Types of DNS servers: Everything you need to know
Every device connected to the internet, from servers to your smartphone, has a unique numerical IP address. Since these number strings are impractical for people to remember, the Domain Name System (DNS) was created.
The system operates through a global network of specialized servers, which translate the domain names you type in a browser into their corresponding IP addresses. This translation is what connects you to the correct website.
The DNS lookup process relies on several types of servers, each performing a specific role. This guide explains what DNS servers do and provides guidance on how to select the right DNS service provider.
What are DNS servers?
DNS servers play a key role in the DNS by translating human-readable hostnames into IP addresses that computers can understand. This process is called domain name resolution.
Main types of DNS servers
There are four types of DNS servers that are important to know about. Here’s a summary of each.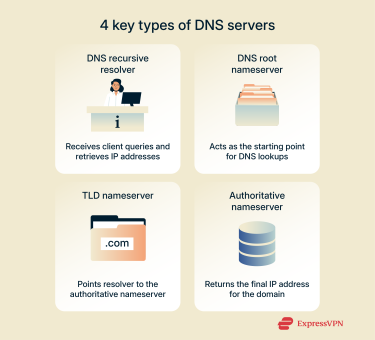
1. Recursive resolver
A recursive resolver is the DNS server responsible for handling the DNS lookup process on your behalf. When you try to visit a website, your device sends the DNS query to this resolver. First, the resolver checks its cache to see if it already knows the IP address for the domain. If the answer is cached, it returns it immediately. If not, it begins a lookup process to find the answer from authoritative sources.
2. Root nameserver (rarely queried)
If the resolver doesn’t already know where to find the relevant top-level domain (TLD) servers, it queries a root nameserver. The root nameserver doesn't provide the final IP address; instead, it responds with the address of the correct TLD nameserver for the domain.
In practice, though, recursive resolvers rarely need to contact root servers because they cache this information.
3. Top-level domain (TLD) nameserver
The TLD nameserver is responsible for domains under a specific TLD, like .com, .net, or .org. The resolver asks the TLD server where to find the authoritative nameserver for the domain in question (e.g., example.com).
4. Authoritative nameserver
The authoritative nameserver is the final stop: it’s the server that holds the DNS records for the domain, including its IP address. The resolver queries this server and receives the final answer: the IP address associated with the domain name. The resolver then returns this IP address to your device and caches the result for a period of time to speed up future lookups.
Why are DNS servers important?
 While the main job of a DNS server is translation, the system supports several key areas of your online activity, including:
While the main job of a DNS server is translation, the system supports several key areas of your online activity, including:
1. Speed and performance
DNS servers play a major role in how quickly websites load, mainly through a process called caching. When a recursive resolver retrieves an IP address for a domain, it stores that information in its cache for a set amount of time (known as the time to live, or TTL).
If another user asks for the same domain while the record is still in the cache, the resolver can provide the IP address immediately. This skips the full lookup process, which improves page load time.
2. Privacy
Your DNS queries create a detailed log of the websites, apps, and online services you use. By default, these queries are sent in plain text, making them visible to your internet service provider (ISP) and anyone else positioned to monitor network traffic, like a public Wi-Fi network operator. This information can be used for advertising, user profiling, or surveillance.
To solve this, technologies like DNS over HTTPS (DoH), DNS over TLS (DoT), and DNS over QUIC (DoQ) were created. They wrap your DNS queries in an encrypted layer, preventing third parties from seeing the domains you’re looking up.
While these protocols are a major step forward for privacy, they only encrypt the DNS lookup itself. Your ISP can no longer read the domain name in your query, but it can still see the IP address of the website or service you ultimately connect to.
For comprehensive privacy, it’s a great idea to use a VPN. It encrypts all of your internet traffic and routes it through a secure server, hiding both your DNS queries and your final IP destination from your ISP.
3. Security
Beyond privacy, a secure DNS service acts as a first line of defense against online threats. This protection is delivered through two key mechanisms: threat filtering and response validation.
Threat filtering blocks attempts to resolve domains known to host malware, phishing, or other malicious content. The DNS provider maintains a blocklist (or uses threat intelligence feeds), and when you attempt to access a blacklisted domain, the DNS resolver refuses to resolve or returns a “block” response.
Domain Name System Security Extensions (DNSSEC) provide response validation. It adds cryptographic digital signatures to DNS records so that a validating resolver can check whether the records have been tampered with or spoofed. This helps protect against DNS spoofing or cache poisoning, where a user might be redirected to a malicious site without knowing.
4. Email routing and authentication
DNS plays a key role in email delivery and security. When you send a message to name@example.com, your email server needs to find the correct mail server for the example.com domain. It does this by looking up the domain’s mail exchange (MX) records in the DNS.
MX records provide a prioritized list of mail servers for that domain. The sending server will always try the primary server first. If that server is unavailable, it will try the next one on the list, ensuring email continues to flow even if a server is down.
Beyond routing, DNS is a cornerstone of email authentication. It hosts text records that enable security frameworks, such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC), which receiving servers use to verify that a message is legitimate and not forged. This is a key defense against spam and phishing.
5. Redundancy and reliability
DNS plays a critical role in maintaining uptime by enabling automatic failover. Many DNS providers offer monitoring and health-check features that detect when a server or service becomes unreachable. If a server fails, the DNS can stop returning its IP address in responses and instead route traffic to a predefined backup. This ensures that services remain accessible, even during hardware failures or outages.
6. Load balancing
DNS can improve performance and scalability through traffic distribution. In DNS-based load balancing, multiple IP addresses are associated with a single domain name. When a user tries to access the site, the DNS responds with one of the available IPs, spreading traffic across multiple servers to prevent overload.
More advanced DNS setups can include geolocation-based routing, directing users to the server nearest to them to reduce latency and improve response times.
Choosing a DNS service
Not all DNS recursive resolvers are created equal. The one provided by your ISP is convenient, but it may not be the best choice. When picking a DNS service, consider these factors:
- Speed: Faster DNS lookups mean websites start loading sooner. A key factor is latency; that is, the physical distance your query must travel. Providers with a global anycast network minimize this delay by routing your request to the optimal server, ensuring the quickest possible response.
- Reliability: You want a DNS provider with 100% uptime. If your DNS server goes down, you won't be able to access any websites by their domain name. Reputable providers run huge, redundant networks to prevent outages.
- Privacy: Your DNS queries reveal every single website you visit. Some ISPs log this data and may use it for marketing or sell it to third parties. A privacy-focused DNS provider will have a strict no-logging policy.
- Security: As mentioned above, a good DNS provider can help to block access to malicious websites. Look for one that supports modern security protocols and DNSSEC validation.
Public DNS server examples
You can switch from your ISP's default DNS to a free public DNS provider. This change is typically made in the network settings of your device or within your router’s administration panel to cover all devices on your network.
Here are four popular choices:
- Cloudflare (1.1.1.1): Often cited as one of the fastest public DNS services available. Its primary focus is on privacy; it doesn’t log user IP addresses and deletes all query data within 25 hours. While this standard service doesn’t filter content, Cloudflare offers a separate address (1.1.1.2) that blocks malicious domains.
- Google Public DNS (8.8.8.8): A reliable and fast service from Google. Google states that it stores full IP addresses in temporary logs for 24–48 hours for security and diagnostic purposes. After this, it retains permanent, anonymized query metadata indefinitely, but this doesn’t contain personally identifiable information.
- Quad9 (9.9.9.9): This non-profit service focuses on security. It blocks access to malicious domains by checking them against multiple threat intelligence feeds, adding a layer of protection to your browsing. Quad9 doesn’t log user IP addresses or store any personally identifiable information from your queries.
- OpenDNS (208.67.222.222): One of the oldest public DNS providers, OpenDNS (now owned by Cisco) is well known for its customizable content filtering options. That said, to provide these features, the service logs user IP addresses and DNS queries.
DNS and security
DNS was designed in the 1980s, an era when the internet was a small, trusted community. This has left the DNS protocol vulnerable to attacks, so understanding these risks is the first step toward protecting yourself.
How DNS servers affect cybersecurity
DNS plays a critical role in your cybersecurity posture. Because it’s the first step in nearly every internet connection, a poorly secured DNS service creates a significant vulnerability. Attackers can exploit this weakness with methods like DNS hijacking to redirect you to fake sites and steal your information.
You can combat this by choosing a secure DNS provider that actively filters malicious domains and uses DNSSEC to verify a website’s authenticity.
Common DNS vulnerabilities (and how to prevent them)
When you know what attackers are looking for, you can better protect yourself. Here are five of the most common issues to watch out for.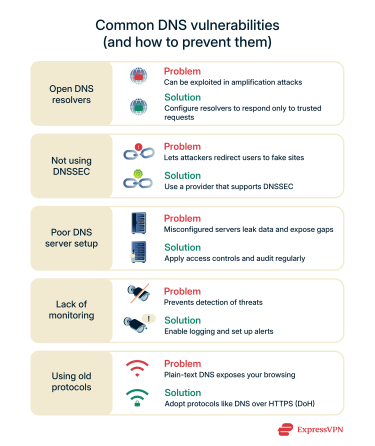
1. Open DNS resolvers
An open DNS resolver is a DNS server that responds to queries from any IP address on the internet, not just those within its network. While this might seem convenient, it poses a serious security risk.
Attackers can send a small query to your open resolver but make it look like the query came from their intended victim. Your server then sends a much larger response to the victim. When thousands of open resolvers are tricked into doing this at once, they flood the target with unwanted traffic, knocking it offline. This is called a DNS amplification attack, and your server is used as an unwilling participant.
What you can do: Configure your resolver to only answer requests from your network and trusted users. You can also consider implementing rate limiting and response-size controls to reduce the risk of your server being used in amplification attacks.
2. Not using DNSSEC
DNSSEC adds a cryptographic signature to DNS records. This allows resolvers to verify that the response they receive actually comes from the authoritative DNS server and hasn't been altered in transit.
Without DNSSEC, there’s no built-in way to ensure the authenticity of DNS responses. An attacker could exploit this by performing a DNS spoofing or cache poisoning attack, where they intercept your request (for example, to your bank’s website) and return a malicious IP address. This could lead you to a fake website designed to steal your credentials or personal information.
What you can do: Use a DNS resolver that validates DNSSEC, such as those offered by Google, Cloudflare, or Quad9 (9.9.9.9). If you own a domain, enable DNSSEC through your DNS hosting provider to help protect your visitors from spoofed responses.
3. Poor DNS server setup
A poorly configured DNS server can introduce significant security risks. For example, leaving DNS zone transfers (AXFR) open to the public can allow anyone to copy your entire DNS zone file, and weak access controls and passwords can make it easier for attackers to alter records or access administrative settings.
In some cases, misconfigurations could allow attackers to execute code on your server, potentially leading to a full-scale data breach or taking your website offline.
What you can do: If you operate a DNS server or manage a domain, you can disable zone transfers unless they’re absolutely necessary, and if you do use them, restrict them to specific IPs. Also, use strong access controls, regularly audit your DNS configuration, and monitor for unexpected queries or changes to zone data.
For general users, choose a reputable DNS provider or public resolver with a strong security reputation and avoid using unknown or obscure DNS servers.
4. Lack of monitoring
Without proper DNS monitoring, attackers can abuse your DNS infrastructure without being detected. They could potentially exfiltrate data from your network, communicate with malware or command-and-control (C2) servers, or probe your environment for weaknesses or misconfigurations. If DNS logs aren't collected and reviewed, these activities can go unnoticed.
What you can do: If you operate your own DNS server or manage enterprise infrastructure, you should enable detailed DNS logging using a centralized logging system or Security Information and Event Management (SIEM) platform to collect and correlate DNS activity.
If you're a general user or small business, use a DNS provider that offers threat detection or basic analytics, enable activity reports if available, and consider using security-focused DNS resolvers that block known malicious domains.
5. Using old protocols
The original DNS protocol sends all its queries in plain text. This is like sending a postcard through the mail; anyone who handles it along the way can read it.
What you can do: Use modern protocols that encrypt your DNS traffic. DoH and DoT wrap your queries in a secure layer, turning that postcard into a sealed envelope. Choose a DNS provider that supports these protocols to keep your browsing history private.
The role of DNS zones
The DNS zone is the part of the DNS namespace that a specific administrator manages. For a small business, the zone might just be the single domain, like mycompany.com. The zone contains all the DNS records for that domain.
These records are stored in a zone file on an authoritative nameserver. Conceptually, this is a plain text file that lists all the records, such as the A record (for the IP address), the MX record (for the mail server), and others. In modern systems, this data may be managed dynamically in a database rather than a static file.
Control over the zone file means control over the domain, so securing access to the zone file and the server that hosts it is a key part of DNS security.
Best practices for securing DNS
Whether you’re managing your home network or a business, you can take simple steps to make your DNS usage more secure.
- Use a secure DNS provider: Switch from your ISP’s default DNS to a reputable third-party provider that supports DoH, DoT, and DNSSEC.
- Use a VPN: A trustworthy VPN like ExpressVPN is one of the best ways to secure your DNS. It encrypts your internet connection and routes your DNS queries through its own private, no-log servers. This hides your browsing activity from your ISP and protects you on public Wi-Fi.
- Enable DNSSEC on your domain: If you own a domain name, make sure DNSSEC is enabled through your domain registrar and DNS hosting provider. This protects visitors to your site from receiving forged or tampered DNS records.
- Keep software updated: For businesses running their own DNS servers, it's vital to keep the server software patched and up-to-date to protect against known vulnerabilities.
Practical guidance for DNS configuration
Here are some best practices you can follow to get both redundancy and performance out of your DNS settings.
Recommended setup for redundancy and performance
For a reliable internet connection, always configure at least two DNS servers: a primary and a secondary. This provides critical redundancy. If your primary DNS server becomes slow or unreachable, your devices will automatically switch to the secondary server, preventing an interruption.
For the best combination of speed and reliability, we recommend using servers from two different, high-quality public DNS providers. This protects you not only from a single server failure but also from a provider experiencing a network-wide problem. For example, you could set your primary DNS server to Cloudflare (1.1.1.1) and your secondary to Quad9 (9.9.9.9). You can apply these settings in your router’s administration panel to cover all devices on your network or configure them on individual devices.
To find the fastest DNS servers for your specific location and connection, you can use free tools like the Gibson Research Corporation's DNS Benchmark, which tests dozens of public servers and ranks them based on real-world performance.
Common misconceptions about DNS servers
There is a lot of misinformation about what changing your DNS can and can’t do.
- “Changing my DNS will make my downloads faster.”
Changing your DNS only affects the speed of the initial lookup. It can make a website start to load faster, but it has no effect on your internet bandwidth. Your download and streaming speeds are determined by your plan with your ISP. - “My ISP’s DNS is the best and safest option.”
While it’s the easiest option because it’s pre-configured, your ISP’s DNS is rarely the fastest or the safest. Some ISPs also log your DNS queries for data collection purposes, making them a poor choice for privacy. - “All DNS servers are the same.”
DNS providers differ significantly in their speed, uptime, security features (like malware filtering), and privacy policies. Choosing a provider that aligns with your needs is worth the few minutes it takes to change settings.
FAQ: Common questions about DNS servers
Who owns 9.9.9.9 DNS?
Quad9, a Swiss-based non-profit organization, operates the 9.9.9.9 Domain Name System (DNS) service. Its mission is to provide free DNS services that protect users from malicious websites while also safeguarding their privacy. A core part of this commitment is their policy of not logging or storing any personally identifiable information from your DNS queries.
Is Google DNS (8.8.8.8) safe to use?
From a technical security perspective, yes. Google's Domain Name System (DNS) is very reliable and fast, and it supports security standards like Domain Name System Security Extensions (DNSSEC), DNS over HTTPS (DoH), and DNS over TLS (DoT).
What are Level 3 DNS servers?
Level 3 Communications, now part of Lumen Technologies, is a major internet backbone provider. For many years, it operated a set of public Domain Name System (DNS) resolvers, including the well-known 4.2.2.1 and 4.2.2.2 addresses. These were among the first alternatives to internet service provider (ISP) DNS servers and gained popularity among tech-savvy users. They’re still operational today, but most modern public DNS services offer better speed and features.
Which DNS server is best?
There is no single "best" Domain Name System (DNS) server. The choice depends entirely on what you prioritize. For speed, Cloudflare (1.1.1.1) is often considered a top performer due to its large global network. If your main goal is security, a service like Quad9 (9.9.9.9) is a strong contender, offering automatic filtering against malicious domains.
What are the most common DNS records?
The most common ones you'll encounter are A and AAAA records, which map a domain to its IPv4 and IPv6 addresses. A Canonical Name record points one domain to another. Mail exchange (MX) records direct a domain's email to the correct mail server, while text (TXT) records associate text with a domain for verification purposes, like authenticating emails with Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM).
How can I set up my own DNS server?
Setting up your own Domain Name System (DNS) server is an advanced task, but it’s possible. On a home network, you can use software like Pi-hole on a Raspberry Pi. Pi-hole acts as a local DNS resolver that blocks ads and trackers for every device on your network. For public-facing DNS, administrators often use software like BIND or PowerDNS on a Linux server.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN