How to stop someone from mirroring your phone

Phone mirroring technology is very useful, but it’s also potentially dangerous. The ability to project photos or videos on a larger screen, like a TV, has obvious applications at home and at work. But in the wrong hands, that same technology can be harmful.
Imagine, for example, if a complete stranger were to remotely view your phone’s screen, tracking your every action. It’s a terrifying form of cyberattack.
Fortunately, most forms of this attack are very rare due to the sophisticated nature of the tools required. Most people simply aren’t at risk. Still, it’s worthwhile to learn about the threat posed by phone mirroring and the steps you can take to stay safe.
Can someone mirror your phone without you knowing?
Yes, resourceful cybercriminals have ways to mirror a victim’s phone without their knowledge. Once the device is mirrored, the attacker can spy on the victim’s screen, tracking their every action.
What is phone mirroring?
Screen mirroring is when a mobile device’s display is transmitted to another device, like a TV, computer monitor, or projector. This can work in two basic ways: casting and true mirroring.
Casting (called Screen Mirroring on iOS devices) is a native, easily accessible feature on most phones. It only displays specific media from your phone onto the second device. For example, you could cast a YouTube video to your TV while texting friends on your phone. Only the video will be displayed on the TV.
With mirroring, the exact same content you see on your phone at a given moment will be displayed on the second device. So if you left the YouTube app to send a text, your messaging app would also be visible on the TV.
Methods used to mirror a phone remotely
 With the right combination of tools, access, and knowledge, a cybercriminal can mirror a victim’s phone fairly seamlessly. An attacker needs to make use of at least one of the following:
With the right combination of tools, access, and knowledge, a cybercriminal can mirror a victim’s phone fairly seamlessly. An attacker needs to make use of at least one of the following:
- Spyware or malware: One of the most common ways criminals obtain remote screen mirroring is via malicious software. Using fake app listings, bogus QR codes, or some other method, these apps are installed on a victim’s phone. From there, they can begin the process of gaining access to the phone’s screen.
- Phishing attacks: Malicious hackers are constantly sending out phishing emails containing malicious links. Clicking one of these won’t immediately grant a hacker the ability to mirror your phone, but it could be the first step in a complex attack.
- Vulnerabilities and exploits: Even the best operating systems have weaknesses in their code. Criminals can exploit these to mirror your phone. That said, this type of attack is extremely difficult and usually very expensive to pull off, so most people aren’t likely to ever be targeted.
- Physical device access: If a criminal somehow gains physical access to your phone, they can install malware or make changes in the settings to grant themselves remote access to screen activity. If you don’t know what changes to look for, you might not know your screen is now being mirrored.
How to tell if someone is mirroring your phone
 Being able to spot the signs of unsolicited phone mirroring is essential if you want to prevent this kind of invasive attack. You won’t always be able to tell, but there are usually some signs to look out for.
Being able to spot the signs of unsolicited phone mirroring is essential if you want to prevent this kind of invasive attack. You won’t always be able to tell, but there are usually some signs to look out for.
Unusual battery drain and overheating
Mirroring uses a lot of your phone’s computing power and resources. As a result, both casting and mirroring will cause the battery to drain more quickly than normal. For the same reasons, the phone is likely to get hot as its chipset works to maintain the mirroring connection.
If your phone is getting hot or rapidly losing battery even though you aren’t using demanding apps or processes, it may be mirroring without your knowledge. Note, however, that there are other possible explanations for this, such as background apps using up your resources, an old battery, or other hardware issues.
Strange apps or admin permissions
Cybercriminals can use various methods to get apps onto your device that can remotely mirror its screen. You may be able to notice them if you regularly scroll through the list of installed apps on your device.
Some apps may appear normal but ask you for an excessive amount of admin permissions, such as the ability to mirror your screen, access your camera, and so on. Be suspicious of apps that need to make use of Accessibility Service, Media Projection, or administrator privileges.
Always be wary of apps that ask for lots of permissions without any logical reason, especially when they come from unofficial libraries.
Duplicate screen activity
If your device is being mirrored, you may notice some unusual behavior on the screen. It might light up randomly or without you interacting with it, which could indicate that a cybercriminal is interacting with your device in some way.
If a malicious actor has simply enabled your phone’s built-in mirroring tools, you should be able to see a notification in your phone’s top bar indicating this. On Android, this will usually say “Link to Windows” or “Casting,” while iOS users should look for anything mentioning mirroring or “Phone Link.”
In extremely rare cases, dedicated attackers can exploit your phone’s built-in processes to mirror your phone in a much more subtle way. Your phone’s built-in safety measures usually require apps running in the background to display a persistent notification. But, seeking to avoid detection and misdirect victims, a hacker could write code so that the notification claims to signal another, innocuous feature completely unrelated to mirroring.
In the most dangerous scenario involving highly advanced exploits, it could be possible for a cybercriminal to run a mirroring app that displays no notification whatsoever. Average users aren’t likely to face this kind of attack, fortunately.
High data usage
Mirroring a device requires an internet connection and can use quite a lot of data. If you suspect your phone is being mirrored, check how much data each app is using and look for anything suspicious. You should be able to do this through your phone’s settings. With some devices, you may be able to display your live data usage in the top bar, so you can see if your phone is using lots of data when it shouldn’t be.
How someone can mirror your phone
As touched on earlier, cybercriminals can use a broad range of malicious tools and tactics to mirror your phone’s screen without your permission or awareness.
Through physical access
Someone with physical access to your phone could potentially set up mirroring on another device. This can be achieved using only your phone’s native features or in combination with malware or legitimate third-party apps.
This is probably the most common method used to mirror phones. The upshot is that, to execute the most basic form of this attack, the malicious actor will need to be nearby and also know the password to your Microsoft or Apple account to set up full mirroring.
But with even a small amount of technical knowledge, someone with physical access could use debug mode to stealthily install a mirroring app even without your password (iPhones are more secure than Androids in this regard).
Depending on whether you are trying to connect an Android or iPhone to a Windows or Mac computer, the mirroring process is different. For example, if a malicious attacker links your iPhone to their PC, they’ll be able to view texts, notifications, and recent photos, but not set up true 1-to-1 mirroring. On the other hand, if your Android is connected to a stranger’s PC, they can mirror your phone and open apps freely thanks to full remote access.
To check for the most basic methods of mirroring, look to your phone’s top tray. You may see an icon from (depending on the devices involved) Link to Windows, AirPlay, or Phone Link. It’s also a good idea to monitor for third-party tools like AirDroid and TeamViewer and check to see whether debug mode has been enabled.
Via spyware or malicious apps
Criminals use a variety of means to get specially designed apps onto victims’ phones. The vast majority of spyware apps are incapable of mirroring your phone’s screen. Instead, they collect other kinds of data, like your location or usage habits. That said, some rare apps can exploit your phone’s mirroring function. In extreme cases, they can even enable mirroring without creating any notification that mirroring has begun. Once infected, the cybercriminal will be able to see what’s on the phone.
Again, true spyware mirroring apps are sophisticated and quite rare. Most people aren’t at risk of being targeted. Still, it’s best to regularly check your phone for unfamiliar apps.
Through public Wi-Fi or Bluetooth
Connecting to public Wi-Fi in places like hotels and airports carries far more risk than using home networks. This is due to the increased risks posed by fake hotspots, man-in-the-middle attacks, and other threats. Connecting to a network or a Bluetooth device can’t automatically enable a hacker to mirror your device. But if the conditions are right and the target is careless, doing so could open them up to a phone monitoring attack.
With phishing
Criminals can also use phishing to begin the process of mirroring a victim’s phone. This can be done through links sent via email, chat, or SMS message. Clicking on a malicious link alone won’t provide a hacker with access to your phone’s screen, but it might be a step in that direction if you’re being targeted by cybercriminals with access to advanced exploits.
Risks of phone mirroring
 Illicit phone mirroring is a very dangerous form of cyberattack. If criminals can see everything you do on your device, there are many ways this can be used against you. Here are just some of the biggest risks to be aware of:
Illicit phone mirroring is a very dangerous form of cyberattack. If criminals can see everything you do on your device, there are many ways this can be used against you. Here are just some of the biggest risks to be aware of:
Privacy invasion
It’s obviously a massive invasion of your privacy for a stranger (or even someone you know) to have the ability to remotely view what’s on your phone’s screen.
They’ll be able to see everything you do, from the websites you visit and the terms you search for to the photos you take and the messages you send.
They could use the information they gain to blackmail you or sell embarrassing details to others. Even if they keep what they learn to themselves, you surely don’t want a stranger knowing everything that you do on your phone.
Credential theft
Every time you open an app or website and log into one of your accounts, a cybercriminal with access to your device’s screen will be able to see the data you enter. That includes your usernames, email addresses, credit card numbers, and passwords.
From there, criminals could steal your accounts, putting you at risk of identity theft and highly targeted scams. Alternatively, they might sell this information on the dark web or make purchases using your cards.
Physical safety concerns
One of the most concerning aspects of phone mirroring attacks is that they can affect your real life as much as your online presence.
If someone can see your device when you open Google Maps, for example, they could then pinpoint your exact location. They could also see your Calendar app or track your messages to determine where you’ll be at a given time.
Again, there are various ways that information could be used against you. Thieves, for example, could plot to break into your home.
How to stop someone from mirroring your phone
Thankfully, there are plenty of ways you can guard against phone mirroring. Even a few small, simple adjustments to your device settings can make all the difference for your long-term safety.
Let’s take a look at how to stop someone from mirroring your phone on both iOS and Android devices.
Stop phone mirroring on iPhone
We’ll begin with steps you can take to stop screen mirroring on iPhones.
Stop screen mirroring on iPhone
This covers stopping someone from mirroring your phone using its built-in tools.
- Swipe down from the top of the screen to access the Control Center and tap the Screen Mirroring icon. It looks like two overlapping rectangles.

- Tap on Stop Mirroring.

Remove mirroring or spy apps from iPhone
- Find the icon(s) of the app(s) you wish to remove from your device.

- Look for any suspicious apps. If you see one you want to uninstall, tap and hold on it, then select Remove App.

Factory reset iPhone to eliminate any screen mirroring access
If you are still worried that your screen is being mirrored, your best option is to initiate a full factory reset of your iPhone. In doing so, you’ll lose any data that isn’t backed up. For this reason, make sure to save copies of any photos, videos, contacts, and documents on a cloud service or secondary device before moving forward. This is a fairly radical step and won’t be necessary in most cases.
Here’s how to do a factory reset:
- Open the Settings app and tap on General.

- Tap on Transfer or Reset iPhone.

- Select Erase All Content and Settings.

- Enter your Apple ID password and wait for the reset to complete.
Stop phone mirroring on Android
Staying safe from criminals seeking to mirror your Android phone or tablet involves similar steps, but the process is different. Note that the exact process may vary depending on the model of your phone and version of Android.
Turn off casting features on Android
If you want to see if someone is using your Android’s native casting function, here’s what to do:
- Open the Settings app.

- In the search bar, type “cast” and tap on the Cast or Screencasting menu that should appear.

- Disconnect from any devices you’re connected to. To do this, just select the device and then tap Disconnect.

Find and remove admin apps that enable mirroring
- Unlike normal apps, admin apps aren’t readily visible, so you won’t find them on your Android’s home screen. To find out if you have any, open your device’s Settings app. Your next step will vary depending on your device and Android version. Another option is to simply search for “admin apps” and proceed from there.

- Look for an option labeled Special app access or Admin apps.

- Tap Device admin.
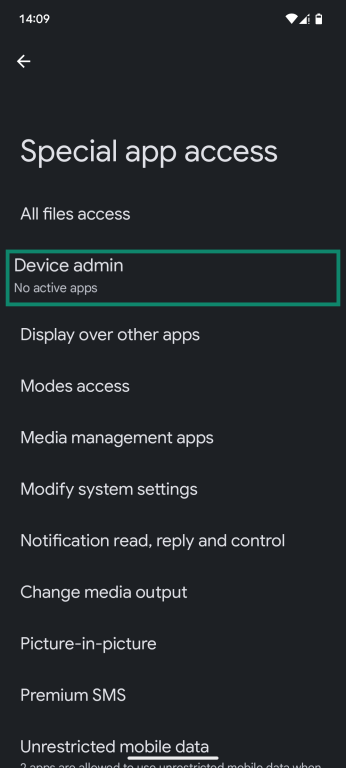
- You’ll see a list of apps with admin privileges. Tap on any unfamiliar app, then toggle its admin rights off.

- Once you’ve removed the admin rights, it’s a good idea to check for regular apps that can mirror your screen, too. The easiest way to review your list of apps is to open the settings tool and search for “apps.”

- In the search results page, tap Apps.
- You will now see a list of every app installed on your phone. Review it for any suspicious entries. Once you find one, tap on it.

- You’ll see information about the app you’ve selected. There should also be an Uninstall button, though in some cases you might need to tap Remove.

Clear cache partition to remove residual tracking components
This step won’t be necessary in most cases, but if you have a strong reason to believe you’re being targeted, it might be a good idea to clear your Android’s cache partition. Here’s how to do it:
- Turn off your device.
- Restart it in Recovery Mode. To do this, you usually need to long-press the Volume Down and Power buttons at the same time, but the exact process can vary on different makes and models of phones.
- Use the Volume buttons to navigate the Recovery menu and find the option to Wipe cache partition.
- Use the Power button to select and confirm this option. Then wait for your device to reboot.
Factory reset Android and reinstall OS
Even more so than clearing your cache, doing a factory reset is a radical step that requires backing up any files you need. Still, if you are confident you’re dealing with an attack that you can’t otherwise manage, it’s a tool you’ll want to know how to use.
- Open the Settings app.

- Type “reset” into the search bar to find the Reset options menu, or locate it via the General Management or System menus, depending on the make/model of your device.

- Tap on Erase all data (factory reset).

- Select Erase all data and enter your PIN or password if prompted.
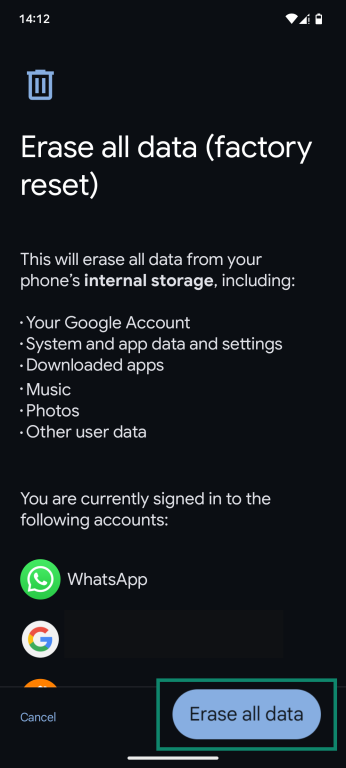
- Confirm the reset and wait for it to finish.
Can you fully prevent phone mirroring?
While there are concrete steps you can take to avoid and detect screen mirroring, there’s no way to stay 100% safe. This is due to the existence of highly sophisticated tools and exploits, some of which lack known countermeasures.
That said, those kinds of attacks are very rare. Only very specific targets are likely to be affected. For most people, phone mirroring is a simpler affair that’s relatively easy to detect. To protect against it, your best bet is to monitor for suspicious activity.
In any case, all users should remain vigilant and aware. Tools like VPNs and anti-malware apps can help you stay safe and enhance privacy across devices, but there are additional things you’ll need to handle yourself in order to stay safe.
Why prevention is stronger than detection
In general, when it comes to cyberattacks like phone mirroring, it’s much better to take preventative measures and avoid becoming a victim in the first place than to worry about detecting and stopping an attack as it happens.
If you wait until an attack has already started to take action, the criminal(s) might have already had enough time to steal your data, copy your credentials, access your accounts, and put your data and identity in jeopardy.
How to prevent unwanted phone mirroring
 Since prevention is the smartest strategy for dealing with phone mirroring attacks, let’s now take a look at the best preventative measures you should follow to stay safe.
Since prevention is the smartest strategy for dealing with phone mirroring attacks, let’s now take a look at the best preventative measures you should follow to stay safe.
1. Keep your OS and apps updated
It’s important to keep your device’s operating system and all the mobile apps you use up to date, especially those that could mirror your screen.
This is because updates often bring security patches, bug fixes, and improvements to address vulnerabilities in the app or system code, making it much harder for cybercriminals to infiltrate the system and carry out their attacks.
Whenever you see that updates are available, download and install them immediately to keep your device as safe and secure as possible.
2. Avoid third-party app stores
When downloading mobile apps, it’s always best to stick to the official stores: the Google Play Store on Android and the Apple App Store on iPhone.
These official stores have strict systems in place to review the apps they host and verify their safety before making them available for download. They also regularly remove apps that are deemed suspicious or unsafe.
On unofficial app stores and APK websites, security standards are lower, putting you at greater risk of downloading an unsafe or malicious app.
3. Don’t root or jailbreak your phone
Some mobile users may be tempted to root (Android) or jailbreak (iOS) their mobile devices. This is done in order to bypass some of the core system limitations and gain more control and customization capabilities.
However, it’s risky to jailbreak/root a device. You may not only void the warranty, but you could also brick your device or open it up to unauthorized access and malicious attacks.
Rooting or jailbreaking may disable some of the key security features that keep criminals out. This can make it easier for cybercriminals to use malware or other means to mirror your phone.
4. Use strong passwords and screen locks
To guard against people physically setting up screen mirroring on your device, make sure to set strong passwords and screen lock settings using a complex PIN, password, or biometric authentication.
This applies to apps and platforms you use as well. Protect them with complex passwords and two- or multi-factor authentication (2FA and MFA). That way, even if someone is able to mirror your device, they’ll have a much harder time getting into your accounts or stealing your credentials. For those who need a high level of security, your best option is to use a hardware key like YubiKey.
5. Turn off Bluetooth, Wi-Fi, and casting when not in use
It’s generally considered a bad mobile habit to leave features like Bluetooth, NFC, and screencasting turned on when you’re not actively using them.
Bluetooth is required for some types of mirroring, so turning it off can block these outright while also reducing your overall attack surface. Others rely on both devices sharing a Wi-Fi connection, so you may want to disconnect when you don’t need to access the internet.
When this isn’t possible or ideal, look closely at any notification your phone sends you relating to any of these features. Don’t accept Bluetooth or casting requests if you aren’t trying to pair a device yourself.
6. Monitor active devices and permissions
When you’re using screen mirroring or casting or connected to devices via Bluetooth, make sure to regularly check the list of connected devices and remove any you don’t recognize or no longer use.
It’s also a good idea to monitor app permissions, checking to see which apps have the ability to share your display with another device, as well as those that can access other key features of your phone, like its microphone and camera.
7. Avoid public charging stations
Many public places, such as airports, malls, and cafes, now offer public phone charging stations, where you can connect your phone to a USB outlet to recharge the battery.
These are generally perfectly safe, but there are some concerns. Though evidence is severely lacking, it is theoretically possible that sophisticated tools could be created that would enable malicious actors to use USB connections to spread malware or run exploits.
The threat of this is marginal and often exaggerated, but anyone with specific concerns that they could be targeted may want to avoid public charging stations out of an abundance of caution.
8. Use mobile security software
Antivirus software isn’t just for computers and laptops. It’s also important to install and use anti-malware apps on your mobile devices, like phones and tablets, too.
For best results, purchase a trusted, reputable antivirus app, and make sure to run scans on a regular basis to help you spot and remove any malware or suspicious files that might make their way onto your device.
9. Encrypt your connection
Installing a VPN app, like ExpressVPN, on your mobile device is another helpful way to guard against certain types of cyberattacks, like man-in-the-middle attacks, which could be used to gain access to your device’s screen.
A VPN will encrypt your phone’s internet connection, masking your IP address and location. This serves as an effective defense against certain methods cybercriminals use to track your activity or listen in on your connections.
10. Secure your Wi-Fi with a strong password
Cybercriminals may try to gain access to your home Wi-Fi network in order to launch screen mirroring cyberattacks. A weak password will make the initial stage of many attacks much easier for cybercriminals.
Ensure that your Wi-Fi is protected with a strong and complex password, and avoid using public Wi-Fi where possible. If you do need to connect to a public hotspot, use a VPN for encryption and additional security.
FAQ: Common questions about phone mirroring
How can I tell if someone is mirroring my phone right now?
There’s no surefire way to tell if someone is mirroring your phone, but you may notice changes in performance. Your battery might drain faster than normal, for example, or your phone might get hot or seem to operate more slowly and sluggishly. You might also notice that you’re using more data than normal or see unknown apps appearing on your device.
Can a factory reset stop phone mirroring completely?
Yes, a factory reset should be sufficient to stop any unauthorized phone mirroring, as it will delete any malware on your device and erase all data that criminals could use to gain access. Note, however, that you will also lose all of your other apps and data if you do this, so it’s worth making a backup before you begin.
Is it illegal to mirror someone’s phone without permission?
Laws vary around the world, and because technology is evolving so quickly, many countries don’t have specific laws in place to protect citizens from malicious screen mirroring. However, it’s generally considered a major invasion of privacy to mirror a phone without permission. Given that various laws exist to protect people’s privacy and data security, mirroring attacks are likely considered illegal in many countries.
How do I report unauthorized phone surveillance?
It depends on your location. In the U.S., you can contact your local law enforcement agency or file a report with the Internet Crime Complaint Center or Federal Trade Commission. Other countries around the world will have their own cybersecurity authorities to deal with matters like unauthorized phone surveillance or screen mirroring.
How do I protect someone else’s phone from being mirrored?
You can guide them on ways to prevent phone mirroring on their device, such as making sure to install all available updates, disabling screen mirroring when they don’t need to use it, and using mobile security software to guard against malware.
What’s the difference between phone mirroring and spyware?
Phone mirroring is a built-in feature on many modern devices. It can serve useful purposes like displaying video on a larger screen or accessing a device that’s in another room. It can also be used maliciously. Spyware is a general term for malware designed to steal data from victims or gain access to their devices.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN



















Comments
Is it possible for someone to access your phone though the WiFi and then mirror your phone using the same name as your phone so if it comes up on your device list it looks like your phone name? Can someone remotely use my phone and information as a remote connection to access, say, my other friends phones? If so how can I prove its not me to the authority? Please help, this is way out of my comfort zone, but I need proof so that it stops!
I'm having the same issue. The police department has installed a device on the inside of my phone that is constantly recording the back drop or the apps running in the back ground. With this they have gotten the IP of the other devices ( yes multiple) they pull this in info weekly off the phone. I also hired a developer to mirror the phone ( legally) of the person's devices that's doing it to me. I've been dealing with this for 5 or longer months and we are about done. It will be a slam dunk case when we are done and the person is looking at 35 years as of now. We have decided to continue surveillance on them maybe 2 more weeks to assure there is no way they can walk per the prosecutor. It's a hard thing to deal with not to mention how you NEVER have any privacy. Talk to your police department daily if you need to and ask for help. It's out there! I'll pray for you and good luck.