Attack surface reduction explained: Principles, techniques, and tools

Every system connects to the outside world through networks, software, and user access. These connections let data and services function, but each one also introduces potential risk.
The more services, permissions, and exposed features a system has, the larger its attack surface becomes. When those elements aren’t actively monitored and controlled, security gaps can accumulate.
A larger attack surface gives attackers more places to probe and exploit, while a smaller, well-managed one is easier to monitor and defend.
In this guide, we explain what attack surface reduction (ASR) is, how it works, and why it matters for modern cybersecurity.
What is attack surface reduction?
ASR involves reducing unnecessary exposure across your systems.
Most attack surfaces fall into three broad categories:
- Digital attack surface: This includes anything that can be reached through a network or the internet, such as websites, applications, online services, connected devices, and software that is outdated or misconfigured.
- Physical attack surface: This includes hardware that can be physically accessed, such as laptops, servers, mobile devices, removable media, and unused or unsecured ports on office equipment.
- Human attack surface: This includes everyday user interactions, such as emails, messages, or requests for access, where people may be tricked into sharing information or granting permissions they shouldn’t.
How attack surface reduction works
In day-to-day terms, ASR comes down to a few recurring actions:
- Understanding what’s actually in use: Identify which services, features, and tools are actively used during normal operations.
- Removing what isn’t needed: Disable or remove features, services, or tools that serve no clear purpose. Fewer active components mean fewer places where issues can arise.
- Securing what must remain accessible: Keep essential systems and features available, but tighten settings, limit permissions, and remove unnecessary capabilities. This reduces exposure without disrupting everyday work.
Core principles of attack surface reduction
ASR is built on a few core principles that focus on limiting what attackers can see, access, and exploit.
Minimization of exposure
Reducing exposure starts with understanding what systems, services, and features are actually in use. Every active component expands the attack surface and must be intentionally managed, monitored, and secured. Components that no longer serve a clear purpose should be disabled or removed entirely, rather than left running by default.
Minimization also means keeping required systems tightly configured so they expose only what’s necessary to function. This includes disabling unused services that start automatically, closing unnecessary ports, and removing default administrative privileges from everyday user accounts. By limiting what remains active and ensuring that what does remain is properly configured, organizations can significantly reduce exposure without disrupting normal operations.
Principle of least privilege
The principle of least privilege is about keeping access sensible and intentional. People and systems should have enough access to do what they need to do, but not more than that. From an ASR perspective, every unnecessary permission increases what an attacker could reach if an account is compromised.
In day-to-day work, having full control over systems is rarely necessary. When elevated access is limited, the potential impact of mistakes or compromised accounts is reduced, which directly shrinks the effective attack surface.
Clear boundaries also make problems easier to contain. If an account is exposed, limited permissions help keep that access from reaching systems or data it was never meant to touch, preventing a single entry point from turning into a wider security issue.
Importance of asset visibility and inventory
It’s hard to protect systems you’re not aware of. Asset visibility is about knowing what hardware, software, and devices are actually connected and in use at any given time. From an ASR perspective, you can’t reduce exposure if you don’t know what exists and how it’s connected.
This includes tools that may not have been formally approved. Personal devices, browser-based apps, or cloud tools can quietly become part of everyday work without being tracked, increasing the attack surface without anyone realizing it.
Keeping an up-to-date inventory helps teams notice changes that don’t belong. When new devices appear or existing ones behave differently, those signals are easier to spot when there’s a clear record of what should be there.
Continuous security validation
Systems don’t stay the same for long. Software gets updated, devices change hands, and access levels shift over time. Continuous security validation focuses on regularly checking that protections still exist when these changes happen, including after updates.
It also means keeping an eye on gradual changes. Settings can drift as systems are updated or adjusted, sometimes without anyone noticing. Regular validation helps catch those changes early before they quietly expand the attack surface or weaken security.
Many teams rely on automated monitoring and configuration tools to support this process, which we cover in more detail below.
Common techniques used in attack surface reduction
In practice, ASR relies on a combination of configuration hardening, access controls, and ongoing maintenance.
System and network hardening
Hardening means configuring systems and networks to expose only what they actually need. Many devices and applications are designed to work out of the box, which often means extra features and services are enabled by default.
One common hardening step is disabling older communication methods that are no longer required. While these legacy options may still function, they’re often harder to secure and easier to misuse. Removing outdated protocols or services that were kept for compatibility can reduce exposure without affecting how systems are used.
Hardening also involves removing software that doesn’t serve a clear purpose. Extra applications or background services can quietly increase complexity, even if they seem harmless. Fewer moving parts make systems easier to understand, manage, and secure.
At the network level, hardening often involves separating systems into smaller, controlled segments. This helps contain issues if something goes wrong, rather than allowing them to spread across the entire environment. Clear boundaries limit how far problems can travel.
Keeping systems updated and patched
Keeping operating systems and key applications updated helps close known weak spots before attackers can take advantage of them. To make this reliable, updates should be applied on a regular schedule.
Automating updates where possible helps ensure patches are applied consistently across devices, reducing the risk that critical fixes are missed. For systems that can’t be updated automatically, setting clear ownership and review intervals helps prevent outdated software from quietly expanding the attack surface.
Reducing external attack paths
Reducing external attack paths focuses on limiting which parts of an internal environment are reachable from the public internet. The fewer systems that are directly exposed, the smaller and more manageable the overall risk becomes.
One common approach is keeping internal tools and databases behind protective layers instead of assigning them public-facing addresses. When systems are accessible only from trusted networks, accidental exposure is less likely.
Remote access is another area where external exposure can grow quickly if it isn’t deliberately constrained. Using encrypted connections helps ensure data travels through protected channels rather than crossing open networks, keeping access more controlled and predictable.
It also helps to limit how much information about internal infrastructure is publicly visible. When internal systems aren’t directly exposed, it becomes harder for outsiders to map how everything is connected. Less external visibility means fewer opportunities for unwanted attention.
Tools that support attack surface reduction
As systems grow more complex, it becomes harder to keep track of what’s exposed and what’s not, which is why continuous attack surface management (ASM) has become essential for modern security teams. These tools help make it clearer what’s exposed, so teams aren’t relying on manual checks or guesswork.
ASM and EASM platforms
ASM and external ASM (EASM) tools are designed to continuously discover and monitor assets and services, helping teams understand what exists, how it’s configured, and where risk may be introduced over time.
ASM focuses on assets within the organization’s environment, while EASM looks at assets that are externally visible from the public internet.
Vulnerability and configuration scanners
These tools help spot problems that are easy to miss in day-to-day operations.
- Vulnerability scanners look at the software you use and check whether it has known security issues that still need fixing.
- Configuration scanners focus on how systems are set up, flagging risky configurations, exposed services, and insecure default settings.
Together, both help teams catch small oversights early, before they quietly turn into real security risks.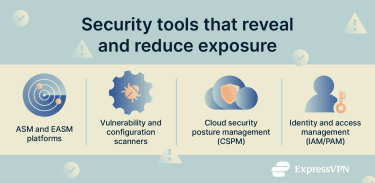
Cloud security posture management (CSPM)
Cloud security posture management (CSPM) tools help by keeping an ongoing check on cloud environments, watching for risky configurations and highlighting when something drifts away from expected security standards. This makes it easier to keep cloud environments consistent, well-configured, and less exposed as they evolve.
Identity and access management (IAM/PAM) tools
Identity and access management (IAM) and privileged access management (PAM) tools help keep access intentional and limited, without getting in the way of everyday work.
- IAM: Handles regular user access. These tools help ensure people can sign in securely and only reach the systems and information they actually need to do their jobs.
- PAM: Focuses on high-level accounts with the ability to make major changes. PAM tools limit when this powerful access is available and keep clear records of its use, which helps prevent mistakes and makes investigations easier if something goes wrong.
How to build an effective attack surface reduction strategy
An effective ASR strategy means understanding what’s in your environment, removing what’s unnecessary, and hardening, monitoring, and maintaining what needs to remain in use, while staying alert as things change.
Identify and classify assets
The first step is to identify all hardware, software, and cloud services connected to the environment. This includes systems that support core operations as well as tools used less frequently.
Once assets are identified, they should be classified based on their function and the type of data they handle. Systems that process sensitive or business-critical information require stricter controls than assets with limited impact. Clear classification helps apply security measures where they’re actually needed.
Assess risks and vulnerabilities
After assets are identified and classified, the next step is to assess where real weaknesses exist. Teams check systems for known software vulnerabilities and configuration issues that could be exploited.
Prioritize remediation actions
Prioritize problems that combine high risk and high impact, such as systems exposed to the internet or critical services missing security updates. Issues with limited reach or lower immediate impact still matter, but they can be addressed after higher-risk items are under control. That way, teams reduce real risk quickly while ensuring lower-priority issues are tracked and resolved over time, rather than ignored.
Implement ASR controls
Next, reduce exposure by applying practical controls across systems and devices, such as:
- Hardening systems: Turning off features, services, or tools that aren’t needed for day-to-day work.
- Restricting access: Making sure users and applications can only see and use what they genuinely need.
- Closing unused ports: Shutting down network ports or connections that no longer serve a clear purpose.
- Blocking risky behavior on endpoints: Using endpoint protection tools that enforce ASR rules to prevent common malicious actions before they spread or escalate.
- Monitor changes to the attack surface: This helps teams spot new exposure early and address it before it turns into a real security issue, focusing on visibility and change detection rather than blocking activity by default.
How network security and virtual private networks (VPNs) help reduce the attack surface
Network access controls reduce the attack surface by limiting which internal systems are reachable from the public internet.
Rather than exposing internal systems directly to the internet, many organizations use private access mechanisms to control how connections are made. Enterprise VPNs (not to be confused with consumer VPNs such as ExpressVPN, which have their own, distinct set of use cases) are one established way to provide this kind of restricted access, allowing users and systems to connect to internal networks without assigning public-facing addresses to internal servers, applications, or databases.
From an attack surface perspective, the benefit is architectural: access is funneled through a limited set of managed gateways where identity checks, access policies, and logging can be consistently enforced, instead of securing each internal system individually.
Zero-trust network access (ZTNA) builds on this approach by further limiting what authenticated users can see and reach. Instead of granting broad network-level access, ZTNA restricts connectivity to specific applications or services based on identity, device posture, and contextual signals. Systems that are not explicitly permitted remain invisible and unreachable, even after authentication.
This application-level access model helps contain security incidents. If an account or device is compromised, limited visibility and narrowly scoped access reduce the risk of lateral movement and prevent a single entry point from exposing the wider environment. From an ASR standpoint, this minimizes both external exposure and internal spread.
FAQ: Common questions about attack surface reduction
What does attack surface mean in cybersecurity?
In cybersecurity, the attack surface is everything in a system that an attacker could potentially reach, such as exposed services, devices, or access points. The larger the attack surface, the easier it is to find weaknesses, which is why attack surface reduction (ASR) is a key part of keeping systems secure.
How does attack surface reduction work?
Attack surface reduction (ASR) works by finding what parts of a system are exposed and removing anything that is not necessary. This includes disabling unused services, closing unnecessary ports, and limiting access so attackers have fewer ways to reach the system through reducing external attack paths.
What methods reduce an attack surface?
An attack surface is reduced by removing anything that doesn’t need to be exposed. This includes turning off unused services, closing unnecessary ports, limiting access permissions, and keeping systems up to date. The goal is to keep only what is essential accessible, following the principle of minimization of exposure.
What tools support ASR initiatives?
Attack surface reduction (ASR) initiatives are supported by tools that help identify, monitor, and control exposed systems. These include asset discovery tools, vulnerability scanners, access management tools, and cloud security posture management platforms, all of which help maintain continuous security validation.
How does ASR relate to zero-trust security?
Attack surface reduction (ASR) supports zero-trust security by minimizing what systems and users can access by default. While zero trust focuses on never automatically trusting access, ASR reduces risk upfront by limiting exposure and enforcing access only where it is truly needed, following the principle of least privilege.
Can a VPN help reduce the attack surface?
Yes, an enterprise VPN can help reduce the attack surface by limiting how internal systems are exposed to the internet. Instead of making services directly reachable, a VPN creates a protected access path that only authorized users can use, which supports reducing external attack paths and makes it harder for attackers to discover or reach internal resources.
What are common vulnerabilities found in an attack surface?
Common attack surface vulnerabilities include outdated software, misconfigured services, open ports that are not needed, weak or overly broad access permissions, and exposed remote access points. These issues increase risk by creating unnecessary entry points, which is why addressing them is a core part of reducing unnecessary exposure.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN