Cybersecurity vulnerabilities explained

Nearly every organization has some weaknesses in its digital defenses. Attackers hunt for cybersecurity vulnerabilities in software, networks, and configurations, as well as chances to exploit human error. To prevent or mitigate these attacks, weak points need to be found and addressed.
Cybersecurity teams and cyber threat hunters can identify and prioritize these vulnerabilities and implement strategies to remediate them. Since it's nearly impossible to avoid vulnerabilities completely, it’s important to understand how to counter them.
What are cybersecurity vulnerabilities?
Cybersecurity vulnerabilities are weaknesses in systems that attackers can use to gain access, steal data, or disrupt operations. Most breaches begin with simple system vulnerabilities that give attackers a window into the system or network. This can happen with any connected system and can involve software, hardware, configurations, credentials, or unintentionally exposed processes.
Sometimes, all it takes is a seemingly minor oversight, like a missed update or an open port; these mistakes can become entry points that facilitate major security incidents.
Vulnerability vs. threat vs. exploit
Vulnerabilities, threats, and exploits are different parts of the same cybersecurity chain. Understanding how they connect makes it easier to see how attacks unfold.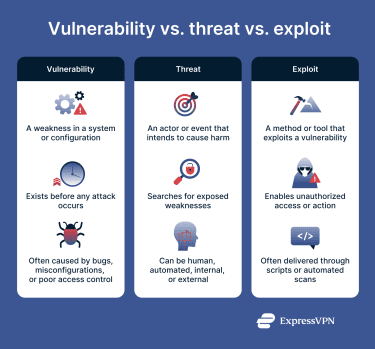
- Vulnerability: This is the weakness. It can be a software bug, a misconfiguration, an exposed service, or a poor access policy. It exists whether anyone has noticed it yet or not.
- Threat: This is the actor or event capable of causing harm. It could be a cybercriminal group or a malicious insider, for example. “Threat” can also refer more broadly to an event like malware activity or automated scanning: a scanning bot that searches the internet for vulnerable systems could be part of a threat actor’s activity.
- Exploit: This is the method used to take advantage of the vulnerability. It’s often a script or tool designed to break in using that specific weakness.
Here’s a simple scenario that illustrates how vulnerabilities, threats, and exploits all work together.
| Scenario element | Classification |
| A missing patch | Vulnerability |
| A cybercriminal group (or its scanning bot) searching for outdated servers | Threat |
| The script used to break in via the unpatched flaw | Exploit |
Why cybersecurity vulnerabilities matter
Cybersecurity vulnerabilities don’t stay contained inside IT systems. When left unaddressed, they spill into other connected systems, including operations, finance, compliance, and more. A single overlooked gap can trigger consequences that affect the entire organization.
Consequences of exploited vulnerabilities can include:
- Operational disruptions: Attackers often use network vulnerabilities or stolen credentials to shut down systems or block access. Production stops and services go offline. What’s more, damage control can divert time and resources that should be supporting business growth.
- Financial losses: Breaches can lead to direct theft, fraud, ransomware demands, and costly recovery efforts. Organizations then spend heavily on threat hunting, forensic investigations, legal support, and rebuilding systems.
- Eroded customer confidence: Customers expect their data to stay protected. A breach breaks that trust quickly and publicly, especially in sectors like finance and healthcare.
- Regulatory penalties: Data protection laws like the General Data Protection Regulation (GDPR) require strict security controls. When vulnerabilities lead to exposure, organizations face fines, audits, and compliance investigations.
- Competitive disadvantage: Security incidents can weaken an organization’s reputation in the market; clients and partners prefer organizations that demonstrate stronger protection practices. What’s more, attackers tend to revisit environments that they know are easy to exploit.
Common types of cybersecurity vulnerabilities
There are many kinds of cybersecurity vulnerabilities, and they differ based on what they target.
Software vulnerabilities
Software vulnerabilities come from bugs or design flaws in operating systems and applications. Attackers use these weaknesses to inject and run unauthorized code or gain access privileges. They may then stay in the system and wait for the right time to attack.
For example, a company dashboard that runs on an outdated version of its framework may contain a known flaw. Attackers can use that flaw to access the server behind the dashboard and move deeper into the network.
Some software vulnerabilities are especially severe. Remote code execution (RCE) flaws allow attackers to execute arbitrary code on a target system from a remote location, often leading to full compromise. Zero-day vulnerabilities are flaws unknown to the vendor and without an available patch, which makes them particularly dangerous.
Many software vulnerabilities become public once vendors release patches. When organizations delay updates, they leave well-known vulnerabilities exposed, which is risky because attackers can run automated scans to identify the systems that lack the relevant updates.
Some organizations delay updates due to operational concerns or compatibility worries, but regular patch management and continuous scanning are vital to help identify unsupported or outdated applications before attackers can do so.
Network vulnerabilities
Network vulnerabilities appear when ports, firewalls, routing rules, or segmentation aren’t properly configured. An exposed service or weak internal separation can give attackers a direct path into sensitive systems.
For example, a remote management port left open to the internet may be discovered by attackers using automated scanning tools. They can then try default credentials or known exploits to enter the network.
Without proper segmentation and monitoring, a single network vulnerability can expose multiple systems at once. Attackers use these openings to move laterally across the environment.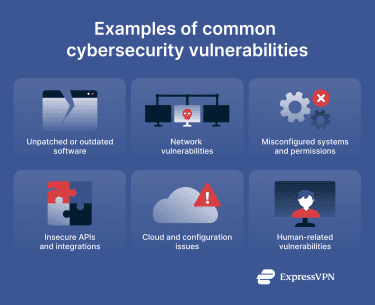
Application and web vulnerabilities
The code, design, or setup of software and websites often contains vulnerabilities. These weaknesses can allow attackers to steal data or take control of systems.
APIs handle data exchange and backend operations, but they often receive less security attention than user-facing systems. When APIs lack proper authentication or monitoring, they can expose sensitive data directly. For example, a web form that doesn’t properly validate input can allow an attacker to insert malicious code into a database query. This may give them access to sensitive records stored behind the application.
Common API security gaps include:
- Broken authentication that fails to verify users.
- Excessive data exposure through responses.
- Lack of rate limiting that allows abuse.
- Insufficient logging that hides misuse.
Data protection failures can also create serious application vulnerabilities, especially when encryption is missing or improperly implemented. Common examples include:
- Data transmitted without encryption, allowing attackers to intercept sensitive information.
- Weak encryption algorithms that attackers can break or bypass.
- Improper key management that exposes encryption keys to unauthorized access.
- Sensitive data stored in plaintext instead of being encrypted.
Attackers actively scan websites, APIs, and backend services for these weaknesses. Once discovered, application vulnerabilities can expose sensitive data or provide access to deeper parts of the environment.
Cloud and configuration vulnerabilities
Cloud vulnerabilities are typically caused by misconfigurations rather than flaws in the cloud platform itself. Public storage, exposed virtual machines, and excessive permissions are common examples.
Sometimes, a cloud storage bucket might be accidentally set to public access during deployment. Attackers can then find it through automated scans and download sensitive files without needing to break into the network.
What’s more, cloud environments change quickly as teams deploy new services. This means that these configuration mistakes, if not carefully supervised, can remain exposed for extended periods.
Human-related vulnerabilities
People play a significant role in cybersecurity risk. While they themselves aren’t “vulnerabilities” in the technical sense, their behavior and decision-making can create or expose weaknesses in systems that attackers can then exploit. For example, employees can be targeted with phishing emails that aim to steal their credentials, and if they haven’t been trained to recognize the red flags, this kind of attack can provide access to a system.
Many cybersecurity incidents start with attackers taking advantage of gaps in awareness or protective controls rather than exploiting flaws in software code. Common human-related weaknesses include:
- Weak passwords: Choosing simple or reused credentials that are easy to guess.
- Missing multi-factor authentication (MFA): Failing to add an extra layer of verification, which increases the impact if credentials are stolen.
- Unpatched devices: Leaving laptops or phones without updates that fix known issues.
- Falling for phishing attempts: Clicking on malicious links or entering credentials into fake pages.
- Malware installation: Downloading infected files or applications without realizing it.
Attackers rely heavily on social engineering because it targets behavior rather than software. An employee who believes they’re responding to IT support or a trusted vendor can unknowingly hand over access to an attacker. The vulnerability isn’t the person; it’s the absence of safeguards like strong authentication and cybersecurity training that reduce human error.
What causes cybersecurity vulnerabilities?
Cybersecurity vulnerabilities exist at multiple layers of modern systems. Some originate in software and infrastructure, while others stem from how systems are configured or used. Understanding both the technical types of vulnerabilities and the underlying causes helps explain how they emerge and persist. While vulnerabilities appear in technical systems, their root causes are often tied to operational and organizational challenges.
| Root causes | Impact |
| Human error and behavior | Configuration mistakes, weak credential practices, and successful phishing attacks can expose systems even when strong technical controls exist. |
| Poor security hygiene | Delayed patching, excessive access permissions, or ignored security alerts can leave known vulnerabilities exposed long after fixes are available, making a system vulnerable to exploitation. |
| System complexity and rapid change | Modern environments include cloud services, APIs, remote access systems, and third-party integrations. As infrastructure evolves, maintaining consistent security across every component becomes more difficult. |
| Limited visibility and monitoring | Without continuous asset discovery and vulnerability scanning, exposed systems or outdated software may remain unnoticed. |
| Resource constraints and operational priorities | Security improvements are sometimes delayed to avoid operational disruption or due to limited staffing, which can extend exposure to attacks that exploit known vulnerabilities. |
How cybersecurity vulnerabilities are identified and managed
Cybersecurity vulnerabilities rarely appear without warning. Most can be found through systematic evaluation, continuous monitoring, and structured testing. That said, there are undiscovered zero-day vulnerabilities, too, and this makes proactive detection and rapid response even more critical.
Modern vulnerability management combines automated discovery with human analysis. Organizations use scanning tools to identify known weaknesses, then apply risk context and threat intelligence to decide which issues require immediate action and which can be scheduled for later remediation.
Vulnerability scanning and assessments
Vulnerability assessments provide continuous visibility into systems rather than a one-time review. They focus on discovery and analysis; the goal is to understand where vulnerabilities exist and how serious they are.
The process typically includes:
- Asset discovery: Identifying all devices, systems, and applications in the environment.
- Automated scanning: Detecting known software vulnerabilities and configuration issues.
- Risk evaluation: Determining which vulnerabilities pose the greatest threat.
- Prioritization: Focusing remediation efforts on the highest-risk exposures.
- Remediation planning: Defining steps to resolve vulnerabilities and reduce exposure.
This process helps organizations maintain visibility into their environments and reduce their attack surface over time. Because environments constantly change, assessments should be repeated regularly to remain effective.
Security audits and penetration testing
Automated scans identify many vulnerabilities, but they don’t provide a complete picture. Organizations also need deeper evaluations that examine how systems are configured, how controls function, and how attackers might actually break in. Security audits and penetration testing serve this purpose, but they approach it in different ways.
- Security audit: Reviews systems, configurations, and policies to identify security weaknesses and compliance gaps. Audits focus on whether controls are properly implemented and aligned with security standards and internal requirements.
- Penetration test: Simulates a real attack to actively exploit vulnerabilities and determine how far an attacker could go. Pen testers use the same techniques as threat actors, but within a defined scope and timeframe. Penetration tests are limited in coverage, so they might not find every vulnerability, but they give valuable insights into which weaknesses could be exploited and how defenses hold up in attack scenarios.
In other words, security audits provide visibility into structural weaknesses and policy gaps, while penetration tests show how those weaknesses could be used in practice. They work together to help organizations understand both where vulnerabilities exist and how dangerous they are in real-world scenarios.
Monitoring, threat intelligence, and continuous improvement
Active monitoring provides real-time context so organizations can understand which weaknesses matter most.
Security teams track things like:
- Emerging exploits and ransomware campaigns.
- Publicly released exploit code.
- Newly exposed internet-facing services.
- Suspicious behavior attempting to use known vulnerabilities.
Threat intelligence helps distinguish theoretical risk from active danger. For example, a severe vulnerability may require less urgency if no exploit exists, while a moderate flaw may demand immediate action if attackers are actively weaponizing it. Endpoint detection tools and attack-surface monitoring solutions can also reveal when attackers attempt to exploit weaknesses, allowing organizations to respond before damage occurs.
All of these insights then feed into a continuous improvement cycle.
Prioritizing and remediating vulnerabilities
As mentioned above, not all vulnerabilities carry the same level of risk. Some are difficult to exploit or have limited impact, while others allow attackers to gain full control of systems. Prioritization helps security teams focus on the most dangerous exposures first.
The Common Vulnerability Scoring System (CVSS) provides a standard way to measure severity. It assigns each vulnerability a score from 0.0 to 10.0 based on how easy it is to exploit and how much damage it could cause.
Severity levels include:
| CVSS score | Severity rating | What it means |
| 0.0 | None | No meaningful security impact |
| 0.1–3.9 | Low | Limited risk and difficult to exploit |
| 4.0–6.9 | Medium | Moderate risk with potential system impact |
| 7.0–8.9 | High | Serious risk that attackers can exploit more easily |
| 9.0–10.0 | Critical | Severe risk that can lead to full system compromise |
While CVSS measures technical severity, real-world risk also depends on exposure and active threat activity. Security teams also use the Common Vulnerabilities and Exposures (CVE) database, maintained by MITRE and the National Vulnerability Database. These databases provide detailed information about known vulnerabilities, affected systems, and available fixes.
Once vulnerabilities are prioritized, organizations take steps to reduce or eliminate exposure. Common remediation measures include:
- Applying software patches and updates.
- Correcting misconfigurations.
- Strengthening access controls and authentication.
- Removing unnecessary services or exposed systems.
After remediation, systems are reassessed to confirm the vulnerability has been resolved and hasn’t reappeared elsewhere.
Best practices for reducing cybersecurity vulnerabilities
Cybersecurity vulnerabilities can’t be fully eliminated, but organizations can significantly reduce their exposure by following consistent security practices. These measures focus on closing known gaps, limiting access, and preparing for incidents before they escalate.
Regular updates and patch management
As discussed above, keeping software updated is vital to fix known vulnerabilities and strengthen system defenses. When updates are delayed, attackers can exploit weaknesses that already have available fixes.
Automatic updates help ensure patches are installed as soon as they become available. Organizations should also avoid using unsupported or end-of-life software, since vendors no longer provide security fixes for those systems. Updates should always come directly from trusted vendor sources to avoid installing malicious software disguised as legitimate updates.
Strong access controls and authentication
Access controls ensure that only authorized users can reach sensitive systems and data. Without proper restrictions, attackers who gain access to one account may be able to move freely across the environment.
Strong access control practices include:
- Least privilege access: Giving users only the permissions they need to perform their roles.
- MFA: Requiring additional verification beyond passwords.
- Regular access reviews: Removing permissions that are no longer necessary.
- Authentication monitoring: Detecting suspicious login attempts or unusual access patterns.
Zero-trust security models strengthen this approach by verifying every access request, regardless of where it originates from.
Employee training and awareness
Awareness training helps users recognize phishing attempts and other common cyberattack methods.
Effective training programs go beyond one-time instruction. Regular phishing simulations and ongoing education help employees identify threats in real-world situations. These programs also help organizations measure risk and identify areas that need improvement. When employees understand how attacks work, they’re less likely to serve as an entry point for attackers.
Incident response and recovery planning
Even with strong defenses, incidents can still occur. Incident response planning ensures organizations can contain threats quickly and restore operations with minimal damage.
A structured response process includes:
- Preparation: Identifying critical systems and defining response procedures.
- Detection and analysis: Monitoring systems and identifying suspicious activity.
- Containment and recovery: Isolating affected systems, stopping the spread of the threat, restoring clean data from backups, and safely returning systems to operation.
- Post-incident review: Analyzing what happened and improving future responses.
Organizations that prepare for incidents in advance can respond faster, reduce damage, and prevent similar vulnerabilities from being exploited again.
FAQ: Common questions about cybersecurity vulnerabilities
What are the main types of cybersecurity vulnerabilities?
The main types of cybersecurity vulnerabilities include software vulnerabilities, network vulnerabilities, application vulnerabilities, cloud misconfigurations, and identity and access weaknesses. Each affects different parts of an environment and requires specific security controls to manage.
What is the biggest cybersecurity vulnerability?
Human error is one of the leading cybersecurity risks. Phishing, weak passwords, and poor security habits often give attackers easy access. Unpatched software is also a major vulnerability, because attackers quickly exploit known flaws.
What is vulnerability management in cybersecurity?
Vulnerability management is the continuous process of finding, prioritizing, and fixing security weaknesses. It involves regular scanning, risk evaluation, remediation, and verification to maintain a strong security posture.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN