What is carding? Payment card fraud explained

Carding is a form of payment fraud in which cybercriminals use stolen or illegally acquired card details to make unauthorized purchases or test stolen data for later misuse. Understanding how it works and its place in the broader landscape of payment card fraud helps individuals and businesses recognize and defend against it.
This guide looks at what carding is, how typical scams tend to occur, and carding prevention strategies.
Note: This information is for general educational purposes and not financial or legal advice.
What is carding?
Carding is a type of card fraud in which criminals, sometimes known as “carders,” use stolen credit or debit card details to make purchases. These often include prepaid cards or gift cards, which may be resold for profit, but stolen card details may also be used to buy goods or services online, create counterfeit cards, produce false identification documents, or be sold to other criminals for further misuse.
Payment card fraud remains a persistent form of organized cybercrime, according to law enforcement agencies such as Europol.
Carding vs. credit card fraud
"Carding" and "credit card fraud" are closely related terms, but they’re not the same.
Carding is a specific type of payment card fraud in which cybercriminals, often referred to as “carders,” use stolen card information from credit or debit cards to make purchases. These transactions are frequently small and usually digital, such as buying prepaid or gift cards online, which the carders can then resell or convert to cash. A defining feature of carding is the testing or monetization of stolen card data, often through online or “card-not-present” (CNP) purchases.
Credit card fraud is a broader term that encompasses all illegal or unauthorized activity involving credit cards. This includes carding but also extends to other forms of fraud, such as skimming or cloning physical cards, account takeover or identity theft, and fraudulent credit card applications.
In short, all carding is a form of payment card fraud, but not all credit card fraud is carding.
How carding fraud works
Carding scams typically proceed through three distinct stages. First, carders obtain stolen card details. They then make small test purchases to verify that the cards are active. Finally, they use the stolen cards to make larger transactions.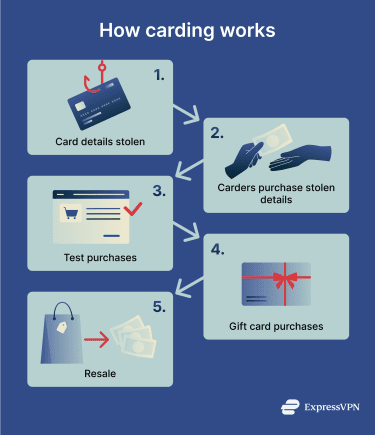
Common stages of carding scams
Carding scams can vary in their execution, but many will include the following steps:
- Attackers steal card data: Cybercriminals use a variety of methods, including phishing scams, malware infections, and card-skimming devices. They can then sell stolen data online, usually via structured carding forums and underground marketplaces.
- Carders purchase stolen data: Carders scour carding sites, forums, and marketplaces (usually via the dark web) to purchase stolen card data from other criminals. They’ll often use hard-to-track payment systems, such as cryptocurrencies, to evade detection.
- Carders test numbers to verify they work: Once they have acquired stolen card details, carders usually want to check that the numbers are genuine without triggering fraud detection systems, so they often make very small online transactions.
- Gift and prepaid card purchases: After verifying that a card is working, carders might use it to purchase gift cards or other prepaid cards from online retailers. This might include gift cards for Amazon, iTunes, or Google Play.
- Reselling for profit: After purchasing gift cards with someone else’s money, scammers may be able to resell those codes on online marketplaces for profit.
Why gift cards are often targeted
Carders don’t always buy gift cards with stolen card details; they may also purchase physical goods, airline tickets, car rentals, or accommodation using compromised cards.
However, gift cards tend to be a common target for these kinds of scammers, for the following reasons:
- Simplicity: Gift cards are quick and easy to buy, available at many online stores, and straightforward to list and resell on other sites. Scammers don’t have to worry about storing or shipping them either; they can just email the codes to buyers.
- Demand: Levels of demand can rise and fall for various products, but there’s near-constant demand for gift cards from well-known brands, giving scammers a better chance of making quick profits before their crimes are even detected.
- Speed: Scammers can purchase gift cards and cash them in more quickly than other products. This minimizes the window in which they might be detected, giving them a better chance of getting away with their crime and making a profit.
- Irreversible: In many cases, once a gift card code has been used, it’s usually not possible for that process to be reversed or undone. So, even if the fraud is eventually detected, using gift cards makes it easier for scammers to keep whatever profits they make.
How do criminals obtain card information?
Stolen payment card details are routinely aggregated, traded, and strategically released into underground markets. Industry reporting shows that stolen payment data often ends up on carding forums and other dark web marketplaces long after the initial theft. For example, Visa’s Biannual Threat Report (Fall 2025) highlights that 85–93% of exposed accounts on the forums it studied related to thefts that occurred up to 12 months prior, which the research cites as an intentional approach to maximize return on investment.
Below are some of the most common methods used by criminals to obtain payment card details.
Phishing and social engineering
Phishing is a form of social engineering in which criminals use fraudulent messages (usually emails, but also texts, calls, or social media messages) to trick victims into disclosing their personal details. They might pose as a bank or retailer, for example, and send a message to a victim, asking them to confirm their card details to secure their account or confirm a purchase.
These emails typically include links to fake, malicious websites. If the victims click those links and enter their details, the criminals will receive them and, in many cases, will then list them for sale on dark web platforms or other digital marketplaces.
Given how widely phishing is used in cybercrime, it’s often the starting point for broader fraud schemes. Recent data from the Anti-Phishing Working Group (APWG) Phishing Activity Trends Report for Q3 2025 shows hundreds of thousands of unique phishing attacks recorded in a single quarter. As a result, phishing remains one of the most common and effective methods scammers use to steal card data.
Malware
Cybercriminals can also spread malware to obtain credit or debit card details.
Keyloggers, for example, are malicious applications that can log every key a person presses without their knowledge. Installing one can allow cybercriminals to record any information the user inputs, including payment card details. This is just one example; there are many other types of malware that can capture card data, including infostealers and banking Trojans.
Data breaches
Data breaches, whether caused by targeted intrusions, insider threats, or accidental leaks, can expose large volumes of customer information, including payment card data. This information may later be traded in bulk on underground marketplaces, where carders purchase compromised accounts and test them to identify valid, usable cards.
Enumeration attacks
In some cases, criminals also generate card details through enumeration attacks, automated attempts to guess valid card numbers and security codes using brute force on online checkout forms, a technique that industry reports from Visa identify as a persistent threat to the payment ecosystem.
Card skimming and fake websites
Card skimming involves the use of special devices, called card skimmers, which can be installed into credit card readers, point-of-sale systems, or ATMs. When a person inserts their card into a reader or machine, the skimmer may be able to read and store the card’s number, then pass that information to fraudsters.
Some scammers also carry out digital skimming, the online equivalent of card skimming. Instead of tampering with a physical payment terminal, attackers inject malicious code into a merchant’s checkout page to secretly capture card details entered by customers. In other cases, scammers may set up entirely fake online stores designed to mimic trusted brands or lure shoppers with unrealistically low prices, stealing card information at checkout.
How to protect yourself against carding

Secure online payment practices
Card payments themselves aren’t inherently insecure; many banks now use fraud monitoring and two-factor authentication (2FA), such as requiring you to approve online purchases through your banking app.
However, you can further reduce risk by using tools that limit the amount of your card information exposed. Some banks offer virtual or disposable card numbers for one-off purchases, so your physical card details aren’t shared with the merchant. Alternatively, digital wallets such as PayPal, Google Pay, or Apple Pay can act as intermediaries, meaning merchants don’t receive your full card number.
Recognizing phishing attempts
The more you know about how phishing works and what phishing messages look like, the easier it should be to avoid.
Common indicators of phishing include:
- Generic greetings: Many phishing messages start with generic salutations like “Dear Customer” or “Sir/Madam” rather than personalized ones.
- Links or attachments: Phishing scams often involve links to malicious sites or attachments that may contain viruses.
- Urgent or threatening language: Scammers use coercive or intimidating language, threatening consequences unless you act quickly.
- Requests for sensitive information: Most legitimate companies will never ask for your payment details or personal information via email, text message, or phone.
If you receive any unsolicited messages bearing these hallmarks, be cautious. Avoid clicking any links or downloading any attachments, and don’t comply with any threatening requests or demands. Learn more in our guide to preventing phishing attacks.
Monitoring accounts and setting alerts
Carding scams can sometimes go unnoticed, especially when fraudsters make small “test” purchases that victims don’t immediately spot. To reduce this risk, it’s important to review your bank statements regularly and make sure you recognize every listed transaction.
Many banks and card providers also let you set up real-time alerts whenever your card is used, so you can quickly flag any unauthorized activity.
In addition, services such as ExpressVPN Identity Defender (available to U.S. users on select subscriptions) can monitor the dark web for exposed personal information, including payment details, and notify you if your data appears in known breach databases or underground marketplaces.
Learn more in our complete guide to dark web monitoring.
How banks and card issuers protect against carding fraud
Banks and card providers also use a range of tools to detect carding and other forms of payment fraud. These may include location analysis to flag transactions outside a cardholder’s usual area, behavioral analytics to identify unusual spending patterns, and machine learning systems trained to detect suspicious activity.
Many banks also integrate additional verification steps into the online payment process. For example, card networks such as Visa offer 3D Secure authentication (often branded as Visa Secure), which often requires you to confirm a purchase via your banking app, enter a one-time code, or use biometric verification before the transaction is approved.
The exact systems and processes vary between financial institutions, so some may detect and block fraudulent activity more quickly than others.
How to detect a carding attack
Even with preventative measures in place, it’s still possible for any cardholder to fall victim to carding attacks. As such, you need to know how to detect a suspected attack so you can respond quickly.
Warning signs of carding fraud
There are two main warning signs that indicate you may be at risk of a carding attack.
Unrecognized transactions and account alerts
A common sign that you’re being targeted in a carding attack is seeing unrecognized transactions on your card statements. This happens when the carders use your card to make small test purchases (which scammers usually do to avoid fraud detection systems) or to buy gift cards.
Watch for:
- Small, unfamiliar charges.
- Multiple low-value transactions in a short period.
- Purchase alerts for transactions you didn’t authorize.
- Declined transactions you don’t recognize.
Regularly review your statements, investigate any transactions you don’t recognize, and act immediately if you receive a transaction alert for a purchase you didn’t make.
Data breach alerts
If a company you’ve done business with announces a data breach, your information could potentially be exposed. While this doesn’t automatically mean your card will be misused, it does increase your risk.
You can check whether your email address or login credentials were exposed via a service such as Have I Been Pwned. Password managers like ExpressVPN Keys can also alert you if saved credentials appear in known data breaches, allowing you to update affected passwords quickly.
These are risk indicators, not guaranteed signs of a carding attack. A data breach does not automatically mean your card will be misused. However, if you discover that your information has been exposed, you should take immediate steps to secure your accounts.
What to do if you’re a victim of carding
If you suspect you’ve been a victim of carding, the sooner you take action, the better. It’s important to stay calm but act swiftly to prevent criminals from using your card for further purchases.
Immediate steps to take
The first and most important step is to contact your bank or card provider immediately. Many banks have dedicated fraud teams you can reach directly. Explain the situation, and they can freeze your card, block further transactions, and issue a replacement if necessary.
Once your card has been secured, take additional steps to limit further risk. Change the password for your online banking account and for any websites where your card details are stored. Enable multi-factor authentication (MFA) on financial and high-value accounts where possible. Review recent transactions carefully to identify any additional unauthorized activity.
Victims in the U.S. can also contact one of the three major credit bureaus (Equifax, Experian, or TransUnion) to place a fraud alert on their account or freeze their credit. Those in other countries should contact the relevant credit reporting agencies or consumer protection authorities in their region.
Reporting carding fraud
Any suspected incidents of carding or other forms of credit card fraud can also be reported to your local police department, as well as other relevant authorities in your location. Examples include the Federal Trade Commission (FTC) and the FBI’s Internet Crime Complaint Center (IC3) in the U.S., and other countries will also have their own authorities and organizations to contact.
Recovering funds and protecting your identity
Victims of carding may be able to recover funds used in fraudulent transactions, though outcomes depend on local laws and individual bank policies. Many financial institutions offer zero-liability protections for unauthorized charges, provided the fraud is reported promptly.
After resolving the immediate issue, continue monitoring your accounts and securing your personal information. Consider reviewing where your card details are stored online and removing them from accounts you no longer use. Following cybersecurity best practices, such as keeping devices up to date and using trusted networks when making purchases, can reduce future risk.
FAQ: Common questions about carding
What is carding in simple terms?
Carding is a type of fraud in which criminals use stolen card details to make purchases, usually online. They’ll often make small purchases first to test that the card details are still usable before making larger purchases, often focusing on gift cards.
Can carding affect my credit score?
Yes, carding can negatively affect your credit score, but it depends on the nature of the attack and how quickly you identify it and report it. If the fraudsters use your details to buy goods or services that you subsequently miss payments on, for example, this could harm your score. But if you spot the fraud early and take appropriate action, there’s less risk of your score being impacted.
How can I protect my card from carding?
The best way to prevent carding is to keep your card details as safe as possible. Never share them with anyone, and if you need to buy online, only do so on secure, trustworthy sites. Opt for secure payment methods like virtual cards, set up alerts with your bank to let you know when your card is used, and consider data breach or dark web monitoring tools to stay alert to potential exposure of your information.
What are the signs of carding fraud?
Signs of carding fraud include random charges that you don’t recognize appearing on your bank or card statements, letters or other correspondence about goods and services you don’t have any recollection of purchasing, or unexpected changes to your credit score.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN