IoT botnets explained: How to detect and defeat them
Botnets were once built almost entirely from infected desktop and laptop computers. The rise of the Internet of Things (IoT) has changed that. IoT botnets exploit vulnerable connected devices at scale, creating larger and more persistent networks for malicious activity.
Here’s how they work, how they spread, and how to identify and mitigate the risk.
What is an IoT botnet?
An IoT botnet is a group of compromised smart devices infected with malware that allows an attacker to control them remotely. Once they’re under an attacker’s control, the devices operate together and can be used to carry out small- or large-scale cyberattacks.
How do IoT botnets work?
Once an IoT device is compromised, it can quietly receive instructions from a remote operator. The operator usually links the device to a command-and-control (C2 or C&C) server, which serves as the hub for issuing tasks and coordinating each infected device.
Because many IoT devices run continuously with stable internet connections, attackers can control large numbers of them at the same time. Compromised devices can then work together to perform disruptive online activities.
The more IoT devices and computers the attacker controls, the more power the botnet has to disrupt systems or overwhelm online services during an attack.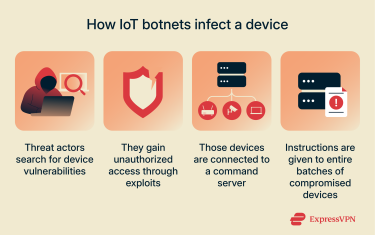
How IoT botnets differ from traditional botnets
Traditional botnets are made up of a network of general-purpose computers, while an IoT botnet is comprised of an army of IoT devices, like cameras, TVs, and routers. Unlike a laptop or desktop, most of these devices don’t have complex operating systems or users installing apps. Their software is minimal, usually just a small embedded operating system or just firmware with a web interface or a few network services. That simplicity, combined with often weak security, makes them an easy target.
PCs usually end up in botnets through social engineering (for example, because the user clicks a link or downloads a dodgy file), or a vulnerability in their browser or operating system is exploited. In other words, there’s often a human element involved, or a fairly sophisticated exploit chain.
IoT devices don’t need humans to make mistakes. Attackers simply scan the internet for devices that are poorly secured. Maybe they still use the default password from the factory, maybe their Telnet or Secure Shell (SSH) port is open, or maybe the device has an unpatched firmware vulnerability. Once they find one, they can log in and drop a tiny piece of malware designed specifically for that type of device.
This malware isn’t like the massive programs you might install on a computer. It’s small, usually just a few hundred kilobytes, and does one thing well: connects to a C&C server and waits for instructions. That could be launching a distributed denial-of-service (DDoS) attack, scanning for more vulnerable devices, or otherwise helping the botnet expand. It’s efficient, low-resource, and disposable (because if the device reboots, the malware often disappears). The attackers don’t mind; they can reinfect it in minutes using the same default credentials or exposed service they exploited in the first place.
The goals are different too. PC botnets often try to steal data, harvest credentials, or install ransomware, because PCs hold valuable information and computing power. IoT devices, in contrast, rarely store sensitive data and aren’t powerful enough for complex attacks, so they’re mainly used as “zombies” in a massive network that can flood websites or services with traffic.
Despite those differences, both traditional and IoT botnets can be used for the same purposes. Attackers can rent or control them to flood websites with traffic, brute-force logins, send spam, or spread additional malware at a large scale.
| Feature | PC botnets | IoT botnets |
| Devices targeted | Laptops, desktops, servers | Smart cameras, DVRs, routers, smart bulbs, other connected devices |
| How infection happens | Usually through phishing, malicious downloads, drive-by exploits | Automated scanning for default passwords, open ports, or known firmware vulnerabilities; no user interaction needed |
| Malware complexity | Often large, sophisticated programs that can steal data, log keystrokes, encrypt files | Small, lightweight binaries designed for a single purpose, like DDoS or scanning |
| Persistence | Often designed to survive reboots and updates (startup scripts, registry, services, rootkits) | Often lost on reboot; attackers reinfect devices quickly using the same weak points |
| User involvement | Often requires tricking the user (clicking, installing, opening files) | Minimal to none; devices are exploited automatically |
| Purpose | Data theft, ransomware, credential harvesting, crypto mining | DDoS attacks, expanding the botnet, occasional crypto mining on more powerful devices |
| Attack surface | Complex OS and applications offer many points of entry | Minimal OS and interfaces but often very poorly secured; weak passwords and exposed ports are common |
| Value per device | High: contains personal data or computing power | Low individually, but extremely powerful in large numbers |
Examples of real IoT botnets
Real-world IoT botnets show how quickly connected devices can be taken over and how much disruption they can cause.
Mirai
The Mirai botnet became widely known for compromising large numbers of IoT devices, including cameras, to generate powerful DDoS attacks. First discovered in 2016, it’s responsible for one of the largest DDoS attacks in history.
Mirai’s impact led to detailed investigations by law enforcement and long-term changes to the IoT cybersecurity industry. It also led to increased pressure on policymakers and manufacturers to improve IoT security standards.
Mozi
Mozi was first reported in 2019 by 360 Netlab, a Chinese internet security company. It is a peer-to-peer (P2P) IoT botnet that infects devices like home routers, DVRs, and other IoT hardware by exploiting weak or default credentials and known vulnerabilities.
Unlike many IoT malware strains that disappeared after a reboot, Mozi used device-specific tricks on gateways to stay active. It installed startup scripts, modified system settings, and disabled remote management to prevent removal. Its P2P design meant infected devices communicated directly, keeping the botnet alive even if parts of it were taken offline.
In August 2023, a sharp decline in Mozi’s activity was observed in India and China. Researchers from cybersecurity company ESET later reported that a kill switch payload had been delivered to the bots, disabling the malware, shutting down services, and replacing Mozi binaries with inert ones, effectively neutralizing the botnet.
Is every IoT device vulnerable?
IoT devices can be vulnerable because they’re usually designed for convenience rather than strong security. Many run on limited hardware and don’t receive regular updates, which leaves them exposed and allows attackers to hijack them for botnet activity.
Some IoT devices, such as smart refrigerators or security cameras, also stay online continuously and are rarely monitored by their owners. This combination of always-on connectivity, inconsistent patching, and minimal user oversight creates an environment where widespread compromise is possible.
However, well-secured IoT devices can be harder for attackers to target. The overall range of threats that affect them is smaller than for traditional computers, and strong passwords, updated firmware, and restricted remote access can significantly reduce risk.
Business and operational impact of IoT botnet attacks
Major companies and governments are frequently the targets of IoT botnet attacks, including devastating DDoS attacks.
- Frequent disruptions and costly downtime: Successful DDoS attacks cause average downtime losses of more than 6,000 dollars per minute, according to 2023 research by the cybersecurity and application delivery company Radware.
- High rate of IoT-related breaches: According to a survey of 1,200 senior leaders across the U.S. and U.K. by IoT connectivity company Eseye, about 75% of businesses experienced at least one IoT security breach in 2025, up 25% year on year.
Emerging trends in IoT botnet development
The landscape of IoT botnets has evolved rapidly, driven by the growing number of connected devices, their varied architectures, and the ingenuity of attackers. Early botnets, such as Mirai, relied on simple techniques: scanning for default or weak passwords and co-opting devices to launch DDoS attacks. Today, the landscape is more complex. Modern IoT malware is increasingly sophisticated, modular, and persistent, reflecting a shift from opportunistic attacks to more strategic, targeted operations.
One noticeable trend is the adoption of P2P architectures, as seen in botnets like Mozi. By removing dependence on a central command server, these botnets can remain resilient even when parts of the network are taken offline. This self-healing ability makes them harder to disrupt and allows attackers to maintain a stable network of compromised devices over extended periods.
Attackers are also increasingly adding layers of automation: botnets can scan for new vulnerabilities, update themselves, and implement persistence mechanisms to survive device reboots or firmware updates. These capabilities enhance both resilience and adaptability, making modern botnets more difficult to contain.
How to prevent IoT botnet infections
By using the right tools and settings, you can reduce the risk of your devices being discovered and brought into a malicious botnet. That said, there isn’t a foolproof method to completely stop an IoT botnet infection.
Device-level protection
Device-level protection starts with the basics: secure the device through strong passwords and updated firmware regularly.
Apply regular firmware updates
Keeping IoT hardware, firmware, and apps updated is one of the most effective ways to reduce botnet infections. Developers regularly issue new patches for vulnerabilities that attackers actively exploit. If you don’t update to the newest patch, your device may be vulnerable to these known problems.
Change default credentials
Use strong, unique credentials on every device and account to further reduce the chances that automated tools will succeed in guessing your passwords. Use a strong password manager to generate hard-to-guess passwords and store them in an encrypted vault.
Disable unused features
IoT devices often ship with unnecessary services, such as Telnet, SSH, Universal Plug and Play (UPnP), or remote administration. To reduce the attack surface, turn off any service you don’t need and disable remote management where possible.
Network-level security measures
Even well-configured devices benefit from strong network protections. Network segmentation, monitoring, and filtering can limit how far an infection spreads and can prevent compromised systems from contacting external command servers.
Use of firewalls and intrusion detection systems (IDS)
IDSs monitor network traffic for patterns that indicate a compromise, such as unusual connections from IoT devices to external servers. When tuned correctly, IDS can alert you to suspected botnet activity and help you respond before attackers fully establish control of compromised devices.
However, it’s important to know that IDS will only inform you of suspicious activity. Without a good firewall, an IDS cannot prevent an attack from happening. Firewalls enforce the traffic rules that IDS systems can only observe.
A properly configured firewall can block inbound and outbound connections from compromised IoT devices, restrict unnecessary services, and stop lateral movement between network segments. This means that when an IDS flags unusual behavior, the firewall stops suspicious traffic from reaching sensitive systems or C&C servers.
Network segmentation
Network segmentation divides your environment into smaller zones, which restricts how easily a botnet infection on one device can move to others. When you place critical systems and vulnerable IoT assets in separate segments, you reduce the chances of them spreading to more devices through your network.
Using VPNs to obscure device traffic
A virtual private network (VPN) encrypts your internet traffic and masks your IP address, which makes it harder for third parties to observe or tamper with your data. ExpressVPN also filters malicious traffic while you browse, which helps you avoid compromised websites harboring botnet malware.
When you route IoT traffic through a secure VPN tunnel, such as an ExpressVPN-compatible router, you reduce exposure of device communications and help protect against some forms of interception and traffic-based profiling.
FAQ: Common questions about IoT botnets
What are some examples of IoT botnets?
How can I tell if my IoT device is compromised?
The warning signs of an infection include unexplained spikes in bandwidth usage, devices that become slow or unresponsive, frequent crashes or reboots, and unusual activity on your router lights or logs when you’re not actively using the device.
You might also see unexpected configuration changes or login attempts. Both can indicate that the device is being used as part of a botnet or that it’s currently the target of a botnet operation. Additionally, rapid battery drain indicates that something is wrong.
Do antivirus solutions help against IoT botnets?
Antivirus software can detect botnet malware that targets Internet of Things (IoT) devices, and it can help prevent your own devices from being used to control or support a botnet. However, many IoT devices have limited processing power and cannot run traditional antivirus tools.
Does a VPN protect my IoT devices from botnet attacks?
A VPN encrypts traffic and masks your true IP address, which makes it harder for attackers to profile your network or intercept traffic, especially when the VPN runs on your router and covers all connected devices.
Using something like ExpressVPN improves your privacy and can limit exposure to botnets, but it won’t fix weak passwords, unpatched firmware, or unsafe device settings, so you still need to employ basic IoT security practices alongside a VPN.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN