What is HIPAA compliance? What you need to know

Every time you visit a doctor, fill a prescription, or use a telehealth app, sensitive information about your health is collected and stored. If that data isn’t handled properly, it can lead to loss of privacy and expose you to issues like discrimination or identity theft. The Health Insurance Portability and Accountability Act (HIPAA) sets the U.S. standards that protect this data.
While HIPAA is often discussed as a regulatory requirement, at its core, it’s a privacy law designed to protect individuals from the long-term risks that come with exposing sensitive health information. Understanding HIPAA through this lens helps clarify why securing personal data matters far beyond healthcare settings.
In this guide, we’ll explain what HIPAA requires and define what counts as protected health information (PHI). You’ll also learn how healthcare providers and other covered entities follow HIPAA requirements to keep medical records secure and maintain patient privacy.
The full meaning of HIPAA
HIPAA is a U.S. federal law that sets national standards to protect sensitive patient information and improve the portability and continuity of health insurance coverage.
Its core provisions include:
- The Privacy Rule: Governs how all forms (written, oral, electronic) of health information can be used or shared.
- The Security Rule: Sets specific standards for safeguarding electronic health data.
- The Breach Notification Rule: Requires organizations to report incidents in which PHI is accessed, used, or disclosed improperly.
Why HIPAA was enacted: Protecting patient data in the digital age
HIPAA was enacted in 1996 for several reasons. The law addressed concerns about “job lock,” a situation in which people stayed in a job mainly to keep their health insurance.
Before HIPAA, insurers could deny coverage or impose long waiting periods for pre-existing conditions when someone changed employers. HIPAA limited these practices, giving workers more freedom to switch jobs without risking gaps in coverage. The Affordable Care Act (ACA), enacted in 2010, expanded these protections and now supersedes them.
HIPAA also aimed to improve the efficiency and effectiveness of the healthcare system by standardizing the electronic transmission of health information. This reduced administrative costs and helped ensure that the additional burden of compliance would not be passed on to consumers or employers.
Finally, HIPAA responded to new risks for patient privacy caused by the growing adoption of electronic health records and public concern over the misuse of medical data.
Who needs to comply with HIPAA regulations?
HIPAA only applies to certain organizations. These include healthcare providers that send health information electronically, health plans such as insurance companies and employer group plans, government programs like Medicare and Medicaid, and healthcare clearinghouses that process health information into standard electronic formats.
In addition, HIPAA applies to business associates of covered entities. These are individuals or organizations that access PHI while carrying out work for a covered entity. Examples include a company that processes health insurance claims, a consultant who evaluates hospital operations, or a lawyer who advises a health plan.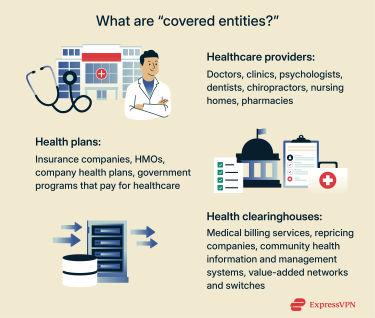
Key HIPAA rules explained
What is the HIPAA Privacy Rule, and how does it work?
The Privacy Rule is the heart of HIPAA’s mission: ensuring that individuals maintain control over who can see their most sensitive personal information. It sets the framework for how covered entities and business associates must handle patients’ medical and personal data. Its goal is to ensure that privacy is maintained while still allowing information to be used for necessary healthcare activities. It’s also the provision that governs the use of PHI for research.
The rule defines what kinds of health information are considered sensitive and establishes boundaries on when and how that information can be shared. For example, patients’ information may be disclosed for treatment, payment (such as billing), or other routine healthcare functions. Other purposes, such as marketing or some disclosures to employers, typically require the individual’s written authorization unless a specific permission in the HIPAA Privacy Rule applies (for example, certain public health or workers’ compensation disclosures).
It also gives patients rights over their own health information. For example, individuals can request access to their records from their healthcare providers or health plans and ask for corrections.
How the HIPAA Security Rule protects electronic PHI (ePHI)
Because healthcare data is one of the most targeted types of personal information in cyberattacks, the Security Rule establishes the technical safeguards needed to protect digital privacy. It sets national standards to safeguard health information when it’s held or transmitted electronically. Its goal is to ensure the confidentiality, integrity, and availability of that data.
At its core, this rule requires that covered entities and their business associates put in place reasonable and appropriate safeguards under three broad categories:
- Administrative safeguards: Guide policies and workforce practices.
- Physical safeguards: Protect facilities and equipment.
- Technical safeguards: Help secure electronic access and transmission of ePHI.
HIPAA Breach Notification Rule: When and how to report incidents
Breach notification requirements exist to prevent individuals from being left in the dark when their private medical information may have been exposed. The Breach Notification Rule establishes data breach reporting requirements for covered entities and their business associates, specifying what they must do when unsecured PHI is accessed, used, or disclosed improperly.
When a breach of unsecured health information occurs, organizations must act without “unreasonable delay” and no later than 60 days. They are required to notify anyone who has been affected by a breach. If the breach has affected more than 500 people in a state or jurisdiction, they also need to notify major media outlets serving the area. In every case, they must inform the U.S. Department of Health and Human Services (HHS).
The rule also requires organizations to keep records proving they’ve sent said notifications or, when applicable, that a breach did not occur.
What is protected health information (PHI)?
PHI matters because it’s uniquely sensitive. Unlike passwords or credit card numbers, medical details can’t be “reset” once they’re exposed. In the following sections, we define PHI, explain what counts as PHI, and provide tips for safeguarding it.
A clear definition of PHI under HIPAA
PHI is individually identifiable health information, in any form or medium, held or transmitted by a covered entity or business associate. It includes details about a person’s past, present, or future health, the care they receive, or payments for that care.
18 identifiers HHS considers especially identifying
- Name
- Geographic subdivisions smaller than a state
- All elements of dates related to an individual (birth, admission, discharge, death) except year.
- Telephone numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- License or certificate numbers
- Vehicle identifiers
- Device identifiers
- Web URLs
- IP addresses
- Biometric data (fingerprints, voiceprints)
- Face photos or similar images
- Any other unique identifier
When exposed, each of these identifiers can be misused for identity theft, insurance fraud, discrimination, and long-term reputational harm, which is why healthcare data remains one of the most valuable targets for cybercriminals.
How to safeguard PHI in your organization
Protecting PHI goes beyond meeting regulatory requirements; it helps prevent privacy harms that can affect people long after a breach occurs. The HIPAA Security Rule sets broad standards rather than prescribing exact technical measures, giving organizations flexibility to implement safeguards that are reasonable and appropriate for their size, operations, and risk environment.
The HHS Office of Inspector General’s (OIG) General Compliance Program Guidance (GCPG) outlines seven key elements that support overall healthcare compliance and security:
- Written policies and procedures: Establish clear rules for handling PHI and responding to potential violations.
- Compliance officer and committee: Assign responsibility for oversight and enforcement of policies.
- Training and education: Ensure staff understand their responsibilities for protecting PHI.
- Effective lines of communication: Provide channels for employees to ask questions or report concerns.
- Enforcement of standards: Apply consistent disciplinary measures for violations and incentives for compliance.
- Risk assessment, auditing, and monitoring: Regularly review practices to identify and correct gaps in PHI protection.
- Response and prevention: Investigate incidents, take corrective action, and adjust policies to prevent recurrence.
HIPAA compliance requirements
Below, we outline the administrative, technical, and physical safeguards required under the HIPAA Security Rule, as well as the documentation obligations.
Note: This article is for general information purposes only. It is not intended to be used as legal advice. Always consult with a professional to build and maintain a compliant HIPAA program.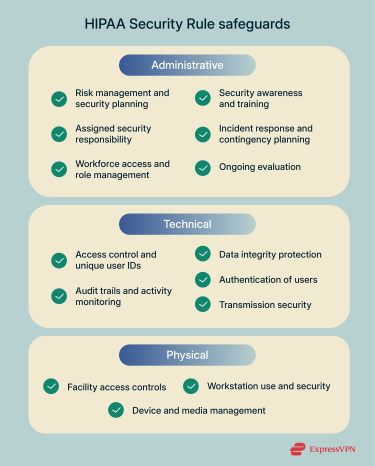
Administrative safeguards: Policies, training, and procedures
- Security management process: Implement policies and procedures to prevent, detect, contain, and correct security violations. This includes risk analysis and management, having a sanction policy for workforce members, and the periodic review of information system activity.
- Assigned security responsibility: Designate a security official responsible for developing and implementing the organization’s security policies and procedures.
- Workforce security: Ensure workforce members have appropriate access to ePHI based on their roles, and supervise and manage access accordingly.
- Information access management: Authorize access to ePHI only as needed for each person’s role, following the minimum necessary standard.
- Security awareness and training: Train all workforce members on security policies and procedures.
- Security incident procedures: Establish processes to identify, respond to, and document security incidents, and mitigate any harmful effects.
- Contingency planning: Prepare for emergencies or disruptions that might affect ePHI, including data backup, restoration, and continuity of critical operations.
- Evaluation: Periodically review how well security policies and procedures are working and update them when there are changes in the environment or operations.
Technical safeguards: Encryption, access controls, and more
- Access control: Implement unique user IDs, emergency access procedures, implement automatic logoff, and a way to encrypt and decrypt ePHI.
- Audit controls: Maintain hardware, software, or procedural mechanisms to record and examine activity in systems that store or transmit ePHI.
- Integrity: Implement policies and procedures to protect ePHI from improper alteration or destruction, including mechanisms to verify that data has not been tampered with.
- Authentication: Use measures to verify that anyone accessing ePHI is who they claim to be.
- Transmission security: Protect ePHI when it’s transmitted over networks, taking measures to guard against interception or alteration in transit.
Physical safeguards: Securing healthcare environments
- Facility access controls: Implement policies and procedures to limit physical access to buildings or areas where ePHI is stored, while allowing authorized personnel to access them as needed.
- Workstation use and security: Define proper use and attributes of workstations and devices that access ePHI and implement measures to prevent unauthorized access.
- Device and media controls: Establish policies for the receipt, removal, disposal, and reuse of hardware and electronic media containing ePHI, including proper destruction and tracking.
Required HIPAA documentation and record-keeping practices
HIPAA requires covered entities and business associates to maintain written policies, procedures, and records that demonstrate compliance with the Privacy, Security, and Breach Notification Rules. All required documentation must generally be kept for at least 6 years from the date it was created or last in effect.
The Privacy Rule requires regulated entities to maintain records describing how they carry out privacy protections, including:
- Written privacy policies and procedures: Documents must describe how the entity protects individuals’ health information and complies with the Privacy Rule, updated whenever practices change.
- Notice of Privacy Practices and acknowledgments: A privacy practices notice must be delivered, and covered entities must make a good faith effort to obtain written acknowledgment and receipt of the document or the reason it wasn’t obtained.
- Complaint procedures and records: Covered entities must show how individuals can submit complaints about privacy practices and document complaints received and their resolution, if any.
- Designation of privacy personnel: Covered entities must appoint a privacy official responsible for implementing policies and a contact person or office for receiving complaints and providing information on privacy practices.
- Special-use documentation: Researchers must obtain approval from the Institutional Review Board (IRB) or Privacy Board in circumstances such as research conducted without individual authorization.
- Accounting of disclosures: Individuals have the right to an accounting of disclosures of PHI made by a covered entity, as outlined in 45 Code of Federal Regulations (CFR) section 164.528.
The Security Rule requires written policies, procedures, and evidence of how an entity protects ePHI. Required documentation includes:
- Policies and procedures: All administrative, technical, and physical safeguards must be kept current and available to responsible personnel.
- Records of actions, activities, and assessments: Risk analyses, risk management plans, periodic security evaluations, workforce training, sanctions, and documentation of security incidents and their outcomes must be maintained.
- Decisions on flexible security safeguards: Documentation when a recommended safeguard is not used and what alternative measures were implemented to provide equivalent protection must be maintained.
- Business associate agreements: Documentation of the required assurances that a business associate will safeguard ePHI.
The Breach Notification Rule requires covered entities to keep records showing how they evaluated and responded to potential breaches of unsecured PHI. Required documentation includes:
- Documentation demonstrating compliance: This includes proof that notifications were made or records showing why notification was not required.
- Breach response documentation: This includes items such as breach policies and training, incident investigations and risk assessments, records of notifications sent, mitigation steps, and sanctions where applied.
Common HIPAA violations healthcare providers should avoid
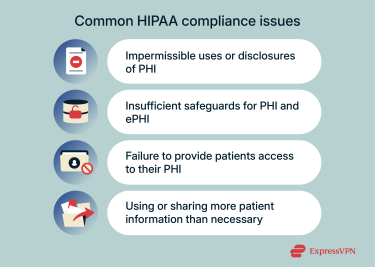 Most HIPAA violations stem from privacy failures, like unauthorized access, oversharing, or inadequate protection of highly sensitive personal data. According to data from the HHS Office for Civil Rights (OCR), the most frequent compliance issues involve:
Most HIPAA violations stem from privacy failures, like unauthorized access, oversharing, or inadequate protection of highly sensitive personal data. According to data from the HHS Office for Civil Rights (OCR), the most frequent compliance issues involve:
- Impermissible uses or disclosures of PHI: HIPAA protects patients’ health information by limiting how it can be accessed and shared. Violations occur when employees view or disclose PHI without authorization or outside permitted purposes. OCR identifies this as one of the most frequently reported HIPAA violations.
- Insufficient safeguards for PHI and ePHI: HIPAA requires covered entities to protect both physical and electronic health information from unauthorized access or loss. In 2022, OCR found that common violations can involve weak access controls, skipped risk assessments, and failure to implement appropriate security measures to mitigate risk.
- Failure to provide patient access to their PHI: Under HIPAA, patients have the right to review and obtain copies of their medical records. OCR’s Right of Access initiative has resulted in enforcement actions for failing to provide records or providing them late.
- Using or sharing more patient information than necessary: HIPAA’s “minimum necessary” standard requires that only the information needed for a specific purpose be used or disclosed.
Insider threats: Why internal users are a risk
Insider threats are a serious consideration for healthcare organizations. Employees, contractors, and other trusted internal users already have legitimate access to PHI and ePHI, which increases the chances of accidental misuse or mishandling.
Malicious insiders pose an even greater risk. If they deliberately exploit weak points to steal or damage information, their actions can go undetected, potentially leading to larger breaches and more severe consequences than external attacks.
HHS and the Cybersecurity and Infrastructure Security Association (CISA) recommend mitigating this risk by giving each employee access only to the data they need for their job, monitoring for unusual account activity, and enforcing strong authentication. Regular training also helps staff understand their responsibilities when handling PHI and ePHI. Combined, these measures make it harder for insider misuse to occur and easier to detect early if it does.
HIPAA compliance best practices
Best practices exist to satisfy regulators and reduce the likelihood that sensitive patient information is exposed, stolen, or misused. In the sections below, we outline the key steps, tools, and training practices that HHS, Office of the National Coordinator for Health Information Technology (ONC), and the National Institute of Standards and Technology (NIST) recommend that organizations use to maintain HIPAA compliance.
A step-by-step HIPAA compliance checklist
- Identify applicable HIPAA rules: Determine whether your organization is a covered entity or business associate and which rules (Privacy, Security, Breach Notification) apply.
- Designate a privacy and security official: Assign responsibility for implementing and overseeing HIPAA policies, training, and incident management. HHS says that this can be the same person, but doesn’t have to be. OIG suggests that you might want to designate a compliance officer or committee, but this isn’t mandatory.
- Conduct a Security Rule risk analysis: Identify ePHI, assess vulnerabilities and threats, and document findings.
- Create written policies and procedures: Cover all applicable standards for PHI use, including (but not limited to): minimum necessary standards, access controls, device/media handling, sanctions, contingency plans, and incident response.
- Establish processes for patient rights: Include procedures for access, amendments, accounting of disclosures, and restrictions on PHI use.
- Develop a risk management plan: Apply administrative, physical, and technical safeguards to address identified risks.
- Provide workforce training: Train all individuals who are under the direct control of the covered entity (paid or not) on HIPAA policies, security requirements, and breach reporting.
- Manage business associate relationships: Execute HIPAA-compliant agreements outlining PHI use, safeguards, subcontractor requirements, and breach reporting.
- Implement breach detection and response procedures: Detect, investigate, document, and report breaches according to HIPAA requirements.
- Monitor and audit regularly: Review security measures, audit system activity, test contingency plans, and update safeguards as required.
- Maintain documentation for at least six years: Keep records of policies, procedures, training, risk analyses, risk management actions, breaches, and business associate agreements.
Recommended tools and software for HIPAA compliance
Here are some useful tools and software that may be helpful for ensuring that your organization is HIPAA compliant:
- Security Risk Assessment (SRA) tool: A free risk‑assessment application developed by ONC and OCR to guide small and medium-sized organizations through HIPAA Security Rule risk analyses.
- HIPAA audit protocol: A detailed checklist created by OCR that outlines requirements in the Privacy, Security, and Breach Notification Rules and explains what documentation or evidence auditors look for. It’s a self-audit guide aligned with official enforcement standards, but it’s not exhaustive, and OCR does not provide compliance certification.
- Cybersecurity Framework (CSF): A federal cybersecurity framework published by NIST that helps organizations identify, protect against, detect, respond to, and recover from cyber threats. While not healthcare-specific, it can help guide Security Rule compliance.
How to train your team on HIPAA requirements
 To address the risk of insider threats, the HHS OIG’s General Compliance Program Guidance recommends that healthcare organizations establish a compliance officer and a compliance committee. These roles are responsible for developing, coordinating, and overseeing training programs tailored to the organization’s specific risks and operations.
To address the risk of insider threats, the HHS OIG’s General Compliance Program Guidance recommends that healthcare organizations establish a compliance officer and a compliance committee. These roles are responsible for developing, coordinating, and overseeing training programs tailored to the organization’s specific risks and operations.
The training program should cover the organization’s compliance policies, federal and state rules, and role-specific responsibilities, including the proper handling of PHI and ePHI. Training should also explain the compliance officer’s role, the function of the compliance committee, how staff can ask questions or report concerns safely, the organization’s nonretaliation policy, and how policies are applied fairly and consistently.
All workforce members should participate in training, which should be held regularly and updated whenever there are new risks, policy changes, or audit findings. Training should be mandatory with consequences for noncompliance.
Finally, the compliance officer should seek opportunities to provide education on compliance topics and risks outside of formal annual training. This can include newsletters, briefings during team meetings, updates on internal communication platforms, or short refresher sessions, helping staff stay vigilant throughout the year.
HIPAA enforcement and penalties
Penalties exist to enforce compliance and protect individuals whose privacy might be jeopardized by unauthorized access or data loss. Below, we take a quick look at how HIPAA violations are enforced and some real-world cases to highlight key lessons for organizations.
Civil and criminal penalties for HIPAA violations
OCR enforces HIPAA by conducting compliance reviews, investigating complaints, and performing educational outreach to foster compliance.
When OCR identifies noncompliance, it may first work with the organization to achieve voluntary compliance or negotiate a corrective action plan or resolution agreement. If those measures are unsuccessful, or if the violation warrants a stronger response, OCR can impose civil money penalties.
For civil penalties, OCR can impose fines up to more than $2 million per violation, depending on the level of culpability. Violations committed unknowingly or with reasonable cause generally receive lower penalties, whereas violations due to willful neglect are penalized more severely. The penalty amounts are revised each year to reflect cost-of-living adjustments.
Criminal penalties apply to individuals who knowingly obtain or disclose PHI in violation of HIPAA and can result in a fine of up to $50,000 and 1 year of imprisonment. The penalty may be increased for offenses committed under false pretense to $100,000 and 5 years of imprisonment. Finally, offenses committed with the intent to sell, transfer, or use the information for commercial advantage, personal gain, or malicious harm can carry fines up to $250,000 and imprisonment for up to ten years.
FAQ: Common questions about HIPAA
What qualifies as a HIPAA violation?
Violations happen when a covered entity or business associate mishandles protected health information (PHI). Examples include unauthorized access or disclosure, inadequate safeguards, failing to give patients access to their records, or sharing more information than necessary. Violations can occur accidentally, through carelessness or oversight, or intentionally, when someone deliberately misuses protected health information.
What are the three primary HIPAA rules?
The main rules are: the Privacy Rule, the Security Rule, and the Breach Notification Rule. The Privacy Rule controls how protected health information (PHI) is used and shared. The Security Rule protects electronic PHI with administrative, physical, and technical safeguards. And the Breach Notification Rule requires prompt reporting of unauthorized access or disclosure. Together, they set the standards for safeguarding patient information.
What types of data are protected under HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) protects any health information linked to an individual, called protected health information (PHI). This includes medical histories, treatment details, and payment information, tied to identifiers like names, addresses, dates, Social Security numbers, device IDs, biometrics, or photos. If it can identify a person and relates to their health, it’s covered.
Who enforces HIPAA and how?
The Health Insurance Portability and Accountability Act (HIPAA) is enforced by the Department of Health and Human Services (HHS) Office for Civil Rights (OCR), which conducts compliance reviews, investigates complaints, provides guidance, and refers criminal cases to the Department of Justice (DOJ). Violations can result in civil fines and, in cases of deliberate misuse, criminal penalties, including imprisonment. OCR may also require corrective action plans to ensure future compliance.
Can HIPAA rules be legally bypassed?
No, the rules generally cannot be waived or bypassed, but limited exceptions exist. For example, during a public health emergency, the U.S. Department of Health and Human Services (HHS) Secretary can temporarily loosen certain Privacy Rule requirements for specific providers and locations. And, in research, an Institutional Review Board or Privacy Board may authorize limited use or disclosure of protected health information (PHI) without patient permission. These exceptions are narrowly defined, temporary, and strictly regulated, so compliance with the Health Insurance Portability and Accountability Act (HIPAA) remains the default obligation.
You should also note that there are provisions for routine use and disclosure of PHI without authorization. These are not bypasses; they are a core part of the Privacy Rule.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN