What is DarkSide ransomware, and how does it work?
DarkSide was a cybercriminal group that operated a ransomware-as-a-service (RaaS) model. First emerging in the latter half of 2020, the group developed the DarkSide ransomware and leased it to affiliate criminals in exchange for a portion of ransom payments.
Before ceasing public operations in 2021, the group and its ransomware were responsible for several high-profile attacks across industries ranging from construction to energy. And although the DarkSide operation itself is no longer active, its tooling and techniques continue to influence modern ransomware campaigns.
This guide explains how DarkSide-style ransomware attacks work, how they can be detected, and how organizations can respond.
What is DarkSide ransomware?
DarkSide ransomware encrypted files on servers and endpoints within targeted networks, allowing attackers to demand ransom payments in exchange for decryption keys. The group behind it operated a ransomware-as-a-service (RaaS) platform, leasing DarkSide to affiliates who conducted attacks independently and paid DarkSide a percentage of any ransom collected.
What made DarkSide especially dangerous was the use of double extortion tactics. Before encrypting a victim’s data, DarkSide operators would exfiltrate sensitive information from compromised systems. This stolen data became leverage for a second threat: if victims refused to pay the ransom, attackers threatened to release the confidential information publicly.
This dual-threat approach significantly increased pressure on victims. Organizations faced not only the operational disruption of systems but also potential regulatory penalties, reputational damage, and competitive harm from exposed proprietary data.
It’s been noted that DarkSide’s code resembled software used by REvil, another infamous ransomware group. This suggests the two may be linked in some way, though no definitive connection has been confirmed.
How DarkSide ransomware works
Like many modern ransomware operations, DarkSide followed a multi-step attack lifecycle rather than immediately encrypting data after initial access. The typical key phases were:
- Infiltration: The cybercriminals first accessed targets through compromised credentials or software vulnerabilities.
- Lateral movement: Once inside a network, attackers moved laterally between connected systems to expand access and identify valuable targets.
- Privilege escalation: Attackers attempted to obtain elevated privileges, enabling fuller control over systems and security mechanisms.
- Internal reconnaissance: With access in place, attackers scanned the network to identify sensitive data and critical systems to target.
- Execution: As part of its double extortion strategy, DarkSide operators exfiltrated sensitive data before encrypting systems. Victims were then pressured to pay a ransom to restore access and prevent the public release of stolen information.
This lifecycle occurred in enterprise environments using a variety of specialized tactics, tools, and stealth methods.
Key DarkSide cyberattacks and their impact
DarkSide was behind several significant cyberattacks. Below are some of the most significant ones.
Colonial Pipeline
The most high-profile DarkSide cyberattack was the Colonial Pipeline attack discovered on May 7, 2021.
The attack forced the Colonial Pipeline company, one of the largest refined petroleum product pipelines in the U.S., to shut down 5,500 miles of pipeline supplying fuel to the Southeast U.S. The shutdown lasted five days, creating widespread fuel shortages. Panic buying led to fuel stations running out of gas, and fuel prices reached their highest level since 2014.
Colonial Pipeline confirmed that it paid the 75 Bitcoin (approximately $4.4 million) ransom. The US Department of Justice later recovered 63.7 Bitcoin from the initial ransom payment, which was valued at approximately $2.3 million at the time.
Brenntag
DarkSide breached the North American division of chemical distributor Brenntag in May 2021. The ransomware gang claimed to have stolen 150GB of data during the attack and created a private data leak page containing descriptions of the stolen data types along with screenshots as proof. According to the group’s claims, the data included chemical formulas, sensitive employee data, ongoing projects, and more.
The initial demand for this attack was 133.65 Bitcoin, which at the time was $7.5 million. However, the company paid $4.4 million after negotiating with the group.
CompuCom
Another noteworthy incident occurred in March 2021, when CompuCom, a managed IT service provider that offers remote support, hardware repair, software repair, and other IT services, suffered a cyberattack that was widely attributed to DarkSide. The attack commenced over a weekend, during which the company’s portal suffered an outage that kept customers from accessing it.
The outage disrupted customer services and was reported to have cost the company millions of dollars in lost revenue.
How DarkSide targets enterprise infrastructures
Targeted ransomware campaigns by the DarkSide group specifically focused on high-revenue organizations to maximize ransom payment potential. Below are the typical phases of an enterprise-level attack.
Initial access phase and attack vectors
The DarkSide group and its affiliates often gained initial access to enterprise networks by purchasing credentials or remote access from network access brokers, rather than conducting reconnaissance themselves.
Once access was obtained, they exploited unpatched software vulnerabilities, conducted brute-force attacks against weak passwords, and leveraged services such as Remote Desktop Protocol (RDP). For example, the Colonial Pipeline attack is believed to have originated from a compromised remote access credential.
Phishing campaigns targeting employees were also used to steal credentials or deliver malicious payloads. What’s more, DarkSide affiliates sometimes deployed malware through botnet loaders to further compromise systems.
Lateral movement
After gaining initial access, DarkSide affiliates worked to expand their presence within the network. This involved moving laterally between connected systems to identify high-value targets and security weaknesses.
Credential harvesting
Once inside a network, DarkSide affiliates worked to capture authentication credentials from compromised systems. They used legitimate administrative tools to extract passwords, security tokens, and password hashes, allowing them to access additional accounts and systems without triggering security alerts associated with brute-force attempts.
Escalating to domain-level privileges
A primary objective during lateral movement is obtaining Domain Controller or Active Directory access. Domain Controllers manage authentication and permissions across the entire network, while Active Directory serves as the central database of users, computers, and resources. Compromising these systems enabled DarkSide attackers to enumerate the entire network structure, identify sensitive data locations, and obtain the elevated permissions needed for widespread ransomware deployment.
Maintaining stealth
DarkSide affiliates moved methodically to avoid detection by security teams. Attackers sometimes disabled logging and auditing features on intermediate systems, reducing the digital trail that incident responders could use to track their activities.
Data exfiltration and encryption
Before encrypting systems, DarkSide attackers typically exfiltrated sensitive data after escalating privileges and gaining broad access to the target system.
They would commonly steal data through encrypted outbound file transfers. By abusing standard network protocols, they could disguise malicious data theft as routine administrative activity. This made detection significantly more challenging for security teams.
Once exfiltration was complete, the attackers proceeded to encrypt systems and data across the network. This rendered critical files and services inaccessible and disrupted business operations.
Victims would then find ransom notes on the affected system that combined both threats: payment was needed to restore access to encrypted systems and to prevent the public release of sensitive data. This dual approach increased the pressure to pay by amplifying the risks.
How to detect DarkSide ransomware activity
Early detection of DarkSide-style ransomware activity can help dramatically improve response outcomes.
Early warning signs
Several early indicators can suggest potential ransomware activity. Some key signs to look out for include the following:
- Unusual command-line activity: Many ransomware families, including DarkSide, use PowerShell to delete shadow copies (backup snapshots of a system). Remember, however, that PowerShell activity alone is not conclusive evidence of an attack, as it's commonly used for legitimate administrative tasks.
- Network activity spikes: A sudden spike in data transmission through your system could indicate ransomware communicating with a command-and-control (C2) server. Note that legitimate activities such as scheduled backups or large file transfers can also cause similar patterns, so you should analyze spikes against general network baselines.
- Unusual administrative logins or privilege changes: Unexpected elevation of account privileges or administrative access from unusual locations or times can signal that attackers are escalating their control within the network.
- Unexpected outbound connections: Network connections to suspicious infrastructure such as Tor exit nodes, known malicious domains, or unfamiliar IP addresses may indicate communication with attacker-controlled servers.
- Security tool disruption or log tampering: Endpoints suddenly losing antivirus protection or event logs being cleared are strong indicators of an attacker’s attempts to hide their activities.
Signs of encryption in progress
If you notice these signs, it could be that the final stages of the attack are in progress:
- Sluggish system performance: Encrypting all files across a system is a resource-intensive process, leading to slowdowns in system performance accompanied by a spike in CPU or disk usage.
- Unexpected file changes: Files unexpectedly having their names or extensions changed can indicate encryption in progress.
Behavioral and anomaly-based detection
Behavioral analysis is an effective detection method, as it monitors system activity for suspicious patterns rather than known malware signatures. This can help to identify unknown variants and zero-day ransomware based on activity, like connections to malicious domains, lateral movement between internal systems, and unusual outbound data transfers.
In addition to rule-based behavioral analysis, anomaly-based detection aims to identify deviations from normal system behavior. Research has shown that machine-learning-based anomaly detection frameworks can detect ransomware-related activity in controlled laboratory environments by analyzing patterns in system activity logs derived from known ransomware samples.
That said, while these approaches show promise, their effectiveness depends on the quality of the baseline data and how closely production activity matches the conditions the models were trained in.
Tools and monitoring techniques
Various cybersecurity tools exist to help detect ransomware attacks via continuous monitoring. Endpoint detection and response (EDR) solutions continuously monitor processes and memory to detect ransomware-like behavior by looking for unusual activity, like high CPU usage or attempts to disable antivirus software.
Network monitoring using intrusion detection systems (IDS) helps identify ransomware behavior like communication with malicious IP addresses or C2 servers. Alongside this, security information and event management (SIEM) systems can correlate events across multiple sources.
Another worthwhile approach is using deception technologies like honeypots to attract ransomware attacks to decoy file shares, providing a key early detection signal.
Recovery strategies after a DarkSide ransomware attack
Given how widespread ransomware attacks are, it’s essential to have a recovery plan in place to minimize the impact of a potential DarkSide-style ransomware incident.
Immediate containment steps
Immediately isolate infected systems by disconnecting them from networks, disabling wireless and Bluetooth connections, and unplugging shared drives. This prevents ransomware from spreading to additional systems.
In some cases, quickly powering off affected systems may interrupt encryption and limit damage. However, if encryption appears complete or forensic investigation is required, systems should remain powered on but isolated to preserve evidence and support incident analysis, in line with guidance from the Cybersecurity and Infrastructure Security Agency (CISA) and incident response professionals.
Incident response team activation
Organizations should either have on-site incident response teams prepared or should engage third-party security investigation firms upon discovering attacks. Colonial Pipeline brought in cybersecurity consulting firm Mandiant to investigate the breach and coordinate response efforts.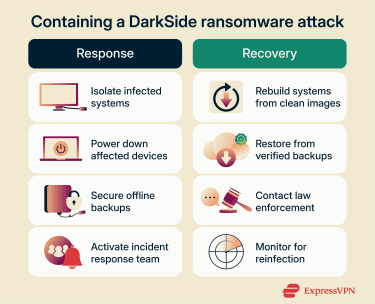
Detailed recovery and restoration process
Organizations should ensure there are pre-configured system templates and backup hardware to rebuild infected computers from scratch. This ensures clean installations free from ransomware signatures.
Working with law enforcement and regulatory bodies
Contact law enforcement immediately in the event of a ransomware attack. In the U.S., incidents can be reported to the FBI via phone at 1-800-CALL-FBI or online through the Internet Crime Complaint Center (IC3) website. Law enforcement agencies may provide guidance and, in some cases, assist with asset recovery.
How to prevent DarkSide and other ransomware attacks
Preventing ransomware attacks involves following strict cybersecurity practices to reduce the risk of attack and enhance the ability to recover in a worst-case scenario.
Implement MFA and zero-trust principles
Enable multifactor authentication (MFA) on all accounts, especially remote access services. It’s also worthwhile to use phishing-resistant passwordless authentication methods rather than relying on traditional tools like SMS-based two-factor authentication (2FA).
Organizations should also implement zero-trust systems that verify every access request regardless of network location and continuously enforce least-privilege access. This limits attackers’ ability to move laterally through the system.
Back up all data regularly
Since DarkSide-style ransomware operators target backup files specifically to prevent recovery, having a thorough backup plan can be crucial in recovery. Maintain comprehensive backup procedures using the 3-2-1-1 strategy: three backups on two different media types, with one copy stored off-site and one read-only copy. It’s also crucial to test backups regularly to ensure they function correctly.
Train staff to recognize social engineering
Employee awareness training helps staff recognize phishing attempts, suspicious emails, and social engineering tactics that attackers use to gain initial access to networks. It’s also worth training employees to report suspicious activity quickly without fear of consequences, as this enables faster incident response and threat containment.
Use email filtering
Deploy email filtering solutions that scan incoming messages for phishing indicators and malicious attachments. These systems improve protection by blocking threats before they reach end users, reducing reliance on human judgment alone to identify sophisticated attacks.
Keep systems and software patched and updated
Apply security patches promptly to address known vulnerabilities. Ransomware groups, including DarkSide affiliates, have exploited known vulnerabilities in widely used enterprise software (such as vulnerabilities affecting VMware ESXi, a type of server software used by organizations to run multiple virtual machines on a single physical server) when organizations failed to apply available patches.
Use secure network practices
It’s essential to establish secure network practices to limit the attackers’ lateral movement within a network. Having clear network segmentation keeps ransomware from being able to spread across other devices within a network. CISA also suggests having a demilitarized zone that eliminates unregulated communication between information technology (IT) and operational technology (OT) networks.
FAQ: Common questions about DarkSide ransomware
What is ransomware-as-a-service (RaaS)?
Ransomware-as-a-Service (RaaS) is a business model where ransomware developers lease their malware to affiliates who conduct attacks. Developers maintain the ransomware infrastructure, while affiliates identify targets, execute attacks, and split the ransom payments with the developer.
How can businesses protect themselves against ransomware attacks?
There are several steps businesses should follow to defend against ransomware attacks, like implementing multi-factor authentication (MFA) on all accounts and maintaining comprehensive backups with the 3-2-1-1 strategy. Additionally, they should keep all software up to date, follow key network security practices, and rigorously train employees to recognize phishing or social engineering attempts.
What are the legal implications of paying a ransomware demand?
Organizations may face regulatory penalties for paying ransoms to sanctioned entities or groups. The U.S. Department of Treasury has warned that ransom payments to actors on its sanctions list may violate U.S. sanctions regulations. While not all ransom payments are automatically illegal, organizations should consult legal counsel and report incidents to the relevant authorities if they are considering paying ransom.
How does DarkSide ransomware get deployed in attacks?
DarkSide-style ransomware generally gets deployed after attackers gain initial access through compromised credentials or unpatched security vulnerabilities. Affiliates often purchased pre-compromised network access from brokers on dark web marketplaces, rather than conducting initial intrusion themselves.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN