What is open source intelligence (OSINT) and why does it matter?
Over 6 billion people worldwide use the internet, leaving a significant trail of data behind. These digital footprints could include social media posts, forum activity, job profiles, public reviews, and company websites.
Open source intelligence (OSINT) involves collecting and analyzing publicly accessible information. Professionals use it in cybersecurity, investigations, and research. However, bad actors can misuse it to profile you or organizations and tailor targeted attacks.
In this guide, we’ll explain what OSINT is, where it’s used, the privacy risks it creates, and how to reduce your exposure.
What is OSINT?
OSINT is information collected from publicly available sources, including websites, public records, news articles, and social media platforms. The key point is that the information is legally accessible; it doesn’t involve unauthorized access to private systems.
This is also what separates OSINT from traditional intelligence gathering. Instead of relying on classified sources or covert methods, OSINT focuses on analyzing open information. The value comes from how analysts interpret the overwhelming volume of information.
Today, OSINT is widely used across many fields, but its roots lie in government intelligence work. During World War II, analysts used newspapers, radio broadcasts, and other publicly available sources to supplement classified intelligence and provide a broader strategic context. Over time, those same principles became useful well beyond intelligence agencies, especially as the amount of public information online grew.
However, public information isn’t always easy to find, even with internet access. It’s often spread across different platforms, and a single post, profile, or record might not seem significant on its own. But when someone systematically combines and verifies multiple publicly available sources of information about a specific person or entity, they can build a detailed profile.
OSINT is common because so much now happens online. People and organizations regularly share information through work, communication, or self-promotion. Over time, this creates a large pool of public data that anyone can review and analyze.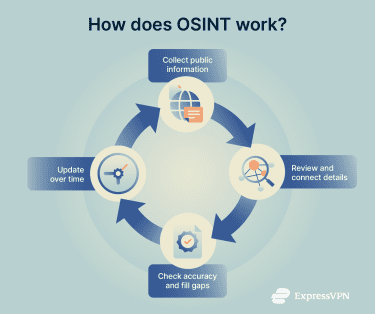
Where OSINT is used today
OSINT has applications across many industries, from cybersecurity to journalism. Here are some examples.
OSINT in cybersecurity and threat intelligence
In cybersecurity, OSINT often supports threat awareness, assessment, and breach detection. Industry estimates often suggest that a large majority of threat intelligence comes from open-source data. It can surface early signs of risk, such as emerging attack trends, malicious infrastructure, or vulnerabilities openly discussed. This helps security teams spot potential threats that don’t appear in internal logs or alerts.
During investigations, OSINT can add context. Public indicators can help link related activity, clarify how attackers operate, or support incident response. Many teams use OSINT alongside internal security data, relying on open information to inform analysis.
OSINT in law enforcement and public safety
Law enforcement and public safety teams often turn to OSINT to support and corroborate other evidence. They may use it to verify identities, confirm timelines, or understand how people or events are connected. Its use, however, is governed by legal and ethical guidelines around privacy, accuracy, and proportionality.
OSINT also helps link online activity to real-world incidents. Public posts, images, or discussions may help clarify what happened or point to developing situations. Over time, this information can highlight broader public safety concerns that warrant closer attention.
OSINT in business and risk analysis
For businesses, OSINT can flag brand impersonation, leaked data, or misleading claims before they escalate.
It’s also widely used to support formal due diligence. Public records and online activity can support background checks during hiring, investor research, or mergers and acquisitions.
The same information can reveal potential risks tied to vendors, partners, or changing market conditions. Together, these insights can inform fraud prevention, reputation management, or strategic decisions.
OSINT in academic and investigative research
Researchers and journalists use OSINT primarily to verify claims, especially when information is disputed or incomplete.
They may also use OSINT to cross-check timelines, locations, or digital content. Comparing information across multiple sources helps confirm accuracy and identify inconsistencies. In fields where transparency matters, this approach typically produces findings that anyone can review and trace to their origins.
Common sources of OSINT
OSINT draws on many different types of publicly accessible information, each offering a different perspective.
Public websites and open data platforms
Much of OSINT comes from information that people and organizations intentionally publish. Company websites, blogs, and online profiles often include details about people, roles, services, or business activity.
Open data portals, people search sites, news sites, and archived reports are also common sources. These may include datasets, public reports, or older articles that remain accessible long after publication. Even when information is no longer actively maintained, it can still be relevant.
Social media and online communities
Public posts, comments, and profiles on social media can reveal interests, connections, or opinions that don’t appear in official records.
Forums, discussion boards, and niche communities can provide even more detail. These spaces tend to include longer conversations or firsthand accounts that add context around events or behavior.
Even when people use pseudonyms instead of their legal names, patterns across public posts can make it easier to link accounts back to real people. For example, the topics they discuss, the locations they mention, or the links they share may allow someone to identify them.
Public records and government databases
Public records and government databases include business registrations, court filings, licenses, property records, and regulatory disclosures.
Availability and detail vary widely by country and jurisdiction. Some records are easy to access, while others are limited or incomplete. Although these sources are official, analysts still need to verify them against other information, especially if they’re outdated or lack context.
Technical and metadata sources
Not all OSINT appears as written content. Some comes from technical details like IP addresses, domain records, or Domain Name System (DNS) information. This information can reveal practical details, such as whether two websites are hosted on the same server or whether a domain has been transferred to a new owner.
Metadata is another example. Images, documents, or videos may contain embedded details like timestamps or location data.
Deep web and dark web sources
Some publicly accessible information isn’t indexed by search engines. This is often referred to as the deep web and includes content such as archived pages, databases, or sites that require direct URLs.
The dark web can also be a source of OSINT. While some material is publicly reachable using specialized tools, access and use are subject to legal and ethical constraints, and analysts typically limit activity to passive observation. Threat intelligence or fraud investigation teams often review these sources for additional context.
OSINT tools and data collection methods
OSINT can be gathered and analyzed in different ways, depending on the goal and context.
Passive vs. active OSINT collection
| Passive OSINT | Active OSINT |
| No deliberate engagement with the source beyond viewing publicly available content | Some interaction with systems or platforms |
| Reading or observing publicly available content | Engaging with content or making public queries |
| Low visibility | More noticeable |
Passive OSINT refers to observing information without engaging with the source. For example, reviewing public websites, social media platforms, or publicly available reports. Because there’s no direct interaction, this approach is less noticeable. On many platforms, someone could view a public profile without triggering any visible activity to the account owner.
Active OSINT involves some interaction with the source, which is why active collection leaves traces you might notice.
Examples of active OSINT include:
- Submitting public queries: Interacting with websites or servers to find details that aren’t visible through observation alone, such as how a service is set up or where it’s hosted.
- Requesting public records: Making formal requests, such as Freedom of Information Act (FOIA) requests, to access records that aren’t published by default but are still legally available.
- Engaging on public platforms: Interacting with public profiles or content, such as sending a connection request or message, to check activity or gather context.
Usually, people use active OSINT when passive methods don’t provide enough information, for example, when they need confirmation or access to records that require a request. However, because these actions can leave traces, they’re typically used with more caution.
While not a formally standardized term, semi-passive OSINT is sometimes used in cybersecurity to describe low-interaction collection methods, such as querying third-party services (for example, WHOIS databases, certificate transparency logs, or passive DNS providers). These techniques avoid direct engagement with the target and do not involve intrusive scanning or brute-force queries.
Open-source vs. commercial OSINT tools
Open-source OSINT tools are often community-developed and widely used across both small and large investigations. They’re often valued for transparency, flexibility, and customization.
Commercial OSINT tools are built for larger-scale use. These paid platforms collect and organize public data in one place, making it easier to review large volumes of information quickly. The underlying data is largely derived from public or lawfully accessible sources, but commercial tools aggregate more sources and process them faster.
Manual vs. automated OSINT collection
Manual OSINT collection relies on human effort. Analysts search for information, review sources, and verify details by hand. While it takes more time, it works better where context and judgment matter, especially with nuanced or easily misinterpreted information.
Automated OSINT collection uses scripts or platforms to quickly gather large volumes of public data. This approach is faster and more scalable, but can produce noise or incomplete results without careful review. Automated OSINT collection methods may include web crawlers, data scraping, and application programming interfaces (APIs).
Most OSINT work combines both: automation handles volume, manual review adds context and accuracy.
Common myths about OSINT investigations
Because OSINT relies on publicly available information, people often misunderstand its scope and limitations. Common myths include:
- “OSINT is just Googling”: People look up information about others for personal reasons, like researching a company, checking out a date, or reconnecting with an old classmate. On its own, casual searching isn’t typically considered OSINT. OSINT focuses on systematic collection, correlation, analysis, and interpretation.
- “If it’s public, it’s legal to use however you want”: Public access doesn’t mean unrestricted use. How OSINT information can be collected or applied depends on local laws and the purpose for which it is used. Even when data is public, legal and ethical responsibilities still apply.
- “OSINT always produces accurate information”: Public information isn’t always reliable. Open sources can be outdated, incomplete, or misleading, especially when taken out of context. That’s why OSINT relies on checking information across multiple sources instead of treating any single detail as definitive.
How OSINT can be misused
OSINT itself isn’t malicious, but someone can combine and exploit public information in harmful ways.
Doxxing and online harassment
Doxxing is a well-documented example of how OSINT techniques can be misused. It involves revealing the identity behind an online account and exposing personal details like legal name, workplace, or location to enable harassment.
Public profiles, old social media posts, domain records, or data broker listings can all make this possible. None of this requires hacking, but once the information is shared, it spreads quickly and becomes difficult to control.
Stalking
OSINT techniques can also help track someone’s activity over time. Public posts reveal where someone spends time, who they interact with, and what their routines look like.
The risk increases when this information appears across multiple platforms. Details that seem minor on their own build a clearer picture when combined, which can lead to intrusive or unsafe outcomes.
Corporate espionage
Organizations can also be targets of OSINT misuse. Public filings, job listings, press releases, and employee activity reveal details about a company's structure, partnerships, and ongoing projects.
In corporate espionage cases, bad actors sometimes use OSINT to map relationships or identify areas of interest. While rarely the only method involved, public information often provides a starting point for deeper investigation.
Building profiles for scams, fraud, and blackmail
Attackers may use OSINT to enable phishing attacks. They can build detailed profiles of individuals or organizations, then target them with personalized messages that feel familiar and trustworthy.
Beyond phishing, the same profiles can be used for other forms of fraud or coercion. Publicly available details may be leveraged to impersonate colleagues or vendors, request urgent payments, or pressure someone into sharing additional information.
How to reduce your exposure to OSINT data collection
The less public data you leave online, the harder it is for someone to build a profile of you. Here are ways to reduce your OSINT footprint.
Manage your public data
You can’t remove all public data from the internet, but small changes can make it harder to collect.
- Audit what’s public: Search online for your name, usernames, email addresses, and phone numbers. Check image search results too. This often surfaces old profiles or social media posts that reveal locations, routines, or personal information that shouldn’t be public. Learn more in our guide on how to deep search yourself.
- Remove unnecessary information: Close accounts you no longer use. On active accounts, consider removing personal details such as phone numbers, birthdays, workplaces, locations, and friend lists.
- Tighten privacy settings: Set posts and profile details to “Friends only” or “Only me” where possible. Check default settings, as many platforms default to “Public.” Some platforms also let you limit search engine indexing.
- Opt out of data brokers: These companies collect personal information from public records and other sources to create profiles, which are often sold to companies for marketing, verification, and other purposes. Most have opt-out pages, but manually removing yourself from each platform can be time-consuming, and some sites re-add your information over time. Data removal services can handle the process for you, including resubmitting opt-out requests if your information resurfaces.
Read more: Learn how to manage your digital footprint with OPSEC best practices.
Use a VPN to limit OSINT-related exposure
A virtual private network (VPN) can help limit how much of your activity is visible at the network level, which can reduce certain forms of OSINT-related exposure.
One way it helps is by hiding your IP address. Your IP can reveal general location and network details to the websites and services you visit. When you use a VPN, those sites see the VPN server's IP address instead of your own, making it harder to link browsing activity back to you or your home network.
A VPN also encrypts your internet traffic. This is particularly useful on public or shared Wi-Fi networks, where others on the same network could otherwise potentially monitor traffic or infer which sites you’re visiting. Encryption prevents this kind of passive observation, even though the traffic itself remains visible.
Some VPN providers offer additional tools that go beyond network privacy. For example, ExpressVPN’s Identity Defender includes a data removal feature (available to users in the U.S. on select plans) that automatically scans where your personal information is listed and helps submit opt-out requests to data broker sites.
A VPN doesn’t remove public posts, records, or profiles you've already shared. It mainly affects how your network activity appears going forward. Managing what information you make public, alongside tools like data broker removal, remains an essential part of reducing your overall OSINT footprint.
OSINT best practices
If you're using OSINT for research or investigation, these principles can help you do it responsibly.
- Stay within legal boundaries: OSINT should rely on information that’s legally accessible and collected in compliance with applicable laws, platform terms, and professional standards.
- Respect privacy and avoid harm: Public information can still be sensitive. Ethical OSINT avoids exposing personal details that could put people at risk.
- Be clear about purpose and scope: There should be a clear, legitimate reason for collecting information, such as research or risk analysis. Set clear boundaries to prevent collecting more data than necessary.
- Validate and cross-check information: Public sources aren’t always accurate or up to date. Check findings against multiple sources, especially when using the data to inform decisions.
- Maintain integrity and accountability: OSINT analysis should be fair, accurate, and well-documented. Be open about limitations so others understand what the findings do and don’t show.
FAQ: Common questions about OSINT
How is OSINT different from hacking?
Open source intelligence (OSINT) relies on publicly accessible information. It doesn’t involve breaking into systems, bypassing security controls, or entering private accounts without permission. Hacking, by contrast, generally refers to activities performed outside authorized or consensual testing scenarios.
Can OSINT be used for cybercrime or fraud?
Open source intelligence (OSINT) is a legitimate practice, but it can be misused. Public information is sometimes collected and combined to enable scams, fraud, or harassment. The risk typically comes from deceptive or harmful use of the information, rather than from its public availability.
What types of information are commonly collected through OSINT?
Open source intelligence (OSINT) can rely on a wide range of publicly accessible data, including personal or organizational details such as names, roles, affiliations, locations, and public statements, as well as activities such as posts and interactions on social media. It can also involve technical details, such as domain ownership or timestamps, as well as contextual information from news reports or open datasets.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN