VPN passthrough: Do you need it, and how does it actually work?

When you use a virtual private network (VPN) to connect to the internet, most modern protocols, like those used by ExpressVPN, work smoothly with your router and don’t need any special settings. But if your VPN relies on older connection methods or a manual setup, you might run into problems like failed connections or frequent drops.
This often happens because those older VPN methods don’t interact well with the way home routers manage and filter traffic. VPN passthrough is a router feature that lets this traffic pass through its security filters so your VPN can establish a stable, encrypted connection.
In this guide, we explain how VPN passthrough works, how to enable it on your router, and how to tell whether you actually need it.
Please note: Changing router settings may affect your network’s security. Only adjust these settings if you understand what they do and return them to their defaults once you finish troubleshooting. If you're not sure which settings are safe to change, contact your router manufacturer or IT administrator.
What is VPN passthrough?
VPN passthrough is a router feature that allows VPN traffic to cross the router’s firewall and reach the VPN server instead of being blocked or mishandled. In practice, it makes sure the router recognizes certain types of VPN data and forwards them correctly.
This becomes important with older VPN protocols, which weren’t originally designed to work with modern home routers. Because they encapsulate data differently, the router may fail to process the traffic properly and end up dropping it. As a result, your VPN might never finish connecting or disconnect soon after it does.
Many modern VPN apps like ExpressVPN don’t require you to think about VPN passthrough at all, because they use newer protocols that are designed to work with today’s routers and Network Access Translation (NAT) setups. However, if you’re using an older or manually configured VPN and it suddenly stops working, especially after changing routers or internet service providers (ISPs), VPN passthrough is one of the first router settings worth checking.
People often confuse VPN routers and VPN passthrough, but they’re not the same. A VPN router runs a VPN client or server itself and encrypts traffic for all connected devices. VPN passthrough, on the other hand, simply lets VPN traffic from devices on your network pass through the router without being blocked.
How does VPN passthrough work?
Behind the scenes, your router inspects incoming and outgoing packets and decides where to send them, both within your home network and out to the internet. It also applies firewall rules to block unsolicited or suspicious traffic.
VPN passthrough adds extra handling for VPN traffic coming from devices on your network. When the router sees VPN packets from a device, it treats them as part of a valid outgoing connection instead of something to block. It keeps track of that VPN session and forwards the encrypted packets to the VPN server rather than dropping them.
This is what allows certain older VPN setups, which may not work well with some routers, to establish and maintain a tunnel without constant connection failures.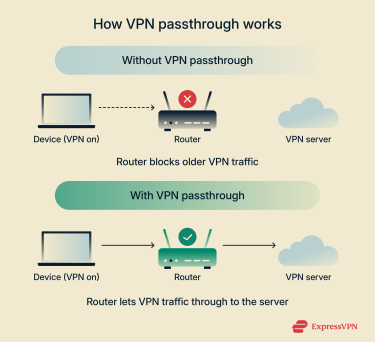
Which VPN protocols require passthrough?
Only a few older VPN protocols need passthrough enabled on a router. Each interacts differently with router firewalls and can affect whether your VPN connects successfully.
- Point-to-Point Tunneling Protocol (PPTP): An older VPN protocol that uses an outdated encryption method and Generic Routing Encapsulation (GRE), a tunneling method that wraps your data in an extra header so it can travel between two endpoints. Many routers performing NAT can’t track GRE properly because it doesn’t use port numbers, so they can’t create the necessary NAT entries for return traffic. As a result, PPTP connections often fail unless the router has PPTP passthrough or other GRE-specific handling enabled. Because PPTP’s encryption is considered broken and insecure, it’s not recommended for general use.
- Layer 2 Tunneling Protocol (L2TP): L2TP is a tunneling protocol that’s usually paired with IP Security (IPsec) for encryption. In this setup, the connection relies on specific User Datagram Protocol (UDP) ports (like 500 and 4500) for key exchange and encrypted traffic. On some older or more restrictive routers, this traffic doesn’t look like “normal” web browsing, so it might be blocked or not handled correctly unless IPsec/L2TP passthrough or similar support is enabled. L2TP, especially without strong IPsec configuration, is considered outdated and is generally not recommended today.
- Internet Protocol Security (IPsec): IPsec protects your traffic by adding extra headers, like the Authentication Header (AH), which checks that the data really came from the claimed source and hasn’t been altered, and the Encapsulating Security Payload (ESP), which encrypts the contents so others can’t read them. Because these headers weren’t originally designed for routers that change IP addresses along the way, IPsec tunnels can break on NAT-based routers. NAT Traversal (NAT-T) works around this by wrapping IPsec packets inside UDP packets so they have clear IP addresses and port numbers for source and destination. This allows routers to handle them like normal outbound traffic and can forward them without breaking the VPN connection. Unlike PPTP and standalone L2TP, IPsec, especially Internet Key Exchange version 2 with Internet Protocol Security (IKEv2/IPsec), remains a secure and widely used protocol today.
Learn more: Read a detailed explanation of the differences between PPTP and L2TP.
The role of NAT in VPN connections
NAT lets multiple devices on your internal network share a single public IP address when they connect to the internet. Each outgoing connection passes through your router’s NAT, which rewrites the source address and keeps a record of which internal device each connection belongs to.
When you visit a website, your router replaces your device’s private IP address with your network’s public IP address and usually assigns a unique source port. It stores this mapping in a NAT table. When the website responds, the router looks up the entry in that table and forwards the data back to the correct device inside your network.
NAT also blocks unsolicited incoming connections. If a packet doesn’t match an existing entry in the NAT table, the router drops it because it has no mapping to any internal device. In normal operation, all allowed inbound traffic must match the NAT table; if traffic that doesn’t match is still getting through, that’s a vulnerability known as NAT slipstreaming.
Still, NAT is designed for address translation and conserving IPv4 addresses, so it shouldn’t be treated as a full replacement for a firewall or other security tools.
Some older VPN protocols were not designed with NAT in mind, which can cause network issues. For example, PPTP uses GRE, which doesn’t include ports that NAT can easily track, and IPsec with the AH can break when NAT modifies packet headers.
In these situations, the router may drop or mishandle the encrypted traffic. VPN passthrough features and NAT traversal extensions help by providing the router with clear rules to recognize these protocols and forward the encrypted packets correctly, rather than discarding them.
Learn more: Check out our complete guide to network mapping.
NAT traversal techniques
Note: “NAT traversal” is a general term for methods that help VPN traffic pass through routers that use NAT. NAT-T is just one of these methods.
Many modern VPN apps include NAT traversal features so they can work through home routers without you changing any settings. These techniques are built into the VPN software and usually run automatically in the background. Two common ideas behind NAT traversal are:
- NAT-T: A method commonly used with IPsec where ESP packets are wrapped inside UDP (usually on port 4500) so they can pass through NAT. Because NAT modifies source IP addresses and ports in the IP header, standard IPsec integrity checks would see those changes as tampering and drop the packets. By encapsulating ESP inside UDP, NAT can safely rewrite the outer headers without breaking IPsec, and VPN clients can send small keep-alive packets (tiny, periodic “I’m still here” messages) over this UDP flow so the NAT mapping doesn’t time out and the tunnel stays up even when traffic is idle.
- UDP encapsulation: A general technique where VPN data (such as IPsec ESP packets) is wrapped inside standard UDP packets so it looks like normal outbound traffic. Encapsulation is needed because raw ESP doesn’t use ports that NAT can easily track. By placing this traffic inside UDP, routers can create and maintain NAT mappings more reliably, helping the VPN tunnel pass through NAT and basic firewalls without breaking IPsec’s integrity checks.
How to enable VPN passthrough on routers
Most modern routers have VPN passthrough enabled by default. You can check or change the setting from your router’s admin page. Turning it on ensures your router recognizes and forwards VPN traffic correctly.
Enabling VPN passthrough via router settings
If your VPN connection fails or won’t stay connected, it’s worth checking whether your router’s VPN passthrough settings are turned on. Most routers include these options under advanced configuration menus, often labeled by the VPN protocol they support.
Here’s how to find and adjust them (using TP-Link as an example):
- Open a browser and go to your router login page (usually 192.168.0.1 or tplinkwifi.net).
- Enter your username and password to sign in.
- In the top panel, select Advanced.
- In the left menu, select Security.
- Look for the VPN Passthrough options (PPTP, L2TP, IPsec).
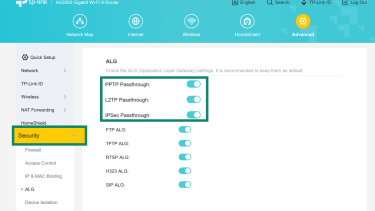
- Click Save to apply the settings and select Enable for each passthrough type you need.
Step-by-step guides for other popular routers
Every router brand handles VPN passthrough settings a little differently. Here’s how it works on other common models:
Netgear Nighthawk
Netgear routers allow VPN passthrough automatically for PPTP, L2TP, and IPsec. They can’t be toggled on or off.
Here are some steps to confirm your router isn’t blocking VPN traffic:
- Open a browser and go to the Netgear router login page.
- Sign in with your router username and password.
- Go to Advanced.
- Open WAN Setup.
- If you’re having trouble connecting, try temporarily turning off Disable Port Scan and DoS Protection, then test your VPN again.
- Review any custom firewall or blocking rules and make sure they’re not filtering GRE (for PPTP) or UDP ports 500 and 4500 (used by IPsec and L2TP).
- Save any changes.
Asus
On Asus routers, VPN passthrough is controlled through a setting called NAT Passthrough. This menu lets you decide whether older VPN protocols like PPTP, L2TP, and IPsec are allowed to pass through the router’s NAT instead of being blocked.
To enable VPN passthrough on an Asus router:
- Connect to the router via a local area network (LAN) or WiFi.
- Open a browser and go to www.asusrouter.com.
- Log in with your router username and password.
- Go to WAN > NAT Passthrough.
- Make sure the passthrough option for the protocol your VPN uses (for example, PPTP Passthrough, L2TP Passthrough, or IPSec Passthrough) is set to Enable, then click Apply.
Common issues and troubleshooting tips
Even when VPN passthrough is on, you can still face connection issues. They often come from misconfigured router settings, outdated firmware, or conflicts with older VPN protocols.
1. VPN connects, but “no internet”
If your VPN connects but can’t send or receive data, your router might be blocking traffic. Some routers include an Application Layer Gateway (ALG) that interferes with older protocols like PPTP or IPsec. Try disabling ALG in your router’s advanced settings.
2. VPN won’t connect
If your VPN fails to connect, the passthrough option might be off, or your router may not support the protocol you’re using. Check that PPTP, L2TP, or IPsec passthrough is enabled and update your router’s firmware.
If you’re using two routers or a modem and router, a double NAT setup might be blocking the connection. Using bridge mode can help, or in some cases, placing the second router in a demilitarized zone (DMZ) to forward all incoming traffic to one device to ensure the VPN traffic isn’t filtered.
3. VPN keeps disconnecting
If the VPN connection keeps dropping, your router may be hitting its limit for simultaneous VPN passthrough sessions. Reboot your router and VPN device to reset the connection.
Repeated disconnects can also happen when old VPN sessions get “stuck” or overlap. If the router or VPN server still thinks there’s an active tunnel, new connections might be dropped. In that case, wait for the existing session to terminate, disconnect any other devices using the same VPN account, or clear the connection by restarting the app or device. If the problem continues, check for firmware updates or consider a router upgrade.
4. Passthrough setting missing
Newer routers often enable VPN passthrough by default, so the setting might not appear. Check the Advanced, Security, or VPN menus for similar options like “VPN passthrough support” or “IPsec NAT-T”. If you still can’t find it, check your router’s manual or support site.
5. Router not compatible with your VPN protocol
Some older routers don’t support NAT-T, which IPsec needs to work correctly. If yours doesn’t, switch to a modern VPN protocol like OpenVPN, IKEv2, or Lightway, which connects without passthrough.
Key advantages and disadvantages of VPN passthrough
Here are the most important benefits and performance trade-offs to keep in mind:
Benefits for home users
- Keeps your VPN working: Helps legacy VPN protocols connect through routers that might otherwise block them.
- Prevents dropped connections: Reduces connection failures for older or manually configured VPN setups, so your tunnel is less likely to drop mid-session.
- Avoids buying new hardware: Lets you keep using your current router instead of upgrading to a VPN router just to support an older work or school VPN.
- Supports remote access for work or school: Makes it easier to connect securely to corporate or campus networks that still rely on PPTP, L2TP/IPsec, or similar legacy setups.
- Usually already available: Most modern routers include VPN passthrough and often have it enabled by default, so you only need to adjust it if you’re having issues.
Risks and security concerns
- Older, weaker protocols: In practice, VPN passthrough is mainly used with older VPN protocols like PPTP and legacy L2TP/IPsec. Some of these are considered outdated or less secure compared with modern options like OpenVPN, IKEv2, or ExpressVPN’s proprietary Lightway protocol.
- Not very future-proof: Relying on VPN passthrough ties you to legacy VPN setups that many providers are phasing out. You may miss out on stronger encryption, better reliability, and newer features available with more modern VPN protocols.
- Slightly larger attack surface: Enabling passthrough keeps specific VPN-related ports and handling rules active. If your router firmware is outdated or misconfigured, that can marginally increase your exposure, which is why keeping firmware up to date is important.
VPN passthrough in corporate networks
In corporate environments, VPN passthrough is about letting specific VPN traffic move through firewalls without exposing the whole network. IT teams configure it so remote employees can reach internal VPN servers while the organization’s security standards still apply.
Here’s how passthrough fits into broader corporate security practices:
Enhanced security
Companies configure VPN passthrough so that only approved VPN traffic reaches the company’s internal VPN server. IT teams control which protocols are allowed and ensure traffic is encrypted and authenticated before it enters the network. They also rely on network configuration management to keep firewall and routing rules consistent, monitored, and secure across devices and locations.
Many organizations are also moving toward zero-trust architecture, which focuses on continuous identity and device verification instead of trusting anything just because it’s “inside” the network. In these setups, traditional VPNs and router-level tunneling still play a role, but modern zero trust access tools reduce reliance on them by enforcing identity-driven security at every step.
Protection of sensitive data
When VPN passthrough and VPN gateways are configured correctly, encrypted VPN traffic can pass through perimeter firewalls and reach internal resources without being blocked. This helps keep sensitive files, internal apps, and business communications protected inside the VPN tunnel as they move between remote workers and corporate systems.
It also supports wider efforts to prevent data leaks and meet regulatory requirements such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), alongside other security and compliance controls.
Learn more: Read our detailed guide on network topology and the best practices for modern networks.
Alternatives to VPN passthrough
VPN passthrough was once essential for outdated VPN protocols, but most modern VPNs don’t need it anymore. Today’s VPN apps and routers handle encrypted connections automatically. If you’re still troubleshooting passthrough settings, it might be time to consider easier, more secure alternatives.
VPN routers vs. VPN passthrough
VPN passthrough keeps a VPN connection working on your network by letting VPN traffic from your device pass through the router so your VPN app can reach the VPN server. This is helpful for older or manually configured VPN protocols, but it doesn’t encrypt your data by itself or protect every device on the network.
A VPN router, on the other hand, connects to the VPN service directly. The router runs the VPN and sends all traffic from connected devices through the encrypted tunnel automatically, so you don’t have to install or configure VPN apps on each device.
If you want simple, always-on protection for your entire home network, a router with built-in VPN is often the better choice. ExpressVPN Aircove does this by running the VPN directly on the router and routing traffic from every connected device through the VPN by default, with the option to customize which devices use it.
FAQ: Common questions about VPN passthrough
Should VPN passthrough be enabled?
Yes, if you’re using an outdated VPN protocol like PPTP, L2TP, or IPsec. VPN passthrough lets these connections work through your router. It’s usually enabled by default, and most modern VPNs don’t need it, so you can leave it as is if your VPN connects without issues.
What’s the difference between a VPN client and VPN passthrough?
A VPN client is software that creates a secure, encrypted connection between your device and a VPN server. VPN passthrough is a router feature that lets the encrypted traffic travel through the router. The passthrough doesn’t encrypt anything; it just allows the VPN to work properly.
Should I disable IPsec passthrough?
Usually, no. Disabling it can stop older VPNs that rely on IPsec from connecting. If your VPN works fine and uses a newer protocol like ExpressVPN’s Lightway, OpenVPN, or WireGuard, it’s safe to leave IPsec passthrough enabled.
What are the security risks of VPN passthrough?
VPN passthrough itself isn’t risky, but it supports older VPN protocols that use weaker encryption. Protocols like PPTP and L2TP are outdated and easier to exploit than modern ones such as Lightway or OpenVPN. Using a VPN with up-to-date encryption removes the need for passthrough and keeps your data safer.
Can I use a VPN without passthrough?
Yes. Most modern VPN technology doesn’t need passthrough because it uses newer protocols that work through routers automatically. If you use ExpressVPN, for example, your connection is encrypted and routed securely without adjusting any router settings. Passthrough only matters if you’re on older protocols like PPTP, L2TP, or IPsec.
Do gamers or remote workers need VPN passthrough?
Usually not. Most gaming and remote work VPNs use modern protocols like Lightway, OpenVPN, or IKEv2 that connect through routers without passthrough. It’s only useful if your VPN relies on older protocols that can’t handle network translation on their own.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN