kernel and device drivers can be especially severe, because successful exploitation may grant direct administrative access.
Credential theft
Attackers might specifically target the credentials of high-privilege users. They can use automated attacks such as brute-force password guessing, use leaked username–password pairs in credential stuffing, or rely on social manipulation such as phishing campaigns.
Credential compromise often stems from poor security practices, such as using weak passwords or sharing accounts. Attackers can even steal passwords through shoulder surfing in public spaces.
More sophisticated approaches include hijacking sessions to steal session tokens. For example, an attacker might capture a session cookie from an authenticated user’s browser and replay it to impersonate them. In other cases, attackers exploit broken access controls by manipulating IDs or token-related parameters in API requests to access other users’ data or higher-privilege functions.
Misconfigurations and excessive permissions
Once attackers gain access to a system, they often look for misconfigurations that allow them to run code, change access rules, or access protected resources. Risk increases when accounts start with excessive permissions.
Common targets include weaknesses in authentication workflows, such as flawed password reset logic, and authorization checks, such as missing role verification.
Misconfigurations can also enable bypasses of authorization, such as insecure direct object references (IDOR). For example, changing user_id=123 to user_id=124 in a request may let an attacker access another user's data if the application doesn't enforce server-side access checks. In identity systems, weak enrollment policies or misconfigurations can sometimes allow an attacker to add a new multi-factor authentication (MFA) method or device without the level of verification normally required for privileged accounts.
On Windows, common privilege escalation vectors include misconfigured services that run as NT AUTHORITYSYSTEM while the service executable (or a loaded dependency such as a dynamic-link library (DLL)) sits in a location writable by lower-privileged accounts. Attackers can replace the executable or dependency with malicious code and then restart the service to run it with SYSTEM-level privileges.
Another widely documented Windows vector is token impersonation, where techniques such as RottenPotato and JuicyPotato can enable SYSTEM-level execution under certain conditions.
On Unix/Linux, attackers can exploit misconfigured sudo rules, unsafe file permissions, or binaries with SUID/SGID bits set, which can allow commands to run with elevated privileges (including root) when misconfigured.
Social engineering
Attackers manipulate users, particularly those with elevated privileges, into divulging information or taking actions that compromise security. For example, they may pose as technical support personnel to trick users into providing them with remote access or sharing their credentials.
The most common type of social engineering is phishing, which often involves realistic-looking emails or login portals. Administrators who believe they're dealing with official communications may share sensitive information, open malicious attachments, or approve unauthorized access requests.
Abusing physical access
If attackers gain physical access to a privileged user’s device, the risk depends heavily on conditions such as whether the device is unlocked or whether attackers can obtain administrative access. In those situations, attackers may create new administrative accounts, change permissions, or install malware.
If a user is already authenticated and signed into accounts via single sign-on (SSO) or Open Authorization (OAuth)-based sessions, an attacker with access to the active session may be able to access multiple accounts without re-entering passwords.
This risk increases when users leave authenticated devices unattended in public settings. Even brief physical access may allow attackers to install keyloggers, capture session identifiers, or modify configurations to maintain or expand access.
Impact of privilege escalation
Once attackers gain elevated privileges, they can cause significant damage:
- Financial losses: Attackers may steal money if elevated access gives them entry to financial accounts or payment systems. Victims may also face ransom demands to recover encrypted data or prevent exposure of stolen information.
- Data theft: Elevated privileges provide access to sensitive data such as customer records, intellectual property, or personal communications. Stolen data may be sold, used for identity fraud, or leaked for extortion, often causing long-term reputational harm.
- Operational disruptions: Cyberattacks can interrupt business operations or essential services. Recovery often involves incident response, investigation, system restoration, and security remediation, which can consume significant time and resources.
- Compliance violations: Major data breaches might trigger regulatory reporting and investigations, particularly when customer or partner data is involved. This can result in legal claims, fines, or penalties, depending on applicable data protection rules and how the incident was handled
How to prevent privilege escalation
Implementing proactive security measures is usually more effective than responding after a breach has occurred.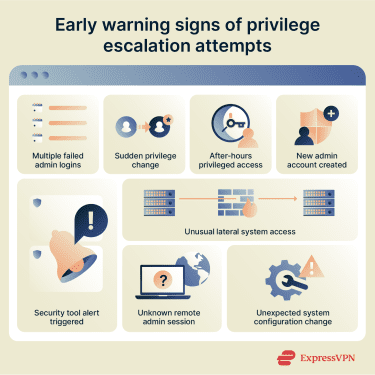
Follow principles of least privilege and zero-trust
This approach involves assigning users only the minimum privileges necessary to perform their tasks. When higher access is required, it can be granted temporarily using just-in-time access and then revoked.
Similarly, zero-trust removes implicit trust based on network location and requires access decisions to be enforced through authentication and authorization checks, often with ongoing evaluation during access sessions.
Use robust authentication practices
This involves enforcing strong passwords, promoting personal cybersecurity hygiene, and implementing additional controls, like MFA or passwordless sign-in.
MFA adds a second verification that can stop many account-takeover attempts, even when passwords are stolen, especially when phishing-resistant methods are used. Passwordless authentication reduces reliance on passwords by using device- or hardware-backed authenticators, such as passkeys or security keys, which can be harder to phish than passwords alone.
Apply strict access controls and audit privileges
Role-based access controls (RBAC) assign permissions through roles that reflect job functions. Regular permissions reviews help reduce permission sprawl and identify unauthorized access.
Privileged access management (PAM) tools can help secure privileged credentials by vaulting, rotating, and monitoring or logging sessions to reduce misuse risk. For remote administrative access, organizations should require encrypted remote access with strong authentication, combined with device controls and least-privilege policies to limit which admins and systems can reach sensitive environments.
Install monitoring and detection tools
Antivirus software may identify and remove some forms of malware commonly use duing intrusions, including trojans, spyware, and rootkits. This protection is available for both individual users and organizations.
Endpoint detection and response (EDR) tools go further by continuously monitoring endpoint activity and flagging suspicious behavior that doesn't match known signatures, such as unusual privilege changes, credential access attempts, or abnormal process execution.
Security information and event management (SIEM) platforms centralize security-relevant data from across systems so it can be correlated and reviewed in one place, while intrusion detection systems (IDS) monitor network or system events and alert on signs of unauthorized activity. Together, they can improve environment-wide visibility beyond what endpoint-only telemetry typically provides.
Segment and isolate critical environments
Organizations can separate sensitive systems, administrative interfaces, and high-value workloads from general networks using network segmentation, virtual local area networks (VLANs), or dedicated management zones with enforced controls between segments. This can limit lateral movement if attackers compromise a low-privilege account.
Communication between segments can be restricted using firewall rules and access policies that allow only essential ports and services. Critical infrastructure, such as domain controllers, backup systems, and security tools, should be isolated to reduce impact and prevent a single compromise from spreading across the environment.
Patch and update management
Keeping OSs, browsers, software, and drivers up to date helps patch known vulnerabilities. Enabling automatic updates or using centralized patch management in organizations can help apply security fixes more consistently and reduce the time systems remain unpatched.
Education and training
The human factor remains a significant cybersecurity risk in many organizations. Training programs help employees recognize threats, understand why security controls exist, follow their responsibilities, and report suspicious activity quickly when compromise is suspected.
FAQ: Common questions about privilege escalation
Can network access controls reduce privilege escalation risk?
Yes. Network access controls (NACs) can reduce the risk of privilege escalation impact by limiting which users, devices, and services can access sensitive systems and administrative interfaces. Techniques like network segmentation and zero-trust policies help restrict access paths, making it harder for attackers to move laterally or reach high-value targets after an initial compromise.
Is privilege escalation possible even in secured networks?
Yes. No network can guarantee 100% effective authentication and authorization across every system and application. Misconfigurations and visibility gaps can arise as organizations manage multiple IT systems and access paths. Attackers may also use social engineering to bypass controls or exploit software flaws on endpoints and servers to gain elevated access.
How do attackers escalate privileges after initial access?
Attackers often exploit known software vulnerabilities, weak credential security, or security misconfigurations to gain higher privileges. From there, they may escalate vertically to higher privileges or expand horizontally by accessing other users’ resources at a similar privilege level.
What security controls are most effective against privilege escalation?
The most effective approach combines least privilege and zero-trust authentication across systems and applications. Security teams should continuously monitor suspicious privilege use, regularly audit access, and use privilege access management (PAM) tools to secure and track privileged accounts and sessions. Keeping security patches up to date and using strong authentication, such as multi-factor authentication (MFA) or phishing-resistant methods where possible, also helps reduce the likelihood that attackers can gain or abuse elevated access.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN