What is EDR in cybersecurity? The ultimate breakdown
A security breach isn’t always obvious. Instead, small signals can show up first: an unusual process, an unauthorized login, or a device behaving differently. Endpoint detection and response (EDR) tools help teams spot suspicious endpoint behavior, investigate what happened, and respond quickly to contain attacks.
In this guide, we’ll cover what EDR is, how it compares to traditional security tools, and how to pick the right EDR solution.
What is EDR?
EDR is security software that continuously monitors endpoint activity to detect and respond to threats. It emphasizes endpoint telemetry and behavioral detection (alongside other detection methods) to support investigation and remediation.
Security teams, particularly defensive blue teams, use EDR because modern attacks frequently bypass perimeter defenses. A single compromised device can serve as an entry point for attackers to access other systems. The risk often grows as the number of endpoints grows, whether it’s an enterprise or a small business.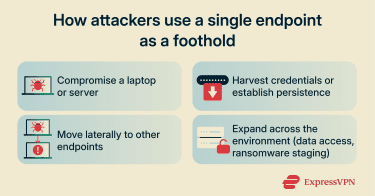
Unlike traditional signature-only approaches, EDR can help detect new and advanced threats, such as ransomware that uses legitimate tools or attackers moving laterally with stolen credentials. Many teams integrate this approach with zero-trust principles, which assume threats may already be inside the network.
EDR also enables effective investigation and threat response. Because endpoint activity (such as process activity and sign-in events), teams can better understand how attackers entered and how far they’ve spread. EDR can help prioritize alerts, isolate compromised devices to limit lateral movement, and terminate malicious processes. Many platforms support automated or rules-based response actions to quickly contain threats.
How does EDR compare to traditional security tools?
The key differences between EDR and other security solutions come down to scope, function, and who operates them.
EDR vs. traditional antivirus software
Traditional antivirus software often focuses on detecting known malware (for example, via signatures), typically by scanning files before or as they run. For example, it might detect and quarantine a Trojan when someone tries to run an infected installer.
EDR addresses a different stage of the attack lifecycle. It's designed to detect threats that slip past preventative controls and gain a foothold on an endpoint. Instead of focusing mainly on pre-execution file scanning, EDR emphasized continuous endpoint telemetry monitoring to help teams detect, investigate, and contain suspicious activity within the environment.
EDR vs. XDR
Extended detection and response (XDR) tools have a broader scope than EDR. They typically pull telemetry across endpoints and other layers, such as network sources, email, identity, applications, and cloud workloads.
Instead of monitoring each security layer separately, XDR correlates signals and alerts across tools. For example, if an attacker sends a phishing email, steals credentials, and then compromises an endpoint, XDR shows all three steps together, supporting a coordinated investigation and response.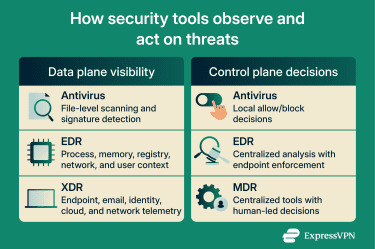
EDR vs. MDR
Managed detection and response (MDR) is a service model rather than a technology. MDR providers handle monitoring, threat investigation, and response using a mix of tools and human expertise, which can reduce the day-to-day burden on in-house teams. They often use EDR as part of their stack.
Benefits of EDR solutions
EDR helps most when endpoint risk spans dozens or thousands of devices and when speed matters during an incident. The benefits below focus on what EDR does at the endpoint level: deeper visibility, faster investigation, and rapid containment to limit damage.
Reduced attack surface
An attack surface is the set of points on the boundary of a system or environment where an attacker can try to enter, cause an effect, or extract data. EDR is often deployed as part of an endpoint security platform that can reduce exposure through controls such as:
- Risky behavior control: EDR can block behaviors commonly abused by malware, such as scripts attempting to download payloads or the execution of potentially obfuscated scripts.
- Exposure and configuration management: Some platforms pair EDR with vulnerability and configuration assessments to identify missing patches and insecure settings (for example, whether encryption or automatic updates are enabled).
- Malicious destination blocking: Network protection features can prevent endpoints from connecting to known malicious IP addresses and domains.
- Ransomware hardening controls: Controlled folder access can block untrusted apps from modifying protected folders, helping limit ransomware’s ability to encrypt critical data.
Enhanced visibility across endpoints
EDR collects telemetry from endpoints, including desktops, laptops, and servers (and, depending on the platform, mobile devices and IoT), so teams can see when threats move between systems.
Near real-time monitoring shows which programs are running, which network connections are active, and which files or system settings are changing.
EDR also records endpoint network activity, which can help reveal lateral movement, such as when attackers pivot from one compromised device to another. This can help teams identify affected endpoints faster and reconstruct what happened for forensic analysis, rather than uncovering compromised devices one by one.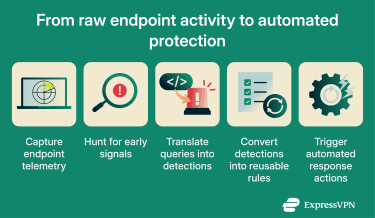
Proactive threat detection
Some EDR platforms let analysts explore endpoint telemetry using hunting queries, for example, Kusto Query Language (KQL) in Microsoft Defender. Teams can proactively hunt for suspicious activity, for example, to:
- Review process launches and triggers.
- Track file creation and modification (altered binaries, unexpected disk writes).
- Monitor registry creation and changes (persistence, configuration tampering).
- Inspect inbound and outbound connections (including listeners).
- Audit authentication events (sign-ins, failures, unusual logins).
Teams can convert hunting queries into custom detection rules that run automatically at regular intervals. When these rules find matches, they generate alerts and trigger response actions, such as isolating a device or taking action on a suspicious file.
Automated incident response
EDR platforms combine detection with endpoint-level response actions that teams can trigger immediately when suspicious activity appears.
For example, teams can isolate compromised endpoints from the network to limit lateral movement and reduce the risk of further data exfiltration while maintaining EDR connectivity. EDR can also terminate malicious processes directly on affected endpoints and collect investigation artifacts (such as process and connection data) to support investigation and remediation.
Data breach and ransomware prevention
EDR can help reduce the impact of breaches and ransomware, a common form of cyber extortion that is often human-led.
EDR can automatically detect and contain ransomware activity at early stages (depending on the platform and configuration). Endpoint isolation contains threats and prevents lateral movement within an environment. Some endpoint platforms bundled with EDR also support anti-ransomware hardening controls, such as blocking untrusted apps from modifying protected folders.
Key considerations when selecting an EDR solution
The key factors to consider when choosing an EDR solution include deployment model, integration depth, threat intelligence, and scalability.
Cloud-based vs. on-premise deployment
Cloud-based EDR uses vendor-managed infrastructure, which is typically easier to deploy, update, and scale. It usually requires reliable outbound connectivity to the vendor’s cloud service endpoints (which can affect firewall/proxy policies and URL allowlists).
Data storage location depends on the tenant's region and the provider’s data residency rules, so it’s important to confirm storage/processing locations against local compliance requirements.
On-premise EDR keeps more components and stored telemetry under an organization’s direct control and can be deployed in restricted connectivity models (for example, through a proxy or in environments with limited external access), depending on the vendor and architecture.
Integration capabilities
EDR often delivers the most value when integrated with other security tools. Integration can enable faster alert triage, more automation, and stronger correlation across data sources.
For example, EDR can forward endpoint alerts to security information and event management (SIEM) systems, helping analysts to view security data in one place. Integration with orchestration tools can automate incident response actions, such as isolating devices or terminating processes.
When integrated with SIEM or XDR platforms, endpoint detection can be correlated with related activity across cloud and on-premises environments, helping teams understand the full scope of an attack.
Threat intelligence feeds
Threat intelligence can provide EDR platforms with context on known and emerging threats through indicators such as IP addresses, domains, URLs, and file hashes. Teams can use these indicators to define detection, prevention, or exclusion rules at the endpoint level.
Organizations can share threat intelligence using standards such as Structured Threat Information eXpression (STIX) and Trusted Automated eXchange of Intelligence Information (TAXII). STIX provides a structured format for describing threats, while TAXII supports automated distribution of threat intelligence over HTTPS. Many EDR and endpoint security platforms also include vendor-maintained threat feeds with built-in reputation data.
EDR can continuously check endpoint activity against reputation data and custom indicators. Where supported, it can help prevent endpoints from connecting to known malicious domains, URLs, or IPs. Teams can also add custom indicators based on internal intelligence, which can help surface emerging risks before they appear in public threat feeds.
Scalability and performance
Scalability determines whether EDR remains reliable as endpoint count grows and investigations become more frequent. Key factors to consider include backend capacity, network connectivity, and the platform's efficiency in processing large volumes of endpoint telemetry.
Self-hosted deployments face practical infrastructure limits. Hardware, storage, and processing capacity can constrain how many endpoints the system can support at a given time, which makes upfront sizing and ongoing capacity planning unavoidable.
Cloud-managed deployments remove much of that backend burden but rely on consistent outbound connectivity as fleets expand. Large deployments need clean access to vendor service URLs/domains (and, where supported, published IP ranges), so firewall and proxy rules stay manageable.
High event volumes can slow ingestion and processing, so EDR platforms need efficient data handling to avoid slow searches and delayed investigations. At scale, these factors directly influence EDR's responsiveness during active incidents.
FAQ: Common questions about EDR
What are EDR and SOC?
Endpoint detection and response (EDR) is a security technology that continuously monitors endpoints to detect and respond to malicious activity. A security operations center (SOC) is a centralized team or function that uses tools like EDR and security information and event management (SIEM) to detect, analyze, and respond to security incidents across the organization.
What is an example of an EDR?
An example of an endpoint detection and response (EDR) solution is CrowdStrike Falcon. It continuously monitors endpoint activity, uses cloud-based analytics to help investigate suspicious behavior, and can support automated containment actions to limit the impact of threats such as ransomware (depending on configuration).
What are the best EDR tools available today?
There’s no single “best” endpoint detection and response (EDR) tool for every environment, but widely used EDR tools include:
| CrowdStrike Falcon | Cloud-native EDR designed for continuous endpoint monitoring and threat hunting, backed by threat intelligence and analytics. Often a fit for larger organizations that need broad endpoint visibility and mature detection workflows. |
| SentinelOne Singularity | AI-driven detection with autonomous response capabilities; some tiers include features such as one-click rollback for remediation. Often a fit for teams that want a high level of automation. |
| Microsoft Defender for Endpoint | EDR and endpoint security capabilities that integrate closely with Microsoft environments and tooling, with broad device coverage and centralized telemetry. Often a fit for organizations invested in the Microsoft ecosystem. |
Why are EDR solutions necessary for modern businesses?
Endpoints are common targets and provide attackers with multiple points of entry, especially as organizations support remote and hybrid work across more devices. Endpoint detection and response (EDR) continuously monitors endpoints for signs of threats and can help organizations detect and contain incidents faster than traditional, prevention-focused endpoint tools alone.
Can EDR prevent ransomware attacks?
Endpoint detection and response (EDR) can help stop ransomware by detecting suspicious behaviors and triggering response actions, such as isolating an affected endpoint from the network or terminating a malicious process. However, EDR works best as part of a layered security setup, not as a standalone defense.
How does EDR integrate with existing security systems?
Endpoint detection and response (EDR) integrates with other security systems by sharing endpoint telemetry and alerts and exposing response actions that other tools can trigger through integrations. It can connect to tools such as security information and event management (SIEM) and security orchestration, automation, and response (SOAR) platforms (and in some environments, network controls like firewalls) via APIs and built-in connectors.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN