What is neighbor spoofing, and how can you stop it?
If you’ve ever answered a call that looked local, only to hear a recorded message or an unexpected sales or warning call, you’ve likely encountered neighbor spoofing. In this kind of scheme, perpetrators manipulate caller ID information to make their calls appear to be coming from nearby, which increases the chance that the target will pick up.
This guide explores what neighbor spoofing is, how it works, why it’s risky, and what you can do to reduce the impact of spoofed calls.
What is neighbor spoofing?
Neighbor spoofing is a type of caller ID spoofing where scammers deliberately change the information shown on someone’s phone to make a call look like it’s coming from a nearby number. The call doesn’t actually come from that number, even though it’s what appears on the screen.
Spoofed calls are sometimes used to check whether a phone line is active. Other times, scammers use automated messages or live calls in an attempt to steal money or personal information. They might also ask victims to press a button to hear an important message.
Because the number seems familiar, people may not question it if someone asks them to provide certain details. This can increase the risk of scams, including identity theft.
In the U.S., caller ID spoofing is illegal when it’s used to defraud, cause harm, or obtain something of value. The Federal Communications Commission (FCC) allows spoofing in limited cases where it isn’t deceptive; for example, when a doctor calls a patient from their personal mobile and wants to display the office number rather than their own.
How neighbor spoofing works
Neighbor spoofing is based on the fact that people generally decide whether to answer based on the number they see, not who’s actually calling. For example, according to the U.K. Home Office, 96% of mobile users decide whether to answer a call based on the number on their screen, and 75% would not pick up if it was from an unknown international number. In other words, when a call looks ordinary or local, it’s less likely to raise suspicion.
Scammers are aware of this. They typically use internet-based calling services that allow them to set or alter the caller ID information before a call is placed. Instead of displaying their real number, they manually enter the number they want recipients to see.
In many cases, they select a number that shares the same area code and prefix as the target’s phone number. This makes the call appear local, even if it originates from another city or even country.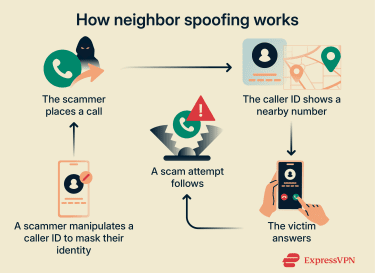
When the call enters the phone network, it carries the supplied caller ID information with it. Most consumer phones simply display that number without confirming whether the caller actually owns it. Newer caller ID verification systems (such as STIR/SHAKEN in the U.S.) help flag suspicious calls, but they don’t eliminate spoofing entirely, especially for international calls.
To reach potential targets, scammers gather phone numbers from publicly available sources, online sign-ups, marketing lists, or data breaches. They may also change the displayed number frequently, which makes it harder to block individual calls.
Why neighbor spoofing is dangerous
The real risk of neighbor spoofing isn’t the call itself, but what can follow once a scammer gets a response. Spoofed numbers are often used to create a false sense of trust by making a call look like it’s coming from a familiar or legitimate caller.
Once scammers have created that trust, they may use social engineering tactics, such as false urgency or authority, to request payments or steal personal details.
Even a short conversation can expose information that scammers can later reuse or combine with other data, raising the risk of identity theft or financial loss.
In some cases, the damage escalates fast. Victims may be persuaded to move money or share account details under pressure, believing they’re preventing a larger problem, such as avoiding account freezes. For example, in one reported spoofing case from CBS, scammers spoofed a woman’s bank’s phone number and convinced her that she needed to quickly transfer money to another account (one controlled by the scammers).
Common characteristics of neighbor spoofing
Neighbor spoofing often appears as part of large-scale robocall campaigns, though some calls also involve live scammers. A few common patterns tend to show up:
- Unexpected contact: The call comes out of the blue, without prior interaction or a clear reason for the call.
- Automated or scripted messaging: Many neighbor spoofing calls use prerecorded robocalls or rigid scripts. Some ask the victim to press a button to continue or to speak to a live agent.
- Urgent or threatening language: The caller introduces a problem that supposedly needs immediate attention, often involving consequences or penalties.
- Requests for payment or sensitive information: The conversation includes demands for money, account details, verification codes, or personal data.
All these are typical signs of phishing.
How to prevent neighbor spoofing
No single tool can fully prevent neighbor spoofing, but there are ways to minimize the risk of being targeted.
Don’t answer or return suspicious calls
Unexpected calls are often part of large-scale scam campaigns. When people answer or interact with these calls, they may receive additional scam attempts later, sometimes from different spoofed or similar-looking numbers.
It helps to distinguish between screening a call and engaging with it. Screening means letting a call go unanswered or reviewing it later through voicemail, while engaging means answering, returning a missed call, or interacting with the caller. The first limits contact, but the second creates it, which is more risky. So if you aren’t expecting the call, screening is always the safer option.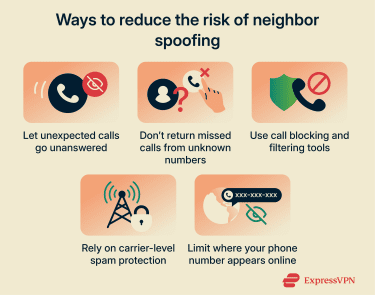
Use call blocking and filtering features
Most phone carriers offer call blocking and filtering tools designed to reduce unwanted calls. These systems analyze calling patterns, known scam indicators, and user reports to label or block suspected spam and spoofed calls.
However, blocking individual numbers has limits. Because spoofed calls can display falsified caller IDs, the same number may not appear again. Providers often rely more on pattern-based filtering than on number-by-number blocking alone, such as tracking withheld or international calls.
Note that while these tools can cut down the volume of scam calls, they don’t stop all of them. Some spoofed calls still reach phones, especially when they appear to be from local or legitimate numbers. It’s important to stay alert to and suspicious of any calls that involve urgent requests, payment demands, or personal information requests.
Protect your phone number online
Phone numbers tend to spread over time through public exposure and data reuse. Websites, social media profiles, online forms, and older accounts often continue to display numbers long after they’re actively used.
Limiting where your number appears reduces your digital footprint and your long-term exposure to spoofed calls. When fewer public sources link a phone number to someone’s personal details, scammers have fewer opportunities to reuse it across different scam attempts.
What to do if you answer a spoofed call
If you answer a spoofed call, it’s important to know what to do. Even a short interaction can create risk, but what happens next can make a big difference.
Hang up immediately
Ending the call quickly limits further contact and pressure, which helps stop the conversation from going any further. Scam calls often depend on keeping someone on the line, so once a call feels suspicious, staying on it rarely helps and can increase risk instead.
Some people try to scambait callers by staying on the line to keep the conversation going as long as possible and to gather more information. However, engaging with scammers, even as a joke, can expose your personal details or encourage follow-up contact.
Don’t share personal information
Scammers often start with small requests to sound legitimate, which can make the conversation feel routine. Details that seem harmless, such as confirming a name or account detail, can still be reused later.
If a caller claims to represent a bank, service provider, or government agency, it’s safer to end the call and contact the organization directly using their official number. You can then verify the request and check whether the call was legitimate.
Monitor accounts for suspicious activity and report the call
Spoofed calls don’t always lead to problems right away. In fact, the results might not start appearing until days or weeks later. It’s important to check for any unexpected charges, password reset emails you didn’t request, new payees added to an account, or alerts about unfamiliar login attempts, as these can all indicate follow-on activity.
Unfamiliar texts, emails, or verification codes can also be suspicious. They might indicate that someone is trying to use your details to access existing accounts or open new ones. Identity monitoring tools can help detect this type of activity earlier, so you can protect your personal information and accounts.
Can you find out who spoofed you?
Usually, it’s extremely difficult to identify who’s behind a spoofed call. This is because the number displayed on your phone doesn’t belong to the caller at all. And because that number has been falsified, reporting the call rarely leads directly back to the person who placed it.
Since calls pass through several networks before they reach a phone, they may move between different carriers or across international systems, which makes it even harder to follow a clear trail back to the source.
Many internet-based calling services and Voice-over-Internet-Protocol (VoIP) platforms make it easy to manipulate caller ID information, which scammers abuse to display almost any number while hiding their true origin.
What phone carriers and authorities can do
Phone carriers can help limit spoofed calls; they have some oversight because they manage how calls move across networks. Many now use network-level tools that look for patterns linked to scam calls and block or label them before they reach phones.
Some providers also offer call blocking and filtering products that handle unwanted calls in specific ways. This can include sending certain calls straight to a junk voicemail box, such as:
- Calls from the provider’s blocklist of known nuisance or scam callers.
- Calls from numbers the user has previously blocked.
- Certain categories of calls, such as those with withheld numbers or calls originating internationally.
Regulators are also trying to close the gaps scammers rely on. In the U.K., for example, authorities have pushed providers to block calls that come from abroad but display U.K. phone numbers, except in limited legitimate cases. This will help to prevent overseas scam calls from appearing local and trusted.
When reporting helps
Reporting a spoofed call usually won’t reveal who made it. That said, reports still serve an important purpose. Regulators and carriers can use reports to try to spot patterns, link related complaints, and identify large-scale scam campaigns. Over time, this information helps improve call blocking systems and supports enforcement efforts so that spoofed calls can’t get through.
In the U.S., you can file a phone complaint to the FCC, and in the U.K., you can report spoofed calls to Report Fraud.
Can a VPN protect you from neighbor spoofing?
Neighbor spoofing happens on the phone network, not the internet. Phone calls use telecom systems that sit outside the traffic a virtual private network (VPN) can see or control. That means a VPN has no way to affect how calls are routed or which number appears on your screen.
However, VPNs can help improve your privacy elsewhere. They limit how much of your online activity can be linked to your IP address, which can reduce tracking when you’re online. This can help cut down on how much of your personal data circulates online in general. The less personal information there is, the less a scammer has to target you with.
That said, a VPN doesn’t protect information you choose to share directly. If you enter your phone number into online forms, accounts, or services, a VPN can’t prevent that data from being collected or reused.
FAQ: Common questions about neighbor spoofing
Is neighbor spoofing illegal?
In the U.S., it’s illegal to spoof caller ID information when it’s done with the intent to defraud, cause harm, or wrongfully obtain something of value. The Federal Communications Commission (FCC) allows caller ID spoofing in limited, legitimate cases, but deceptive spoofing tied to scams is unlawful. Enforcement can be difficult, especially when calls originate outside the country.
What are the signs of neighbor spoofing?
Neighbor spoofing usually involves unexpected calls that appear local or familiar, sometimes mirroring your own number. Common red flags include creating a sense of urgency, pressuring you to act immediately, or asking for money, account details, or personal information. These calls often arrive without any prior contact or clear reason. Scammers may use a prerecorded robocall message or connect you to a live caller following a script.
What should I do if I get a call from my own number?
Calls that appear to come from your own number are a known spoofing tactic. This doesn’t mean your phone or account has been taken over. It simply means the caller ID information was falsified, and you can ignore the call.
Can text messages be spoofed the same way as neighbor spoofing?
Yes. Scammers can spoof sender information in text messages as well as phone calls. Texts may appear to come from local numbers or trusted organizations, even when they don’t, and these are often used in similar scam attempts.
Will neighbor spoofing ever stop completely?
No one can tell with certainty. While carriers and regulators continue to improve blocking, verification, and enforcement, spoofing techniques evolve over time. Current efforts focus on reducing harm and limiting large-scale abuse rather than stopping every spoofed call. There are also steps users can take to try to limit neighbor spoofing, such as screening suspicious calls and using the available filtering tools.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN