What is wire fraud, and how can you avoid it?
Wire fraud is a type of scam where the fraudster uses electronic communication to trick the victim into sending money or sensitive information.
You may not think you’re at risk for wire fraud. After all, an email from a “foreign prince” promising a fortune in exchange for a small upfront fee is easy to laugh off and ignore. But modern wire fraud is often far more sophisticated.
For example, a scammer might pose as a family member in urgent need of money. Or, they might send messages that appear to come from your bank or other trusted institutions, asking you to confirm a payment or transfer funds. These schemes are designed to blend into everyday digital interactions, making them much harder to spot.
In this article, we explain what wire fraud is, how it works, and provide practical tips on how to protect yourself.
What is wire fraud?
“Wire fraud” is the term for a specific U.S. federal offense. It occurs when a criminal uses electronic communications, such as email, text messages, phone calls, or online platforms, to deceive someone. The goal is to obtain money or sensitive information, such as bank account details, login credentials, Social Security numbers, or credit card information.
In other countries, similar offenses exist but are prosecuted under different laws and called by different names. For example, in the U.K., it could generally fall under “fraud by false representation” or other offenses defined in the Fraud Act 2006. In Canada, comparable crimes are usually prosecuted as “fraud” or “computer fraud” under the Criminal Code.
How wire fraud works in modern cybercrime
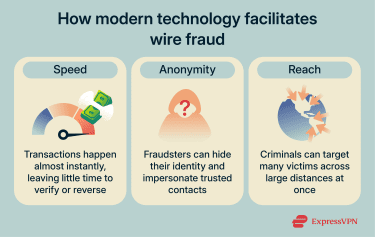
Wire fraud has been around for as long as electronic communications. However, the way it occurs has changed dramatically with the evolution of technology, such as online banking platforms, payment apps, and messaging systems.
These technologies make it easy for users to manage payments and communicate but also create opportunities for criminals. Major ways that digital systems facilitate wire fraud include:
- Speed: Financial transactions can be completed almost instantly, reducing the window for verification or correction.
- Anonymity: It’s easier to mask a message sender’s identity, allowing fraudsters to pose as trusted contacts or institutions. This also makes it harder for authorities to trace perpetrators.
- Reach: Fraudsters can target many victims at once and across large geographic areas, increasing the chances that some will fall for the scam.
How wire fraud happens
Wire fraud often targets the human component of digital transactions. Instead of exploiting technical vulnerabilities, scammers use social engineering to deceive victims and influence them into taking harmful actions.
Common tactics used in wire fraud schemes include:
- Phishing: Emails or links are designed to look like they come from trusted contacts or institutions, like a major bank or payment service provider.
- Creating a sense of urgency: Fraudsters claim that immediate action is required to pressure the victim into acting without thinking. For example, the message may claim that the victim’s account will be locked unless they respond right away.
- Invoking fear: Scammers may threaten consequences like legal trouble or missed payments. This makes the victim more likely to transfer money or provide sensitive details to avoid the perceived risk.
- Appealing to greed: Messages promise refunds, prizes, investment returns, or exclusive offers. Victims are asked to share payment information or send money to secure the benefit.
- Appealing to sympathy: Scammers claim to be in distress to prey on the victim’s goodwill. For example, they may pretend to be in urgent need of funds for a medical operation.
- Impersonating a trusted contact: Scammers sometimes pose as someone the victim knows or trusts and request an urgent wire transfer or sensitive information. These messages often reference familiar details to appear legitimate (for example, “I’m stuck abroad and need help right now” or “I need this payment sent before the end of the day”).
How wire fraud differs from other financial scams
A financial scam can't be considered wire fraud if it doesn't use electronic communications. For example, mail fraud, which relies on the postal system, doesn't count.
Wire fraud shouldn’t be confused with wire transfer scams, either. Unlike wire fraud, “wire transfer scam” isn’t a formal legal term. Additionally, it refers specifically to schemes that trick victims into sending money via wire transfer. Wire fraud covers a broader range of schemes. In other words, all wire transfer scams are wire fraud, but not all wire fraud is a wire transfer scam.
What legally qualifies as wire fraud?
According to the U.S. Department of Justice's Criminal Resource Manual (18 U.S.C. 1343), a crime is defined as wire fraud if it includes:
- A scheme to defraud: There’s a plan to deceive someone for money or property.
- Intent to defraud: The perpetrator must knowingly act to mislead or cheat the victim.
- Use of wire communications: The act includes the use of any interstate or foreign electronic transmission.
If a financial scam meets all of the other requirements but occurs entirely within one state, it doesn’t officially count as wire fraud by this definition. Those cases are prosecuted under the appropriate state law instead.
Note that someone can also be charged with wire fraud even if the scheme doesn’t succeed.
Most common types of wire fraud
In the sections below, we break down common schemes that involve wire fraud.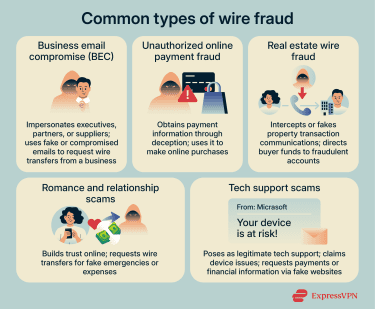
Business email compromise (BEC)
This type of scam targets companies and organizations by exploiting email systems. In a typical BEC scam, fraudsters impersonate executives, partners, or suppliers and request a wire transfer to a fraudulent account. These attacks often use spoofed or compromised email addresses to make the request appear legitimate.
Unauthorized online payment fraud
Online payment fraud is a type of scam that involves using stolen payment information to obtain money or goods. Most commonly, it refers to stealing someone’s payment details to make online purchases in their name. It can qualify as wire fraud if the scam uses electronic communications to trick the victim into giving away their payment information.
Real estate wire fraud
This type of scam occurs when fraudsters fake or intercept communications during property transactions. For example, a buyer may receive fraudulent wiring instructions from a scammer posing as a real estate agent and end up sending money to the wrong person.
Romance and relationship scams
Romance scams involve a fraudster building a relationship with a victim online. Once the scammer has gained trust, they may request money for fabricated emergencies, travel costs, or other urgent needs.
Tech support scams
In tech support scams, fraudsters pretend to be a legitimate technical support team from a well‑known company. They claim there’s a problem with the victim’s device when there isn’t one. Afterward, they might request payment to fix the “issue.” They might also direct the victim to a website designed to steal financial information or request remote access to the victim’s device, using the opportunity to install credential-stealing malware.
How to protect yourself from wire fraud
Here are some strategies to protect yourself or your business from money transfer fraud risks.
Recognizing social engineering behind wire fraud
The Phishing Trends 2025 report by Hoxhunt (a cybersecurity company specializing in phishing prevention and training) revealed that only a small percentage (0.7% to 4.7%) of surveyed phishing emails were written by AI. However, the same report predicts that this number could grow as these tools become more widespread. This development creates new challenges for financial scam detection.
AI technology allows fraudsters to personalize messages more effectively. For example, scammers may use AI to pull details about the target from public sources (e.g., social media) to craft messages that feel timely and relevant. AI may also be able to imitate a trusted contact’s writing style, voice, branding, logos, and more.
Despite these advances, there are still signs you can watch for to recognize social engineering attempts, such as:
- Unsolicited or unexpected messages: Communications from strangers or from contacts/companies you weren’t expecting to hear from.
- High-pressure tactics: Messages that push for immediate action or threaten consequences if you delay.
- Unrealistic promises or deals: Offers that are too good to be true, such as unexpected prizes, refunds, or investment opportunities.
- Mismatched URLs or sender addresses: Phishing emails that come from addresses that look almost like legitimate contacts but have small changes. For example, “support@bankofarnerica.com” instead of “support@bankofamerica.com” (the first link uses “rn” instead of “m”). Similarly, links may appear correct at a glance but actually direct you to a fake site, such as www.paypal-secure.com instead of www.paypal.com.
- Unusual tone or content: Messages may be out of character for the sender. For example, a friend emailing you about a “business opportunity” they’ve never mentioned, or a bank email requesting account details (which legitimate banks never do via email). You should also look for signs of AI-generated text. AI messages are often overly formal, repetitive, or generic.
Best practices for individuals
It’s important to build smart digital habits and perform careful verification before sending money or sharing financial information online. Key practices include:
- Pause before acting on time-sensitive requests: Avoid rushing into payments even if messages claim emergencies or deadlines. Scammers often create pressure to bypass your usual caution.
- Verify unexpected payment instructions: Confirm requests using trusted channels. For example, call the company or contact the relevant person directly.
- Use official platforms: Make transfers through known banking apps or websites rather than clicking links in emails or text messages.
- Be cautious with sensitive information: Avoid sending login credentials, passwords, or account details in response to emails, texts, or social media messages.
- Educate yourself on scammer tactics: Learn how to recognize phishing red flags.
- Enable two-factor authentication (2FA): 2FA adds an extra layer of security by requiring two forms of verification before granting access. This makes it harder for scammers to access your accounts even if they obtain your password.
- Use a virtual private network (VPN): VPNs, like ExpressVPN, encrypt all internet traffic from your device to the VPN server. This secures your online activity on risky networks, like public hotspots.
- Check if your connection is secure: Before making payments or entering sensitive information, look for a small padlock icon in your browser bar. This will tell you if the website uses HTTPS encryption to protect the traffic between your device and the site.
- Use encrypted messaging apps: Some messaging apps encrypt texts, calls, and other communications. This prevents third parties from seeing sensitive information you share with friends, colleagues, or service providers.
Best practices for organizations
Protecting your business from wire fraud requires a combination of employee awareness, secure communication, and careful verification of financial transactions. Key practices include:
- Employee training: Educate staff on phishing, BEC, and social engineering red flags.
- Verify payment requests: Require dual approval for large or unusual wire transfers; confirm requests using a separate communication channel.
- Secure email systems: Mandate strong passwords, 2FA, and email security tools to prevent account compromise.
- Limit access: Restrict who can initiate or approve payments, and regularly review permissions.
- Monitor transactions: Track outgoing payments for unusual patterns or high-risk destinations.
- Implement email authentication: Set up protocols that let other servers verify whether emails really come from your domain.
- Enforce strict domain policies: This makes it harder for attackers to impersonate your organization.
What to do if you’re a victim of wire fraud
If you believe you’ve been defrauded, here are a few steps you can take to protect your accounts and report the incident:
- Contact your bank or payment provider immediately: It’s a good idea to report the fraudulent transaction and ask whether it can be stopped or reversed.
- Secure your accounts and credentials: Change passwords, enable 2FA, and review recent account activity for other unauthorized transactions.
- Gather and preserve evidence: Save transaction records, payment confirmations, emails, messages, invoices, and any instructions or communications related to the fraud. Clear documentation can help investigations and recovery efforts.
- Report the fraud to the appropriate authority: In the U.S., you can file a report with the Federal Trade Commission (FTC) and the Internet Crime Complaint Center (IC3).
- Monitor your accounts and credit: Continue reviewing financial statements and credit reports for signs of further misuse, especially if sensitive information was exposed.
How VPNs help reduce wire fraud risks
Some wire fraud schemes involve exploiting technical vulnerabilities. Here’s what a VPN can do to reduce these risks.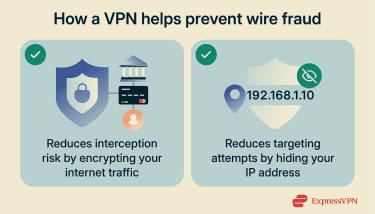
Limit the risks of man-in-the-middle (MITM) and evil twin attacks
A man-in-the-middle (MITM) attack occurs when a cybercriminal secretly intercepts or alters communications between two parties. It can be used to deceive victims as part of a wire fraud scheme.
For example, the attacker might intercept the victim’s internet connection to a website and redirect the victim to a fake site instead. They can then view and steal information the victim enters into that site, like login credentials.
MITM attacks can be a risk on public Wi-Fi because these networks are often unsecured and shared by many users. That makes it easier for a potential attacker to hijack your connection.
They might also set up a fake network (an “evil twin”) with a name that looks similar to a normal free hotspot to trick you into connecting. When you connect to this fake network, the attacker can monitor your online activity and steal inputted information like payment details.
A VPN can help in both scenarios by encrypting your internet traffic before it leaves your device. That means, even if an attacker successfully intercepts your connection, they can’t see what you’re doing online and steal sensitive info. They’ll only see scrambled, encrypted data.
Mask your IP address
An IP address can reveal general information about a user, such as their approximate location, internet service provider, or where they’re connecting from. Fraudsters can use this information to profile potential victims, tailor scams, or identify users who may be easier to target.
A VPN can hide your real IP address, which limits the amount of identifying information exposed during online activity.
Block malicious sites
A VPN can't stop you from voluntarily sending money to a scammer or entering your credentials on a shady website, so it's not a replacement for careful behavior. That said, some VPNs include features that block malicious sites. For example, ExpressVPN’s Threat Manager prevents connections to known phishing domains.
FAQ: Common questions about wire fraud
What is an example of wire fraud?
One example of wire fraud is a scammer impersonating a trusted person or organization to trick someone into sending money. For instance, the scammer might pretend to be a friend or family member in urgent need of money or pose as a tech support agent asking for payment to resolve a fake device issue.
Can I recover money lost to wire fraud?
It may be possible to recover money, but success depends on how quickly you act and the payment method used. Bank transfers or credit card payments are sometimes reversible if reported immediately. Funds sent via cryptocurrency or gift cards are much harder to recover.
What should I do if I wire money to a scammer?
If you wire money to a scammer, it’s best to contact your bank or payment provider immediately. Afterward, secure your accounts and credentials and gather evidence to assist with investigations and recovery efforts. Finally, you can file a report with the appropriate government agencies and monitor your accounts and credit for signs of further misuse.
What are the main types of wire fraud?
The main types of wire fraud include business email compromise (BEC), unauthorized online payment fraud, real estate wire fraud, romance scams, and tech support scams.
How can I spot fraudulent transfer requests?
Scammers often try to manipulate your emotions. Common tactics include creating urgency, invoking fear, appealing to sympathy, or promising rewards. You may also be able to spot fraudulent transfer requests by double-checking the sender’s address or URL for misspellings, slight variations, or domains that don’t match the legitimate organization.
Does a VPN help reduce the risk of wire fraud?
Yes, a VPN can help reduce the risk of wire fraud. Encrypting your internet traffic makes it harder for cybercriminals to intercept your connection and steal information, such as login credentials. It also masks your IP address, limiting the amount of personal information exposed online, which makes it harder for fraudsters to target or tailor scams to you.
However, a VPN won’t protect you from deceptive messages or requests that try to trick you into sending money. It’s important to remain vigilant and verify any suspicious emails, messages, or payment requests.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN