What is Lapsus$? A deep dive into its attacks and tactics

Lapsus$ is a small, extortion-focused group that broke into a series of high-profile organizations. It did so primarily by targeting people, identities, and everyday processes rather than carrying out complex technical exploits.
Those incidents showed how far an intruder could get by exploiting stolen passwords, weak multi-factor authentication (MFA), and insider help. They also pushed many security teams to rethink how they protect accounts and manage third-party access.
In this article, we’ll break down how the group carried out its attacks, what happened in the major incidents, and the practical steps organizations can take to avoid ending up in the same situation.
Who is the Lapsus$ group?
Lapsus$ is the name of an international, extortion-focused cyber group that ran its most active campaigns from around mid-2021 through 2022. During that time, it broke into large organizations worldwide, then used stolen data and the threat of public leaks as leverage.
One of the things that made Lapsus$ stand out was its decision to operate in public. The group ran an open Telegram channel where it announced breaches, leaked samples of stolen data, recruited insiders at targeted firms, and even ran polls asking followers which organization to go after next.
Security bodies track Lapsus$ under various names. For example, Microsoft labeled it DEV-0537 (later renamed to Strawberry Tempest in its new threat actor naming taxonomy), and MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) lists it as Group G1004 / LAPSUS$.
Most Lapsus$ activity has been traced back to a small set of members in the UK and Brazil, many of whom were teenagers at the time. Police in both countries made arrests, but the tactics it popularized (social engineering + identity abuse) are widely used by other groups.
How did Lapsus$ carry out data extortion attacks?
Lapsus$ didn’t operate like a typical ransomware group. Instead of building or deploying sophisticated malware, its attacks were largely about getting access and then using whatever sensitive data that access exposed as leverage.
In many cases, there was no file encryption at all. Microsoft has described Lapsus$ as using a pure extortion approach, where pressure came from the threat of data exposure instead of locking systems or demanding payment to restore access.
Reports about the group point to a few common themes rather than a fixed playbook. One was the misuse of legitimate accounts. Lapsus$ tended to go after weaknesses in how organizations handled logins, authentication, and account recovery, especially when those processes relied heavily on human judgment or error or could be influenced through social engineering.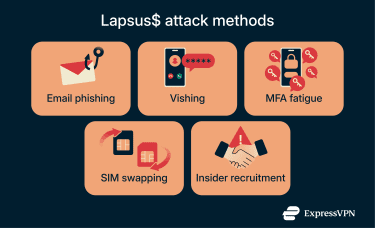
Trust relationships also played a role. Access sometimes depended on help desks, service providers, or third-party partners, and those relationships became points of exposure when controls were weak or processes were inconsistent. In some cases, insider access contributed as well, usually in a limited, transactional way rather than as part of a long-term compromise.
Overall, Lapsus$ shows that data extortion doesn’t always rely on advanced technical exploits. Even well-defended organizations can be exposed when identity systems, support workflows, or trusted relationships are easier to abuse than the technology itself.
Major Lapsus$ attacks: Companies targeted
Lapsus$ targeted high-profile brands such as chipmakers, phone manufacturers, cloud providers, telecom providers, and game studios. The goal was usually the same: break in using stolen or abused identities, grab sensitive data at speed, and then use public leaks or leak threats for leverage.
Nvidia
The Nvidia Lapsus$ hack in February 2022 became one of the group’s most widely reported intrusions. It led to the theft of what it claimed was 1TB of data and the leaking of a sample containing internal files, password hashes for more than 71,000 employees, and proprietary source code (Nvidia only confirmed that the breach happened, without specifying the amount or type of data that was stolen).
The group then tried to pressure Nvidia into removing cryptocurrency mining limits on certain GPUs and open-sourcing its drivers, threatening further leaks if the company didn’t comply. Nvidia did not comply with either demand.
Samsung
Within days of the Nvidia Lapsus$ cyberattack, Lapsus$ also claimed responsibility for a Samsung data leak that involved about 190GB of internal data. The company later confirmed that the leak contained source code for Galaxy devices.
The company stated that the incident involved internal business data and said it did not expect customer personal information to be affected.
Vodafone
In February 2022, Lapsus$ claimed it had stolen roughly 200GB of Vodafone source code from around 5,000 GitHub repositories and threatened to leak it.
Vodafone said it was investigating the claims and acknowledged that some proprietary source code may have been accessed. The company stated there was no indication that customer data or core network systems were affected.
Okta
Also in early 2022, Lapsus$ obtained remote access to the laptop of a customer support engineer at Sitel, a contractor for Okta. For about five days, the attackers could use that context to interact with a limited Okta admin interface.
When the group later posted screenshots, the Okta security incident was confirmed by the company, and it said about 2.5% of its customers (roughly 366 organizations) might have been affected, while stressing that support engineers couldn’t create or delete users or download full customer databases.
Microsoft
In March 2022, Microsoft confirmed that Lapsus$ had compromised a single employee account, granting limited access to the perpetrators. The company said no customer data or production systems were affected and emphasized that its security model does not rely on source secrecy.
Uber
The Uber security breach linked to Lapsus$ in September 2022 started with stolen credentials, an external contractor, and an MFA fatigue attack to gain access. This type of social engineering attack involves spamming push requests until one is approved.
It then pivoted into internal tools such as Google Suite, Slack, and some admin dashboards, even posting a message in a company-wide channel. Uber says it found no evidence that highly sensitive user data, like trip history or payment information, was accessed.
Rockstar Games
In September 2022, someone using the alias “teapotuberhacker” accessed Rockstar’s internal collaboration tools, reportedly including Slack, and leaked more than 90 development clips from Grand Theft Auto VI, as well as claiming to have access to game source code.
Courts later tied the Rockstar Games hack and the Uber incident to Arion Kurtaj, a key Lapsus$ member.
What is the current status of Lapsus$?
Lapsus$ is no longer dominating technology and cybersecurity headlines the way it did during its peak activity in early 2022. Law enforcement actions and the loss of its primary public communication channels significantly reduced the group’s visibility, and there have been no widely verified major breaches attributed to Lapsus$ in recent years.
The original Lapsus$ collective is generally assessed by security researchers and journalists to no longer be operating in the same organized form seen during its 2022 campaign. Public reporting suggests that the group’s activity declined sharply following arrests and coordinated law-enforcement disruption, and there has been no clear evidence of sustained operations under the Lapsus$ name since then.
In the United Kingdom, City of London Police arrested several individuals in 2022 in connection with Lapsus$ activity. One of the most prominent cases involved Arion Kurtaj, who was a minor at the time of the 2022 Rockstar Games breach. UK courts later described him as a highly capable member of the group. In December 2023, Kurtaj, who has severe autism, was given an indefinite hospital order after a judge ruled that he posed a continuing risk due to his stated intent to resume hacking if released.
While U.S. authorities, including the FBI, have publicly sought information related to Lapsus$ activity, no publicly confirmed U.S. arrests directly tied to the group have been announced.
Although the Lapsus$ name has largely disappeared from major incidents, many of the techniques it popularized, such as social engineering, credential theft, SIM swapping, and extortion without traditional ransomware, remain in active use by other threat actors. As a result, Lapsus$ is often cited as influential, even if the original group itself no longer appears to be operating as a distinct entity.
How to protect your organization from Lapsus$-style attacks
Lapsus$ proved that a strong perimeter is useless if an attacker can simply log in as an employee.
Security awareness training
In terms of employee education, standard phishing training may no longer be enough. Staff need to be informed of the specific tactics used by modern extortion groups.
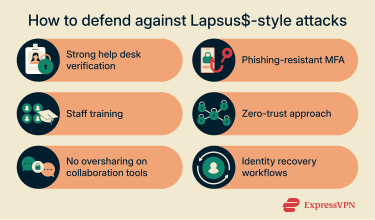
- Strengthening help desk processes: Support teams are often targeted by attackers, which makes their workflows an important area to review. Sensitive actions, such as password resets or adding a new MFA device, are generally safer when they don’t rely solely on knowledge-based checks like a mother’s maiden name. That kind of information is frequently easy for attackers to obtain. Many organizations are exploring verification steps that are harder to spoof, such as brief video confirmation or an additional approval step (for example, from a manager) before account recovery is completed.
- Raising staff awareness: Lapsus$ drew attention for using platforms like Telegram to solicit or bribe insiders for access. This highlights the value of ensuring employees know how to recognize and report unusual or inappropriate approaches, as well as understand the serious legal consequences associated with selling credentials or access.Training can also help employees recognize that attackers may try to appear credible by referencing org charts, LinkedIn profiles, or internal tools. Framing this as an issue of process manipulation (rather than just traditional phishing links) can help broaden awareness.
- Reducing oversharing in collaboration tools: Lapsus$ investigations also illustrated how screenshots, chat logs, and internal documentation shared too broadly can be misused. Encouraging staff to be cautious about posting sensitive details in public Slack or Teams channels can help limit unintended exposure. Raising awareness of “ambient data leakage” can address a risk area that is often underestimated.
Implementing technical defenses
The single most critical lesson from the Lapsus$ era is that SMS and push-based MFA are definitely not foolproof ways to protect an account. These methods are vulnerable to SIM swapping and "MFA fatigue" (spamming a user with notifications until they accept).
- Phishing-resistant MFA as a longer-term goal: Many organizations are evaluating phishing-resistant MFA options such as FIDO2 and WebAuthn. These standards support hardware security keys (like YubiKeys) and built-in authenticators such as Touch ID or Face ID. Because authentication is tied to a specific device and domain, they can significantly reduce the risk of credential reuse or fake login pages. Even if a password is exposed, access typically still depends on possession of the trusted device.
- Applying zero-trust principles: Incidents involving groups like Lapsus$ highlighted how quickly attackers can move once an initial foothold is gained. Zero-trust architectures focus on continuously validating identity, device health, and access context. In practice, this can mean requiring reauthentication for sensitive resources and avoiding situations where a virtual private network (VPN) connection or single login grants broad internal access. High-profile incidents, including Okta’s security disclosures and Lapsus$’s attempts to recruit insiders, are often cited as examples of why treating all identities (employees, contractors, and vendors alike) as potentially compromised can reduce the extent of the damage.
- Protecting identity-recovery workflows: Strong MFA controls can be undermined if recovery processes are easy to abuse. Actions such as adding a new security key, enrolling a new device, changing phone numbers, or updating email aliases tend to be safer when handled with the same care as other privileged operations. Some organizations address this by requiring higher-assurance reauthentication, logging all recovery attempts, and monitoring for unusual or unexpected changes that could indicate abuse.
Identity threat detection considerations
As attackers increasingly abuse non-human identities (API keys, service accounts, and Open Authorization (OAuth) tokens), monitoring needs to extend well beyond traditional login logs. Here are some of the capabilities that can help security teams detect and contain this category of activity:
- OAuth integration oversight: OAuth enables applications to access data without sharing passwords, but incidents involving compromised third-party integrations have underscored the value of ongoing visibility into connected apps. Periodic reviews of which applications and services have access, the permissions they hold, and whether those permissions remain necessary can help reduce risk. Removing unused or outdated OAuth grants can also limit opportunities for attackers to maintain access through overlooked integrations.
- Behavioral monitoring of identities: Monitoring for deviations from typical user behavior can help surface signs of compromised access. Examples often include near-simultaneous logins from distant locations, unexpected enrollment of new MFA or recovery methods, or sudden increases in access to sensitive data. Tools that collect identity telemetry and establish baselines of normal activity can be useful for highlighting anomalous or higher-risk behavior.
- Auditing privileged access changes: Investigations into Lapsus$ activity showed that attackers often sought to elevate privileges after an initial compromise. Having clear visibility into changes to administrative roles and sensitive group memberships, along with alerts for privilege escalations that fall outside normal workflows, can help organizations detect and respond to this kind of activity more quickly.
Incident response readiness
Lapsus$ forced security teams to rethink what an active breach looks like. The group often announced its presence while still within the network, putting legal, PR, and security teams under simultaneous pressure. Companies learned they need a pre-agreed plan for handling public extortion threats instead of improvising in the moment.
The group used legitimate tools and valid credentials, so traditional malware alerts weren’t enough. Teams had to monitor identity logs for signs of abuse, such as unexpected password resets on high-privilege accounts, new device enrollments, or unusual admin activity. Containment meant revoking session tokens immediately and isolating affected systems.
Even though these incidents targeted large companies, the underlying techniques aren’t limited to big organizations. SIM swaps, fake support calls, and MFA fatigue attacks can hit small businesses or everyday users, too, which is why stronger authentication and smarter account hygiene matter for everyone.
FAQ: Common questions about Lapsus$
What are the most common Lapsus$ tactics?
Lapsus$-style attacks typically target people rather than software bugs. The original group’s main tools were social engineering (tricking help desks), spamming login requests until a user accepts, and SIM swapping to steal phone numbers. It was also known for openly bribing employees on Telegram to provide access to corporate networks.
What makes Lapsus$ different from traditional ransomware groups?
Since it didn’t encrypt files, Lapsus$ is technically not a ransomware group. While most ransomware groups lock data and demand payment for a key, Lapsus$ stole sensitive data and threatened to leak it publicly. The group also behaved in a much more public, attention-seeking way than typical ransomware crews, often posting screenshots, internal chats, or victim polls on Telegram while attacks were still unfolding.
What should an organization do if it suspects a Lapsus$-style breach?
Assume the attacker can fully impersonate the user online. They might have the password, active session tokens, and access to SMS or email for account recovery. So the first move is to revoke active sessions and freeze any account that shows unusual activity. Security teams should also review identity logs for odd sign-ins, new device enrollments the user didn’t request, or unusual help desk interactions.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN