What is quantum-resistant encryption (and why you need it now)

The encryption that protects your organization’s data today will not work forever. A new kind of computer is coming that will break it. This is the quantum threat, and preparing for it now is one of the most important security decisions you will make.
You do not need to be a quantum physicist to make your organization secure. A new generation of quantum-resistant encryption is already ready. This guide gives you the information you need to act. You will learn what the quantum threat means for your security, what the new cryptographic solutions are, and the exact steps to take to build your migration plan.
What is quantum-resistant encryption?
Quantum-resistant encryption, also known as post-quantum cryptography (PQC), is a class of cryptographic systems built to be secure from attacks by both classical and quantum computers. It was developed to counter the quantum threat: the risk that a future quantum computer will break the asymmetric encryption that secures global data and communications.
Today’s popular encryption, such as Rivest-Shamir-Adleman (RSA) and elliptic curve cryptography (ECC), relies on mathematical problems that are too difficult for ordinary computers to solve. A quantum computer, however, could solve these specific problems easily and make this type of encryption useless.
PQC solves this problem by using new algorithms built on different kinds of mathematical problems (like those in lattice-based or code-based cryptography) that researchers believe are hard for any computer, including a quantum one, to crack.
This quantum-proof encryption provides long-term security against quantum attacks and stops future attempts at quantum decoding. Adopting it is a proactive step to make your data secure for the future.
Understanding the quantum threat to cryptography
Your need for quantum-resistant encryption comes from the security holes that quantum computers will create. The first step in preparing for this change is to understand the threat itself.
What makes quantum computers different?
Classical computers use bits, which are either 0 or 1. Quantum computers use qubits, which can exist in a superposition: a unique quantum state that isn’t just 0 or 1 but a mix of both. When measured, the qubit “collapses” into either 0 or 1. The outcome is not fixed in advance, but it does occur with certain probabilities that are built into the qubit’s state.
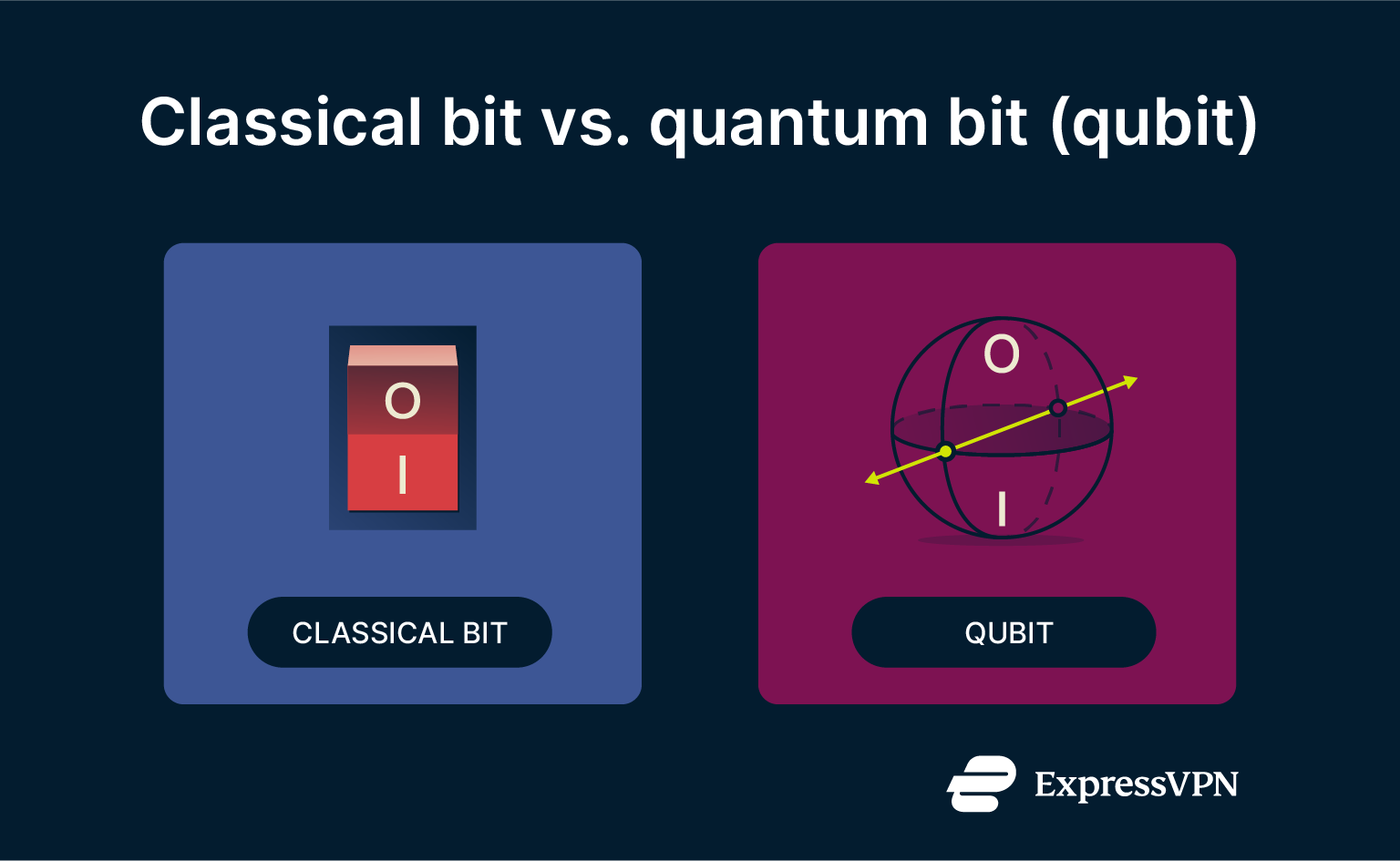
These properties give quantum computers the ability to process a massive number of calculations at once. For specific problems, this creates a significant quantum advantage. They can find answers exponentially faster than any classical computer.
Which encryption methods are vulnerable?
To understand the quantum threat, it’s important to know that not all encryption is equally vulnerable. The quantum threat has a catastrophic impact on one type of encryption and a manageable impact on another.
The most urgent threat is to the asymmetric encryption algorithms that secure our digital infrastructure. This includes common standards like RSA, ECC, and Diffie-Hellman (DH) key exchanges. These are the algorithms that power modern public key infrastructure (PKI), which is used to secure web traffic (HTTPS), virtual private networks (VPNs), and digital signatures.
You can think of these algorithms as complex mathematical puzzles. For today’s computers, they are practically unsolvable. However, a quantum computer running Shor’s algorithm has a special trick that can solve these specific puzzles with ease, rendering the encryption completely useless. This is the primary vulnerability that PQC is designed to fix.
Symmetric encryption, on the other hand, faces a much less severe threat. This category includes algorithms like Advanced Encryption Standard (AES), which are typically used for encrypting the data itself after a secure connection has been established.
To use the analogy, symmetric encryption is not a puzzle with a shortcut. It’s more like a simple, strong, locked box. There is no special mathematical trick to open it; you have to try every possible key one by one. A quantum computer running Grover’s algorithm could speed up this guessing process, but not exponentially.
The solution here is straightforward: use a longer key. By doubling the key length, for example, by moving from AES-128 to AES-256, you increase the number of possible keys so dramatically that even with a quantum speedup, it would still take too long for an attacker to find the right one. For this reason, AES-256 is considered quantum-resistant.
Why post-quantum security matters now, not later
Now that we have distinguished between the catastrophic threat to asymmetric encryption and the manageable threat to symmetric encryption, the next question is when this becomes a problem. The short answer is: Now.
The urgency to adopt quantum-safe security stems from the immediate risk of “Harvest Now, Decrypt Later” (HNDL) attacks. Adversaries can capture and store sensitive encrypted data today, betting that they can perform quantum decoding on it once a quantum computer is available.

Any data that must remain confidential for years to come but is considered valuable enough to justify the high cost of long-term storage and future decryption efforts (such as government secrets) is already vulnerable to this strategy. Because migrating an organization’s entire cryptographic infrastructure is a complex, multi-year effort, the process must begin long before the threat becomes acute.
Waiting for “Q-Day,” the day a quantum computer breaks public-key encryption, means it will already be too late to protect your most valuable data.
When are quantum computers expected to become a real risk?
At the moment, nobody knows for certain when powerful quantum computers will become a reality; predictions range from a few years to several decades. Researchers and engineers still face significant technical challenges before quantum computing becomes practical and widespread.

That said, the more critical question for any organization is not “When will a quantum computer arrive?” but “Am I already vulnerable?” Given the possibility of harvest-now-decrypt-later attacks, the timeline for action for most organizations is now.
Quantum-resistant algorithms and cryptographic approaches
You now see the threat quantum computers pose to current encryption. Fortunately, a new generation of cryptographic tools is ready to meet this challenge. These tools are not just theoretical; they are practical, standardized solutions that you can prepare to implement.
Overview of quantum-resistant algorithms
The core of post-quantum security is a set of new quantum cryptographic algorithms. Researchers have been developing and testing these for years. The U.S. National Institute of Standards and Technology (NIST) has been running a global competition to identify the best ones. And, in 2022, it announced its first group of standardized PQC algorithms with official standards published in 2024.
These new standards are built on mathematical problems that are difficult for both classical and quantum computers to solve. They generally fall into a few families. One of the most prominent is lattice-based cryptography. This family includes algorithms like CRYSTALS-Kyber and its standardized version Module-Lattice–based Key-Encapsulation Mechanism (ML-KEM), which is designed for establishing encryption keys, and CRYSTALS-Dilithium for digital signatures. (The ML-KEM standard, by the way, is ExpressVPN’s quantum-resistant algorithm of choice; read more about it here.)
While your organization does not need to understand the deep mathematics behind these algorithms, it is important to follow NIST’s advice to only use algorithms that have been officially standardized.
The reason is simple: the standardization process is a multi-year, global effort where cryptographers from around the world try to find flaws in the proposed algorithms. The ones that survive this intense public scrutiny are considered the most secure and reliable.
Using a non-standardized algorithm means you are taking a risk on a method that has not been thoroughly vetted, which could contain hidden vulnerabilities. Sticking to the official standards ensures you are using a strong, trusted, and interoperable solution.
What is cryptographic agility, and why does it matter?
Sticking to the official NIST standards is the correct first step. But because the post-quantum landscape is still evolving, this reality leads to a critical need for what is known as cryptographic agility.
NIST defines cryptographic agility as the ability of a system to switch its encryption protocols and algorithms with minimal disruption. Think of it like having a door with a standard lock fixture. You can easily replace an old lock with a new, more secure model without needing to replace the entire door.
This capability is fundamental to your long-term security posture for several reasons:
- Future standards: The field of PQC is still developing. NIST is already evaluating additional algorithms that may become standards in the future.
- Potential vulnerabilities: No algorithm is guaranteed to be secure forever. A flaw might be discovered in a current algorithm, requiring a rapid transition to an alternative.
- Avoiding “hard-coding”: If your encryption methods are hard-coded into your applications, you will face a massive and costly effort to make changes.
With cryptographic agility, your systems are flexible enough to adapt. You can update your security in response to new information, keeping your organization protected.
Hybrid encryption strategies for the transition era
How do you start the move to quantum-safe encryption without abandoning the proven security of today’s algorithms? You can use a hybrid encryption approach.
Hybrid encryption combines a classical algorithm (like ECC) and a new quantum-resistant one (like ML-KEM). When you establish a secure connection, you use both to create the shared keys. An attacker would then need to break both cryptographic methods to access your data.
This strategy gives you two layers of protection: it protects you from the immediate threat of HNDL quantum attacks, and it keeps your systems secure with today’s trusted encryption in case a weakness is found in a new PQC algorithm.
Exploring quantum key distribution (QKD)
The PQC algorithms discussed earlier are a software-based defense. There is another, physically different approach to quantum safety: QKD. QKD is not a method of encryption itself. It is a highly secure method for two parties to share an encryption key. Its security rests on the laws of physics, not on the difficulty of solving a mathematical problem.
How QKD works
Imagine you need to send a secret key to a colleague. With QKD, you would encode parts of the key onto individual photons, which are particles of light, and send them over a fiber optic cable. The security of this key distribution method comes from a core principle of quantum mechanics: the act of observing a quantum particle disturbs it.
If an attacker tries to intercept and measure the photons as they travel, their measurement will inevitably alter the photons' states. When the transmission is complete, you and your colleague can test a small portion of the key. If your test reveals that the photons were disturbed, you know an eavesdropper was present. You can then discard the key and generate a new one. An attacker cannot spy on the key exchange without leaving a detectable trace.
QKD implementation challenges
QKD is more than a theory. Various companies around the world offer QDK products and services. Their clients include financial institutions, data center operators, and even government agencies that use it to protect classified communications.
However, QKD faces significant practical challenges that have led major cybersecurity bodies, including the U.S. National Security Agency (NSA), to recommend PQC as the preferred solution for most applications. The primary limitations of QKD include:
- It requires specialized hardware: QKD cannot be implemented as a software update. It relies on dedicated hardware, such as fiber optic lines, to transmit keys via photons (particles of light). This makes it expensive and difficult to integrate into existing networks.
- It does not solve the authentication problem: QKD is designed to securely share an encryption key, but it cannot verify the identity of the parties sharing the key. To prevent man-in-the-middle (MITM) attacks, QKD systems must still use an authentication method, which typically relies on the same classical asymmetric algorithms that are vulnerable to quantum attack.
- It has distance and infrastructure constraints: The quantum signal degrades over distance, limiting QKD to point-to-point connections, often under 100km, without specialized repeaters that introduce their own costs and security considerations.
For these reasons, PQC is the recommended and more practical solution for securing the world’s data. PQC algorithms are software-based, can be deployed on existing infrastructure, and provide a complete solution that includes quantum-resistant digital signatures for authentication. This makes PQC a scalable and comprehensive defense against the quantum threat.
How to prepare your organization for the quantum future
You now know the threat from quantum computers and the solutions available. You can move from awareness to action. Preparing for the transition to quantum-resistant encryption is a manageable process if you start now. Here are the steps you can take to protect your organization.
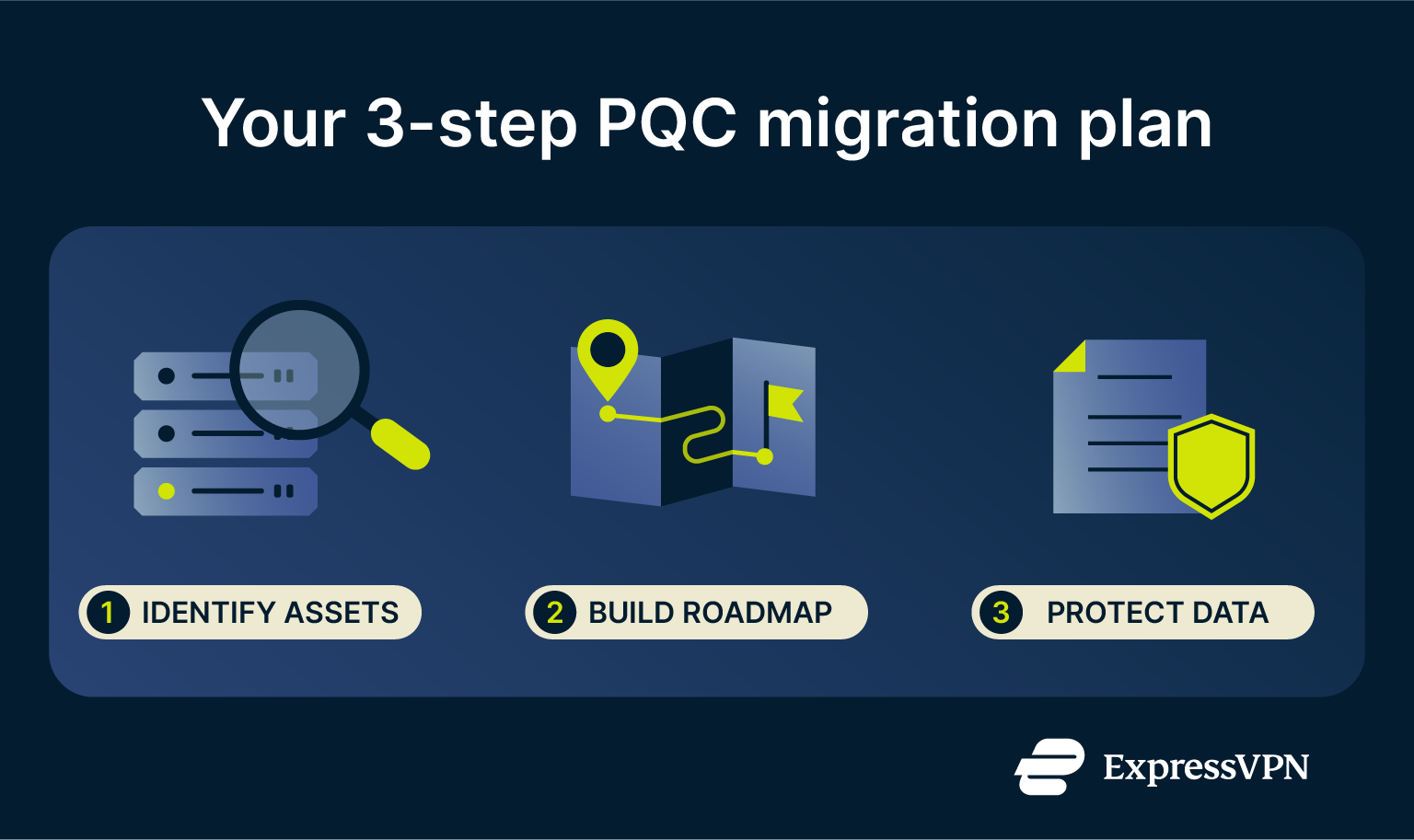
1. Identify cryptographic assets at risk
Create an inventory of all the cryptography your organization uses. You need to find every piece of software and hardware that uses an encryption algorithm.
Look for encryption in your applications, network devices like VPNs and firewalls, code-signing certificates, and your entire PKI. Your inventory should detail what is being encrypted, the algorithm used (such as RSA-2048 or ECC P-256), and its location within your systems. This inventory will be the foundation for your entire migration plan.
2. Build a migration roadmap
With your inventory complete, you can build a migration roadmap. This is not just a technical plan but a strategic one that should be informed by guidance from cybersecurity authorities. Both the U.S. Department of Homeland Security and the European Commission have published roadmaps that emphasize a coordinated, risk-based approach.
Your roadmap should plan the migration in phases:
- Prioritize based on risk: Start with the systems that protect your most sensitive information, especially data that must remain secure for many years. These assets are the most vulnerable to HNDL attacks. Make the quantum threat an official part of your organization's risk management framework.
- Set clear timelines: The European Commission has urged that high-risk systems in critical sectors be migrated to PQC no later than 2030. Use this as a benchmark for your own planning. A gradual, planned transition is much more practical than a last-minute replacement of every system.
- Engage your supply chain: Your organization’s security depends on the readiness of your technology vendors. Start conversations now with your cloud providers and software suppliers about their PQC roadmaps and timelines.
This is where cryptographic agility becomes a real asset. Systems that are already agile will be far easier to upgrade to new quantum-safe algorithms as you execute your roadmap.
3. Considerations for long-term data protection
Some of your data, like intellectual property, engineering designs, or intelligence records, may need to stay secure for decades. This data is at risk today. An attacker can steal it now and wait for a quantum computer to break its encryption.
You can protect this long-term data immediately by using hybrid encryption. Re-encrypt your most sensitive archives using both a trusted classical algorithm and a new quantum-safe algorithm. This approach provides immediate protection against future decryption attempts. It is a key risk-management strategy you can implement before you begin migrating your live communication systems.
4. Aligning with emerging standards and regulations
The move to quantum-safe security is not happening in a vacuum. Government bodies and industry groups are creating new standards. You must align your migration plan with these developments.
Future industry regulations, similar to the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), will likely mandate the use of quantum-resistant methods. You should also talk to your vendors now. Ask your cloud providers and software suppliers about their roadmaps for implementing PQC. Your organization’s security depends on the readiness of your entire technology supply chain.
Proactive industry leaders are already making this transition. For example, ExpressVPN has integrated post-quantum protections into both its proprietary Lightway protocol and its implementation of WireGuard. By using a hybrid approach that combines a classical algorithm with a quantum-resistant algorithm, ExpressVPN protects its user traffic against the immediate HNDL threat. This serves as a tangible example of a major vendor implementing the forward-thinking security posture required in the post-quantum era.
FAQ: Common questions about quantum-resistant encryption
What encryption algorithms are quantum-resistant?
As of August 2025, there are three National Institute of Standards and Technology (NIST)-standardized quantum-resistant algorithms: Federal Information Processing Standard (FIPS) 203, FIPS 204, and FIPS 205. These standards are based on algorithms selected from different families of mathematical problems that are believed to be secure against quantum computers.
- For general encryption and key exchange, the primary standard is FIPS 203, which is based on the CRYSTALS-Kyber algorithm.
- For digital signatures, the primary standards are FIPS 204 (based on CRYSTALS-Dilithium) and FIPS 205 (based on SPHINCS+).
These are the first official post-quantum cryptography algorithms, and you can expect to see them integrated into software and hardware products.
Is 256-bit AES considered quantum-resistant?
Yes. Symmetric encryption, like the Advanced Encryption Standard (AES), is not nearly as vulnerable to the quantum algorithm that breaks asymmetric systems. A quantum search algorithm could theoretically speed up a brute-force attack on symmetric keys, reducing their effective strength. However, to counter this, you simply need to use a larger key size. While AES-128 is considered at risk, the 256-bit key length of AES-256 provides more than enough security to be considered quantum-resistant.
Is TLS 1.3 quantum safe?
No, the standard version of Transport Layer Security (TLS) 1.3 is not quantum safe. TLS is the main encryption protocol that secures internet traffic (HTTPS). It uses a combination of symmetric and asymmetric encryption. While its symmetric part using Advanced Encryption Standard (AES) is fine, the asymmetric part used for the initial key exchange, usually with elliptic curve cryptography (ECC), is vulnerable to quantum attacks. The solution is a post-quantum version of TLS that uses hybrid encryption during the handshake, combining a classical algorithm with a new quantum-safe algorithm like Kyber.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN