CEO fraud: How it happens and how to protect your business
Sometimes, all it can take is one convincing message to move real money. A finance manager might get an email that looks like it came from the CEO, asking them to pay an invoice. It looks normal, the tone feels familiar, and the sender name seems correct. But that’s the trap of CEO fraud. This guide explains what CEO fraud is, how these scams typically unfold, who attackers target, and the practical steps organizations can take to reduce risk.
What is CEO fraud?
CEO fraud is a type of internet fraud where an attacker pretends to be a senior executive to trick the victim into sending money or sharing sensitive information. It typically targets specific roles that can move money or access sensitive data, like an HR senior manager, and the request is usually a routine business task, like paying an invoice. The scam relies on social engineering, rather than technical exploits or malicious software.
Is CEO fraud the same as business email compromise (BEC)?
No, CEO fraud is a type of BEC. BEC is the broad category of scams where attackers use emails to impersonate trusted people or organizations so they can trick you into sending money or sensitive information.
CEO fraud is one example of this, focused specifically on impersonating senior executives. Other BEC schemes can be vendor invoice fraud, credit card fraud, account takeover scams, and payment diversion attacks where attackers pose as some form of business entity.
These types of attacks are very popular, too. In fact, between October 2013 and December 2023, the FBI’s Internet Crime Complaint Center (IC3) stated it received 305,033 BEC reports, with an exposed dollar loss of about $55.5 billion. Similarly, the IC3 Internet Crime Report 2024 stated that BEC was the second highest in financial impact across all complaints reported to IC3 in 2024, accounting for roughly $2.77 billion in losses.
How CEO fraud works
CEO fraud typically begins with reconnaissance. Attackers use publicly available information to understand how a company operates: who the senior executives are, who supports them, who is authorised to approve payments, and how internal emails are usually written and signed. This preparation allows the attacker to blend in and avoid raising suspicion.
Once they understand the environment, the attacker selects a specific employee and sends an email that appears to come from a senior executive, such as a CEO or CFO.
The message usually asks for something that sounds ordinary, such as paying an invoice, transferring funds, or sharing sensitive documents or information. More recent scams use AI to generate messages that closely match an executive’s writing style or create realistic-looking email chains.
In most cases, the message also creates a time crunch. The victim may be told the matter is confidential or business-critical in order to push them to act fast instead of verifying.
Common CEO fraud attack methods
CEO fraud always involves impersonating a senior executive. What varies is how the impersonation is delivered and reinforced. Common methods include:
Email impersonation
In most cases, the attacker sends an email directly to the victim’s inbox. They may use a spoofed email address, where they make the sender's address look like that of the senior executive. Other times, attackers may simply compromise the email of the executive in question.
Conversation hijacking
Sometimes, scammers that have managed to compromise an internal or vendor email account slip into an existing email thread. Because it follows earlier messages, it can feel more legitimate than a new, unexpected request.
Abuse of trusted services
Attackers may send requests through platforms the victim uses for work, such as document signing tools, cloud storage services, or payment notifications. Since the company, or at the very least employees within the company, use these tools, receiving a message might not seem suspicious.
Email-to-phone escalation (vishing)
After an initial email, the victim may be asked to switch to a phone call to confirm details or discuss the request. If the victim hears a real person, especially one claiming to be an executive or partner, it can make the request feel more urgent and harder to question.
Virtual meeting or conference impersonation
In some cases, attackers exploit virtual meetings or conference calls to make their requests more believable. This can involve joining a real meeting under a trusted name, or sending a follow-up message immediately after a scheduled call to imply prior discussion. The timing and context make the request feel legitimate and urgent.
Real examples of CEO fraud attacks
Unfortunately, many organizations have found themselves targeted by CEO fraud, often after a single convincing message or call.
In late 2021, several French companies were targeted as part of a coordinated CEO fraud campaign. According to Europol, the European Union’s law enforcement agency, a criminal network impersonated company executives and contacted finance staff with urgent and confidential payment requests. The same group successfully tricked a real estate developer into transferring €38 million, believing the funds were being sent to a legitimate French accounting firm.
In 2019, a British energy company also fell victim to a scam that used voice impersonation. According to The Wall Street Journal, a senior executive received a phone call that appeared to come from the company’s CEO, authorizing an urgent transfer of $243,000. The voice on the call sounded convincing enough that the transfer was approved.
Who is at risk of CEO fraud?
High-risk roles targeted by CEO fraud
CEO fraud usually doesn’t target company roles at random. Apart from executives and senior leaders who are targeted through account takeovers, attackers focus on people whose roles give them access to money, sensitive data, or authority to make decisions, including:
Finance and accounting teams
Employees who handle wire transfers, invoice payments, or bank account changes are frequent targets. These tasks often come with tight deadlines, especially during payment cycles, and urgent requests from leadership may not seem unusual. Scammers exploit that pressure to push fraudulent payments through quickly.
Human resources teams
HR roles typically manage payroll, tax forms, and employee records, all of which contain valuable personal information. Because they already deal with confidential data, requests to update direct deposit details or process payroll changes can look routine, even when they aren’t.
Executive assistants and administrative staff
Individuals acting as a gatekeeper for leadership may be asked to relay messages, schedule payments, or handle urgent requests on an executive’s behalf. That trust, combined with limited context, can make it harder to spot when a request isn’t legitimate.
Procurement and vendor management roles
These roles regularly communicate with suppliers and manage invoices and payment details. Because vendor relationships are ongoing and familiar, scammers can exploit that trust through fake invoice requests or payment diversion schemes.
Industries most affected by CEO fraud
Industries that are commonly targeted include:
- Finance and banking: These organizations process large transfers and complex financial activity, which makes executive impersonation attempts more attractive to attackers.
- Healthcare: Healthcare providers handle sensitive personal data alongside financial transactions, making them appealing targets for BEC and related scams.
- Manufacturing: Frequent vendor payments and high-value orders create opportunities for invoice fraud, impersonation, or identity theft, especially within complex supply chains.
- Technology: Tech companies and Software-as-a-Service (SaaS) providers hold valuable intellectual property and client data, which can invite attempts to exploit communication and payment processes.
- Legal services: Law firms regularly manage confidential information and high-value transactions, making them targets for scams that impersonate partners or trusted clients.
Warning signs of CEO fraud
CEO fraud often feels convincing because the request itself doesn’t always look obviously wrong. Warning signs to look out for include:
- Unusual urgency or secrecy: Requests are framed as time-critical or confidential, with pressure to act immediately. You may be told the matter can’t wait or shouldn’t be shared with anyone else.
- Requests that bypass standard processes: The message asks you to skip approvals, audits, or secondary sign-offs. Language like “I’ll explain later” or “don’t loop anyone else in” is often used to discourage checks.
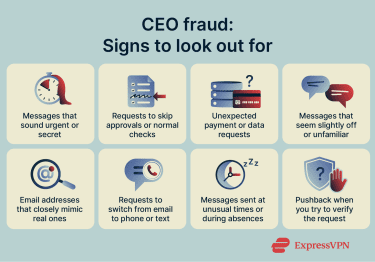
- Unexpected payment or data requests: You’re asked to make a sudden wire transfer, pay an invoice, buy gift cards, or share sensitive information. This can also include requests for payroll changes, employee records, or tax documents that you weren’t expecting.
- Changes in communication style: The message sounds slightly off compared to how the executive normally writes. This might show up as unusual phrasing, a different tone, or formatting that doesn’t quite match previous emails.
- Suspicious sender details: The sender’s email address looks similar to a real one but includes subtle spelling changes or extra characters. Replies may not line up cleanly with known internal email threads.
- Requests to switch communication channels: You’re asked to move from email to a phone call, text message, or messaging app to confirm details. The contact information provided may not match what’s on record.
- Unusual timing: Messages arrive outside normal working hours or during known absences, such as when leadership is traveling or unavailable to confirm the request.
- Resistance to verification: When you try to double-check the request, you receive pushback. The sender may discourage callbacks, delay confirmation, or create additional pressure to proceed without checks.
How to prevent CEO fraud
The most effective defenses against CEO fraud focus on education and minimizing risk, rather than simply blocking any and all suspicious messages. This involves a combination of employee awareness, clear processes, and regular checks.
Employee awareness and security training
Training helps employees recognize the patterns behind urgent or authoritative requests and understand when to pause. Rather than making people suspicious of everything, it’s important to teach others how to be confident in spotting red flags. Effective training focuses on:
- Recognizing pressure tactics like urgency, secrecy, and authority.
- Understanding how modern scams can appear, including fake threads or trusted platforms.
- Reinforcing that questioning unusual requests is expected, not risky.
- Educating people that slowing down to double check requests can help minimize risk.
- Refreshing training regularly so it keeps pace with changing tactics.
Secure payment authorization procedures
Clear financial controls reduce the risk that a single request can move money without oversight. They matter most when requests feel urgent or unusual, because that’s when people can be more likely to skip checks. Strong payment processes usually include:
- Separating payment authority so no one person can approve a transfer alone.
- Multi-step approvals for wire transfers, invoices, and bank account changes.
- Using secure online payment methods to protect transactions.
- Out-of-band verification for financial requests, rather than replying to the same message.
- Clear rules for handling urgent or last-minute changes.
- Logging and reviewing payment requests to spot irregularities.
Email and account security
CEO fraud relies on social engineering rather than technical exploits, but securing key accounts still helps limit your exposure. Basic protections include using strong, unique passwords, enabling multi-factor authentication (MFA), and watching for unusual login activity or access attempts. It’s also important to limit access to shared inboxes and financial systems, so only the people who need them for their work can use them.
You can also set up email security tools that detect look-alike domains that closely resemble your company’s real address, since attackers often use small changes to appear legitimate. Some organizations also register common misspellings or variations of their domain name to prevent attackers from using them to impersonate the company.
Clear verification and escalation policies
Policies only work if they’re easy to follow under pressure. When something feels off, clear guidance helps employees know how to pause, check the request, and involve the right people without second-guessing themselves.
Policies should include information about how to verify executive or vendor requests, who to contact when in doubt, and when and how to escalate concerns. It’s also important that everyone knows which policies apply to them, including senior leadership. Finally, because CEO fraud tactics and business workflows change over time, policies should be regularly tested and reviewed.
What to do if you’re a victim of CEO fraud
If you’ve been targeted by CEO fraud, acting quickly matters. Even if you’ve already sent money or data, you can help limit further loss and support recovery by reporting through the correct channels.
Immediate steps to take
First, focus on containing the scam and documenting it. The sooner you identify and escalate the incident, the better the chance of reducing its impact. You should:
- Contact your bank or payment provider immediately: If a payment was made, notify your bank or payment processor right away. In some cases, you can freeze or recall transfers if you take action quickly.
- Secure affected accounts and systems: Lock down any email accounts, devices, or systems involved in the incident to prevent further misuse.
- Reset compromised credentials: Change passwords and revoke access for any exposed accounts, especially email and financial systems.
- Preserve evidence: Keep copies of emails, message headers, call details, transaction records, and logs. This information can be important for internal investigations, banks, insurers, or law enforcement.
- Notify internal teams: Inform your IT, security, finance, and leadership teams as soon as possible so they can coordinate next steps and assess wider risk.

Reporting the incident to authorities
Reporting CEO fraud is still important, even if you’re not sure the money can be recovered. Reports help authorities track patterns, warn other businesses, and improve future prevention efforts. In some cases, timely reporting can also support fund recovery or insurance claims.
In the U.S., you can report CEO fraud and BEC incidents to the FBI’s IC3, which collects national reports and works with law enforcement and financial institutions to help prevent fraud. In the U.K., you can report incidents to Report Fraud, the national fraud and cyber crime reporting centre run by the City of London Police.
Legal and compliance considerations
CEO fraud can trigger legal and compliance obligations, especially if you lose money or share sensitive data. Depending on where your business operates and what information was exposed, you may need to notify regulators or affected individuals.
These may have strict timelines, so it’s important to assess them early. For example, New York’s updated breach notification law requires companies to inform affected residents within 30 days of discovering an incident that exposes private information.
You may need to look at your contracts with banks, vendors, and partners. Some agreements might ask you to report fraud within a certain time or follow specific steps after an incident. It’s a good idea to keep clear records of what happened, including emails, payments, and actions taken, which helps if you need to deal with audits or insurance claims later.
Legal advice can also help you understand your responsibilities and decide what to do next based on the details of the incident, which is especially important if it involves financial loss or exposed data.
Best tools for detecting CEO fraud
No single tool can stop CEO fraud on its own, but the right combination can help you spot suspicious activity earlier and reduce the chance that a scam goes unnoticed.
Email filtering and AI solutions
Email security tools help detect suspicious messages before they reach your inbox. They look for signs of impersonation, such as spoofed sender details, unusual domains, or language patterns that don’t match normal communication. Some tools also use AI to flag emails that create urgency or request sensitive actions, even when the message looks polished.
Real-time transaction monitoring
Financial monitoring tools watch for unusual payment activity, such as unexpected transfers, changes in payment details, or transactions that don’t match normal patterns. Alerts can give you a chance to pause and review a request before money leaves the account. This kind of monitoring helps catch problems at the payment stage, but it usually works after a request has already been approved. It supports detection, not prevention on its own.
Case management and incident response tools
When something does go wrong, case management tools help teams track incidents in one place. They can centralize emails, logs, payment records, and response actions, making it easier to coordinate between finance, IT, security, and leadership. Although these tools don’t stop CEO fraud from happening, they can help you respond faster and learn from incidents or near-misses.
How virtual private networks (VPNs) can help prevent CEO fraud
A VPN can reduce one risk that can enable CEO fraud: email account compromise. When executives work remotely, they may sometimes connect to unsecured or fake Wi-Fi networks, where attackers can redirect them to convincing fake login or re-authentication pages and capture credentials directly.
A VPN encrypts and tunnels all network traffic, preventing local network attackers from manipulating connections in this way and reducing the likelihood that an attacker gains access to an executive’s mailbox.
VPNs vs. zero trust: What’s better?
| VPN | Zero trust | |
| Goal | Securing the network connection | Controlling access to systems and data |
| How it works | Encrypts traffic between your device and a secure server | Grants access based on identity, device, and context |
| Public Wi-Fi protection | Encrypts traffic on untrusted and public networks | Doesn’t encrypt traffic by default |
| Identity verification | Doesn’t verify user identity or intent | Continuously evaluates identity and access |
| Lateral movement control | Limited | Can restrict access after a compromise |
| Best use case | Encrypting individual connections | Managing access to internal systems |
VPNs and zero trust are often mentioned together, but they serve different purposes. A VPN protects your internet connection, which is especially useful when you work remotely or rely on public Wi-Fi. It reduces the risk of network-level interception, but it doesn’t confirm whether a request is legitimate.
Zero trust focuses on access control. Instead of securing the connection itself, it controls who can access systems and how much they can do. If an account is compromised, zero trust can limit how far an attacker can move by restricting access to only what’s necessary. This is known as lateral movement control.
This is why VPNs and zero trust are often used together, as when combined, they can both help reduce exposure to CEO fraud and contain damage. That said, neither approach can prevent social engineering. That requires effective awareness and training to make sure you can identify potential CEO scams when they appear.
FAQ: Common questions about CEO fraud
What is the most common tactic used in CEO fraud?
The most common tactic used in CEO fraud is executive impersonation via email. Attackers send an email that appears to come from a CEO, CFO, or other senior leader and make a request that looks routine, such as approving a payment, handling an invoice, or dealing with a confidential task.
How can small businesses protect themselves from CEO fraud?
Small businesses can reduce CEO fraud risk by setting clear rules and sticking to them. Require more than one approval for payments, confirm unusual requests through another channel, and make it normal to question urgent instructions, even when they appear to come from leadership.
What are the legal consequences of CEO fraud?
The legal consequences depend on what you lose or expose. If you send money, contracts or insurance policies may apply. If you share personal or confidential data, data protection and breach notification rules may impact you.
Are deepfakes commonly used in CEO fraud?
Yes, deepfakes and AI-generated voices are starting to appear in CEO fraud cases. That said, many incidents still involve basic impersonation and pressure tactics where the scam succeeds when a request isn’t verified, not because advanced technology is used.
What industries are most vulnerable to CEO fraud?
CEO fraud affects many industries, but it shows up more often where employees handle payments, payroll, or vendor relationships. This includes finance, professional services, real estate, manufacturing, healthcare, and energy.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN