What is password cracking and how can you prevent it?
Password cracking is a technique attackers use to uncover passwords by systematically guessing them or analyzing stolen, hashed password data. Weak or reused passwords make the process far easier than many people realize.
This guide explains why password cracking happens, how attackers take advantage of everyday habits, and what you can do to protect your accounts and lower your risk.
What is password cracking?
Password cracking is the process of gaining unauthorized access to an account by figuring out the password. Cybercriminals do this to steal personal data, money, or gain access to more accounts. The cracking process doesn’t always involve advanced hacking skills. In many cases, it relies on weak passwords, reused logins, or data from past breaches.
How password cracking works
Most password cracking starts after attackers obtain stolen password data, usually from a breached website’s database. However, when websites store passwords, they don’t keep the original text. Instead, they use a hash function, which turns a password into a long scrambled string of characters. The hash is what gets stored, not the actual password.
To further protect passwords, many systems also add a piece of random data called a salt before hashing each password. The salt is unique for every password and ensures that even identical passwords produce different hashes. This prevents attackers from using precomputed tables of hashes to crack many passwords at once, forcing them to attack each one individually. You can learn more in this detailed guide to password hashing.
Once attackers acquire a database of salted password hashes, they can use automated tools to guess possible passwords, hash each guess (with the salt included), and compare the results to the stolen hashes. Depending on the hashing algorithm and hardware involved, these tools can test millions, billions, or even more password guesses per second.
Various cracking methods apply this general process. Some attacks try large numbers of combinations, while others use lists of common or previously leaked passwords to find matches more quickly.
It is important to note that not all account compromises involve cracking. Many result from attackers obtaining unauthorized account access through phishing, malware, or other forms of credential theft. Password cracking typically refers to the offline process of analyzing hashed (and usually stolen) password data.
Most common password cracking techniques
Brute-force attacks
A brute-force attack tries every possible password combination until one works. Automated tools start by guessing simple patterns before moving to more complex ones. Short or predictable passwords fall quickly because there are fewer possibilities, while long, random passwords take far more time and computing power to crack.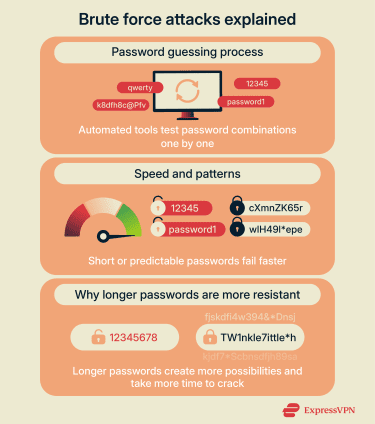
Dictionary attacks
Dictionary attacks are similar to brute-force attacks but more targeted. Instead of random guesses, they use lists of common words and phrases. These lists often come from language dictionaries, leaked password databases, and past data breaches. They include popular passwords, names, and simple variations. Passwords based on real words or predictable patterns are easier to crack using this method.
Rainbow table attacks
Rainbow table attacks use precomputed lists of password hashes to quickly find matches against stolen hashed passwords, reducing the need for repeated guessing. These tables contain vast databases of common passwords and their corresponding hashes, allowing attackers to reverse-engineer passwords from hashes more efficiently.
However, salting significantly reduces the effectiveness of rainbow tables. Since each password is combined with a unique random value (the salt) before hashing, the same password will produce different hashes across different accounts. This means attackers would need to generate separate rainbow tables for every unique salt, which is computationally impractical.
Other password theft techniques
While password cracking involves guessing or computing passwords, attackers often obtain credentials through alternative methods that do not require cracking.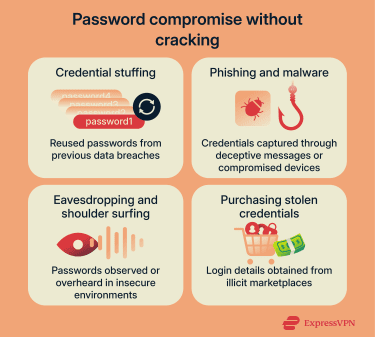
Credential stuffing and password reuse risks
Credential stuffing involves using login details obtained from previous data breaches to attempt access across multiple websites. Attackers often rely on botnets and automated tools to test these passwords at scale. Even if a site was breached years ago, the password may still work today. This technique succeeds because password reuse is common.
Phishing and malware-based credential theft
As mentioned above, some attacks don’t crack passwords at all. Phishing is a social engineering technique where attackers impersonate trusted entities (typically via deceptive emails, messages, or phone calls) to trick users into revealing login details or other sensitive information. These messages often create a sense of urgency or trust to encourage users to act without careful scrutiny.
Malware, short for malicious software, is any software designed to harm or exploit a device or network. In some cases, it can steal passwords directly by running on a compromised device. It may be able to record keystrokes as you type, copy saved browser passwords, or monitor active sessions.
Eavesdropping and shoulder surfing
Not all password theft relies on malware or technical attacks. Some methods exploit human behavior or insecure environments rather than compromised devices.
- Eavesdropping: This involves passively collecting sensitive information without installing software, such as overhearing passwords during phone calls or meetings, capturing keystrokes through a device microphone, or intercepting data on unsecured networks.
- Shoulder surfing: These attacks are visual. Perpetrators watch someone enter a password on a screen or keyboard, whether over a shoulder, from a nearby desk, or even using a camera in public spaces. Short or simple passwords are easier to capture this way.
Purchasing stolen credentials
Attackers sometimes acquire already compromised login details by purchasing them from illicit marketplaces on the dark web. These credentials have often been obtained through previous breaches, phishing campaigns, or malware infections, allowing attackers to bypass cracking efforts entirely.
What are the signs my password was compromised?
 Passwords can be exposed without your knowledge, and noticing the warning signs early helps protect your accounts. Common indicators include:
Passwords can be exposed without your knowledge, and noticing the warning signs early helps protect your accounts. Common indicators include:
- Unexpected account activity: Logins, changes, or actions on your online accounts that you don’t recognize.
- Password reset emails: Messages prompting a reset that you didn’t request (for example, a Google critical security alert).
- Unauthorized charges: Unexplained transactions or purchases linked to your accounts.
- Security alerts: Notifications from dark web monitoring or data breach monitoring tools about suspicious activity.
If you suspect your password was compromised, you can use a password manager with built-in breach monitoring like ExpressKeys, which offers a Password Health tool to identify exposed passwords and help you strengthen them.
Preventing password cracking
Prevention focuses on reducing how useful a stolen password is. This means using strong and unique passwords for every account and adding extra security steps in case the password is stolen.
How to create strong, unique passwords
A strong password is both long and unpredictable. While including a variety of character types increases the number of possible combinations, password length and randomness typically have a greater impact on security.
As outlined above, attackers use various techniques to recover passwords. These may include brute-force attempts that systematically try combinations, as well as dictionary- and rule-based methods that prioritize common words, patterns, or known password variations.
Passwords with high entropy, meaning they’re rare and hard to guess, are far more resistant to these attacks. Aim for at least 16 characters whenever possible, and avoid common words, dates, patterns, or predictable substitutions.
Another key principle is to never reuse passwords. Using the same password across multiple accounts increases risk because a compromise of one account can potentially expose others protected by the same password.
Below are some methods and tools you can use to create strong and reliable passwords.
- Diceware method: Diceware uses random dice rolls to select unrelated words from a predefined list. The result is a long passphrase that’s hard to guess but easier to remember than random characters.
- Passphrase method: This technique creates a password by combining several unrelated words or a memorable sentence into a single string. This makes it more memorable while keeping the password unique and personal.
- Password generator: A password generator can generate long, random passwords for you.
The three-word password rule (does it work?)
The three-word password rule can work if done correctly. It combines three random, unrelated words into a single passphrase that is long and easier to remember than random characters. The strength comes from unpredictability: the words shouldn’t form a common phrase or reference personal information.
To make it more secure, include numbers, special characters, or mixed capitalization rather than relying solely on regular letters (for example, “Purple*Coffee@Skateboard!”).
Tip: Check how strong your passwords are with these tests to verify password security.
How often should I change my passwords?
You don’t need to change passwords on a strict schedule unless there’s a reason to. It’s more important to change them immediately if you suspect a breach, notice suspicious activity, or learn a service you use was compromised. Regularly updating passwords after such events helps reduce the risk of unauthorized access and ensures the security of your accounts.
Other ways to protect your passwords
- Enable multi-factor authentication (MFA): This method, most commonly used in its two-factor authentication (2FA) variation, adds an extra step after entering your password. This might be a code sent to your phone or approval from an app. Even if someone knows your password, they can’t log in without this second factor.
- Keep your software updated: Regular updates patch security vulnerabilities in your operating system, apps, and browsers.
- Get a password manager: Password managers like ExpressKeys are among the best ways to store passwords. It lets you create, store, and autofill strong, unique passwords for every account, making them easy to use without memorizing each one.
Using passkeys for passwordless authentication
Passkeys replace traditional passwords with cryptographic keys stored securely on your device. They allow you to log in using your device’s built-in authentication, such as a fingerprint, face scan, or PIN, without typing a password. Because there’s no password to guess or steal, common cracking methods such as brute force or dictionary attacks become ineffective.
How a VPN helps protect your passwords
A virtual private network (VPN) creates an encrypted tunnel between your device and the internet. This encryption protects the data you send and receive from being intercepted by others on the same network. VPNs are particularly valuable when using unsecured or public Wi-Fi networks, where the risk of eavesdropping is higher.
Protecting encrypted login traffic
Most websites use encryption protocols such as HTTPS to secure login data in transit. A VPN adds an additional layer of encryption by securing all traffic leaving your device. This can reduce the risk of interception or tampering before your data reaches the website’s servers. Additionally, a VPN may help protect apps and services that do not use strong encryption by default.
What a VPN can’t do against offline password cracking
A VPN doesn’t protect passwords once they’re stolen from a database or captured through physical methods like shoulder surfing or eavesdropping. Offline password cracking occurs when attackers attempt to recover passwords from encrypted password hashes they have already acquired. Since this process happens outside of the network communication channel, a VPN does not provide protection in these cases.
FAQ: Common questions about password cracking
How did the 16 billion passwords get leaked?
The “16 billion passwords” didn’t come from a single breach but were collected from many incidents over time, including hacked websites, exposed databases, malware, and phishing. If you suspect your credentials have been exposed, change your passwords and consider setting up passkeys and using multi-factor authentication (MFA) to make stolen credentials much harder for attackers to use.
What is the 3-word password rule?
The three-word password rule is a method for creating long and memorable passwords. It works by combining three random, unrelated words into a single password. When the words are truly random, this approach increases length and makes guessing harder.
How can I create a strong password?
A strong password is long, unique, and hard to guess. Length and randomness matter more than symbols alone. Avoid reusing passwords or including personal information. You can make them even stronger and easier to manage using methods like Diceware, random character strings, or mnemonic techniques.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN